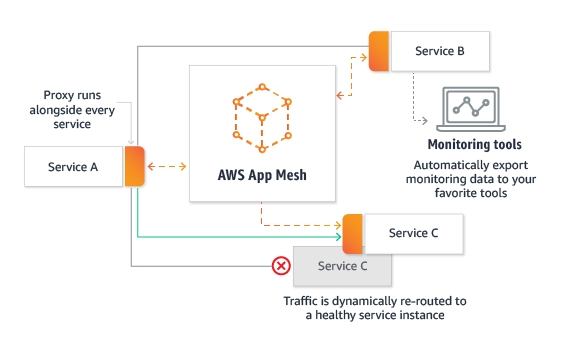
Components of App Mesh
Following are the main components of App Mesh:
-
Service mesh
A service mesh is a boundary for network traffic between the services inbuilt in it. You can create virtual services after creating your service mesh, virtual routers, and virtual nodes, and it handles different routes to distribute traffic between the applications in your mesh.
-
Virtual services
A virtual service is a method of an essential service provided by a virtual node, directly or indirectly, using a virtual router. Two virtual services represent the two critical services in the illustration. The key is the names of the virtual services. When a virtual service and a genuine service have the same name, multiple services can communicate using the same names before App Mesh was implemented.
-
Virtual nodes
A virtual node behaves as a logical pointer to a recognizable service, such as the Kubernetes and Amazon ECS. At least you should have one virtual node for each virtual service.
-
Virtual routers and routes
Virtual routers operate traffic for one or more virtual services within your mesh. A route is connected with a virtual router. The route matches the virtual router's requests and distributes traffic to its associated virtual nodes.
-
Virtual Gateways
A virtual gateway allows resources located outside your mesh to communicate with resources within your mesh. The virtual gateway is an Envoy proxy running in an Amazon ECS service, a Kubernetes service, or an Amazon EC2 instance.
We will now discuss the security in AWS Mesh.
Security in AWS App Mesh
AWS places the highest priority on cloud security. You have access to a data center and network architecture designed to meet the needs of the most security-conscious organizations as an AWS customer.
Security of the cloud
AWS is in charge of safeguarding the infrastructure that supports AWS services in the AWS Cloud. AWS also offers services that can be used securely. Third-party auditors regularly test and verify our security effectiveness as part of the AWS compliance programs.
Security in the cloud
- The AWS service you use determines your liability. You are also in charge of other elements, such as.
- The sensitivity of your data, the needs of your firm, and any applicable laws and regulations.
- The App Mesh data plane's security setup includes the composition of security groups that allow traffic to transit between services within your VPC.
- App Mesh is responsible for configuring your computational resources.
Transport Layer Security
Transport Layer Security (TLS) encrypts communication between Envoy proxies deployed on computing resources represented by mesh endpoints in App Mesh, such as Virtual nodes and Virtual gateways. TLS is negotiated and terminated by the proxy. When the proxy is used in conjunction with an application, your application code is not in charge of negotiating a TLS session. TLS is negotiated on your application's behalf by the proxy.
You can provide the TLS certificate to the proxy using App Mesh in the following ways:
- AWS Certificate Manager (ACM) private certificate issued by an AWS Certificate Manager Private Certificate Authority (ACM PCA).
- Your certificate authority issued a certificate and stored it on the local file system of a virtual node (CA).
Mutual TLS Authentication
Mutual TLS (Transport Layer Security) authentication is a TLS option that provides two-way peer authentication. Mutual TLS authentication adds an extra layer of security to TLS and allows your services to validate the client making the connection.
- During the session negotiation process, the client in the client-server relationship also provides an X.509 certificate. The server uses this certificate to identify and authenticate the client.
- This process assists in determining whether the certificate was issued by a trusted certificate authority (CA) and whether the certificate is valid. It also uses the certificate's Subject Alternative Name (SAN) to identify the client.
-
You can enable mutual TLS authentication for all AWS App Mesh protocols. They are TCP, HTTP/1.1, HTTP/2, gRPC, and SOAP.
For mutual TLS authentication, AWS App Mesh supports two certificate sources. Client certificates for a TLS Client Policy and server validation for a listener TLS configuration can be obtained from the following sources:
- File System– Certificates from the running Envoy proxy's local file system. To distribute certificates to Envoy, you must provide the App Mesh API with file paths for the certificate chain and private key.
- Secret Discovery Service (SDS) for Envoy – Bring your sidecars that implement SDS and allow certificates to be sent to Envoy. SPIFFE Runtime Environment is one of them (SPIRE).
Now, let us see resilience in AWS App Mesh.
Resilience in AWS App Mesh
AWS Regions and Availability Zones form the foundation of the AWS global infrastructure. AWS Regions offer several physically separated and isolated Availability Zones linked by low-latency, high-throughput, and highly redundant networking. You can use Availability Zones to design and run applications and databases seamlessly failover between Availability Zones. Availability Zones provide greater availability, fault tolerance, and scalability than traditional single or multiple data center infrastructures.
App Mesh distributes its control plane instances across multiple Availability Zones to ensure high availability. App Mesh detects and replaces unhealthy control plane instances and provides automated version upgrades and patching.
We will close the article now with faqs since you get some idea of the AWS App Mesh.
Frequently asked questions
What is AWS APP mesh used?
AWS App Mesh is a utility mesh that gives application-level networking to make it comfortable for your services to interact with each other across multiple types of computing infrastructure. App Mesh gives end-to-end visibility and high availability for your applications.
How does APP meshwork?
App Mesh manages and sets a service mesh for your services. You run the open-source Envoy proxy with each service side-by-side, and App Mesh configures the proxy to operate all communications into and out of each container.
What is Mesh API?
Mesh API securely transfers healthcare data between organizations using the Message Exchange for Social Care and Health (MESH), a Spine component. You interact with MESH via a virtual mailbox, only accessible to your organization, by making calls to this API from your application.
What is service mesh in Mulesoft?
A service mesh in a Mulesoft is a software architectural pattern utilized for microservices deployments with a sidecar proxy to enable fast, secure, and reliable service-to-service communications.
What capabilities does a service mesh allow?
The mesh allows critical capabilities, including load balancing and support for the circuit breaker pattern, encryption, traceability, observability, service discovery, authorization, and authentication. It is generally implemented by providing a proxy instance, called a sidecar, for each service instance.
Conclusion
In this article, we have extensively discussed the AWS App Mesh, How to get started with App Mesh. We also learned various components of it.
After reading about the AWS App Mesh, are you not feeling excited to read/explore more articles on the topic of AWS? Don't worry; Coding Ninjas has you covered. To learn, see Introduction to AWS, AWS Features, Managing Devices with AWS IoT, AWS Amplify, and AWS Cost & Usage Report.
Refer to our Guided Path on Coding Ninjas Studio to upskill yourself in Data Structures and Algorithms, Competitive Programming, JavaScript, System Design, and many more! If you want to test your competency in coding, you may check out the mock test series and participate in the contests hosted on Coding Ninjas Studio! But if you have just started your learning process and are looking for questions asked by tech giants like Amazon, Microsoft, Uber, etc., you must look at the problems, interview experiences, and interview bundle for placement preparations.
Nevertheless, you may consider our paid courses to give your career an edge over others!
Do upvote our blogs if you find them helpful and engaging!
Happy Learning!