How Amazon Elastic Container Registry(ECR) works
The Amazon Elastic Container Registry generates and packages code as a Docker image.
It then compresses, encrypts, and manages image access, as well as image lifecycles, including all tags and versions.
Finally, the Amazon ECS retrieves the required Docker images from the ECR for use in-app deployment and continues to manage containers across all platforms, including Amazon Elastic Kubernetes Service (Amazon EKS), AWS cloud, and on-premise networks.
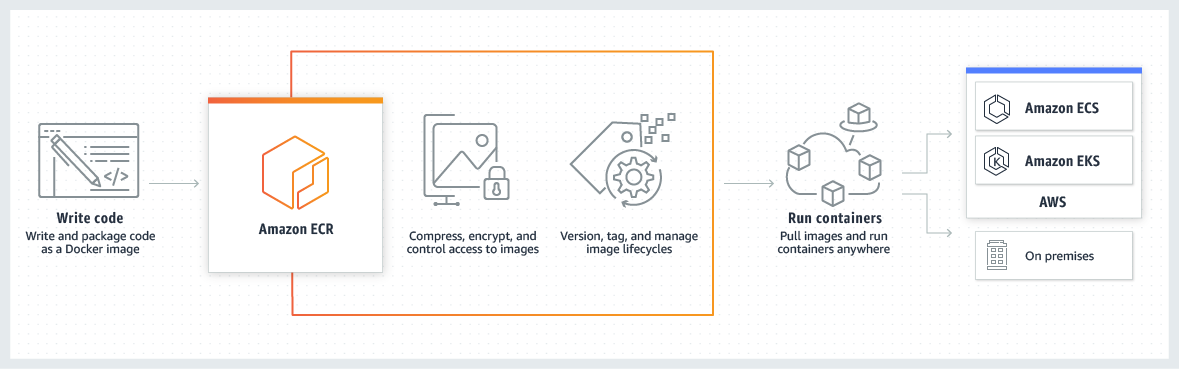
Source: Amazon ECR working
Besides that, Amazon ECR uses Amazon Simple Storage Service (Amazon S3) server-side encryption to encrypt container images at rest, and administrators can use AWS Identity and Access Management (AWS IAM) to create access restrictions for each repository. Container images are saved in S3 by the container registry for superior efficiency.
Components of Amazon Elastic Container Registry(ECR)
-
Docker images: Docker images are a type of container. That's the file that a Docker container uses to execute code.
- Repository: The Amazon ECR repository holds the Docker images. Images can be pushed and pulled from the repository by programmers.
- Repository policy: These policies are used by developers to control access to repositories and the pictures enclosed within them.
- Registry: Amazon ECR is available to all AWS accounts, making it possible to create repositories and store images in them.
-
Authorization token: The Docker client must be acknowledged as an AWS account holder before it can push and pull images.

Operations performed by Amazon ECR
The various operations like pushing a Docker image, viewing the image details, deleting an image, retagging an image, etc. are some of the operations that can be done. Everything is discussed below.

Source: AWS
Pushing a Docker image
The docker push command can be used to push your Docker containers to an Amazon ECR repository. Amazon ECR also allows you to create and push Docker express lists, which are used to create multi-architecture images. Each image in a manifest list must have already been pushed to your repository.
Pushing a Docker image to an Amazon ECR repository
- Log in to the Amazon ECR registry where you plan to push your image with your Docker client. For each registry that is used, authentication tokens must be obtained, and the tokens are genuine for 12 hours.
- If your picture repository does not yet appear in the registry to which you intend to push, create it.
- Determine which local image to push. To list the container, use the docker images command.
- Use the Amazon ECR registry, repository, and optional image tag name combination to tag your image. The registry format is aws_account_id.dkr.ecr.region.amazonaws.com.
