Introduction
The UGC NET, also known as the NTA-UGC-NET, is an examination used to determine eligibility for assistant professorships and Junior Research Fellowships at Indian universities and colleges. The National Testing Agency administers the exam on behalf of the University Grants Commission.
Now we will look at some of the questions that came in UGC NET Dec 2012 Paper II.
Also check Dec 2012 Paper II - Part 1 here.
Questions with Solutions
1. To insert keys 55, 58, 68, 91, 27, 145, a hash function f defined as f (key) = key mod 13 is employed with linear probing. What will the address of 79 be?
(A) 1
(B) 2
(C) 3
(D) 4
Solution) None of the above
Explanation) Ans will be 5, because when we perform linear probing, we need to insert 79 at position 1, but this location is already taken, so we move in a linear way and find an empty space at position 5, where we can insert it.
2. When translating CFG to LL(I) grammar, which of the following is true?
(A) Remove left recursion alone
(B) Factoring grammar alone
(C) Both of the above
(D) None of the above
Solution) (C) Both of the above
Explanation) we need to see Remove left recursion,Factoring grammar while converting CFG to LL(I) grammar.
3. Identify the Risk factors associated with the Electronic payment system.
(A) Fraudulent use of Credit Cards.
(B) Sending Credit Card details over the internet.
(C) Remote storage of Credit Card details.
(D) All of the above
Solution) (D) All of the above
Explanation) It is clear to see the options, and we can assume that if someone uses online banking, these are the primary issues.
Using a credit card fraudulently
Using the internet to send credit card information
Credit card information is stored remotely.
Aside from these, there are a slew of more.
4. Which of the following are two special functions for handling exceptions that occur during exception handling itself?
(A) Void unexpected ( ) and Void terminate ( )
(B) Non void terminate ( ) and void unexpected ( )
(C) non void unexpected ( ) and Void terminate ( )
(D) non void unexpected ( ) and Non void terminate ( )
Solution) (A) Void terminate ( ) and Void unexpected ( )
Explanation)
terminate void ()
The std::terminate() function is called as follows:
If an exception is thrown but not captured, it is considered uncaught.
If the stack is found to be corrupted by the exception handling mechanism.
If a destructor throws when uncaught exception() is true and propagates an exception during stack unwinding due to another exception.
The function terminate() invokes teminate handler(), which calls abort by default (). By passing a function pointer to set terminate, the behaviour of terminate() can be changed ().
unexpected void ()
If a function throws an exception that isn't authorised by the function's exception specification (see below), the following happens:
For the function, the stack is unwound.
The unexpected() function is invoked.
unexpected() invokes unexpected handler(), which calls terminate by default (). By passing a function pointer to set unexpected, the behaviour of unexpected() can be changed ().
5. External fragmentation occurs in which of the following memory allocation schemes?
(A) Segmentation
(B) Pure demand paging
(C) Swapping
(D) Paging
Solution) (A) Segmentation
Explanation) External fragmentation occurs in Segmentation.
6. Basis path testing falls under
(A) system testing
(B) white box testing
(C) black-box testing
(D) unit-testing
Solution) (B) white box testing
Explanation) Basis route testing, often known as structured testing, is a white box method for creating test cases in software engineering. The approach examines a program's control flow graph to identify a set of linearly independent execution routes.
7. The User Work Area (UWA) is a group of Program variables defined in the host program that allows communication of individual records' contents.
(A) DBMS & the Host record
(B) Host program and Host record
(C) Host program and DBMS
(D) Host program and Host language
Solution) (C) Host program and DBMS
Explanation) The User Work Area (UWA) is a buffer that allows a user to interface with a database while using one of the standard host languages.
- In the host programme, a collection of programme variables is declared.
- Each record type has a single programme variable with the same format.
8. Consider the following tree:
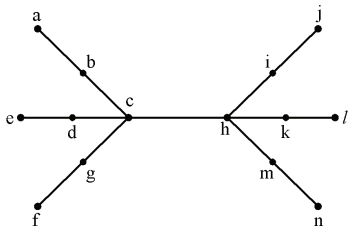
Find every vertex in the center of the provided tree using the eccentricity property.
