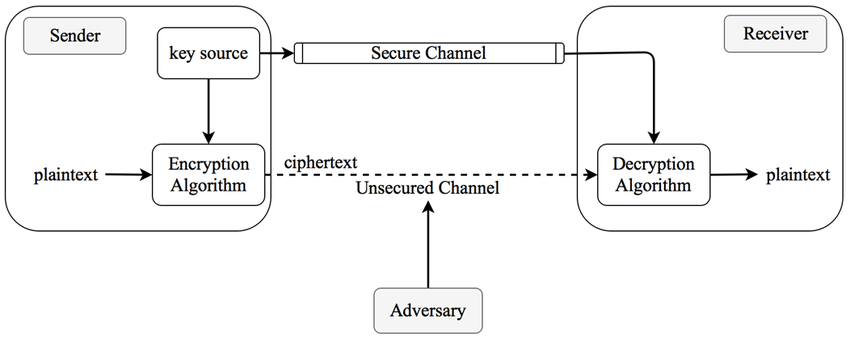
Components of Cryptosystem
The different components of a cryptosystem are as follows:
- Plaintext: It is the data that needs protection during transmission.
- Encryption Algorithm: This mathematical algorithm takes the Plaintext as input and produces an encoded plaintext form and an encryption key for that text.
- Ciphertext: This is the encoded form of the message. It is also known as the unreadable version.
- Decryption Algorithm: This mathematical algorithm takes the Ciphertext as its input and derives the original message using the decryption key.
- Encryption Key: This is a value known to the sender to encrypt the Plaintext into Ciphertext.
- Decryption Key: This is a value known to the receiver used to decrypt the Ciphertext to derive the Plaintext.
Types of Cryptosystems
Based on how encryption-decryption is performed, cryptosystems can be classified into two types:
- Symmetric Key Encryption
- Asymmetric Key Encryption
Symmetric Key Encryption
It is a type of encryption where only one key is used to encrypt and decrypt the Plaintext. This means the encryption key and decryption key are similar in Symmetric Key Encryption. The sender and receiver must communicate to share the key for the decryption process. Symmetric encryption is an older encryption method. It is faster and more efficient than asymmetric encryption because asymmetric encryption experiences performance issues due to data size and heavy CPU usage. Due to its better performance, Symmetric Encryption is used in encrypting large amounts of data like a database. Some examples of symmetric Encryption are Payment applications, card transactions, etc.
Some Symmetric Encryption algorithms are:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- RC4 (Rivest Cipher 4)
Asymmetric Key Encryption
This type of encryption uses two keys for encryption and decryption, respectively. The two keys, however, are mathematically related. The key used for encryption is a public key, and the key used for decryption is a private key. Asymmetric Key Encryption is also called public-key encryption. The public key is open to everyone, which means anyone can encrypt the data using it. But the private key is kept secret so that only authorized persons can access the encrypted data. Asymmetric encryption can be used to authenticate parties, verify data integrity, symmetric exchange keys, etc. If you see right now on your browser's address bar, you will see a lock icon. This lock icon means you are connected to a website that uses SSL/TLS certificates and the secure TLS protocol. This uses asymmetric key encryption to verify the identity of the server. Once the verification is done, the webserver switches to symmetric encryption for the rest of the session. Asymmetric encryption is more secure than symmetric encryption.
Some standard asymmetric encryption algorithms are:
Kerckhoff's Principle of Cryptosystem
In the 19th century, Auguste Kerckhoff, a Dutch cryptographer, gave some design principles for a good cryptosystem. Kerckhoff believed that a cryptographic system must be secure even when everything about the system is public knowledge, except the key.
The six design principles given by Kerckhoff are:
- The system must be indecipherable practically, if not mathematically.
- If it falls into enemy hands, it should not be a problem, i.e., there should be no secrecy.
- It must be possible to communicate and remember the key without using written notes, and correspondence must be able to change or modify it at will.
- The encoded information must be transmissible by even insecure channels such as the telegraph.
- The encryption system must be portable and operable by a single individual.
- The system must be easy to use, requiring minimal or no knowledge of a long set of operating rules, and it must not put the operator under mental strain.
Most of the above-stated rules have become outdated due to technological advancement and increased operating speed. However, the second hypothesis is critical in today's world and is known as Kerckoff's principle.
Also read - active and passive attacks
FAQs
-
Which Cryptosystem is faster, Symmetric or Asymmetric?
Symmetric Cryptosystem is faster than Asymmetric Cryptosystem.
-
Which Cryptosystem is more secure, Symmetric, or Asymmetric?
Asymmetric Cryptosystem is more secure than symmetric Cryptosystem.
-
RSA algorithm is the algorithm for Symmetric or Asymmetric Cryptosystem?
RSA algorithm is an asymmetric cryptosystem algorithm.
-
What are encryption keys and decryption keys?
The encryption key is used to encrypt the Plaintext, and the decryption key is used to decrypt the Ciphertext.
-
Which Cryptosystem is used to establish a secure connection with a third party?
Asymmetric Cryptosystem is used for this purpose.
Key Takeaways
In this article, we have extensively discussed the cryptosystem topic. We have discussed the components and the types of Cryptosystem. We have also discussed Kerckhoffs' principle.
We hope that this blog has helped you enhance your knowledge regarding cryptosystems and if you would like to learn more, check out our articles.
Recommended Readings:
- Difference between Public Key and Private Key
- Cyber attacks & their types
- Cyber Security and Cyber Crime
- Cyber Security Challenges
- Active and Passive Attacks
-
Active Attack and Passive Attack
Do upvote our blog to help other ninjas grow.
Happy Coding!