What's the History of Asymmetric Cryptography?
Asymmetric cryptography didn't just appear overnight; it has a fascinating history that traces back to the early days of cryptographic research. It's a tale of evolving technology and groundbreaking ideas that paved the way for secure digital communication as we know it today.
The concept of public key cryptography was first published in 1976 by Whitfield Diffie and Martin Hellman. This was revolutionary because, until then, all cryptographic systems were symmetric, meaning they used the same key for both encryption and decryption. Diffie and Hellman's paper introduced a new idea: a cryptographic system where the keys used for encryption and decryption were different. This system could solve the fundamental problem of key distribution – a major hurdle in cryptographic communications.
Their work laid the groundwork for the RSA algorithm, named after its inventors, Ron Rivest, Adi Shamir, and Leonard Adleman, who first publicly described it in 1978. The RSA algorithm was the first to enable secure communication over a public channel without needing a shared secret key in advance.
Understanding the historical context of asymmetric cryptography helps appreciate its profound impact on digital security. From securing emails to authenticating digital signatures, the principles established in the 1970s are still in use today, underlying the security of modern internet communications.
How Does Asymmetric Cryptography Work?
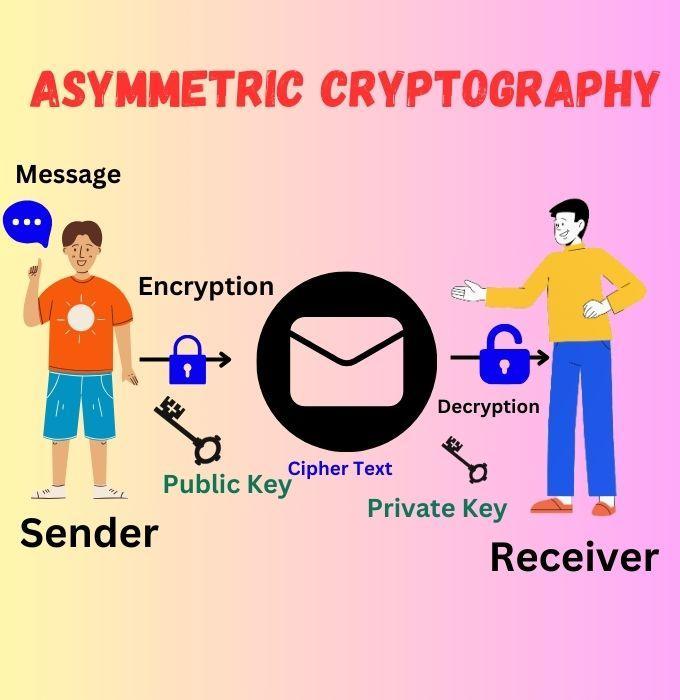
Asymmetric cryptography, unlike its symmetric counterpart, utilizes a pair of keys – a public key and a private key – for encryption and decryption. This key pair is bound together by mathematical relationships, yet they are not identical. This distinction is crucial for the security and functionality of asymmetric cryptography.
The Key Pair Mechanism
Key Generation
The process starts with the creation of the keys. A large number, typically a prime number, is chosen. This number is used in a mathematical algorithm to generate two keys. These keys are mathematically related yet functionally distinct.
Encryption
When a message needs to be sent securely, the sender encrypts it using the recipient's public key. This key is available to anyone, and once a message is encrypted with this key, it cannot be decrypted by it again.
Decryption
On the other side, the recipient uses their private key to decrypt the message. The private key is not shared and remains confidential with the recipient. The unique aspect here is that the message encrypted with the public key can only be decrypted by its corresponding private key.
Example in Python
Let's look at a simple Python example to understand this better:
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives.asymmetric import rsa
from cryptography.hazmat.primitives import serialization, hashes
from cryptography.hazmat.primitives.asymmetric import padding
# Generate the public and private keys
private_key = rsa.generate_private_key(
public_exponent=65537,
key_size=2048,
backend=default_backend()
)
public_key = private_key.public_key()
# Message to be encrypted
message = b"Secure message using asymmetric cryptography"
# Encrypting the message
encrypted = public_key.encrypt(
message,
padding.OAEP(
mgf=padding.MGF1(algorithm=hashes.SHA256()),
algorithm=hashes.SHA256(),
label=None
)
)
# Decrypting the message
original_message = private_key.decrypt(
encrypted,
padding.OAEP(
mgf=padding.MGF1(algorithm=hashes.SHA256()),
algorithm=hashes.SHA256(),
label=None
)
)
print("Original Message:", original_message)

You can also try this code with Online Python Compiler
In this script, we use the RSA algorithm to generate a private key and then derive the public key from it. We encrypt a message using the public key and decrypt it using the private key, demonstrating the fundamental principle of asymmetric cryptography.
