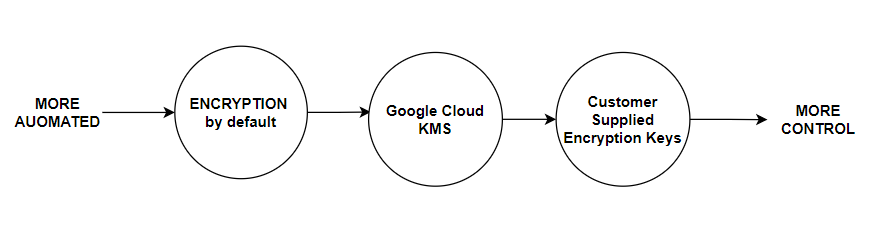
Integration with Google cloud services🔧
Other Google cloud services that deal with encryption key authentication, such Cloud Identity and Access Management, connect to Cloud KMS. Together, the services regulate the security policies and permissions that govern key access and KeyRing access. When dealing with compliance standards and regulations, Cloud KMS also interfaces with Cloud Audit Logging, which keeps track of administrative access and usage activity.
Users can choose when the encryption keys cycle automatically or manually using options for automated and manual key rotation. Either the command-line interface or the API is used for this. Millions of encryption keys with an arbitrary number of key versions can be supported by Google Cloud KMS. It can be employed in a single geographic cloud data center or as a distributed service.
Create encryption keys with Cloud KMS🔑
A random string of bits created especially to jumble and unscramble data is often used as an encryption key. Algorithms used to construct encryption keys make sure that each key is distinct and unpredictable. The encryption code is more difficult to decipher the longer the key is created in this manner.
Now, we will require a Cloud KMS key, which is a piece of a key ring, to encrypt and decrypt material.
Make a key called “demonstration” and a key ring called “demo.” See the object hierarchy overview for further details on these objects and their connections.
gcloud kms keyrings create "demo" \
--location "global"
gcloud kms keys create "demonstration" \
--location "global" \
--keyring "demo" \
--purpose "encryption"
Encrypt and decrypt data with a symmetric key🔑
Install the most recent version of Google Cloud CLI or upgrade to it before using Cloud KMS on the command line.
ENCRYPTION
gcloud kms encrypt \
--key key \
--keyring key-ring \
--location location \
--plaintext-file file-with-data-to-encrypt \
--ciphertext-file file-to-store-encrypted-data
DECRYPTION
gcloud kms decrypt \
--key key \
--keyring key-ring \
--location location \
--ciphertext-file file-path-with-encrypted-data \
--plaintext-file file-path-to-store-plaintext
Replace the key with the name of the encryption key that will be used. Substitute the name of the key ring where the key is situated for "key-ring." Replace location with the key ring's Cloud KMS location. Replace the local file paths for reading the plaintext data and saving the encrypted output with file-with-data-to-encrypt and file-to-store-encrypted-data, respectively.
Encrypt and decrypt data with an asymmetric key🔑
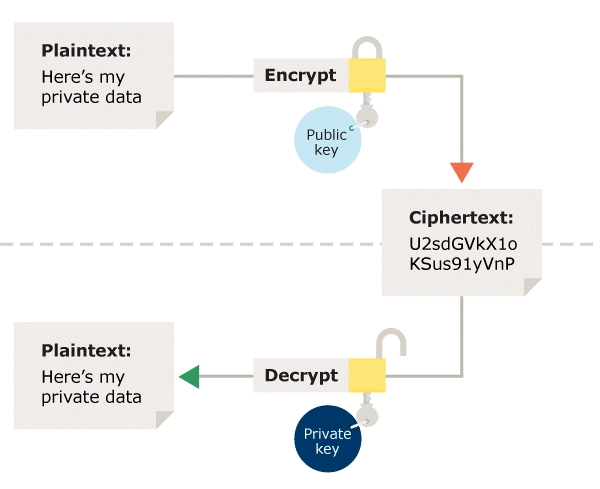
Now we will learn, how to generate and use an RSA key for asymmetric encryption. The asymmetric key's private key is used for decryption while the public key is used for asymmetric encryption. Decrypting ciphertext that was encrypted with the public key is possible with the help of the Cloud Key Management Service's capabilities. The private key cannot be accessed directly through Cloud KMS.
ENCRYPTION
openssl pkeyutl -in cleartext-data-input-file \
-encrypt \
-pubin \
-inkey public-key-path \
-pkeyopt rsa_padding_mode:oaep \
-pkeyopt rsa_oaep_md:sha256 \
-pkeyopt rsa_mgf1_md:sha256 \
> encrypted-data-output-file
Replace the location and file name to encrypt with cleartext-data-input-file.
Replace public-key-path with the location and name of the public key file that you downloaded.
The path and file name to save the encrypted data should be substituted for encrypted-data-output-file.
DECRYPTION
gcloud kms asymmetric-decrypt \
--version key-version \
--key key \
--keyring key-ring \
--location location \
--ciphertext-file file-path-with-encrypted-data \
--plaintext-file file-path-to-store-plaintext
Change key-version to the actual key version, or omit the —version parameter to let the system figure it out for you. Substitute the key with the name of the decryption key. Substitute the name of the key ring where the key will be kept for “key-ring” instead. Replace location with the key ring's Cloud KMS location. Replace the local file paths for reading the encrypted data and storing the decrypted output with file-path-with-encrypted-data and file-path-to-store-plaintext, respectively.
Creating symmetric encryption keys↕️
For your new key, make a key ring by following these instructions. Instead, you can make a key to use with an existing key ring.
-
Navigate to the console's Key Management page.
- Head over to the Key Management page.
