Introduction
The UGC NET, also known as the NTA-UGC-NET, is an examination used to determine eligibility for assistant professorships and Junior Research Fellowships at Indian universities and colleges. The National Testing Agency administers the exam on behalf of the University Grants Commission.
Now we will look at some of the questions that came in UGC NET Dec 2012 Paper II..
Questions with Solutions
1. Have a look at the circuit below. Y is at logical 'l' in a specific stable state. What are the potential A, B, and C values?
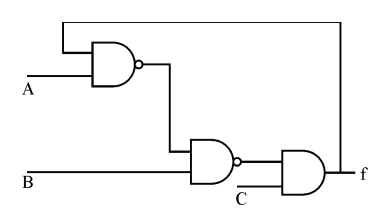
(A) A = 0, B = 0, C = 1
(B) A = 0, B = C = 1
(C) A = 1, B = C = 0
(D) A = B = 1, C = 1
Solution)
(A) A = 0, B = 0, C = 1 or (D) A = B = 1, C = 1
Explanation)
Assuming f is Y, the last AND gate must have both inputs set to 1 in order to reach the y=1 (stationary) state. As a result, C=1 (choice C is no longer an option), and for the other input to be 1, either B=0 or C=1 (which ensures output of 2nd NAND gate as 1)
or A=1 ensures that the output of the second NAND gate is 0 if the other input is also 1. Now, which is f, which might be 0 or 1, so leave it alone.
i.e. B=0 and A=1 or B=0 and C=1 option A)satisfy, as well as option D)
As a result, the answers should be A and D.
2. The worst-case time complexity of the AVL tree is better in comparison to the binary search tree for
(A) Search and Insert Operations
(B) Search and Delete Operations
(C) Insert and Delete Operations
(D) Search, Insert and Delete Operations
Solution) (D) Search, Insert and Delete Operations
Explanation) As previously stated, binary tree and BST search operations have a worst-case temporal complexity of O. (n). The AVL tree, on the other hand, has a worst-case time complexity of O. (logn). As a result, the best solution is (D).
3. The GSM network can be broken down into three major systems:
(A) SS, BSS, OSS
(B) BSS, BSC, MSC
(C) CELL, BSC, OSS
(D) SS, CELL, MSC
Solution) (A) SS, BSS, OSS
Explanation) The protocols for second-generation (2G) digital cellular networks used by mobile phones are referred to as GSM. GSM allows for up to 9.6 kbps data transfer and voice conversations. It uses the TDMA (time division multiple access) mechanism. The 850MHz, 900MHz, 1800MHz, and 1900MHz frequency bands are currently used by GSM networks.
4. The power set of the set {} is
(A) {}
(B) {, {}}
(C) {0}
(D) {0, , {}}
Solution) (B) {, {}}
Explanation) The set of all subsets of a set S, including the empty set and S itself, is called the power set of that set.
5. Find the number of disc transfers necessary with FCFS if the disc queue of I/O block requests is 98, 124, 37, 14, 65, and 67 if the disc head is initially situated at 32.