-
Use the docker push command to push the image: docker push aws_account_id.dkr.ecr.region.amazonaws.com/my-repository:tag
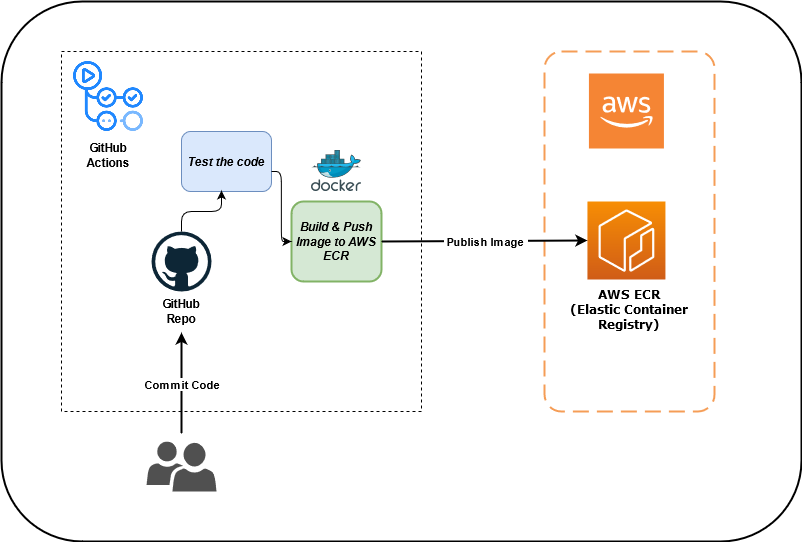
Source: Build and push docker image AWS ECR using GitHub actions
Viewing image details
You can view an image's details in the AWS Management Console after you've pushed it to your repository. The following information is included:
- Image URI
- Image tags
- Artifact media type
- Image manifest type
- Scanning status
- The size of the image in MB
- When the image was pushed to the repository
- The replication status
To view image details, click here (AWS Management Console):
-
Go to https://console.aws.amazon.com/ecr/repositories to reach the Amazon ECR console.
- Select the Region that holds the repository comprising your image from the navigation bar.
- Select Repositories from the navigation pane.
- Select the repository to display.
- On the Repositories: repository_name page, choose the image to view the details.
Pulling an image
The docker pull command to pull your image to your local environment.
To retrieve a Docker image out of an Amazon ECR repository.
- Authenticate your Docker client with the Amazon ECR registry from which you want to pull your image. For each registry that is used, authentication tokens must be obtained, and the tokens are genuine for 12 hours.
- Select the image to be pulled.
- Use the AWS ecr describe-images command to describe the images in a repository. aws ecr describe-images --repository-name
-
By using the docker pull command, pull the image. To pull by tag, the image name format must be registry/repository[:tag]; to pull by digest, the image name format should be registry/repository[@digest].
 Source: Docker image
Source: Docker image
Using pull through cache rules
Pull limits and costs are associated with Docker Hub, Quay, and other registry providers. Trying to run large builds (or many small builds on a regular basis) may result in costs, rate limiting, or both. The use of a "pull-through" cache reduces network traffic while avoiding the limits placed by registry providers.
A registry mirror with no images is regarded as a pull-through cache. When your client searches the registry for an image, the registry will either:
Provide an existing response from its cache, avoiding egress (or a pull) from your registry, or
Alternatively, you can have the image and its metadata pulled from the registry on your behalf and cached for later use.
Deleting an image
After an image has completed its task, you can delete it.
To remove an image (AWS Management Console)
-
Go to https://console.aws.amazon.com/ecr/repositories to access the Amazon ECR console.
- From the navigation bar, select the Region containing the image to be deleted.
- Select Repositories from the navigation pane.
- On the Repositories page, select the repository containing the image to be deleted.
- On the Repositories: repository_name page, click Delete in the box to the left of the image you want to delete.
- In the Delete image(s) dialogue box, confirm that the images you want to delete should be deleted and click Delete.
Retagging an image
To retag an existing image with Docker Image Manifest V2 Schema 2 images, you can use —image-tag option of the put-image command.
Using the AWS CLI to retag an image
- Run the batch-get-image command to obtain the image manifest for the image to be retagged and save it to a file.
- Use the —image-tag option of the put-image command to add a new tag to the image manifest in Amazon ECR.
- Check to see if your new image tag is tied to your image.
Private image replication
Amazon ECR configures private image replication at the registry level using registry settings. A private registry hosted by Amazon ECR can be configured for cross-region or cross-account replication. Each Region has its own replication configuration for a private registry. The following section goes into greater detail about the replication methods that are supported.
Cross-region replication: Enabling cross-Region replication for your registry creates replicas of the repositories in one or more desired location Regions. Only images that are pushed to a repository ever since cross-Region replication has been configured are copied.
Cross-account replication: Enabling cross-account replication for your registry creates replicas of the repositories in the location account and Regions you specify. To enable cross-account replication, the destination account must set up a registry permissions policy that allows replication from your registry.
Lifecycle policies
AWS offers ECR Lifecycle policies, which allow users to set validity periods for their images. This means that you can automate the deletion of ECR images that you no longer require. Many other AWS services, such as S3 buckets, include lifecycle policies.
use cases: There are numerous use cases for applying a lifecycle policy to ECR containers:
- Create more space: Both free-tier users will receive 50 GB of always-free storage for their public repositories per month. However, for private repositories, only have entry to 500MB of disk space per month.
-
Lower storage costs: The cost of storage above these free-tier limits For data stored in both private and public repositories, storage costs $0.10 per GB per month.
