Introduction
UGC NET Exam is a very popular exam in India for people interested in the research domain. NET(National Eligibility Test) is conducted by NTA (NATIONAL TESTING AGENCY) to identify qualified candidates for Assistant Professor positions in colleges and universities, as well as Junior Research Fellowships (JRF). This article will discuss the UGC NET Exam of Aug 2016 Paper-III (Re-Test) - Part 2 solutions from questions 25 to 50. You can find the solutions to Q1 to 25 in Aug 2016 Paper-III (Re-Test) - Part 1 and Q51 to 75 in Aug 2016 Paper-III (Re-Test) - Part 3.
Questions
25.Suppose transmission rate of a channel is 32 kbps. If there are ‘8’ routes from source to destination and each packet p contains 8000 bits. Total end to end delay in sending packet P is ................
(A) 2 sec (B) 3 sec
(C) 4 sec (D) 1 sec
Answer: A
Solution: It is assumed that a channel's transmission rate is 32 kbps, that there are eight paths from source to destination, and that each packet p has 8000 bits.Routes * packets / transmission rate = total delay.8 * 8000 bits per second / 32 kbps = 8 * 8000 bits per second / 32000 bits per second = 2 seconds
26.Consider the following statements :
a. High speed Ethernet works on optic fiber.
b. A point to point protocol over Ethernet is a network protocol for encapsulating PPP frames inside Ethernet frames.
c. High speed Ethernet does not work on optic fiber.
d. A point to point protocol over Ethernet is a network protocol for encapsulating Ethernet frames inside PPP frames.
Which of the following is correct ?
(A) a and b are true; c and d are false.
(B) a and b are false; c and d are true.
(C) a, b, c and d are true.
(D) a, b, c and d are false.
Answer: A
Solution: Optical fibre is used for high-speed Ethernet. Correct
A point-to-point protocol over Ethernet is a network protocol that encapsulates PPP frames inside Ethernet frames rather than PPP frames inside Ethernet frames.Correct.
27.In CRC checksum method, assume that given frame for transmission is 1101011011 and the generator polynomial is G(x) = x4 + x + 1.
After implementing CRC encoder, the encoded word sent from sender side is .............
(A) 11010110111110
(B) 11101101011011
(C) 110101111100111
(D) 110101111001111
Answer: A
Solution:Generator x 4 + x+ 1 can be written as 10011
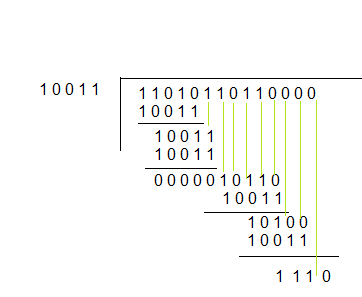
append remainder 1110 to the actual word.
We have to append 1110 to the frame. Now our frame for transmission is 11010110111110.
28.A slotted ALOHA network transmits 200 bits frames using a shared channel with 200 kbps bandwidth. If the system (all stations put together) produces 1000 frames per second, then the throughput of the system is .................
(A) 0.268 (B) 0.468
(C) 0.368 (D) 0.568
Answer: C
Solution: G =1 S=G×e−G=0.368 (36.8%)
Throughput = 1000 × 0.0368 = 368 frames.
29.An analog signal has a bit rate of 8000 bps and a baud rate of 1000.
Then analog signal has .............. signal elements and carry ............ data elements in each signal.
(A) 256, 8 bits (B) 128, 4 bits
(C) 256, 4 bits (D) 128, 8 bits
Answer: A
Solution: The bit rate of an analogue signal is 8000 bits per second, while the baud rate is 1000. As a result, bit rate / baud rate bits will be plainly visible in each communication.
i.e. 8000 / 1000 = 8 bits and 28 = 256 signal.
30. The plain text message BAHI encrypted with RSA algorithm using e=3, d=7 and n=33 and the characters of the message are encoded using the values 00 to 25 for letters A to Z. Suppose character by character encryption was implemented. Then, the Cipher Text message is ............