(A) 239
(B) 310
(C) 321
(D) 325
Solution) (C) 321
Explanation) (98-32) + (98-37) + (37-14) +(124-14) + (124-65) + (67-65)
= 66+61+23+110+59+2 =321
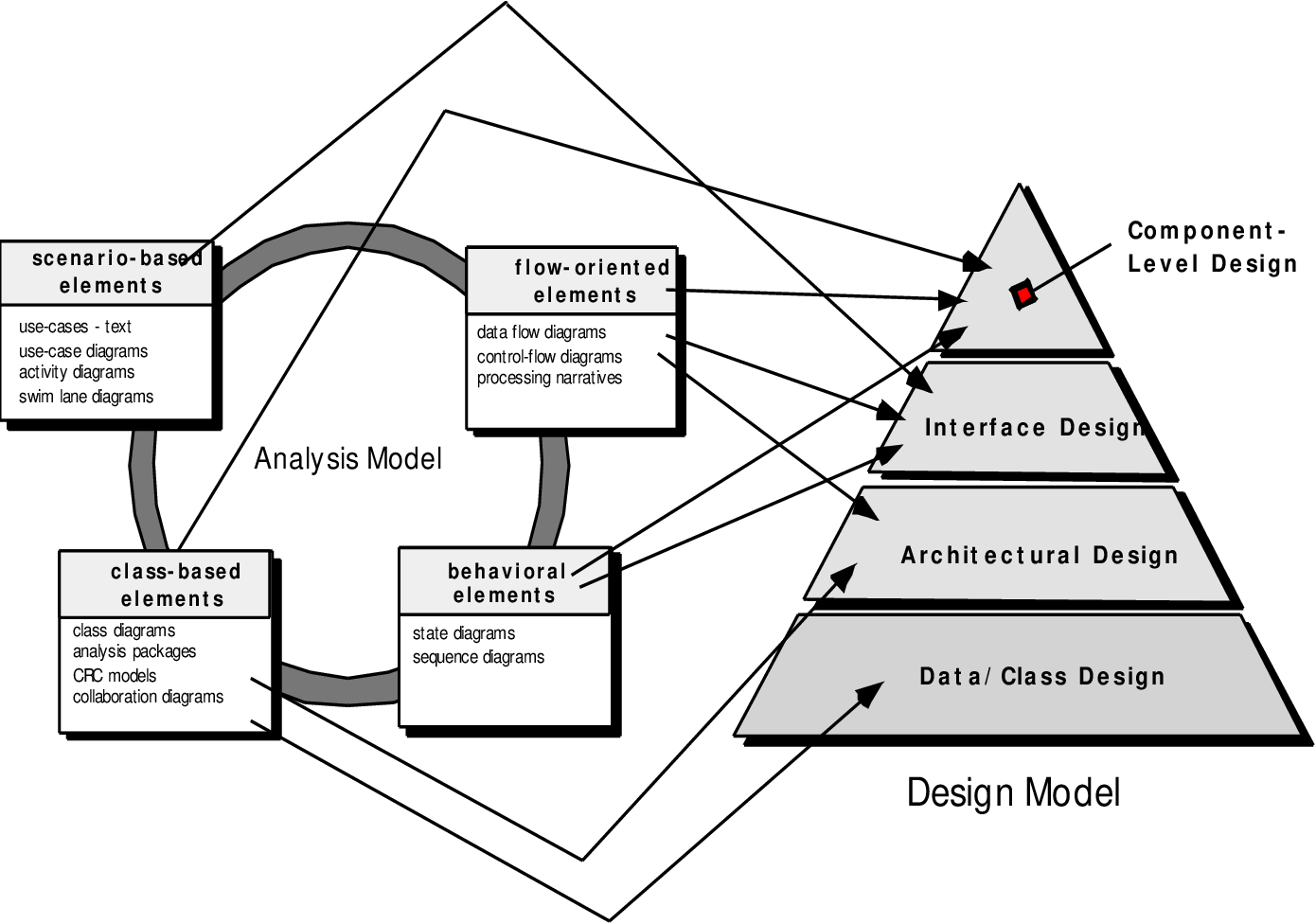
6. Component level design is concerned with
(A) Flow oriented analysis
(B) Class based analysis
(C) Both of the above
(D) None of the above
Solution) (C) Both of the above
Explanation) The design job is fed by the analysis model, which is manifested through scenario-based, class-based, flow-oriented, and behavioural features.
Design creates a data/class design, an architectural design, an interface design, and a component level design using design notations and procedures.
7. The 'C' language is
(A) Context-free language
(B) Context-sensitive language
(C) Regular language
(D) None of the above
Solution) (A) Context free language
Explanation) C and C++ are context-sensitive languages.
8. Which protocol is commonly used to execute the Mobile Application Protocol (MAP)?
(A) SNMP (Simple Network Management Protocol)
(B) SMTP (Simple Mail Transfer Protocol)
(C) SS7 (Signalling System 7)
(D) HTTP (HyperText Transfer Protocol)
Solution) (C) SS7 (Signalling System 7)
Explanation) The following are the main SS7 functions.
- Establishing and dismantling circuit-switched connections, such as phone calls.
- Advanced network functions (calling name/number presentation, Automatic Callback, and so on) are provided by supplemental services.
