Introduction
Akamai is a technology company that provides Internet and cloud services. They are mainly known for their Edge network and Edge Network servers. They were one of the first in the world to offer Edge computing services and Edge Networks. They allow web servers to scale and provide services worldwide with very little latency.
Postman is an API development tool. Postman offers a versatile amount of services in API development, such as testing, designing, documentation, etc. Its most common use is in testing REST APIs during development since it allows automation of sending requests.

In this blog, we will discuss what edge computing is and how Akamai implements it, what Akamai EdgeGrid is, and how we can use it in Postman.
Akamai
Akamai is a technology company that provides Edge Computing and Content Delivery Network services. Their network is spread over 4200 locations and active in 1400+ networks and 135+ countries. This gives their customers a reach unlike any other.
Let’s now see what Edge Computing is.
Edge Computing
Edge Computing is a form of distributed computing in which servers, data centres, and other devices used for computation are brought closer to the users, i.e., to the network's edge. This is done by placing these devices worldwide at strategic locations. Sometimes these devices also take the form of Internet of Things (IoT) devices. Other times they are simply standard servers placed at different locations.
What benefit does this provide?
Let's assume Bob is the owner of a website hosted at a server located in Mumbai. Initially, only people in Mumbai know about his business, so only they access the website. Since their computers, phones, and devices are physically close to the server, they quickly get the data. His website quickly grows in popularity, and soon people from across India are accessing it. There is some lag, but it's not noticeable.
But what happens when someone from New York or London tries to access Bob's website?
The signals must travel across land and ocean cables to reach India, from where they are routed to Bob's server in Mumbai, and then the response is sent back the same way. This results in huge buffer times and latency.
With Edge Computing, we can solve this problem. We can place Edge servers near New York to serve all the users in the US, another for London and the UK, and, similarly, for anywhere we need. This shortens the distance between the end user and the host server, reducing latency and increasing speed.
What are the advantages of this?
-
Performance - This is the most significant benefit of an Edge Network and the reason that Edge Networks were created in the first place. By reducing the response time and latency, Edge Networks provide substantial performance improvements to a network that has users around the globe. Studies have shown that increase in response time by 1-second causes a 7% decrease in conversions, an 11% drop in views, and a 16% drop in user satisfaction.
-
Availability - An Edge Network's distributed network ensures that the website is up and running even during high traffic and congestion times. Even when 1 million requests are hitting the network, no single server has to serve all 1 million. Thus Edge Network also acts as a load balancer by distributing the loads of various requests from around the world to different servers and data centres.
If a popular E-commerce store hosts a sale starting at midnight, at that time, a lot of requests would come all together. If they were to hit a single server, it would cause a lot of load to that server, increasing response times and costs, and it might even cause the server to crash. An Edge Network prevents that.
-
Maintaining uptime even if a server goes down - Most Edge Networks today are robust, intelligent and battle-tested. Even if multiple Edge Network servers go down due to any software or hardware malfunction, the Edge Network redistributes the load to other servers that are still operational.
-
Security- Modern Edge Networks have built-in security features and won't let malicious attacks reach the origin server. Moreover, they also protect against DDoS attacks, in which attackers try to overwhelm a network by making a lot of requests in a short period. They do this so that it's impossible to distinguish malicious requests from normal ones. An Edge Network increases the network capacity by a lot; thus, it would be harder to mount a DDoS attack against an Edge Network.
Akamai Edge is one such Edge Network which leases its servers, devices and data centres to its customers so that they can scale their website and reduce latency.
Akamai EdgeGrid is the security protocol that Akamai Edge uses. Let’s now see it in detail.
Akamai EdgeGrid
Akamai EdgeGrid is a custom HTTP request signing protocol developed by Akamai. For any HTTP API request made to Akamai APIs, we need to sign them with this protocol. Otherwise, the API will treat us as an unknown user and will not grant us access to whatever resource we request. Let’s see the process of signing an HTTP request with Akamai EdgeGrid.
