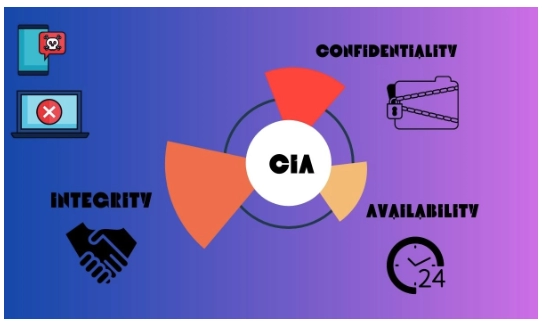
Confidentiality
Here are some points to know about confidentiality:
-
It involves protecting your information from unapproved access or sharing.
-
It ensures that sensitive data only reaches authorized persons.
-
You can have it using password encryption, authentication, and biometrics.
-
Confidential information may include trade secrets, personal information, and financial data.
-
Failure to ensure confidentiality can result in financial loss, cybersecurity incidents etc.
-
You have to balance it with the need for information sharing.
-
It's an ongoing process involving regular reviews and updates of security policies.
- A real-life example can be a lawyer keeping his client's data confidential to protect his legal rights. Similarly, a journalist protects the identities of his sources in a sensitive news story.
Integrity
Here are some points to know about integrity:
-
It means having data accuracy throughout its lifecycle.
-
You can prevent unauthorized deletion, corruption of data etc., by ensuring integrity.
-
You can use cryptographic techniques such as hashing or digital signatures.
-
Maintaining it in the network, servers, and storage devices is necessary.
-
Examples of data needing integrity protection are financial, medical, and scientific data.
- A real-life example is how the voting system maintains the integrity of ballots to prevent election fraud. Similarly, a bank ensures that financial transactions are accurate for its customers.
Availability
Here are some points to know about availability:
-
It means ensuring that data and system resources are available.
-
It is useful when authorised parties want it.
-
Availability involves reducing disturbances. For example, mission-critical services and financial transactions should have availability.
-
You have it using backups and disaster recovery plans.
-
Network and system monitoring tools help to ensure presence by detecting and answering issues.
-
A real-life example is how a public library ensures the availability of its resources by staying open during regular hours. They provide access to its books and digital collections. Similarly, a power company ensures the availability of electricity to its customers. They give a dependable power grid and respond quickly to outages.
- Your network may become inaccessible due to attacks such as DoS or DDoS. For example, a DDoS attack in 2018 on GitHub.
Examples of CIA Traid
Now, we will talk about a few examples of the CIA Triad in practice:
-
A bank ensures that only authorized employees can access customer account data.
-
A hospital ensures patient records are only available to staff members with permission.
-
A software system regularly checks its system. System repair damaged files.
-
A government agency restricts access to some documents to approved persons only.
-
A social media platform monitor data. They ensure it does not compromise user privacy.
- A cloud storage provider replicates data across multiple servers. They ensure availability even in a server failure.
History of the CIA Triad
The history of the CIA triad can be traced back to the early days of information security and computing. The origins of the CIA triad are associated with the US military, where the principles of confidentiality, integrity, and availability were considered to be crucial components of securing classified information and data. However, the formalization of the CIA triad as a model in information security is often credited to early computer security frameworks developed in the 1970s and 1980s.
The next section will tell about the different reasons for using the CIA triad for protecting your crucial data.
Why Should You Use the CIA Triad?
The CIA triad offers many significant benefits that help you protect sensitive information systems and networks. Following are some reasons why you should use the CIA triad:-
-
Comprehensive Approach: The CIA triad uses 3 core principles of information security which ensures a well-rounded approach to data protection.
-
Risk Management: By applying the CIA triad's principles, you can identify potential security risks and vulnerabilities and deal with them accordingly.
-
Regulatory Compliance: Many laws and regulations require organizations to protect sensitive information. The CIA triad helps organizations meet these compliance requirements.
-
Data Protection: The triad ensures that sensitive data is adequately protected from unauthorized access and manipulation, reducing the risk of data breaches and leaks.
Now we will discuss some advantages of the CIA triad.
Advantages of CIA Triad
Here are some pros of using the CIA triad:
-
It is a complete structure for analyzing danger. It deals with security risks.
-
It helps to prioritize security efforts to focus on critical areas.
-
It gives a clear structure for designing and having security controls.
-
It ensures security measures are balanced. It also ensures they are not overly focused on one place.
-
It is the basis for regular improvement and updating of security measures.
-
It first identifies. Then it prioritizes critical data.
- It mainly creates a security awareness among people.
Overall, the CIA triad is widely recognized as an effective way to address security dangers and protect data. But there are some limitations also.
Limitations of CIA Triad
Here are some cons of the CIA Triad:
-
It can sometimes be resource-demanding and time-consuming.
-
It may not resolve the human factor in cybersecurity. An example can be insider threats.
-
It may not be suitable for new types of cyber-attacks.
-
It may not be enough for businesses with complex supply chains and third-party relationships.
- The principles of the CIA Triad can sometimes dispute with each other.
Models Related to the CIA Triad
Here are some other models and structures related to the CIA triad:
-
Donn Parker's Hexad: It extends the CIA triad. It has authentication, non-repudiation, and accountability.
-
AIC triad: It expands the CIA triad. It has authenticity, integrity, and confidentiality.
-
McCumber Cube: It is a model with confidentiality, integrity, availability, privacy, processing integrity, and legal compliance.
-
STRIDE: It is a threat modelling skeleton that classifies risks. Fraud with user identity, Tampering with data, Repudiation, Information disclosure, Denial of service, and Elevated privilege.
-
NIST Cybersecurity Framework: It includes five functions - Identity, Protect, Detect, Respond, and Recover. It is to manage and reduce cybersecurity risk.
-
CIS Controls: A set of 20 critical security controls which help organizations prioritize and focus their cybersecurity efforts.
-
OWASP Top Ten: It has the top ten most critical web application security risks.
Also read - active and passive attacks
Frequently Asked Questions
What is the CIA Triad?
CIA triad stands for Confidentiality, Integrity, and Availability. It is a fundamental model in information security that represents three core principles or goals for protecting information and data. All of its components are essential for maintaining the security of information systems.
What does the CIA triad include?
The three core components of the CIA triad are Confidentiality, Integrity, and Availability. They are crucial for making information systems reliable and secure from various threats and risks. Organizations use these principles to design security measures and assess risks.
What is the CIA triad in forensics?
CIA triad in forensics is a set of core principles of information security applied during the investigation and analysis of digital evidence. It puts emphasis on maintaining the confidentiality, integrity, and availability of digital evidence throughout the forensic process.
Conclusion
This article explored the CIA triad's values, definition, and advantages. The article also includes practical examples of attacks affecting the CIA triad in real-world cases. It would help if you referred to other cybersecurity resources and materials. They will amplify your learning of the CIA triad.
Refer to our guided paths on Coding Ninjas Studio to learn more about DBMS, Data Structure, Javascript, Python, etc. Enroll in our courses, refer to the mock test, and problems look at the interview experiences and interview bundle for placement preparations.