Features of Hash Functions
The Hash function in cryptography is an algorithm that receives any amount of data input and produces a constant length encrypted text output. The encrypted output text is known as a hash value or hash.
Some of the essential features of Hash Functions are:-
1.) The hash function converts data of any arbitrary length to a fixed length. This process is known as hashing the data.
2.) Generally, the hash is smaller than the input data; hence hash functions are sometimes also known as compression functions.
3.) Since a hash is a miniature representation of extensive data, it is also known as a digest.
4.) Hash function having n-bit output is known as an n-bit hash function. Famous hash functions generate values between 160 and 512 bits.
5.) Hash functions are much faster than symmetric encryption in terms of computation.
Properties of Hash Functions
The hash function should have the following properties to be an effective cryptographic tool:-
Pre-Image Resistance
This property signifies that it should be computationally tough to reverse a hash function. It will protect against a hacker who only has a hash value and is trying to find the input.
Second Pre-Image Resistance
This property signifies that if the input and its hash are given, it should be tough to find a different input with the same hash. It protects against a hacker with an input value and its hash and wants to replace the original input value with another legitimate value.
Collision Resistance
This property signifies that it should be tougher to find two different inputs of arbitrary length that will result in the same hash value. This property is known as a collision-free hash function. This property will create many difficulties for a hacker to find two input values with the same hash.
Efficiency of Operation
The hash function should be designed to process input data quickly and with minimal computational resources. This means that even large volumes of data should be hashed without causing significant delays or requiring excessive processing power. Efficiency is crucial for real-time applications and systems where performance is critical.
Fixed Output Size