- Then select Create key ring.
- In the field labeled "Key ring name," type the name you wish for your key ring.
- Choose a place like "us-east1" from the “Key-ring” location dropdown menu.
- Press Create.
To produce a symmetric encryption key on the designated key ring and location, follow these instructions.
-
Navigate to the console's Key Management page.
- To create a key for a specific key ring, click its name.
- Choose to Create key.
- Select Generated key from the type of key you want to create.
- Enter the name of your key in the Key name area.
- Select Software from the Protection level menu by clicking it.
- Symmetric encrypt/decrypt can be chosen by selecting the Purpose dropdown menu.
- Accept the default settings for Starting on and Rotation period.
- Press Create.
Set a key rotation period and starting time
Before you press the Create button while designing your key, but before choosing a different rotation duration and starting time:
- Select a value for the rotation period by clicking the Rotation period dropdown.
- Choose a date for the following cycle after clicking the date in the Starting the field.
Cloud External Key Manager🧑💼
With Cloud EKM, you may secure Google Cloud data using keys that you control through an approved external key management partner. By directly accessing the Cloud Key Management Service API or using one of the available CMEK integration services, you may secure data while it is in transit.
Several advantages of cloud EKM include:
- Key provenance: The distribution and location of your externally maintained keys are under your control. Keys that are maintained outside of Google Cloud are never cached or kept there. Instead, each request is communicated to the external key management partner directly through Cloud EKM.
- Access management: You control who has access to your externally managed keys. Before using an externally managed key to encrypt or decrypt data in Google Cloud, you must provide the project access to the key. This access is always revocable by you.
- Centralized key management: Regardless of whether the data they protect is stored on your premises or in the cloud, you can manage your keys and access policies from a single location and user interface.
Importing a key into Cloud KMS🗝️
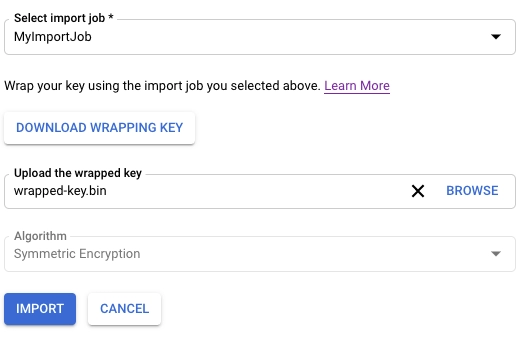
The methodology used to construct the wrapping key that safeguards imported keys while they travel from your local system to the intended Google Cloud project is defined by the import method. A 4096-bit or a 3072-bit RSA key is available. It is advised to use the 3072-bit wrapper key unless you have unique requirements.
-
Navigate to the console's Key Management page.
- To select the desired key ring, click its name.
- Select either the Software or the HSM protection level. Apply the same level of protection that you did for the target key.
- Create an import job by clicking.
- Enter the name of your import task in the Name column.
- Choose either 3072-bit RSA or 4096-bit RSA as the import method from the Import method option.
- Press Create.
Retrieving a public key🔐

Using the Cloud Key Management Service API, Google Cloud CLI, and the Google Cloud console, you can access the public key component of an asymmetric key version.
-
Navigate to the console's Key Management page.
- Click the name of the key-ring holding an asymmetric key to retrieve the public key for that key.
- Select the key whose public key you want to retrieve by clicking on its name.
- Click View more vert on the row corresponding to the key version for which you wish to retrieve the public key.
- Press Get Public Key.
- The public key is shown in the prompt. You can copy the public key to your clipboard. To download the public key, click Download.
Destroying and restoring key versions🔃

This article demonstrates how to plan for the eventual deletion of a key version. When a key version is destroyed, the key material is erased but not other information like the key name or key version number. Data that was encrypted with a key cannot be decrypted after the key has been destroyed.
-
Navigate to the console's Key Management page
- To schedule the key version you want to destroy for destruction, click the name of the “key-ring” it is on.
- To set a key version for destruction, click the desired key.
- The key version that you want to indicate for deletion should have a checkmark next to it.
- In the header, select Destroy.
- Enter the key name in the confirmation box, then click Schedule Destruction.
Frequently Asked Questions❓
What is a cloud key management service?
You can perform cryptographic operations and create, import, and maintain cryptographic keys using the Cloud Key Management Service, a centralized cloud service.
Why do we need a KMS key?
You can encrypt little data bits with your KMS keys (up to 4096 bytes). However, the data keys that encrypt your data outside of AWS KMS are often generated, encrypted, and decrypted using KMS keys. Data keys may encrypt data of any size and format, including streamed data, unlike KMS keys.
How does Google KMS work?
If you need to use keys that you create yourself, Cloud Key Management Service enables you to import your cryptographic keys. You have the option to use Cloud KMS-generated keys with other Google Cloud services. Customer-managed encryption keys are the name for such keys (CMEK).
What is a key management server?
To manage the whole lifecycle of cryptographic keys and safeguard them from theft or unauthorized use, key management servers (KMS) are employed. The development, use, storage, archival, and destruction of encryption keys are ultimately under the control of KMS systems and other key management technology.
What is a private key?
The private key is utilized for encryption and digital signatures in public key cryptography.
Conclusion✉️
This article covers everything you need about Google Cloud Key Management Service. Still have more questions; Here are some articles and courses for rescue:
Refer to our guided paths on Coding Ninjas Studio to learn more about DSA, Competitive Programming, JavaScript, System Design, etc. Enroll in our courses and refer to the mock test and problems available. Take a look at the interview experiences and interview bundle for placement preparations.
Do upvote our blog to help other ninjas grow.
Happy Learning!
 .
.