Introduction
UGC NET Exam is a very popular exam in India for people interested in research. Previous Year Questions are an excellent option to learn about the exam pattern. By solving the PYQs, you will get a basic idea about your preparation.
Refer to Dec 2014 Paper III Part 2 here.
Refer to Dec 2014 Paper III Part 3 here.
You can evaluate your weak areas and work on them to perform better in the examination. In this article, we have given the questions of UGC NET Dec 2014 Paper III. We have also explained every problem adequately to help you learn better.
Must Read, 8085 Microprocessor Pin Diagram
Dec 2014 Paper III Part 1
1. A hierarchical memory system that uses cache memory has a cache access time of 50 nanoseconds, a main memory access time of 300 nanoseconds, and 75% of memory requests are for reading, a hit ratio of 0.8 for reading access and the write-through scheme is used. What will be the average access time of the system both for read and write requests?
(A) 157.5 n.sec. (B) 110 n.sec.
(C) 75 n.sec. (D) 82.5 n.sec.
Answer: A
The average access time of the system for memory read cycle is
0.8x50+0.2x350=110ns
The average access time of the system for both read and writes request is
0.75x110+0.25x300=82.5+75=157.5
2. For switching from a CPU user mode to the supervisor mode following type of interrupt is most appropriate
(A) Internal interrupts (B) External interrupts
(C) Software interrupts (D) None of the above
Answer: C
For switching from a CPU user mode to the supervisor mode Software interrupts occurs. Software interrupts is an internal interrupts triggered by some software instruction. An external interrupt is caused by some hardware module.
3. In a dot matrix printer the time to print a character is 6 m.sec., the time to space in between characters is 2 m.sec., and the number of characters in a line is 200. The printing speed of the dot matrix printer in characters per second and the time to print a character line are given by which of the following options?
(A) 125 chars/second and 0.8 seconds
(B) 250 chars/second and 0.6 seconds
(C) 166 chars/second and 0.8 seconds
(D) 250 chars/second and 0.4 seconds
Answer: A
Time to print a character = 6+2=8 m.sec.
Number of characters in a line = 200
Time to print a character line = 200x8=1600 m.sec. = 1.6 seconds
Printing speed in characters per second = 200/1.6 = 125 chars/second
4. Match the following 8085 instructions with the flags :
List – I List – II
a. XCHG i. only carry flag is affected.
b. SUB ii. no flags are affected.
c. STC iii. all flags other than the carry flags are affected.
d. DCR iv. all flags are affected.
Codes :
a b c d
(A) iv i iii ii
(B) iii ii i iv
(C) ii iii i iv
(D) ii iv i iii
Answer: D
XCHG: Exchange H and L with D and E No flag is affected in these instructions
SUB: Subtract All flags(CY, S, Z, AC, P) are affected by subtracting operation
STC: Set carry flag to 1 so Only carry flag is affected
DCR: Decrement All flags other than the carry flag is affected
5. How many times will the following loop be executed?
LXI B, 0007 H
LOP : DCX B
MOV A, B
ORA C
JNZ LOP
(A) 05 (B) 07
(C) 09 (D) 00
Answer: B
value seven is placed in register pair B every time value is reduced by one by DCX B
contents of B are moved to Accumulator and logical OR is performed with C but that don't affect the repetition of the loop which is controlled by JNZ (jump is not zero) LOP instruction so the loop executes for B values 7,6,5,4,3,2,1 total of 7 times
6. Specify the contents of the accumulator and the status of the S, Z and CY flags when the 8085 microprocessor performs addition of 87 H and 79 H.
(A) 11, 1, 1, 1 (B) 10, 0, 1, 0
(C) 01, 1, 0, 0 (D) 00, 0, 1, 1
Answer: D
Addition of 87H and 79H.
87 H - 1 0 0 0 0 1 1 1
79 H - 0 1 1 1 1 0 0 1
1 0 0 0 0 0 0 0 0
S - sign flag - Since the MSB of the result is 0, hence sign bit should be 0.
Z - Zero flag - Since the result is zero, hence zero bit should be 1.
CY - Carry flag - Since there is a carry from MSB (8th to 9th bit), hence CY = 1
7. Location transparency allows :
I. Users to treat the data as if it is done at one location.
II. Programmers to treat the data as if it is at one location.
III. Managers to treat the data as if it is at one location.
Which one of the following is correct?
(A) I, II and III (B) I and II only
(C) II and III only (D) II only
Answer: A
In distributed computer networks, location transparency is the use of names to identify network resources, rather than their actual location. For example, files are accessed by a unique file name, but the actual data is stored in physical sectors scattered around a disk in either the local computer or in a network.
8. Which of the following is correct?
I. Two-phase locking is an optimistic protocol.
II. Two-phase locking is a pessimistic protocol
III. Time stamping is an optimistic protocol.
IV. Time stamping is a pessimistic protocol.
(A) I and III (B) II and IV
(C) I and IV (D) II and III
Answer: D
Two-phase locking is a pessimistic protocol and Time stamping is an optimistic protocol.
9. ............... rules used to limit the volume of log information that has to be handled and processed in the event of system failure involving the loss of volatile information.
