Introduction
UGC NET Exam is a very popular exam in India for people interested in research. Previous Year Questions are an excellent option to learn about the exam pattern. By solving the PYQs, you will get a basic idea about your preparation.
Refer to Dec 2014 Paper III Part 1 here.
Refer to Dec 2014 Paper III Part 2 here.
You can evaluate your weak areas and work on them to perform better in the examination. In this article, we have given the questions of UGC NET Dec 2014 Paper III. We have also explained every problem adequately to help you learn better.
Dec 2014 Paper III Part 3
51. Consider an imaginary disk with 40 cylinders. A request come to read a block on cylinder 11. While the seek to cylinder 11 is in progress, new requests come in for cylinders 1, 36, 16, 34, 9 and 12 in that order. The number of arm motions using shortest seek first algorithm is
(A) 111 (B) 112
(C) 60 (D) 61
Answer: D
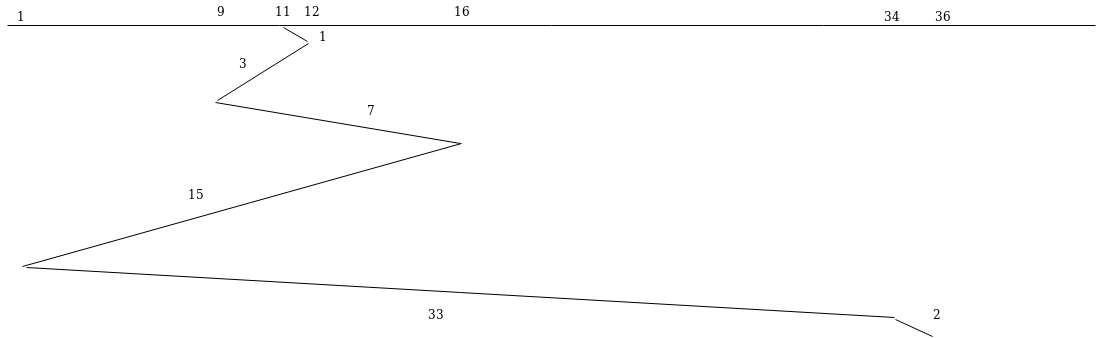
1 + 3 + 7 + 15 + 33 + 2 = 61.
So, option (D) is correct.
52. An operating system has 13 tape drives. There are three processes P1, P2 & P3. Maximum requirement of P1 is 11 tape drives, P2 is 5 tape drives and P3 is 8 tape drives. Currently, P1 is allocated 6 tape drives, P2 is allocated 3 tape drives and P3 is allocated 2 tape drives. Which of the following sequences represent a safe state ?
(A) P2 P1 P3 (B) P2 P3 P1
(C) P1 P2 P3 (D) P1 P3 P2
Answer: A
The maximum need for the process P1, P2, P3 is 11, 5, 8 and the current allocation is 6, 3, and 2 respectively. A total of 13 tape drives were present out of which 11 are allocated and left with 2 drives.
Now P1 needs 5; P2 needs 2; P3 needs 6 tapes. Only P2’s need can be fulfilled. Now after P2 execute 5 tapes are free which can fulfil P1’s demand after that P1 will execute.
The execution order will be P2 P1 P3.
53. Monitor is an Interprocess Communication (IPC) technique which can be described as
(A) It is higher-level synchronization primitive and is a collection of procedures, variables, and data structures grouped together in a special package.
(B) It is a non-negative integer that apart from initialization can be acted upon by wait and signal operations.
(C) It uses two primitives, sends and receive which are system calls rather than language constructs.
(D) It consists of the IPC primitives implemented as system calls to block the process when they are not allowed to enter critical regions to save CPU time.
Answer: A
The monitor is a thread-safe class, object, or module that uses wrapped mutual exclusion in order to safely allow access to a method or variable by more than one thread. The defining characteristic of a monitor is that its methods are executed with mutual exclusion: At each point in time, at most one thread may be executing any of its methods. Using a condition variable(s), can also provide the ability for threads to wait on a certain condition (thus using the above definition of a "monitor"). For the rest of this article, this sense of "monitor" will be referred to as a "thread-safe object/class/module".
54. In a distributed computing environment, distributed shared memory is used which is
(A) Logical combination of virtual memories on the nodes.
(B) Logical combination of physical memories on the nodes.
(C) Logical combination of the secondary memories on all the nodes.
(D) All of the above
Answer: B
The answer should be B only physical memory is combined logically in a distributed system
In computer science, distributed shared memory (DSM) is a form of memory architecture where the (physically separate) memories can be addressed as one (logically shared) address space. Here, the term "shared" does not mean that there is a single centralized memory but "shared" essentially means that the address space is shared (the same physical address on two processors refers to the same location in memory). Distributed global address space (DGAS), is a similar term for a wide class of software and hardware implementations, in which each node of a cluster has access to shared memory in addition to each node's non-shared private memory.