Regardless of the length or size of the input data, the hash function should always generate a hash of a fixed, predetermined size. For example, a hash function might produce a 256-bit hash output regardless of whether the input is a short text string or a large file. This fixed output size simplifies storage and comparison of hash values.
Deterministic
he hash function must be deterministic, meaning it will consistently produce the same hash value for identical input data. This property is essential for verifying data integrity and authenticity, as it ensures that the hash value will always match if the data has not been altered.
Fast Computation
The hash function should compute the hash value quickly to facilitate efficient processing. Fast computation is important for applications requiring rapid hashing of data, such as secure transactions, data indexing, and real-time security checks. A well-designed hash function balances speed with security to maintain overall system performance.
Each of these properties ensures that the hash function performs effectively and securely, making it a reliable tool for cryptographic applications.
Designing of Hashing Algorithm
A mathematical function that operates on two fixed-size data blocks to create a hash code lies at the core of hashing. Part of the hashing algorithm is this hash function.
Depending on the algorithm, the size of each data block varies. Block sizes generally range from 128 to 512 bits.
The hash function is demonstrated in the diagram below:
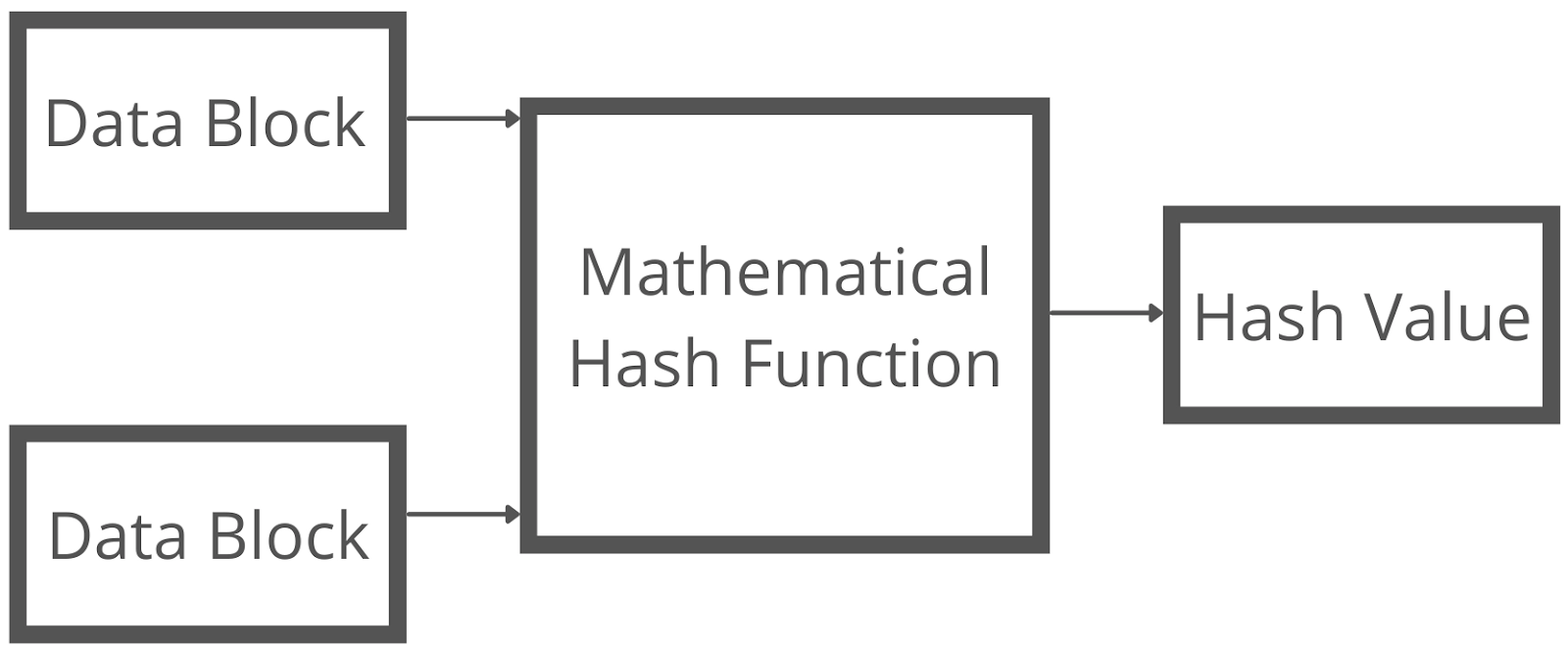
Like a block cipher, the hashing method uses rounds of the hash function, as mentioned earlier. Each round accepts a fixed-size input, which is usually a combination of the most recent message block and the previous round's output.
This procedure is repeated as many times as necessary to hash the entire message.
The following diagram shows a schematic of the hashing algorithm:
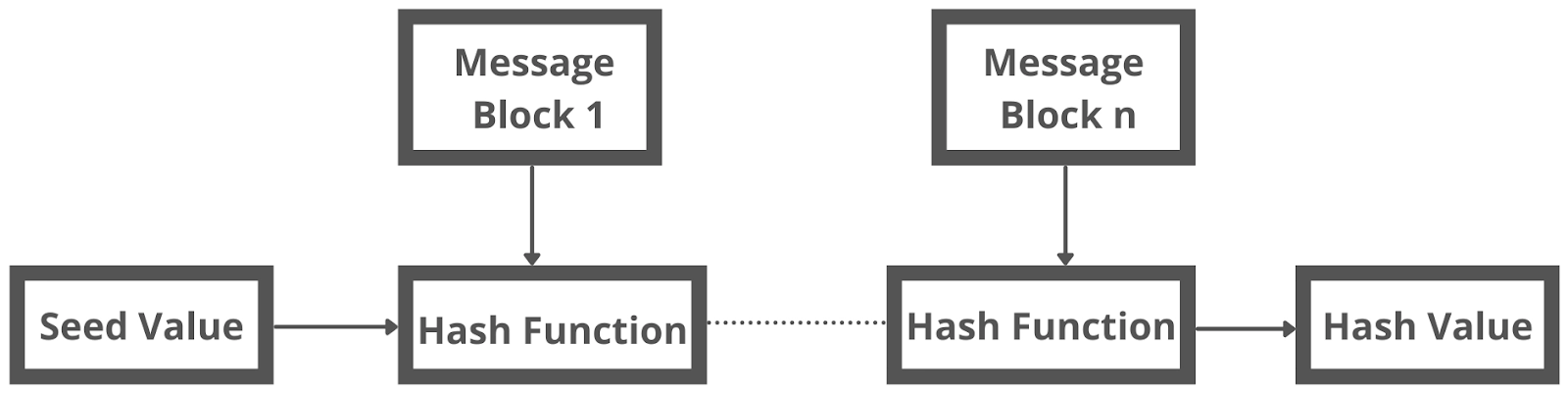
As a result, the first message block's hash value becomes an input to the second hash operation, whose output changes the result of the third operation, and so on. This is known as the Avalanche effect of hashing.