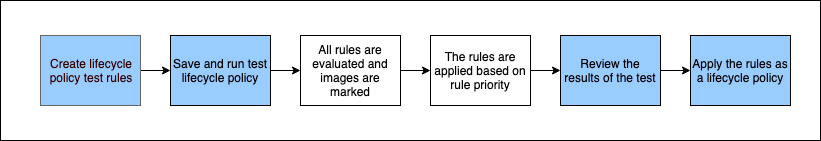
The above picture depicts the workflow of the lifecycle policy
- Establish one or maybe more test rules.
- Save all the test rules before running the preview.
- The lifecycle policy evaluator would go through all rules and note which images each rule affects.
- Based on rule priority, the lifecycle policy evaluator then applies the rules and displays which images in the repository are set to expire.
- Examine the test results to ensure that the images marked as expired are the ones you intended.
- Use the test rules as the repository's lifecycle policy.
- After the lifecycle policy is developed, the images that are affected expire within 24 hours.
Image tag mutability
Immutable tags are supported by Amazon ECR, which prevents image tags from becoming overridden. Previously, ECR tags could be overwritten; however, this could be avoided by mandating users to authenticate an image using a naming convention.
Tag immutability allows users to rely on an image's descriptive tags as a mechanism for tracking and uniquely identifying images. By making an image tag immutable, developers can use it to link the deployed image version to the build that created it.
Image scanning
You can use Amazon ECR image scanning to scan your Docker images against Known Vulnerabilities without paying anything extra or deploying a third-party scanning tool (CVEs). Amazon ECR uses the open-source CoreOS Clair project's CVE database to provide you with a list of scan findings and vulnerability scores. Static container image scanning is supported for major versions of Amazon Linux, Amazon Linux 2, Debian, Ubuntu, CentOS, Oracle Linux, Alpine, and RHEL Linux distributions. The following scanning types are available.
- Improved scanning—Amazon ECR works in conjunction with Amazon Inspector and provides automated, continuous scanning of your repositories.
- Basic scanning—Amazon ECR makes use of the open-source Clair project's Known Vulnerabilities (CVEs) database.
Container image manifest formats
Amazon ECR supports the container image manifest styles listed below:
- Schema 1 of the Docker Image Manifest V2 (used with Docker version 1.9 and older)
- Docker Image Manifest Version 2 Schema (used with Docker version 1.10 and newer)
- Specifications of the Open Container Initiative (OCI) (v1.0 and up)
Support for Docker Image Manifest V2 Schema 2 adds the following features:
- The possibility to use multiple tags on the same image.
- Storage of Windows container images is supported.
Using Amazon ECR Images with Amazon ECS
The following are the prerequisites for using Amazon ECR Images with Amazon ECS:
- While using the EC2 launch type for the Amazon ECS tasks, your container instances must use the Amazon ECS container agent version 1.7.0 or later.
- The Amazon ECS container instance IAM role (ecsInstanceRole) that you use must have the appropriate Amazon ECR IAM policy permissions.
- Ensure that you use the full registry/repository:tag naming convention for your Amazon ECR images in your Amazon ECS task definitions.
Using Amazon ECR Images with Amazon EKS
Amazon Elastic Kubernetes Service is a Kubernetes service provided by AWS infrastructure. Kubernetes resources, like any other AWS service, will be fully managed by AWS, reducing the burden on developers to maintain them. AWS also ensures that these resources are always highly available and reliable.
Necessary requirements:
-
Kubectl — This is the communication tool that we will use to interact among our Kubernetes cluster and device. Instructions for installation can be found at https://kubernetes.io/docs/tasks/tools/install-kubectl/.
-
AWS Command Line Interface (CLI) — An AWS tool that will be used to issue commands related to AWS configurations. Follow this link to install: https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-configure.html
-
AWS iam authenticator — Grant access to our Kubernetes cluster using IAM roles. https://docs.aws.amazon.com/eks/latest/userguide/install-aws-iam-authenticator.html
- eksctl — AWS EKS's official CLI tool.
Amazon Linux container image
The Amazon Linux container image is made up of the same software components as the Amazon Linux AMI. It can be used as a reference image for Docker workloads in any environment. If you use the Amazon Linux AMI for applications in Amazon EC2, you can containerize them using the Amazon Linux container image.
In your local software platform, you can use the Amazon Linux container image and then push your application to AWS via Amazon ECS.
To obtain the Amazon Linux container image from Amazon ECR Public, follow these steps.
- Log in to the Amazon Linux Public Registry with your Docker client. Authentication tokens are valid for a period of 12 hours.
- Use the docker pull command to obtain the Amazon Linux container image.
- Start the container locally.
Amazon ECR private repositories
Amazon ECR provides API operations for creating, monitoring, and deleting image repositories, as well as setting permissions that regulate who has direct connections to them.
