Introduction
The UGC NET, also known as the NTA-UGC-NET, is an examination used to determine eligibility for assistant professorships and Junior Research Fellowships at Indian universities and colleges. The National Testing Agency administers the exam on behalf of the University Grants Commission.
Now we will look at some of the questions that came in UGC NET Dec 2018 Paper II.
Also check Dec 2018 Paper II - Part 1, Dec 2018 Paper II - Part 2, and Dec 2018 Paper II - Part 4 here.
Questions with Solutions
51.Consider the C/C++ function f() given below:
void f(char w[])
{
int x=strlen(w); //length of a string
char c;
for (int i=0; i<x; i++)
{
c=w[i];
w[i]=w[x-i-1];
w[x-i-1] =c;
}
}
Which of the following is the purpose of f()?
(1) It outputs the contents of the array in reverse order
(2) It outputs the contents of the array in the original order
(3) It outputs the contents of the array with the characters shifted over by one position
(4) It outputs the contents of the array with the characters rearranged so they are no longer recognized as the words in the original phrase
Solution) It outputs the contents of the array in the original order
Explanation)
Let i be the position in the array from the left side then (x-i-1) will be the ith position from the right. When for loop starts running upto mid point,
c=w[i]
w[i]=w[x-i-1]
w[x-i-1]=c