(A) Write-ahead log (B) Check-pointing
(C) Log buffer (D) Thomas
Answer: B
Check-pointing rules are used to limit the volume of log information that has to be handled and processed in the event of system failure involving the loss of volatile information.
The write-ahead log provides atomicity and durability in a transaction.
A log buffer is a small contiguous memory which holds memory transaction logs per database.
Thomas write rule is a timestamp-based concurrency control protocol.
10. Let R = ABCDE is a relational scheme with functional dependency set F = {A®B, B®C, AC®D}. The attribute closures of A and E are
(A) ABCD, f (B) ABCD, E
(C) F, f (D) ABC, E
Answer: B
The attribute closures of A:
A+ = ABCD
The attribute closures of E:
E+ = E.
11. Consider the following statements :
I. Re-construction operation used in mixed fragmentation satisfies the commutative rule.
II. Re-construction operation used in vertical fragmentation satisfies the commutative rule
Which of the following is correct?
(A) I
(B) II
(C) Both are correct
(D) None of the statements are correct.
Answer: D
The reconstruction rule of data fragmentation states that, if a relation R is decomposed into
fragments R_{1}, R_{2},...R_{n} it must be possible to define a relational operation that will reconstruct the
relation R from fragments R1, R2,...Rn. This rule ensures the constraints defined on data in the form of functional dependencies are preserved during data fragmentation.
In the case of vertical fragmentation, a relation is partitioned along with its attributes. In this fragmentation, the reconstruction operation is a natural join operation, which is commutative.
In the case of mixed fragmentation, a relation is partitioned along with its attributes as well as along rows.
The reconstruction operation involves both union and natural join. Both operations are commutative.
In the answer keys, it is given that none of the operations is commutative.
12. Which of the following is false?
(A) Every binary relation is never in BCNF.
(B) Every BCNF relation is in 3NF.
(C) 1 NF, 2 NF, 3 NF and BCNF are based on functional dependencies.
(D) Multivalued Dependency (MVD) is a special case of Join Dependency (JD).
Answer: A
Every binary relation is never in BCNF. This statement is incorrect because Every binary relation is always in BCNF.
Every BCNF relation is in 3NF. Correct.
1 NF, 2 NF, 3 NF and BCNF are based on functional dependencies. Correct.
Multivalued Dependency (MVD) is a special case of Join Dependency (JD). Correct.
13. Which of the following categories of languages do not refer to animation languages?
(A) Graphical languages (B) General-purpose languages
(C) Linear-list notations (D) None of the above
Answer: D
All 3 mentioned languages refer to animation languages
14. Match the following :
List – I List – II
a. Tablet, Joystick i. Continuous devices
b. Light Pen, Touch Screen ii. Direct devices
c. Locator, Keyboard iii. Logical devices
d. Data Globe, Sonic Pen iv. 3D interaction devices
Codes :
a b c d
(A) ii i iv iii
(B) i iv iii ii
(C) i ii iii iv
(D) iv iii ii i
Answer: C
Tablet are Joystick are Continuous devices used in computer graphics.
Light Pen, Touch Screen are Direct devices used in computer graphics
Locator are Keyboard areused in computer graphics
Data Globe and Sonic Pen are 3D interaction devices used in computer graphics
15. A technique used to approximate halftones without reducing spatial resolution is known as .................
(A) Halftoning (B) Dithering
(C) Error diffusion (D) None of the above
Answer: B
Halftone is a graphic design technique in which images is reproduced with the help of dots(various colour).
A technique used to approximate halftones without reducing spatial resolution is known as Dithering.
Error diffusion is a type of halftoning in which neighbouring pixels are disturbed(quantization residual is distributed ) that have not yet been processed.
16. Consider a triangle represented by A(0, 0), B(1, 1), C(5, 2). The triangle is rotated by 45 degrees about a point P(–1, –1). The co-ordinates of the new triangle obtained after rotation shall be ..................
(A) A'(-1,√2 - 1), B'(-1,2√2 - 1), C'(3/2√2 – 1, 9/2√2 – 1)
(B) A'(√2 - 1, -1), B'(2√2 - 1, -1), C'(3/2√2 – 1, 9/2√2 – 1)
(C) A'(-1, √2 - 1), B'(2√2 - 1, -1), C'(3/2√2 – 1, 9/2√2 – 1)
(D) A'(-1, √2 - 1), B'(2√2 - 1, -1), C'(9/2√2 – 1, 3/2√2 – 1)
Answer: A
Ans is C with some correction C' should be (3√2/2-1,9√2/2-1)
17. In the Cyrus-Beck algorithm for line clipping, the value of the t parameter is computed by the relation :
(Here, P1 and P2 are the two endpoints of the line, f is a point on the boundary, and n1 is inner normal)
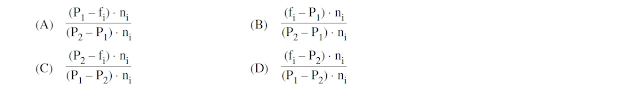
Answer: B
The parameter t is calculated as t = (f-p1)/(p2-p1) where f is a value from the point in question, p1 and p2 are endpoints Option (B) is just a vector notation of the same.