When two messages differ by even a single bit of data, the avalanche effect results in significantly differing hash values.
Realize the difference between a hash function and an algorithm correctly. The hash function generates a hash code by working on two blocks of fixed-length binary data.
The hashing algorithm specifies how the message will be broken up and how the results from previous message blocks will be linked together when using the hash function.
Famous Hash Functions
Some of the famous Hash Functions are:-
Message Digest (MD)
MD2, MD4, MD5, and MD6 are hash functions in the MD family. It's a hash function with a 128-bit length. MD5 was the most popular and commonly used hash function for many years. MD5 digests are widely used in the software industry to ensure the integrity of transferred files. MD5 was discovered to have collisions in 2004. Using a computer cluster, an analytical attack was reported to be successful in less than an hour. Because of the compromised MD5 resulting from the collision attack, it is no longer recommended for use.
Secure Hash Algorithm (SHA)
SHA-0, SHA-1, SHA-2, and SHA-3 are the four SHA algorithms that make up the SHA family. Despite being from the same family, they are structurally distinct. The National Institute of Standards and Technology (NIST) published the original version of SHA-0, a 160-bit hash function, in 1993. It had few flaws and did not gain widespread popularity. Later in 1995, SHA-1 was created to address SHA-0's reported faults. Of the available SHA hash functions, SHA-1 is the most extensively used. It's utilized in various popular applications and protocols, including the Secure Socket Layer (SSL) security protocol. The Keccak algorithm was chosen as the new SHA-3 standard by the NIST in October 2012. Keccak has several advantages, including efficient performance and strong assault resistance.
RIPEMD
RIPEMD is an acronym for RACE Integrity Primitives Evaluation Message Digest. The open research community created this family of hash functions known as the European hash functions family. RIPEMD, RIPEMD-128, and RIPEMD-160 are included in the collection. This method is also available in 256 and 320-bit versions. The original RIPEMD (128 bit) is built on the same design ideas as MD4 and has been found to be insecure. The 128-bit version of RIPEMD was released as a rapid repair to address vulnerabilities in the original RIPEMD. RIPEMD-160 is the most frequently used and enhanced form of the family. Compared to RIPEMD-128 and RIPEMD-160, the 256 and 320-bit variants lessen the likelihood of an accidental collision but do not provide improved levels of security.
Whirlpool
It is a 512-bit hash function. It's based on a modified version of the Advanced Encryption Standard (AES). Whirlpool is available in three versions: WHIRLPOOL-0, WHIRLPOOL-T, and WHIRLPOOL.
Applications of Hash Functions
Based on its cryptographic features, a hash function has two direct uses:
Password Storage
Password storage is protected using hash functions. Rather than saving passwords in plain text, most login processes save hash values of passwords in a file. A table of pairs in the format (user id, h(P)) makes up the Password file. Even if he accessed the password, an intruder could only read the hashes of passwords. He can't use the hash to log in, and he can't deduce the password from the hash value because the hash function has the property of pre-image resistance.
Data Integrity Check
The most general use of hash functions is to verify data integrity. Checksums on data files are generated with it. This application gives the user assurance that the data is correct. The integrity check aids the user in detecting any modifications to the original file. It does not, however, guarantee that the work is unique. Instead of changing file data, the hacker can change the entire file and compute a new hash before sending it to the recipient. This integrity testing tool is only helpful if the user is certain of the file's uniqueness.
Frequently Asked Questions
What is the cryptography hash function?
A cryptographic hash function is an algorithm that converts input data into a fixed-size hash value, ensuring data integrity and security.
What are two common hash functions?
Two common hash functions are SHA-256 and MD5, used for generating fixed-size hash values from varying input data.
What is MAC and hash function in cryptography?
A MAC (Message Authentication Code) verifies data integrity and authenticity, while a hash function produces a fixed-size hash value from input data.
What is the difference between hash function and cipher?
A hash function generates a fixed-size hash from input data, while a cipher encrypts data into unreadable form, requiring a key for decryption.
Conclusion
In this article, we have extensively discussed the Cryptography Hash Function, features of hash functions, and applications of the hash functions.
We hope that this blog has helped you enhance your knowledge regarding Cryptography. If you want to learn more, check out our articles on the Difference Between Cryptography And Cyber Security and Cyber Security