Uses of Asymmetric Cryptography
Asymmetric cryptography has become a cornerstone of modern digital security. Its unique properties make it ideal for a variety of applications, far beyond basic encrypted communication. Here are some of the key areas where asymmetric cryptography shines:
Secure Communications
The most common use of asymmetric cryptography is to secure data transmission over the internet. Whether it's emails, messaging apps, or secure file transfers, asymmetric cryptography ensures that only the intended recipient can access the sent information.
Digital Signatures
Asymmetric cryptography enables digital signatures, which provide authentication, integrity, and non-repudiation to digital documents. For example, when you sign a PDF electronically, asymmetric cryptography is at work, ensuring that the signature is valid and the document hasn't been tampered with.
SSL/TLS for Secure Websites
Every time you see a padlock icon in your web browser's address bar, it's a sign that asymmetric cryptography is being used. SSL/TLS protocols use asymmetric cryptography to establish a secure connection between your browser and the website, safeguarding any data exchanged.
Cryptocurrency Transactions
In the world of cryptocurrencies like Bitcoin and Ethereum, asymmetric cryptography is used to create and manage wallets and transactions. Your private key is essential to authorize transactions, ensuring that only you can spend your digital currency.
Government and Military Communications
Asymmetric cryptography plays a crucial role in protecting sensitive government and military communications. Its ability to secure data makes it invaluable in scenarios where information confidentiality is paramount.
Access Control in Corporate Environments
In corporate settings, asymmetric cryptography can be used for access control, ensuring that only authorized individuals can access certain data or systems.
IoT Device Security
With the rise of the Internet of Things (IoT), securing the vast array of connected devices becomes critical. Asymmetric cryptography offers a way to authenticate devices and secure the data they transmit.
Each of these applications demonstrates the versatility and importance of asymmetric cryptography in our digital world. Its ability to secure communications, authenticate parties, and guarantee data integrity makes it an indispensable tool in many areas.
Advantages and Disadvantages of Asymmetric Cryptography
Asymmetric cryptography, like any technology, has its share of strengths and weaknesses. Understanding these can help us appreciate where it excels and where it might need support from other cryptographic methods.
Advantages of Asymmetric Cryptography
Enhanced Security
The use of two keys (public and private) adds an extra layer of security. Since the private key is never shared, the risk of interception is significantly reduced.
Simplified Key Distribution
In asymmetric cryptography, there’s no need for the sender and receiver to share a secret key in advance. The public key can be openly distributed without compromising security.
Digital Signatures
Asymmetric cryptography enables the use of digital signatures, which provide authentication, data integrity, and non-repudiation. This is crucial for legal and financial transactions.
Versatility
It’s used in various applications, from secure email communications to blockchain transactions, demonstrating its flexibility and wide applicability.
Disadvantages of Asymmetric Cryptography
Computational Intensity
Asymmetric algorithms require more computational power compared to symmetric ones, making them slower for certain applications.
Key Management
Managing public and private keys, especially in large-scale deployments, can be complex and challenging.
Vulnerability to Certain Attacks
While highly secure, asymmetric cryptography is not immune to certain types of cryptographic attacks, like man-in-the-middle attacks, if not implemented with proper safeguards.
Size Limitations
Asymmetric cryptography is not well-suited for encrypting large amounts of data due to its computational demands and the size of the ciphertext it produces.
Asymmetric vs Symmetric Cryptography
In the vast world of digital security, understanding the distinction between asymmetric and symmetric cryptography is key to comprehending their applications and limitations. Both play vital roles but in different contexts.
Asymmetric Cryptography
Asymmetric cryptography, as we've discussed, involves two keys - a public key for encryption and a private key for decryption. It's ideal for scenarios where secure key exchange over an insecure medium is necessary.
Key Characteristics
-
Two keys (public and private) are involved.
-
It provides a solution for key distribution issues.
-
Well-suited for digital signatures and establishing secure connections.
- Typically slower due to more complex algorithms.
Symmetric Cryptography
Symmetric cryptography, on the other hand, uses a single key for both encryption and decryption. This key must be kept secret and shared between the parties involved in the communication.