(A) d & h
(B) c & k
(C) g, b, c, h, i, m
(D) c & h (image)
Solution) (D) c & h
Explanation) Eccentricity of Vertex: The eccentricity of a vertex is defined as the largest distance between a vertex and all other vertices, denoted by e. (V). The eccentricity is the distance between a given vertex and all other vertices in the graph, and it is the greatest of those distances.
For this graph
e(a)=5 e(b)=4 e(c)=3
e(d)=4 e(e)=5 e(f)=5
e(g)=4 e(h)=3 e(i)=4
e(j)=5 e(k)=4 e(l)=5
e(m)=4 e(n)=5
Radius:-The minimum eccentricity from all the vertices is considered as the radius of the Graph G denoted by r(G). The minimum among all the maximum distances between a vertex to all other vertices is considered as the radius of the Graph G.
Here
r(c)=3 and r(h)=3 which is the minimum eccentricity for c and h.
Center:- If the eccentricity of a graph is equal to its radius, then it is known as the central point of the graph. If
e(V) = r(V),
then ‘V’ is the central point of the Graph ’G’.
Here
e(c)=r(c)=3 and e(h)=r(h)=3
Hence, both c and h are center of tree.
9. The maximum number of keys stored in a B-tree of order m and depth d is
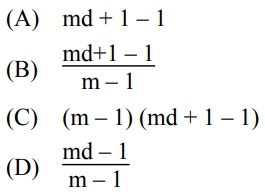
Solution) None of the above
Explanation)

10. Which of the following is the most powerful parring method?
(A) LL(I)
(B) Canonical LR
(C) SLR
(D) LALR
Solution) (B) Canonical LR
Explanation) Canonical LR is the most powerful parser as compared to other LR parsers.
11. In UNIX, which of the following command is used to set the task priority?
(A) init
(B) nice
(C) kill
(D) PS
Solution) (B) nice
Explanation) Nice Command - run a program with modified scheduling priority
12. AES is a round cipher that employs a 128-bit block of data and is based on the Rijndael Algorithm. There are three possible configurations for AES. _ rounds with a key size of 128 bits, _ rounds with a key size of 192 bits, and _ rounds with a key size of 256 bits are available.
(A) 5, 7, 15
(B) 10, 12, 14
(C) 5, 6, 7
(D) 20, 12, 14
Solution) (B) 10, 12, 14
Explanation) For 128-bit keys, there are 10 rounds, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys. A round consists of numerous processing steps that change the input plaintext into the final output of ciphertext, including substitution, transposition, and mixing.
13. Match the following IC families with their basic circuits:
a. TTL 1. NAND
b. ECL 2. NOR
c. CMOS 3. Inverter Code:
a b c
(A) 1 2 3
(B) 3 2 1
(C) 2 3 1
(D) 2 1 3
Solution) (A) 1 2 3
Explanation)
a. TTL (Transistor–transistor logic) 1 NAND
b. ECL (Emitter-coupled logic) 2 NOR
c. CMOS (Complementary metal–oxide–semiconductor) 3 Inverter
14. Match the following concerning C++ data types:
a. User-defined type 1. Qualifier
b. Built-in type 2. Union
c. Derived type 3. Void
d. Long double 4. Pointer Code:
a b c d
(A) 2 3 4 1
(B) 3 1 4 2
(C) 4 1 2 3
(D) 3 4 1 2
Solution) (A) 1 2 3
Explanation)
a. User defined type 2. Union
b. Built in type 3. Void
c. Derived type 4. Pointer
d. Long double 1. Qualifier
15. Given an empty stack, after performing push (1), push (2), Pop, push (3), push (4), Pop, Pop, push(5), Pop, what is the value of the top of the stack?