Creating a private repository
To create a repository, follow the steps below:
-
Go to https://console.aws.amazon.com/ecr/repositories to access the Amazon ECR console.
- From the navigation bar, select the Region in which you want to create your repository.
- Select Repositories from the navigation pane.
- On the Repositories page, select the Private tab, followed by Create repository.
- In the Visibility settings, make sure that Private is selected.
- Enter a unique name for your repository in the Repository name field.
- For Tag immutability, select the repository's tag mutability setting. Immutable tags in repositories protect image tags from becoming overridden.
- For Scan on Push, while basic scanning can be configured at the repository level, it is best practice to configure the scan configuration at the private registry level.
- Select whether to enable AWS Key Management Service encryption of images in the repository for KMS encryption. When KMS encryption is activated, Amazon ECR utilizes an AWS managed key (KMS key) with the alias aws/ecr by default. When KMS encryption is enabled, go to Customer encryption settings (advanced) and enter your own KMS key.
- Select Create repository.
Viewing private repository details
The following details can be viewed:
- What types of images are saved in a repository?
- Information about each image in the repository, such as its size and SHA digest.
- The frequency with which the repository's contents are scanned
- Whether or not the repository is associated with an active pull-through cache rule.
- The repository's encryption settings.
Editing a private repository
To edit a repository, follow these steps:
- Select the Region that includes the repository to edit from the navigation bar.
- Select Repositories from the navigation pane.
- On the Repositories page, click the Private tab, then click the repository you want to edit and click Edit.
- For Tag immutability, select the repository's tag mutability setting.
- For image scan settings, while basic scanning can be specified at the repository level, it is best practise to specify the scan configuration at the private registry level.
- This is a view-only field for Encryption settings.
- Select Save to save the repository settings.
Deleting a private repository
To delete a repository, follow these steps:
-
Go to https://console.aws.amazon.com/ecr/repositories to access the Amazon ECR console.
- From the navigation bar, select the Region containing the repository to be deleted.
- Select Repositories from the navigation pane.
-
On the Repositories page, select the Private tab, then select the repository to remove and press the Delete button.In the Delete repository name window, confirm that the chosen repositories should be removed and press the Delete button.
See this, Amazon Hirepro
Benefits of Amazon Elastic Container Registry(ECR)
-
Increased security is one of the most significant benefits offered by Amazon ECR. In Amazon ECR, all images are sent over HTTPS. To ensure increased security, images at rest are instantly encrypted.

Source: ECR
- For the interface, AWS security groups can be chosen to control if each host is allowed to communicate with it. AWS security groups are online firewalls that can be easily created, attached, and deleted at the instance level.
- The Amazon ECR architectural style is scalable, long-lasting, and redundant. As a result, Docker images are readily available and accessible, allowing users to deploy new containers for their apps quickly and reliably.
- Amazon ECR does not provide any software that must be installed and managed, nor does it include a scalable infrastructure. Users simply upload images to ECR and retrieve them when they're needed using any container management tool.
Frequently Asked Questions
What is the pricing for Amazon ECR?
There are no costs involved or commitments with Amazon ECR. You only pay for the data you save in your public or private libraries, as well as the data you upload to the internet.
What is the difference between Amazon ECR public and private repositories?
A private repository does not support content search and needs Amazon IAM-based authentication with AWS account credentials before photos may be retrieved. A public repository contains descriptive content and lets anyone from anywhere pull photos without the requirement for an AWS account or IAM credentials. The Amazon ECR public gallery also has photographs from public repositories.
Does the Amazon ECR public gallery provide AWS-published images?
Yes. Amazon ECR hosts official public use container images and artifacts from services including Amazon EKS, Amazon SageMaker, and AWS Lambda.
Does Amazon ECR work with Amazon ECS?
Yes. Amazon ECR is linked with Amazon ECS, making it simple to store, execute, and manage container images for Amazon ECS-based applications. Simply specify the Amazon ECR repository in your task configuration, and Amazon ECS will retrieve the images you require for your applications.
Conclusion
To summarise this blog, we first talked about Amazon Elastic Container Registry (ECR), how to set it up, and how it works, and then we talked about the components and benefits of Amazon Elastic Container Registry (ECR).
Refer to our guided paths on Coding Ninjas Studio to upskill yourself in Data Structures and Algorithms, Competitive Programming, JavaScript, System Design, and many more! If you want to test your competency in coding, you may check out the mock test series and participate in the contests hosted on Coding Ninjas Studio! But if you have just started your learning process and looking for questions asked by tech giants like Amazon, Microsoft, Uber, etc; you must have a look at the problems, interview experiences, and interview bundle for placement preparations.
Nevertheless, you may consider our paid courses to give your career an edge over others!
Do upvote our blogs if you find them helpful and engaging!
Happy Learning!