(A) ABHI (B) HAQC
(C) IHBA (D) BHQC
Answer: B
Solution: RSA Encryption algorithm
Obtains the public key of recipient B. (n, e).
The plaintext message is represented as a positive integer m, 1 < m < n
calculate the ciphertext c = m*e mod n.
Sends the ciphertext c to the RECEIVER
Decryption
We Use his private key (n, d) to compute m = cd mod n.
Extracts the plaintext from the message representative m.
For word BAHI
A-1 ,B-2, C-3 , D-4,E-5,F-6,.... etc (Message Encoded Using 01-26)
B -->2=> 27 mod 33 = 8 =>H
A --> 1=>17 mod 33 = 1 =>A
H -->8=> 87 mod 33 = 17 =>Q
I--> 9=>97 mod 33 = 3 => C
Cipher Text Message for word BAHI = HAQC
A-0 ,B-1, C-2 , D-3,E-4,F-5,.... etc ( Message Encoded Using 00-25 as per question)
B-->1=> 17 mod 33 = 0 =>B
A --> 0=>07 mod 33 = 1 =>A
H -->7=> 77 mod 33 = 13 =>N
I--> 8=>87 mod 33 = 17 => R
Cipher Text Message : BANR
31.Consider the problem of a chain <A1, A2, A3, A4> of four matrices. Suppose that the dimensions of the matrices A1, A2, A3 and A4 are 30 × 35, 35 × 15, 15 × 5 and 5 × 10 respectively. The minimum number of scalar multiplications needed to compute the product A1A2A3A4 is ................
(A) 14875 (B) 21000
(C) 9375 (D) 11875
Answer: C
Solution: For the smallest number of scalar multiplications, matrix parenthesizing will be A1((A2A3)A4).
Dynamic programming will be used to tackle this problem.
The given matrix has the following dimensions:
A1 (30×35) , A2 (35×15 ) , A3 ( 15×5 ) and A4 (5×10)
A12=30×35×15=15750
A23=35×15×5=2625
A34=15×5×10=750
A13 = min ( A12 + A33 + 35×15×5 = 18375, A11 + A23 + 30×35×5=9375 )
A24= min ( A23 + A44 + 5×10×5 =9375 , A22+ A34 +5×20×5= 6776)
A14 = min ( A11 + A24 + 10×5×5 , A12 + A34 + 10×20×5>= 6736 , A13 + A44 + 10×20×5 )
32.Consider a hash table of size m = 10000, and the hash function h(K)=floor(m(KAmod1)) for A = (√5 – 1)/2. The key 123456 is mapped to location ...............
(A) 46 (B) 41
(C) 43 (D) 48
Answer: B
Solution: h(123456) = floor(10000 * (123456 * (√5 − 1) / 2) mod 1)
= floor(10000 * (76300.004115 mod 1)
= floor(10000 * (.004115))
= 41.15
= 41
33.Consider a weighted complete graph G on the vertex set {v1, v2, …. vn} such that the weight of the edge (vi, vj) is 4 |i – j|. The weight of minimum cost spanning tree of G is:
(A) 4n2 (B) n
(C) 4n – 4 (D) 2n – 2
Answer: C
Solution: Weight of the minimum spanning tree
=4|2 – 1| + 4|3 – 2| + 4|4 – 3| + …. + 4| n – (n-1) |
= 4n – 4
34. A priority queue is implemented as a max-heap. Initially, it has five elements. The level-order traversal of the heap is as follows:
20, 18, 15, 13, 12
Two new elements ‘10’ and ‘17’ are inserted in the heap in that order. The level-order traversal of the heap after the insertion of the element is:
(A) 20, 18, 17, 15, 13, 12, 10
(B) 20, 18, 17, 12, 13, 10, 15
(C) 20, 18, 17, 10, 12, 13, 15
(D) 20, 18, 17, 13, 12, 10, 15
Answer: D
Solution: When inserting data in a heap, it is always done from left to right at the last level. So we add 1 and 7 as children of node 5, then run the heapify algorithm until the heap property is met, and we get a heap with level order traversal of 10,8,7,3,2,1,5.