This swaps both the elements which are at ith and (x-i-1)th position hence reverses the input order from midpoint to the end of the array same code is applied.
Reverse of input order = original order of input preserve at the end.
Let's take an example-
Input length=7
Maximum index =6
i=0, x-i-1=6 a[0] swapped with a[6]
i=6, x-i-1=0 a[6] swapped with a[0]
52. The Software Requirement Specification (SRS) is said to be ................ if and only if no subset of individual requirements described in it conflict with each other.
(1) Correct
(2) Consistent
(3) Unambiguous
(4) Verifiable
Solution) Consistent
Explanation) SRS is regarded to be correct if the system meets all of the standards that are required of it. If there are no conflicts between any set of requirements in SRS, they are considered to be consistent. Differences in terminologies used at different locations, logical conflicts such as the time period for report generation, and so on are examples of conflict.
53. Software products need perfective maintenance for which of the following reasons?
(1) To rectify bugs observed while the system is in use
(2) When the customers need the product to run on new platforms
(3) To support new features that users want it to support
(4) To overcome wear and tear caused by the repeated use of the software
Solution) When the customers need the product to run on new platforms
Explanation) This is because perfective maintenance extends the software by adding extra functions.
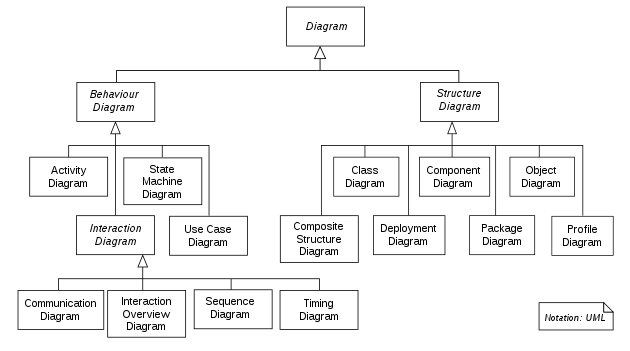
54. Match each UML diagram in List I to its appropriate description in List II
List I List II
(a) State Diagram (i) Describes how the external entities
(people, devices) can interact with the system
(b) Use-Case Diagram (ii) Used to describe the static or
structural view of a system
(c) Class Diagram (iii) Used to show the flow of a business
process, the steps of a use-case or the logic of an object behaviour
(d) Activity Diagram (iv) Used to describe the dynamic behaviour
of objects and could also be used to describe the entire system behaviour
Code:
(1) (a)-(i); (b)-(iv); (c)-(ii); (d)-(iii)
(2) (a)-(iv); (b)-(ii); (c)-(i); (d)-(iii)
(3) (a)-(i); (b)-(iv); (c)-(iii); (d)-(ii)
(4) (a)-(iv); (b)-(i); (c)-(ii); (d)-(iii)
Solution) (a)-(iv); (b)-(i); (c)-(ii); (d)-(iii)
Explanation) Here we have all the diagram images to understand better -
State diagram-
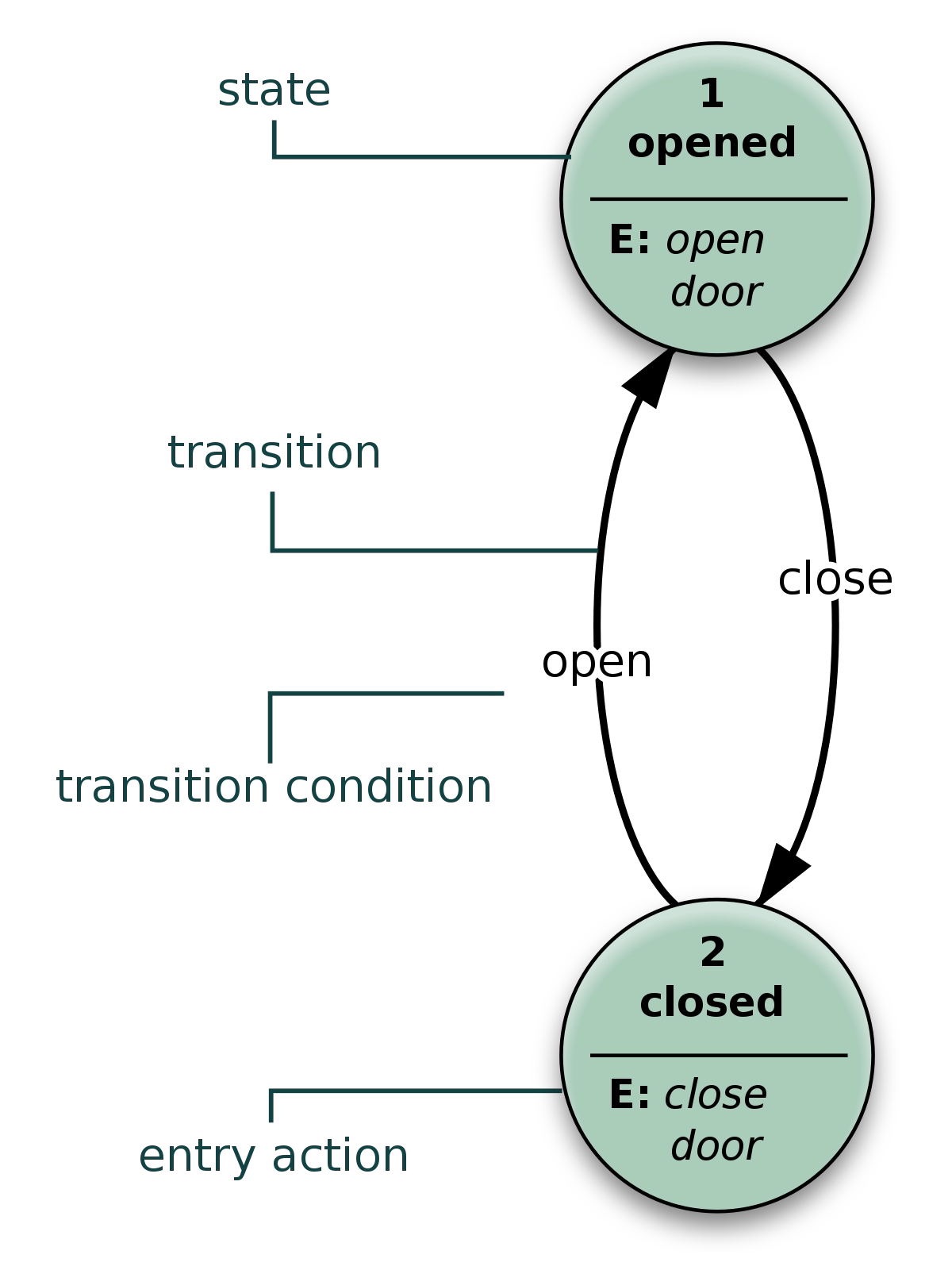
Source - Wikimedia
Use-Case Diagram-
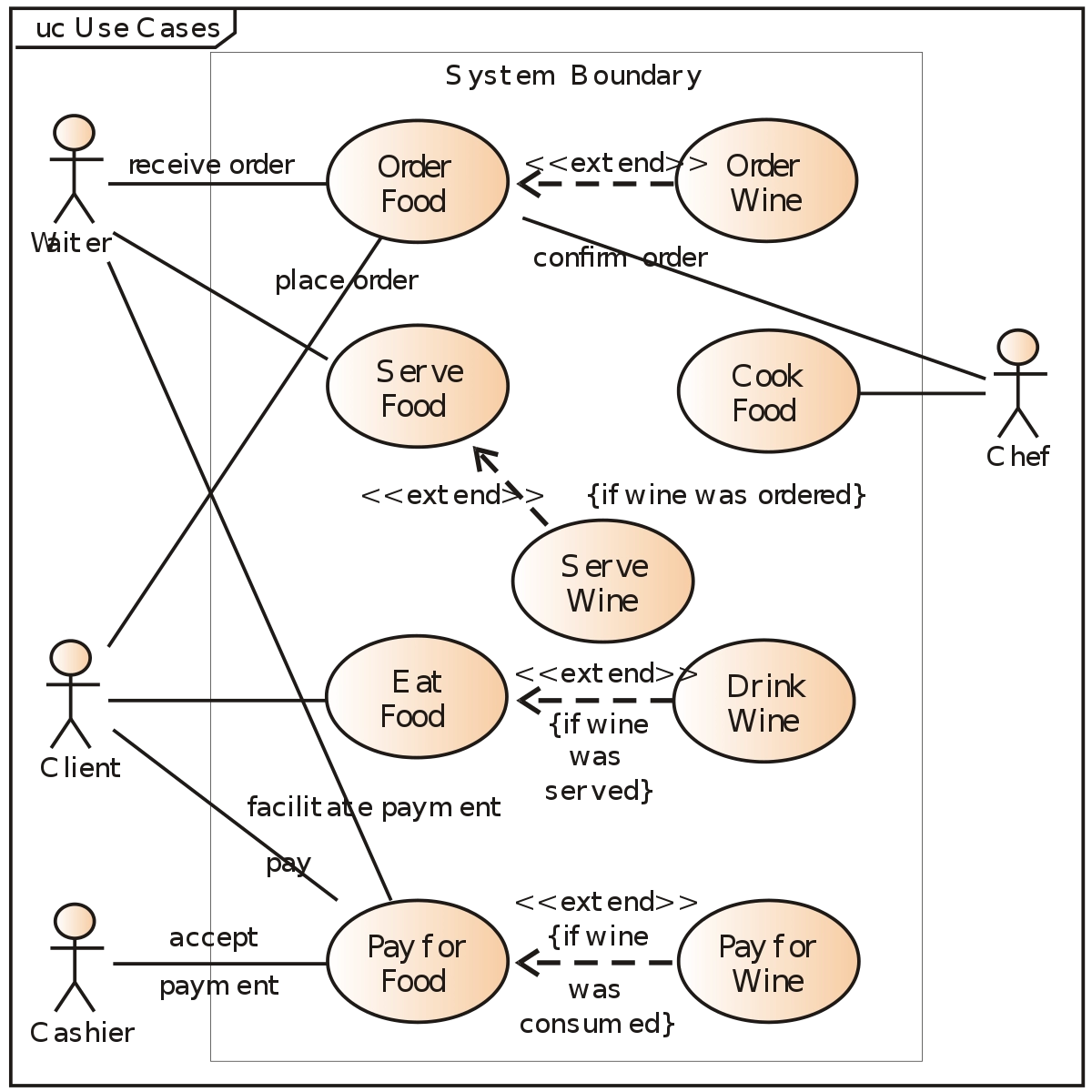
Source - Wikimedia
Class Diagram-
Source - Wikimedia
Activity Diagram-
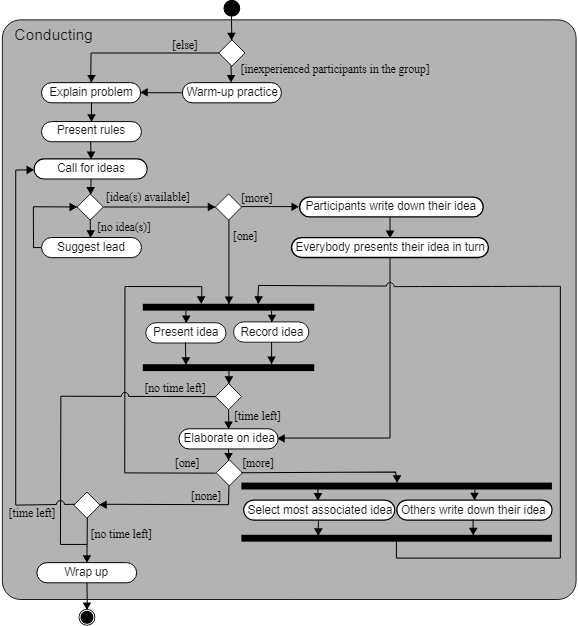
Source - Wikimedia
55. Which of the following statements is/are false?
P: The clean-room strategy to software engineering is based on the incremental software process model.