55. Equivalent logical expression for the Well Formed Formula (WFF), ~("x) F[x] is
(A) "x (~F[x]) (B) ~($x) F[x]
(C) $x (~F[x]) (D) "x F[x]
Answer: C
~(∀x) F(x)
=(∃x)(~F(x))
56. An A* algorithm is a heuristic search technique which
(A) is like a depth-first search where the most promising child is selected for expansion
(B) generates all successor nodes and computes an estimate of distance (cost) from the start node to a goal node through each of the successors. It then chooses the successor with the shortest cost.
(C) saves all path lengths (costs) from the start node to all generated nodes and chooses the shortest path for further expansion.
(D) none of the above
Answer: B
Option (A) defines Hill climbing search
Option (B) defines A* search
Option (C) defines Branch and Bound search
57. The resolvent of the set of clauses
(A Ú B, ~A Ú D, C Ú ~B) is
(A) A Ú B (B) C Ú D
(C) A Ú C (D) A Ú D
Answer: B
A∨B, ∼A∨D, C∨∼B
A and ∼A will cancel out and so will B and ∼B
58. Match the following :
a. Script i. Directed graph with labelled nodes for graphical representation of knowledge
b. Conceptual Dependencies ii. Knowledge about objects and events is stored in record-like structures consisting of slots and slot values.
c. Frames iii. Primitive concepts and rules to represent natural language statements
d. Associative Network iv. Frame like structures used to represent stereotypical patterns for commonly occurring events in terms of actors, roles, props and scenes
Codes :
a b c d
(A) iv ii i iii
(B) iv iii ii i
(C) ii iii iv i
(D) i iii iv ii
Answer: B
- The script is a frame structure used to represent stereotypical patterns for commonly occurring events in terms of actors, roles, props and scenes.
- Conceptual dependencies are primitive concepts and rules to represent natural language statements.
- In frames, knowledge about objects and events is stored in record-like structures consisting of slots and slot values.
- An associative network is a directed graph with labelled nodes for graphical representation of knowledge.
59. Match the following components of an expert system :
List – I List – II
a. I/O interface i. Accepts user’s queries and responds to question through I/O interface
b. Explanation module ii. Contains facts and rules about the domain
c. Inference engine iii. Gives the user, the ability to follow inferencing steps at any time during consultation
d. Knowledge base iv. Permits the user to communicate with the system in a natural way
Codes :
a b c d
(A) i iii iv ii
(B) iv iii i ii
(C) i iii ii iv
(D) iv i iii ii
Answer: B
- I/O interface – Permits the user to communicate with the system in a natural way
- Explanation module – Gives the user, the ability to follow inferencing steps at any time during consultation
- Inference engine – Accepts user’s queries and responds to questions through the I/O interface.
- The knowledge base contains facts and rules about the domain.
60. A computer-based information system is needed :
I. as it is difficult for administrative staff to process data.
II. due to the rapid growth of information and communication technology.
III. due to the growing size of organizations which need to process large volumes of data.
IV. as timely and accurate decisions are to be taken.
Which of the above statement(s) is/are true?
(A) I and II
(B) III and IV
(C) II and III
(D) II and IV
Answer: B
As we are comparing computers to humans and reason is asked. For 3rd we can use batch processor or mass of persons. For 4th we will use AI.
61. Given the recursively enumerable language (LRE), the context-sensitive language (LCS), the recursive language (LREC), the context-free language (LCF) and deterministic context-free language (LDCF). The relationship between these families is given by
(A) LCF⊆ LDCF⊆ LCS⊆ LRE⊆ LREC
(B) LCF⊆ LDCF⊆ LCS⊆ LREC⊆ LRE
(C) LDCF⊆ LCF⊆ LCS⊆ LRE⊆ LREC
(D) LDCF⊆ LCF⊆ LCS⊆ LREC⊆ LRE
Answer: D
LDCF⊆ LCF⊆ LCS⊆ LREC⊆ LRE as defined by the Chomsky diagram.
62. Match the following :
List – I List – II
a. Context-free grammar i. Linear bounded automaton
b. Regular grammar ii. Pushdown automaton
c. Context-sensitive grammar iii. Turing machine
d. Unrestricted grammar iv. Deterministic finite automaton
Codes :
a b c d
(A) ii iv iii i
(B) ii iv i iii
(C) iv i ii iii
(D) i iv iii ii
Answer: B
- Context-free grammar can be recognized using push down automata.
- Regular grammar can be recognized using deterministic finite automaton
- Context-sensitive grammar can be recognized using a linear bounded automaton.