(A) 4
(B) 3
(C) 2
(D) 1
Solution) (D) 1
Explanation)
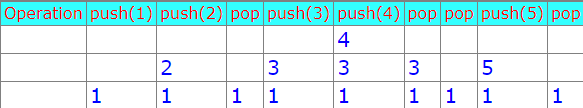
16. Enumeration is a process of
(A) Declaring a set of numbers
(B) Sorting a list of strings
(C) Assigning a legal value possible for a variable
(D) Sequencing a list of operators
Solution) (C) Assigning a legal values possible for a variable
Explanation) A complete, ordered listing of all the elements in a collection is known as an enumeration. In mathematics and computer science, the phrase refers to a list of all the components that make up a set.
17. To open a file for input, which of the following mode declarations is used in C++?
(A) ios : : app
(B) in : : ios
(C) ios : : file
(D) ios : : in
Solution) (D) ios : : in
Explanation)
Clarification: ios::beg is used to reposition the file pointer to the beginning of the file. It is whenever you want to reposition the pointer at the beginning from any point to the start of the file.
18.Data Encryption Techniques are particularly used for ______.
(A) protecting data in Data Communication System.
(B) reduce Storage Space Requirement.
(C) enhances Data Integrity.
(D) decreases Data Integrity.
Solution) (A) protecting data in Data Communication System.
Explanation) Data Encryption Techniques are especially useful for securing data sent between interacting systems. The Presentation Layer implements this feature in the OSI Model.
19.What is the result of the following expression ? (1 & 2) + (3 & 4)
(A) 1
(B) 3
(C) 2
(D) 0
Solution) (D) 0
Explanation)
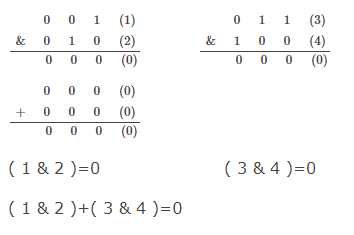
20. Backpropagation is a learning technique that adjusts weights in the neural network by propagating weight changes.
(A) Forward from source to sink
(B) Backward from sink to source
(C) Forward from source to hidden nodes
(D) Backward from since to hidden nodes
Solution) (B) Backward from sink to source
Explanation) Back propagation is a learning technique that adjusts weights in the neural network by propagating weight changes backward from sink to source.
Backpropagation is shorthand for "the backward propagation of errors," since
an error is computed at the output and distributed backwards throughout the network's layers.
21. Match the following :
a. TTL 1. High fan-out
b. ECL 2. Low propagation delay
c. CMOS 3. High power dissipation

Solution) (A) 3 2 1
Explanation)
a.TTL draws more power => 3
b. ECL has highest speed ; Hence it must have lowest propagation delay =>2
c. CMOS has high fan out =>1
22. The activity of _____ is used as an "umbrella" activity in the software engineering process.

Solution) (D) Software quality assurance
Explanation) Umbrella activities are the activities that span all the stages of the SDLC.
umbrella activities include:
• software project management
• formal technical reviews
• software quality assurance
• software configuration management
• reusability management
• measurement
• document preparation and production
• risk management
23. Identify the operation which is commutative but not associative?
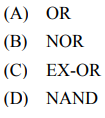
Solution) (B) NOR or (D) NAND
Explanation) NAND operation is commutative but not associative.
24. Given a Relation POSITION (PostingNo, Skill), then query to retrieve all distinct pairs of posting-nos. requiring skill is

Solution) (C) Select p1.posting-No, p2.postingNo from position p1, position p2 where p1.skill = p2.skill and p1.posting-No < p2.postingNo
Explanation) Select p1.posting-No, p2posting-No from position p1, position p2 where p1.skill = p2.skilland p1.posting-No < p2.posting-No
25. Let L be a nondeterministic finite automaton's accepted set. The number of states in a nondeterministic finite automaton is |Q|. In equivalent finite automata that accept L, the most significant number of states is
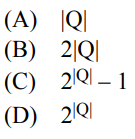
Solution) (D) 2|Q|
Explanation) Conversion from NFA to DFA is done by subset construction .If a problem can be solved with n state in NFA then in worst case number of states in the resulting DFA is 2n
Given Number of states in NFA = |Q|
then Maximum number of states in equivalent DFA =2|Q|