- Mobility management is a feature of cellular networks that allows users to roam about while remaining connected to the network, even if they are on a call.
- Short Message Service (SMS) and Enhanced Messaging Service (EMS) are functions of SS7.
- Intelligent Network (IN) services such as toll-free (800) calling are supported.
- ISDN support is available.
- Subscribers can change their service, service provider, and location without having to change their phone number thanks to Local Number Portability (LNP).
9. It is a _____ fragment if a packet arrives with an M-bit value of 'l' and a fragmentation offset value of '0'.
(A) First
(B) Middle
(C) Last
(D) All of the above
Solution) (A) First
Explanation) M = 1 denotes that this packet is not the final of all the fragments.
0 Offset This packet contains the 0*8 =0th byte from the original transmission. As a result, the answer is A - First packet.
10. The amount of eight-bit strings that either start with a 1 bit or terminate with two bits 00 shall be
(A) 32
(B) 64
(C) 128
(D) 160
Solution) (D) 160
Explanation) Ending with 00 = 256/4 = 64 numbers
Half of these 64 numbers start with 1, leaving 32.
Assuming starting with 1 and ending with 00 is counted only once:
128 + 32 = 160 numbers
11. What does 'reducing the strength' refer to in compiler design?
(A) lowering the range of input variable values
(B) code optimization using cheaper machine instructions.
(C) reducing the efficiency of the program.
(D) None of the above
Solution) (B) code optimization using cheaper machine instructions.
Explanation) Strength reduction is a compiler optimization technique in which expensive operations are replaced with equivalent but less expensive operations in software engineering. The classic example of strength reduction is when "strong" multiplications inside a loop are converted into "weaker" additions, which is common in array addressing.
- substituting a multiplication within a loop with an addition as an example of a strength decrease
- a multiplication in place of an exponentiation within a loop
12. The effective address of the operand is formed by adding a constant value to the contents of the register in which addressing mode?
(A) Absolute
(B) Indirect
(C) Immediate
(D) Index
Solution) (D) Index
Explanation) The address might be the beginning of an array or vector, and the index could be used to choose a specific array element. The index register can be scaled by the CPU to accommodate the size of each array element.
Note that this is similar to base-plus-offset addressing mode, except that the offset is large enough to target any memory region in this case.
Example: A programmer can declare a string as a local constant or a static variable within a procedure. The string's address is saved in the instruction's literal address. In the index register, the offset (which character of the string to use on this iteration of a loop) is saved.
13. Which of the following is true?
(A) BCNF's relation is always in 3NF.
(B) 3NF's relation is always in BCNF.
(C) BCNF and 3NF are the same.
(D) BCNF's relation is not in 3NF.
Solution) (A) BCNF's relation is always in 3NF.
Explanation) BCNF is a more powerful version of 3NF. As a result, every BCNF relationship will also exist in 3NF.
14. Using the first-fit technique, which memory partition would the process requiring 426 K be placed in, given memory partitions of 100 K, 300 K, 500 K, 200 K, and 600 K (in order) and processes of 212 K, 112 K, 417 K, and 426 K (in order)?
(A) 500 K
(B) 200 K
(C) 300 K
(D) 600 K
Solution) None of the above
Explanation) First-Fit:
212K is put in 500K partition.
417K is put in 600K partition.
112K is put in 288K partition (new partition 288K = 500K - 212K).
426K must wait.
Best-Fit:
212K is put in 300K partition.
417K is put in 500K partition.
112K is put in 200K partition.
426K is put in 600K partition.
Worst-Fit:
212K is put in 600K partition.
417K is put in 500K partition.
112K is put in 388K partition.
426K must wait.
In this example, Best-Fit turns out to be the best.
15. In the Windows Operating System, what is the size of a Unicode character?
(A) 8-Bits
(B) 16-Bits
(C) 32-Bits
(D) 64-Bits
Solution) (B) 16-Bits
Explanation) A Unicode character takes up 2 bytes of space so the answer is (B)sixteen bits.