-
Unrestricted grammar can be recognized using the turing machine
63. According to the pumping lemma for context-free languages :
Let L be an infinite context-free language, then there exists some positive integer m such that any w ∈ L with |w|³m can be decomposed as w = u v x y z
(A) with | vxy | ≤ m such that uvixyi z∈L for all i = 0, 1, 2
(B) with | vxy | ≤ m, and | vy | ³ 1, such that uvixyiz∈L for all i = 0, 1, 2, …….
(C) with | vxy | ≥ m, and | vy | £ 1, such that uvixyiz∈L for all i = 0, 1, 2, …….
(D) with | vxy | ≥ m, and | vy | ³ 1, such that uvixyiz∈L for all i = 0, 1, 2, …….
Answer: B
Context-free pumping lemma to be the following. Let L be an infinite context-free language. Then there exists some positive integer m such that any w that is a member of L with |w| ≥ m can be decomposed as
w = uvxyz,
with |vxy| ≤ m, and |vy| ≥ 1,
such that wi = uvixyiz,
is also in L for all i = 0, 1, 2, ....
64. Given two spatial masks

The Laplacian of an image at all points (x, y) can be implemented by convolving the image with a spatial mask. Which of the following can be used as the spatial mask?
(A) only S1 (B) only S2
(C) Both S1 and S2 (D) None of these
Answer: B
The answer is S2 only i.e., option B.
Spatial mask for point (x,y) used to implement the digital laplacian of the 2-D is given by
[f(x+1,y),f(x-1,y),f(x,y+1),f(x,y-1)]-4f(x,y)
So possible masks are:-
0 1 0 1 1 1
1 -4 1 or 1 8 1
0 1 0 1 1 1
Here in S1 a1 is missing on the right side of -4.
65. Given a simple image of size 10 × 10 whose histogram models the symbol probabilities and is given by

The first order estimate of image entropy is maximum when
(A) a = 0, b = 0, c = 0, d = 1
(B) a =1/2, b =1/2, c = 0, d = 0
(C) a =1/3, b =1/3, c =1/3, d = 0
(D) a =1/4, b =1/4, c =1/4, d =1/4
Answer: D
The first order estimate of image entropy is maximum when a =1/4, b =1/4, c =1/4, d =¼.
66. A Butterworth lowpass filter of order n, with a cutoff frequency at distance D0 from the origin, has the transfer function H(u, v) given by

Answer: A
The transfer function of a Butterworth lowpass filter of order n with a cutoff frequency
at distance D0 from the origin is defined as:
H(u,v) = 1/1+(D(u,v)/D0)2n
67. If an artificial variable is present in the ‘basic variable’ column of the optimal simplex table, then the solution is
(A) Optimum (B) Infeasible
(C) Unbounded (D) Degenerate
Answer: B
If an artificial variable is present in the ‘basic variable’ column of the optimal simplex table, then the solution is infeasible.
68. The occurrence of degeneracy while solving a transportation problem means that
(A) total supply equals total demand
(B) total supply does not equal total demand
(C) the solution so obtained is not feasible
(D) none of these
Answer: C
Choice A is a must start for a solution
Choice B is converted to case A first then we try soln
We can find unfeasible soln i.e allocations are less than m+n-1 which is a case of degeneracy
69. Five men are available to do five different jobs. From past records, the time (in hours) that each man takes to do each job is known and is given in the following table :
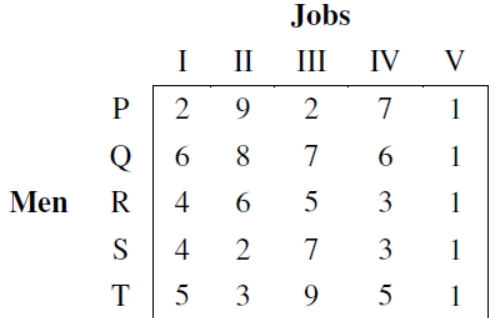
Find out the minimum time required to complete all the jobs.
(A) 5 (B) 11
(C) 13 (D) 15
Answer: C
Consider the matrix of numbers:

Column reduction (directly as a shortcut, instead of row reduction first, since all value in the fifth column are ‘1’): subtracting the minimum number in each column, from all the other numbers in that column:

Allocations can be made as shown above. However, each row and column does not have an allocation. So drawing minimum number of lines through the zeros:
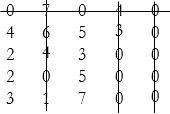
A number of lines = 4, while the order of the matrix = 5. So the solution is not optimal.
From all uncovered elements, we take the minimum of these elements (here 2) and subtract it from all the uncovered elements, while we add it to the elements where two lines intersect:
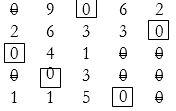
Allocations can be made as shown above.
