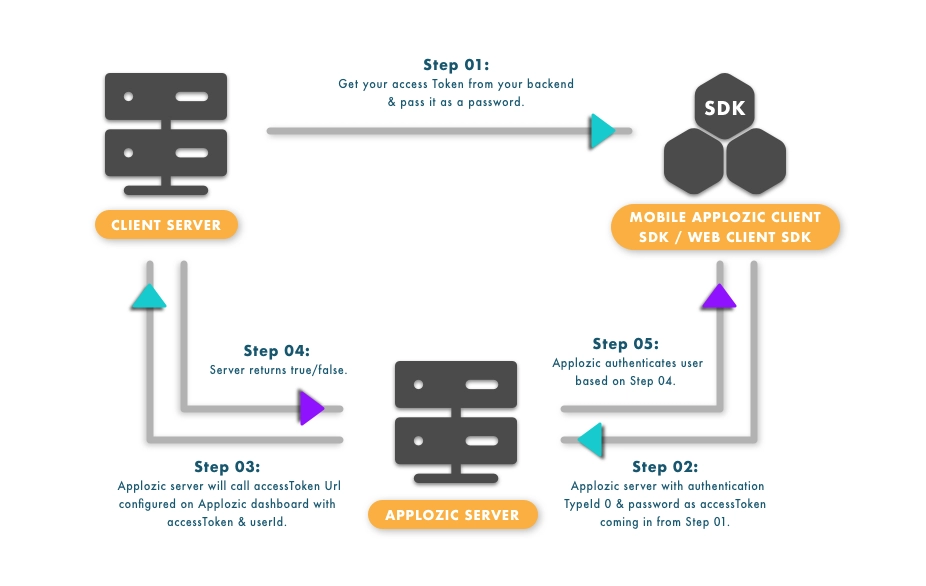
Utilization of Access token
An access token is used to identify the system used when a virus connects with an accessible object or tries to perform a system task that requires privileges. Application developers use access tokens to make API calls on behalf of users. The access token denotes a specific application's permission to access specified user data elements.
The following information is contained in access tokens:
- The user's or the user's groups' privileges are listed here.
- The current logon session is identified by a logon SID.
- SIDs for the groups that the user belongs to.
- When a user creates a secure object without specifying a security descriptor, the system uses the default DACL.
-
The user's account's security identification (SID).
Moving to the next section to learn about Elements of Token.
Elements of Access Token
An access token regularly consists of three pieces that work together to verify a user's right to access a resource. Most access tokens that include the primary three key elements are as follows:
- Header
- Payload
- Signature
Header
It contains information on the type of token and the algorithm used to create it.
Payload
It contains user information, such as permissions and expiration dates. Payload is also known as Claim Section, and it is crucial to the token's success. If you wish to visit a specific server resource but don't have the correct permissions within the payload, you won't be able to. Developers can also include whatever custom data they want in the payload.
Signature
It includes verification information so that the receiver may verify the token's originality. Because this signature is usually hashed, it is difficult to hack and duplicate.
In the next section, you will see the Types of the Access Token.
Types of Access Token
Primary and Impersonation tokens are two types of tokens available in the operating system. A primary token is always in every process that describes the user account's security context about the process. When a process virus connects with an accessible object, then By default, the system uses the primary token. Apart from this, viruses can mimic a client account, and mimicking allows the viruses to connect with accessible objects using the client's security context. A virus that mimics a client has two tokens: one primary and one mimic.
Primary Token
Primary tokens can only be connected with processes and reflect the security topic of that process. The production of primary tokens and their affiliation with functions are both beneficial procedures that necessitate two distinct advantages in the name of privilege separation. The authentication service generates the token, subsequently associated with the operating system shell via a login service. Processes inherit a copy of the parent process's primary token at the start.
Impersonation token
Impersonation is a Windows NT security feature that allows a server application to act as a client to access secure objects. Four possible levels of Impersonation are as follows:
- Impersonation enables the server to behave in the client's place.
- Giving the server access to an anonymous or unidentifiable user is Anonymous.
- Delegation is similar to Impersonation, but it extends to remote systems connected to the server.
- Thanks to the Identification, the server can check the client's identity but not utilise it to access objects
Please move to the next section to learn about how it works.
Working of Access Token
Users do not create their passwords. Servers connect with devices, and the entire process takes only a few minutes. Several steps must be taken:
Login -> Verification -> Storage -> Communication -> Deletion.
Access tokens can also be used for single sign-on (SSO). Your credentials from one site are used to gain access to another. Several steps must be taken:
Authorization -> Connection -> Storage -> Entry.
SSO requests expire fast. Most requests are valid for roughly 10 minutes; however, some are only valid for 60 seconds.
In the last section, we’ll discuss the Security concern of Access Token.
You can also read about the Multilevel Queue Scheduling.
Security of Access Token
Access tokens walk across the open space of the internet; they should be protected. Companies could allow third parties to grab tokens, which means prohibited access to crucial data that doesn't use encryption or protected communication channels. Being extremely cautious pays off.
Most access tokens have an expiration date that grants websites to ensure that whether the user is still active or not, this could aid in the avoidance of large-scale duplication or deletion. Expiration dates differ from one company to the next.
Check out this problem - Smallest Distinct Window.
Let us now see some of the FAQs related to the topic.
Must Read Evolution of Operating System
Frequently Asked Questions
What is API Access Token?
A credential that a program can use to access an API. An opaque string or a JSON Web Token (JWT) can be used as an access token. They tell the API that the bearer of the token has been granted access to a specific service or set of services.
How does the Access token Work?
Token-based authentication allows a program to access an API by using access tokens. After a user has successfully authenticated and authorized access, the application obtains an access token, which it then uses as a credential when calling the target API.
What is the use of the Access token?
Application developers use access tokens to make API calls on behalf of users. The access token denotes a certain application's permission to access specified user data elements.
How are Tokens created?
An initial coin offering (ICO) is used to create tokens. The cryptocurrency is equivalent to an IPO (IPO). Tokens are created by cryptocurrency companies that seek to raise funds. Investors with an interest in the company can purchase these tokens.
What does an Access Token contain?
The access token identifies the user, the user's groups, the user's privileges, and, in some situations, a specific application and holds the security credentials for a login session.
Conclusion
In this article, we have extensively discussed Access Token. We learned the types of Access Token and its working, the security aspect, and some faqs related to this topic.
Recommended Reading:
Refer to our Guided Path on Coding Ninjas Studio to upskill yourself in Data Structures and Algorithms, Competitive Programming, JavaScript, System Design, and many more! If you want to test your competency in coding, you may check out the mock test series and participate in the contests hosted on Coding Ninjas Studio! But suppose you have just started your learning process and are looking for questions asked by tech giants like Amazon, Microsoft, Uber, etc. In that case, you must look at the problems, interview experiences, and interview bundle for placement preparations.
Nevertheless, you may consider our paid courses to give your career an edge over others!
Do upvote our blogs if you find them helpful and engaging!
Happy Learning!