16. In which tree does the height of its left subtree and right subtree differ almost by one for every node?
(A) Binary search tree
(B) AVL tree
(C) Threaded Binary Tree
(D) Complete Binary Tree
Solution) (B) AVL tree
Explanation) The AVL tree is a tree in which the heights of the left and right subtrees of each node differ by almost one.
17. The design issue of the Datalink Layer in the OSI Reference Model is
(A) Framing
(B) Representation of bits
(C) Synchronization of bits
(D) Connection control
Solution) (A) Framing
Explanation) (B) and (C) are related to Physical Layer.
(D) is related to Transport Layer.
18. Given the following expressions of a grammar E E * F / F + E / F F F – F / id Which of the following is true ?
(A) * has higher precedence than +
(B) – has higher precedence than *
(C) + and – have same precedence
(D) + has higher precedence than *
Solution) (B) – has higher precedence than *
Explanation) Let say i/p is 3*4-5 when we draw parse tree according to grammar
As we can see first ‘- ‘ will be evaluated then ‘ * ‘ is evaluated so ‘ – ‘ has higher precedence then *.
19. The maturity levels used to measure a process are
(A) Initial, Defined, Repeatable, Managed, Optimized.
(B) Primary, Secondary, Defined, Managed, Optimized.
(C) Initial, Stating, Defined, Managed, Optimized.
(D) None of the above
Solution) (A) Initial, Defined, Repeatable, Managed, Optimized.
Explanation) CMM levels
Level 1->Initial
Level 2 ->Repetable
Level 3->Defined
Level 4->Managed
Level 5 ->Optimized
20. In a general priority scheduling algorithm, the problem of indefinite blockage of low-priority jobs can be overcome by:
(A) Parity bit
(B) Aging
(C) Compaction
(D) Timer
Solution) (B) Aging
Explanation) Aging is a solution to the problem of low-priority processes being blocked indefinitely. Aging is a method of gradually raising the priority of processes that have been waiting for a long time in the system.
21. To draw a circle, which API is used?
(A) Circle ( )
(B) Ellipse ( )
(C) Round Rect ( )
(D) Pie ( )
Solution) (B) Ellipse ( )
Explanation) Syntax
- ellipse(a, b, c, d)
A circle is an ellipse with equal width and height. The first two arguments determine the shape's placement by default, while the third and fourth parameters determine the shape's width and height.
22. In DML, RECONNECT command cannot be used with
(A) OPTIONAL Set
(B) FIXED Set
(C) MANDATORY Set
(D) All of the above
Solution) (B) FIXED Set
Explanation) RECONNECT works with both OPTIONAL and MANDATORY sets, but not with FIXED sets.
23. Coaxial cables are classified according to their Radio Government grade and are designed for specific applications. The impedance 75 of category RG-59 was used for
(A) Cable TV
(B) Ethernet
(C) Thin Ethernet
(D) Thick Ethernet
Solution) (A) Cable TV
Explanation) RG-59/U is a type of coaxial cable that is commonly used to link low-power video and RF signals. Consumer electronics such as VCRs and digital cable/satellite receivers are frequently bundled with RG-59 coaxial wire.
24.RAD stands for ______.
(A) Rapid and Design
(B) Rapid Aided Development
(C) Rapid Application Development
(D) Rapid Application Design
Solution) (C) Rapid Application Development
Explanation) RAD stands for Rapid Application Development
25. Let's say someone sends out a chain letter. Each person who receives the letter is requested to forward it to four additional individuals. Some people do this, while others do not write letters at all. If no one receives more than one letter and the chain letter ends after 100 individuals have read it but not sent it out, how many people have seen it, including the original person? Find out how many people sent the letter out as well.
(A) 122 & 22
(B) 111 & 11
(C) 133 & 33
(D) 144 & 44
Solution) (C) 133 & 33
Explanation) Either a person sends to 4 people or he doesn't send it. So, let x be the number of persons who sends to 4 people.
100 people didn't send any letter. Except 1 (the initial person) all others
(x+100) must have a sender. So, we can write
No. of receivers=4×No. of senders+1
(Initial person doesn't have a sender)
No. of receivers=4×No. of senders+1(Initial person doesn't have a sender)
x+100=4x+1⟹3x=99
x=33