18. Match the following :
a. Cavalier Projection i. The direction of projection is chosen so that there is no foreshortening of lines perpendicular to the XY plane.
b. Cabinet Projection ii. The projection direction is chosen so that lines perpendicular to the XY planes are foreshortened by half their lengths.
c. Isometric Projection iii. The direction of projection makes equal angles with all of the principal axes.
d. Orthographic Projection iv. Projections are characterised by the fact that the projection direction is perpendicular to the view plane.
Codes :
a b c d
(A) i iii iv ii
(B) ii iii i iv
(C) iv ii iii i
(D) i ii iii iv
Answer: D
In Cavalier Projection – The projection direction is chosen to avoid foreshortening of lines perpendicular to the XY plane.
In Cabinet Projection – The projection direction is chosen so that lines perpendicular to the XY planes are foreshortened by half their lengths.
In Isometric Projection – The direction of projection makes equal angles with all of the principal axes.
In Orthographic Projection – The Projections are characterised by the fact that the projection direction is perpendicular to the view plane.
19. Consider the following statements S1, S2 and S3 :
S1: In call-by-value, anything that is passed into a function call is unchanged in the
caller’s scope when the function returns.
S2: In call-by-reference, a function receives an implicit reference to a variable used as
argument.
S3: In call-by-reference, the caller is unable to see the modified variable used as an argument.
(A) S3 and S2 are true. (B) S3 and S1 are true.
(C) S2 and S1 are true. (D) S1, S2, S3 are true.
Answer: C
In call-by-value, anything passed into a function call is unchanged in the caller’s scope when the function returns. Correct.
In call-by-reference, a function receives an implicit reference to a variable used as an argument. Correct.
In call-by-reference, the caller is unable to see the modified variable used as an argument. Incorrect.
20. How many tokens will be generated by the scanner for the following statement ?
x = x * (a + b) – 5;
(A) 12
(B) 11
(C) 10
(D) 07
Answer: A
x|1 =|2 x|3 ∗|4 (|5a|6 +|7 b|8)|9 –|10 5|11;|12
Total 12 tokens are there.
21. Which of the following statements is not true?
(A) MPI_Isend and MPI_Irecv are non-blocking messages passing routines of MPI.
(B) MPI_Issend and MPI_Ibsend are non-blocking messages passing routines of MPI.
(C) MPI_Send and MPI_Recv are non-blocking messages passing routines of MPI.
(D) MPI_Ssend and MPI_Bsend are blocking message passing routines of MPI.
Answer: C
Message-Passing Interface (MPI) standard
MPI_Isend and MPI_Irecv are non-blocking MPI_Ibsend buffered nonblocking so options A and B are correct.
MPI_Ssend and MPI_Bsend are blocking message so D is also
22. The pushdown automation M = ({q0, q1, q2}, {a, b}, {0, 1}, d, q0, 0, {q0}) with
d (q0, a, 0) = {(q1, 10)}
d (q1, a, 1) = {(q1, 11)}
d (q1, b, 1) = {(q2, l)}
d (q2, b, 1) = {(q2, l)}
d (q2, l, 0) = {(q0, l)}
Accepts the language
(A) L = {an bm | n, m ≥ 0} (B) L = {an bn | n ≥ 0}
(C) L = {an bm | n, m > 0} (D) L = {an bn | n > 0}
Answer: B
This PDA clearly accepts an bn , as its language
But as we see that there is a production from Q2 to Q0 that makes the input string halt on Q0, so our final state will be Q0 .
So it will accept empty strings.
23. Given two languages :
L1 = {(ab)n ak | n > k, k ≥ 0}
L2 = {an bm | n ¹ m}
Using a pumping lemma for regular language, it can be shown that
(A) L1 is regular, and L2 is not regular.
(B) L1 is not regular, and L2 is regular.
(C) L1 is regular, and L2 is regular.
(D) L1 is not regular, and L2 is not regular.
Answer: D
L1 is not regular, and L2 is not regular. We would not be able to create finite automata for both the given languages because there is no concept of memory in finite automatas. Hence, both the given languages are not regular.
24. Regular expression for the complement of language L = {an bm | n ≥ 4, m ≤ 3} is
(A) (a + b)* ba(a + b)*
(B) a* bbbbb*
(C) (l + a + aa + aaa)b* + (a + b)* ba(a + b)*
(D) None of the above
Answer: D
The complement of the language L = {anbm|n ≥ 4, m ≤ 3} is L` = {anbm|n < 4} U {anbm|m > 3}:
L` = Universal set – L.
L` = Universal set – {anbm|n ≥ 4, m ≤ 3}
= (λ + a + aa + aaa)b* + a*bbbbb* + (a + b)* ba(a + b)*
Option (D) is giving freedom on constraints on number of a’s and number of b’s.
25. For n devices in a network, .............. number of duplex-mode links are required for a mesh topology.
(A) n(n + 1) (B) n (n – 1)
(C) n(n + 1)/2 (D) n(n – 1)/2
Answer: D
For n devices in a network, n(n – 1)/2 number of duplex-mode links are required for a mesh topology.