Making the same allocations is the main matrix:

So minimum total time taken: 4 + 2 + 2 + 3 + 1 = 12
NOTE: To make allocations, follow this rule:
- Starting from the 1st row, make an allocation to a 0 if it is the only zero present in that row.
- After making an allocation in a row, cancel the other 0s in the column where the allocation was made (since only one allocation per row and column is allowed). Make sure to do this before you move to the next row.
- When you move to the next row, do not allocate a 0 that has been cancelled in the previous step.
- In case there are more than one 0s in any row, do not make any allocation & go to the next row.
- Continue till you reach the last row.
- After considering rows, now consider columns. Starting from the 1st column, make an allocation to a 0, if it is the only zero present in that column, and it is not cancelled.
- After making an allocation in a column, cancel the other 0s in the rowwhere the allocation was made (since only one allocation per row and column is allowed). Make sure to do this before you move to the next column.
- When you move to the next column, do not allocate a 0 that has been cancelled in the previous step.
- If there are more than one 0s in any column, do not make any allocation & go to the next column.
- Continue till you reach the last column.
- Repeat steps 1 & 2 in sequence till it is not possible to make any more allocations.
70. Consider the following statements about a perception :
I. Feature detector can be any function of the input parameters.
II. Learning procedure only adjusts the connection weights to the output layer.
Identify the correct statement out of the following :
(A) I is false and II is false. (B) I is true and II is false.
(C) I is false and II is true. (D) I is true and II is true.
Answer: D
Both the given statements are true and are facts.
71. A ............... point of a fuzzy set A is a point x∈X at which μA(x) = 0.5
(A) core
(B) support
(C) crossover
(D) a-cut
Answer: C
The Crossover point of a fuzzy set is the element in U at which its membership function is 0.5
The Support of a fuzzy set F is the crisp set of all points in the Universe of Discourse U such that the membership function of F is non-zero.
if membership is 1 then it is core of a fuzzy set alpha cut (or λͅ -cut) can be anything from 0 to 1 (0<= λͅ<=1)
μA(x)=0.5
72. Match the following learning modes w.r.t. characteristics of available information for learning :
List – I List – II
a. Supervised i. Instructive information on desired responses, explicitly specified by a teacher.
b. Recording ii. A priori design information for memory storing
c. Reinforcement iii. Partial information about desired responses, or only “right” or “wrong” evaluative information
d. Unsupervised iv. No information about desired responses
Codes :
a b c d
(A) i ii iii iv
(B) i iii ii iv
(C) ii iv iii i
(D) ii iii iv i
Answer: A
Supervised --->under some guidance by some teacher
Reinforcement--->evaluation in form of reward or critics (minus points)
Unsupervised ---->no information about desired responses
Recording --->some memory storage
73. Which of the following versions of Windows O.S. contain a built-in partition manager which allows us to shrink and expand pre-defined drives?
(A) Windows Vista (B) Windows 2000
(C) Windows NT (D) Windows 98
Answer: A
- Reliability and Performance Monitor includes various tools for tuning and monitoring system performance and resource activities of CPU, disks, network, memory and other resources. It shows the operations on files, the opened connections, etc.
-
Disk Management: The Logical Disk Manager in Windows Vista supports shrinking and expanding volumes on-the-fly.
74. A Trojan horse is
(A) A program that performs a legitimate function that is known to an operating system or its user and also has a hidden component that can be used for nefarious purposes like attacks on message security or impersonation.
(B) A piece of code that can attach itself to other programs in the system and spread to other systems when programs are copied or transferred.
(C) A program that spreads to other computer systems by exploiting security holes like weaknesses in facilities for the creation of remote processes
(D) All of the above
Answer: A
In computing, a Trojan horse, or Trojan, is any malicious computer program which is used to hack into a computer by misleading users of its true intent. The term is derived from the Ancient Greek story of the wooden horse that was used to help Greek troops invade the city of Troy by stealth.
75. Which of the following computing models is not an example of distributed computing environment?
(A) Cloud computing (B) Parallel computing
(C) Cluster computing (D) Peer-to-peer computing
Answer: B
The two concepts of parallel computing and distributed computing are very closely related; they mostly come from very different backgrounds.
Parallel computing means that different activities happen at the same time. The term was mostly used in scientific computing (consumer computers until very recently simply were not parallel) where it typically means: spread out a single application over many many cores/processors/processes to get it done bigger/faster. Current big parallel computers have 100 thousand to a million parallel processors/cores/threads/whatever.
Distributed computing comes from the business world where you have distributed systems such as airline reservation systems, where many people access and modify the same data at the same time. The machinery involved here is typically much looser coupled, and the activities in a distributed system are typically far less synchronised.