35. If there are n integers to sort, each integer has d digits, and each digit is in the set {1, 2, …, k}, radix sort can sort the numbers in:
(A) O (k (n + d)) (B) O (d (n + k))
(C) O ((n + k) l g d)(D) O ((n + d) l g k)
Answer: B
Solution: Radix sort is a digit-by-digit sorting method that starts with the least significant digit and progresses to the most significant digit.
36.Match the following:
a. Prim’s algorithm i. O(V2E)
b. Bellman-Ford algorithm ii. O(VE lgV)
c. Floyd-Warshall algorithm iii. O(E lgV)
d. Johnson’s algorithm iv. O(V3)
Where V is the set of nodes and E is the set of edges in the graph.
Codes :
a b c d
(A) i iii iv ii
(B) i iii ii iv
(C) iii i iv ii
(D) iii i ii iv
Answer: C
37. Constructors have ............. return type.
(A) void(B) char
(C) int (D) no
Answer: D
Solution: constructors do not have any return type, not even void for more information click here
38.Method over-riding can be prevented by using final as a modifier at ...............
(A) the start of the class.
(B) the start of method declaration.
(C) the start of derived class.
(D) the start of the method declaration in the derived class.
Answer: B
Explanation: When used at the start of a class, it prevents it from being extended or subclassed, as well as being overridden.
The final keyword is provided at the beginning of the method to avoid overriding.
39.Which of the following is a correct statement?
(A) Composition is a strong type of association between two classes with full ownership.
(B) Composition is a strong type of association between two classes with partial ownership.
(C) Composition is a weak type of association between two classes with partial ownership.
(D) Composition is a weak type of association between two classes with strong ownership.
Answer: A
Solution: It is called composition when one object contains another object and the contained object cannot exist without the container object.
It is powerful and has a complete owner relationship.
40. Which of the following is not a correct statement?
(A) Every class containing abstract method must be declared abstract.
(B) Abstract class can directly be initiated with ‘new’ operator.
(C) Abstract class can be initiated.
(D) Abstract class does not contain any definition of implementation.
Answer: B
Solution: An abstract class cannot be directly initiated with the new operator; Since an abstract class does not contain any implementation definition, it is impossible to create an abstract object.
41.Which of the following tag in HTML is used to surround information, such as signature of the person who created the page ?
(A) <body> </body> (B) <address> </address>
(C) <strong> </strong> (D) <em> </em>
Answer: B
Solution: The <address> tag specifies the author/owner of a document or article's contact information.
<body> tag defines the document's body.
<strong> defines important text eg: This is strong
<em> Renders as emphasized text eg: This is em
42.Java uses threads to enable the entire environment to be ................
(A) Symmetric (B) Asymmetric
(C) Synchronous (D) Asynchronous
Answer: D
Solution: Threads are used in Java to make the entire environment asynchronous. Asynchronous threading is pre-emptive, meaning that once a thread begins executing a job, it can stop in the middle, store the current state, and begin executing another task (context switching) based on priority and other threading criteria.
43.An Operating System (OS) crashes on the average once in 30 days, that is, the Mean Time Between Failures (MTBF) = 30 days. When this happens, it takes 10 minutes to recover the OS, that is, the Mean Time To Repair (MTTR) = 10 minutes. The availability of the OS with these reliability figures is approximately :
(A) 96.97% (B) 97.97%
(C) 99.009% (D) 99.97%
Answer: D
Solution: According to the question system crashes once in 30 days (= 30x24x60 minutes) and need 10 minutes to get repaired.
fraction of time system is not available = 1030∗24∗60∗100 = 0.023%
Availability =100-0.023 = 99.97%
44.Match each software lifecycle model in List – I to its description in List – II:
List – I List – II
I. Code-and-Fix a. Assess risks at each step; do most critical
action first.
II. Evolutionary prototyping b. Build an initial small requirement specifications,
code it, then “evolve” the specifications and code
as needed.