Key Characteristics
-
Only one key is used for both encryption and decryption.
-
The key must be shared and kept secret, making key distribution challenging.
-
Faster and more efficient for encrypting large volumes of data.
- Commonly used for bulk data encryption.
The Comparison
Key Management
Symmetric cryptography's biggest challenge is the secure distribution of the secret key. Asymmetric cryptography addresses this issue with its public/private key mechanism.
Performance
Symmetric cryptography is generally faster and more efficient, especially for large data volumes. Asymmetric cryptography is computationally heavier, making it slower in comparison.
Use Cases
Asymmetric cryptography is often used for establishing secure communication channels (like SSL/TLS for websites) and digital signatures. Symmetric cryptography is preferred for continuous data encryption due to its efficiency.
Security Level
Both offer high security, but the methods of attack and defense differ. Asymmetric cryptography is more about protecting the private key, while symmetric cryptography focuses on protecting the single shared key.
Examples of Asymmetric Cryptography
Asymmetric cryptography is not just a theoretical concept; it's a practical tool used in various aspects of our digital lives. Here are a few examples that illustrate its wide-ranging applications:
Email Encryption (PGP - Pretty Good Privacy)
One of the earliest and most famous uses of asymmetric cryptography is in PGP for email encryption. PGP uses a combination of asymmetric and symmetric encryption to secure emails. The message is encrypted using symmetric cryptography, while the symmetric key is encrypted using the recipient's public key. This ensures that only the intended recipient can decrypt the message.
SSL/TLS Protocols for Secure Internet Browsing
When you visit a secure website (indicated by HTTPS), asymmetric cryptography is at work. SSL/TLS protocols use asymmetric cryptography to establish a secure connection between your browser and the server. Initially, asymmetric cryptography is used to securely exchange a symmetric key, which is then used for the rest of the session for efficient encryption.
Blockchain and Cryptocurrencies
Blockchain technology and cryptocurrencies like Bitcoin heavily rely on asymmetric cryptography. Each user has a public and private key pair. Public keys serve as addresses for receiving funds, while private keys are used to sign transactions, ensuring that only the owner of the private key can spend their cryptocurrencies.
Digital Signatures in Document Signing
Digital signatures in electronic documents use asymmetric cryptography to verify the authenticity of the document. When you digitally sign a document, you use your private key to encrypt the signature. The recipient can then use your public key to decrypt and verify that it's truly from you.
Secure Shell (SSH) for Secure Remote Logins
SSH, used for secure remote logins to servers, uses asymmetric cryptography to establish a secure and encrypted communication channel. The server has a public/private key pair, and the client uses the public key to authenticate the server's identity and establish an encrypted connection.
Each of these examples highlights the versatility and importance of asymmetric cryptography in providing secure digital communication, authentication, and data integrity. From sending confidential emails to signing documents and securing online transactions, asymmetric cryptography plays a pivotal role in our digital security infrastructure.
Frequently Asked Questions
How does asymmetric cryptography ensure data confidentiality?
Asymmetric cryptography uses two keys: a public key for encryption and a private key for decryption. Data encrypted with the public key can only be decrypted by its corresponding private key, ensuring that only the intended recipient can access the information.
Can asymmetric cryptography be used for large data encryption?
While theoretically possible, asymmetric cryptography is not typically used for encrypting large volumes of data due to its computational intensity. It's more commonly used for encrypting small pieces of data, like keys or small messages.
Is asymmetric cryptography completely secure?
No cryptographic system can be deemed completely secure, but asymmetric cryptography provides a high level of security. The main vulnerability lies in the private key; if it is compromised, the security of the system is breached.
Conclusion
Asymmetric key cryptography stands as a pillar in the realm of digital security. From its fascinating history and intricate workings to its diverse applications and comparison with symmetric cryptography, we've explored the various facets of this powerful cryptographic method. Asymmetric cryptography not only secures our digital communications but also plays a crucial role in authentication and data integrity. Understanding its principles and applications equips us with knowledge critical in today's digitally interconnected world.
You can refer to our guided paths on the Coding Ninjas. You can check our course to learn more about DSA, DBMS, Competitive Programming, Python, Java, JavaScript, etc.
Also, check out some of the Guided Paths on topics such as Data Structure and Algorithms, Competitive Programming, Operating Systems, Computer Networks, DBMS, System Design, etc., as well as some Contests, Test Series, and Interview Experiences curated by top Industry Experts.