The two main things we will need are the client_token, client_secret and the access_token. Both will be provided when you create an Akamai account and set up access to APIs.
Let’s now see the steps involved in signing the request.
Step 1: Get the primary data
The basic details that we will need are:
-
Signing Algorithm - This is the signing algorithm followed by the rest of the steps.
For example, using EdgeGrid version 1, HMAC, and SHA-256 for hashing, this will be: EG1-HMAC-SHA256 - Client Token
- Auth Token
- Client Secret
-
Timestamp - The UTC when the request is signed. This is in the format yyyyMMddTHH:mm:ss+0000
Step 2: Create the nonce
Nonce stands for a number used once. Here, instead of a number, it is a string. It must be randomly generated. It is assigned to each request. This helps detect replayed requests, i.e. if the same request is being replayed more than once at the server due to connectivity or other issues.
Step 3: Create a signing key and signature
We do not sign our string directly with our secret key for extra security. To add additional layers of security, we generate a new signing key from our client_secret and other data.
What was the HMAC thing that we mentioned above?
HMAC is a function that takes two values - a secret key and the data to sign. Using various mathematical operations and a hash function, HMAC generates a hash output.
When we send a message to a receiver, we send them the data and the HMAC hash value. The receiver also has the same secret key as the sender. The receiver uses it to generate an HMAC of the data at their end. If their HMAC matches the one the sender sent, they will know that the data sent is secure and valid and that no one has tampered with it. Otherwise, they will reject the message.
So how do we create the signing key? The following steps are to be followed:
- Calculate HMAC of timestamp, using client_secret as key
- Encode the timestamp using base64 encoding- Base64 Encoding is an encoding scheme that converts binary data to textual data in a particular format. It is widely used, and the standards for it are known. Any data, such as text, images, numbers, etc., can be encoded in base64. The base64 encoding result will be our signing key.
- Sign the data with the signing key using HMAC
-
Base64 encode the HMAC output. This will be our signature.
Step 4: Attach the signature to the request
Finally, just one step is left!
Now, we simply attach our signature to the Authorization header in our request in the following way:
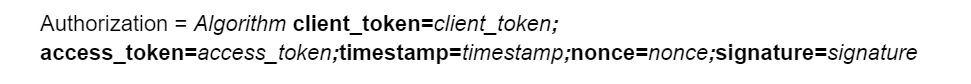
An example would be:
Authorization:EG1-HMAC-SHA256 client_token=akaa-xxxxxxxxxxxxxxxx-xxxxxxxxxxxxxxxx;
access_token=akaa-xxxxxxxxxxxxxx-xxxxxxxxxxxxxx;timestamp=20130817T02:49:13+000;
nonce=dd9957e2-4fe5-48ca-8d32-16a772ac6d8f;signature=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Attach this to your HTTP request in the Authorization header, and you’re done!
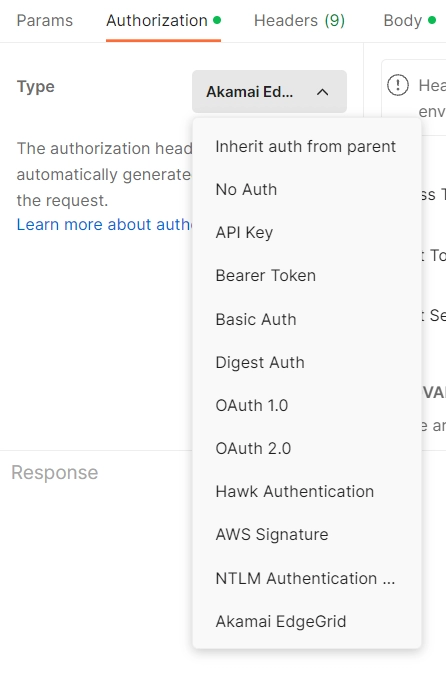
But what if we want to add our Akamai API to our Postman testing? Will we have to implement all this? Fortunately, the answer is no. Postman implements this for you. Let’s try it out!