III. Spiral c. Build initial requirement specification for
several releases, then design-and-code in
sequence
IV. Staged Delivery d. Standard phases (requirements, design,
code, test) in order
V. Waterfall e. Write some code, debug it, repeat
(i.e. ad-hoc)
Codes :
I II III IV V
(A) e b a c d
(B) e c a b d
(C) d a b c e
(D) c e a b d
Answer: A
Solution: Write some code, debug it, and repeat under the Code-and-Fix methodology (i.e. ad-hoc)
Build an initial tiny requirement definition, code it, then "develop" the specs and code as needed under the evolutionary prototyping paradigm.
Assess risks at each level in the Spiral model; take the most crucial action first.
Build initial requirement specifications for numerous releases using the Staged Delivery paradigm, then design and code in order.
Standard phases (requirements, design, code, and test) are used in the Waterfall methodology.
45.Match each software term in List – I to its description in List – II:
List – I List – II
I. Wizards a. Forms that provide structure for a document
II. Templates b. A series of commands grouped into a
single command
III. Macro c. A single program that incorporates most
commonly used tools
IV. Integrated Software d. Step-by-step guides in application software
V. Software Suite e. Bundled group of software programs
Codes :
I II III IV V
(A) d a b c e
(B) b a d c e
(C) d e b a c
(D) e c b a d
Answer: A
Solution: Wizards are step-by-step instructions in software applications.
Templates are forms that provide a document structure.
A macro is a collection of commands that are combined into a single command.
Integrated software is a single program that contains the most regularly used tools in one package.
A software suite is a collection of related programs.
46.The ISO quality assurance standard that applies to software Engineering is
(A) ISO 9000 : 2004 (B) ISO 9001 : 2000
(C) ISO 9002 : 2001 (D) ISO 9003 : 2004
Answer: B
Solution: ISO 9001: 2000 is the ISO quality assurance standard that applies to software engineering. It lays out the specifications for a quality management system.
47.Which of the following are external qualities of a software product ?
(A) Maintainability, reusability, portability, efficiency, correctness.
(B) Correctness, reliability, robustness, efficiency, usability.
(C) Portability, interoperability, maintainability, reusability.
(D) Robustness, efficiency, reliability, maintainability, reusability.
Answer: B
Solution: External qualities of a software product:
- Efficiency
- Usability
- Correctness
- Reliability
- Robustness
Internal qualities of a software product:
- Interoperability
- Maintainability
- Reusability
- Portability
48.Which of the following is/are CORRECT statement(s) about version and release ?
I. A version is an instance of a system, which is functionally identical but nonfunctionally distinct from other instances of a system.
II. A version is an instance of a system, which is functionally distinct in some way from other system instances.
III. A release is an instance of a system, which is distributed to users outside of the development team.
IV. A release is an instance of a system, which is functionally identical but onfunctionally distinct from other instances of a system.
(A) I and III (B) II and IV
(C) I and IV(D) II and III
Answer: D
Solution: A version is a system instance that is functionally distinct from other system instances in some way.
A release is a version of a system that is made available to those outside of the development team.
49.The Unix Operating System Kernel maintains two key data structures related to processes, the process table and the user structure. Now, consider the following two statements:
I. The process table is resident all the time and contain information needed for all processes, even those that are not currently in memory.
II. The user structure is swapped or paged out when its associated process is not in memory, in order not to waste memory on information that is not needed.
Which of the following options is correct with reference to above statements ?
(A) Only (I) is correct.
(B) Only (II) is correct.
(C) Both (I) and (II) are correct.
(D) Both (I) and (II) are wrong.
Answer: C
Solution: The process table is always present and contains data for all processes, including those that are not currently in memory. This is correct; the kernel saves all PCBs (Process Control Block)
50. Consider a system which have ‘n’ number of processes and ‘m’ number of resource types. The time complexity of the safety algorithm, which checks whether a system is in safe state or not, is of the order of:
(A) O(mn) (B) O(m2n2)
(C) O(m2n) (D) O(mn2)
Answer: D
Solution: The complexity of the Bankers algorithm will be O(m*n 2) in a system with 'n′ processes and'm′ resource categories.
The Bankers algorithm is incapable of allocating resources to numerous processes at once. The resource allocation graph technique is only O(n 2) in complexity.





