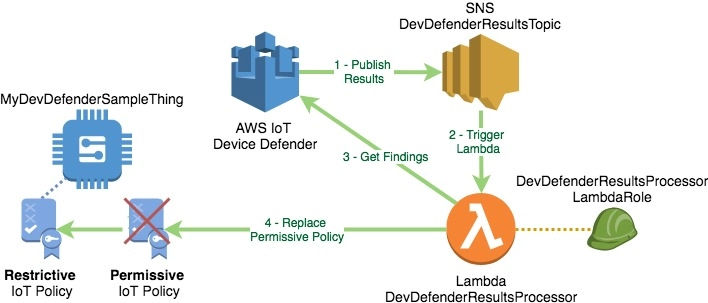
Setup and Working of AWS IOT Device Defender Detect
We establish security profiles, which mainly define the expected device behaviors and then assign them to our entire fleet of devices. AWS IoT Device Defender Detect uses the established security profiles to detect any anomalies and deliver alarms via Amazon CloudWatch metrics if any abnormal behaviour is detected.
Source: aws.amazon.com
Uses
-
Assess the attack area:-
AWS IoT Device Defender Detect can be used to assess the attack surface of your devices. For example, devices with service ports that are frequently the target of attack operations can be identified. We can reduce the attack surface (by reducing unneeded network services) or do additional assessments to discover security flaws when AWS IoT Device Defender Detect alerts you to it.
-
Identify unusual device behavior and possible security causes:-
Unexpected device behavioural data (the count of open ports, number of connections, an unusual available port, connections to unfamiliar IP addresses) could indicate a security breach using AWS IoT Device Defender Detect. A greater proportion of TCP connections, for example, could mean that a device is being used in a DDoS attack.
-
Identify a device that is wrongly set up:-
An increase in the number or length of messages sent from a device to your account could indicate that the device is wrongly set up. A device like this could raise your per-message charges. Similarly, a device with many authorization failures may necessitate a policy change.
Monitoring the behavior of unregistered devices
AWS IoT Device Defender Detect can be used to detect abnormal behavior of devices that are not registered in the IoT registry. We can create security profiles for the devices. A security profile sets the steps to execute when an anomaly is discovered and provides a set of expected behaviors for devices in our account. Security profiles should be tied to the most particular targets to provide us granular control over which devices are evaluated against that profile.
Concepts
Metric
AWS IoT Device Defender Detects analyses metrics to spot unusual device activities. It compares a metric's reported value to the value we provide. These figures are derived from two sources: cloud-based and device-based data.
Security Profile
A Security Profile determines which actions should be taken when an anomaly is discovered for a group of devices (an item group) or for all devices in your account. We can create a Security Profile and link it with a collection of devices using the AWS IoT console or API commands. AWS IoT Device Defender Detect begins collecting security-related data and employs the behaviors set in the Security Profile to identify anomalies in device behavior.
Behavior
A behavior instructs AWS IoT Device Defender Detect when a device is acting strangely. An alarm is triggered when a device activity does not match a behavior. The predicted device behavior is described by a metric and an absolute-value or statistical threshold with an operator (for example, less than or equal to, larger than or equal to). A metric plus an ML Detect configuration makes up an ML Detect behavior, which instructs an ML model to understand the normal behavior of devices.
ML model
A machine learning model is built to track each behavior that a consumer configures. The model is trained on metric data patterns from specific device groups and generates three anomaly confidence levels for metric-based behavior (high, medium, and low). It infers anomalies at the device level based on imported metric data. One ML model is generated in the context of ML Detect to evaluate one metric-based behavior.
Alarm
Whenever an anomaly is discovered, an SNS notification can be used to send an alarm. The AWS IoT console also shows an alert notice, along with details about the alarm and history of alarms for the device. When a monitored device ceases exhibiting abnormal behavior or stops notifying for an extended time, an alarm is also sent.
Frequently Asked Questions
What is AWS IoT Device Defender Detect?
AWS IoT Device Defender is a security service that lets you check your devices' configurations, monitor connected devices for unusual behavior, and reduce security concerns.
List some of the uses of AWS IoT Device Defender Detect.
AWS IoT Device Defender Detect can be used to assess the attack surface of your devices, identify unusual device behavior and possible security causes, or identify a device that is wrongly set up.
What is a Security Profile?
A Security Profile determines which actions should be taken when an anomaly is discovered for a group of devices (an item group) or all devices in your account. We can create a Security Profile and link it with a collection of devices using the AWS IoT console or API commands.
What is Behavior in AWS IoT device defender?
A behavior instructs AWS IoT Device Defender Detect when a device is acting strangely. An alarm is triggered when a device activity does not match a behavior.
How can we monitor the behavior of unregistered devices?
AWS IoT Device Defender Detect can be used to detect abnormal behavior of devices that are not registered in the IoT registry. You can create security profiles for the devices. A security profile sets the steps to execute when an anomaly is discovered and provides a set of expected behaviors for devices in your account.
Conclusion
In this article, we studied in detail AWS IoT Device Defender Detect. We saw its uses and key concepts. We hope that this blog has helped you enhance your knowledge of the AWS IoT Device Defender Detect. Do upvote our blog to help other ninjas grow.
After reading about the AWS X-rayIoT Device Defender, are you not feeling excited to read/explore more articles on AWS? Don’t worry; Coding Ninjas has you covered. To learn, see Important AWS Interview Questions, AWS EC2 Auto Scaling, AWS CloudHSM, AWS License Manager, and AWS DeepRacer Part-1.
Check out this article - Components Of IOT
Refer to our Guided Path on Coding Ninjas Studio to upskill yourself in Data Structures and Algorithms, Competitive Programming, JavaScript, System Design, and many more! If you want to test your competency in coding, you may check out the mock test series and participate in the contests hosted on Coding Ninjas Studio! But if you have just started your learning process and are looking for questions asked by tech giants like Amazon, Microsoft, Uber, etc; you must look at the problems, interview experiences, and interview bundle for placement preparations.
Nevertheless, you may consider our paid courses to give your career an edge over others!
Do upvote our blogs if you find them helpful and engaging!
Happy Learning!