Q: The clean-room strategy to software engineering is one of the ways to overcome “unconscious” copying of copyrighted code.
Choose the correct answer from the code given below:
Code:
(1) P only
(2) Q only
(3) Both P and Q
(4) Neither P nor Q
Solution) Neither P nor Q
Explanation)
Clean room strategy -
Software engineering is a process model which removes discrepancies and defects before serious hazards. It is based on an incremental model of software development, which accumulates into the final product. Its main goal is to produce zero error based software to avoid rework.
56. Consider the following method:
int f(int m, int n, boolean x, boolean y)
{
int res = 0;
if (m<0) {res = n - m;}
else if (x || y)
{
res = -1;
if(n == m){res = 1;}
}
else {res = n;}
return res;
} /*end of f */
IF P is the minimum number of tests to achieve full statement coverage for f(), and Q is the number of tests to achieve full branch coverage for f(), then (P,Q) =
(1) (3,4)
(2) (4,3)
(3) (2,3)
(4) (3,2)
Solution) (3,4)
Explanation)
Branch coverage:
It indicates that during programme testing, each branch in a statement must be run at least once.
Statement coverage:
It means that during testing, all computer code statements must be executed at least once.
57. A legacy software system has 940 modules. The latest release required that 90 of these modules be changed. In addition, 40 new modules were added and 12 old modules were removed. Compute the software maturity index for the system.
(1) 0.849
(2) 0.524
(3) 0.725
(4) 0.923
Solution) 0.849
Explanation)
SMI = Mt – ( Fa + Fc + Fd)/Mt, Where
SMI – is the Software Maturity Index value
Mt – is the number of software functions/modules in the current release
Fc – is the number of functions/modules that contain changes from the previous release
Fa – is the number of functions/modules that contain additions to the previous release
Fd – is the number of functions/modules that are deleted from the previous release.
SMI =(940 - (40 + 90 + 12 )) /940
=0.8489
=0.849
58. Which of the following statements is/are true?
P: Software Reengineering is preferable for software products having high failure rates, having poor design and/or having poor code structure.
Q: Software Reverse Engineering is the process of analysing software with the objective of recovering its design and requirement specification.
Choose the correct answer from the code given below:
Code:
(1) P only
(2) Q only
(3) Both P and Q
(4) Neither P nor Q
Solution) Both P and Q
Explanation)
Re-engineering is the process of reorganising and modifying existing software systems for making them more maintainable.
Reverse Engineering is a process that from an analysis of its code, recovers the requirement specifications, design, and functions of a product. It builds a program database and generates information from this.
59. Which of the following is not one of the principles of agile software development method?
(1) Customer involvement
(2) Embrace change
(3) Incremental delivery
(4) Following the plan
Solution) Following the plan
Explanation)
Principles Agile Software Development:
1. The highest priority is to satisfy the customer by delivering business-critical software on a timely and consistent basis.
2. Accept changing needs, even late in the development process 3. Frequently deliver working software
4. Throughout the project, businesspeople and developers must collaborate on a daily basis with complete openness.
5. Create projects that revolve around motivated people.
6. Face-to-face communication is the best method of communication 7. Working software is the major indicator of progress 8. Ability to keep a consistent pace
9. Consistent focus on technological quality
10. Simplicity is vital – the art of minimising the amount of work not done.
Teams that self-organise
12. The team reflects on how to become more effective at regular intervals, then tunes and adjusts its behaviour accordingly.
60. Software coupling involves dependencies among pieces of software called modules. Which of the following are correct statements with respect to module coupling?
P: Common coupling occurs when two modules share the same global data.
Q: Control coupling occurs when modules share a composite data structure and use only parts of it.
R: Content coupling occurs when one module modifies or relies on the internal working of another module.
Choose the correct answer from the code given below:
Code:
(1) P and Q only
(2) P and R only
(3) Q and R only
(4) All of P, Q and R
Solution) P and R only
Explanation) Coupling means to connect/pair two or more things together.
- The sharing of common data or global data between several modules comes under Common coupling.
- Controlling data shared between modules comes under Control coupling.
- Stamp coupling basically means that modules share a composite data structure.
- One module relies on or is dependent on the internal workings of another module in content coupling.
61. Match the following Secret Key Algorithms (List I) with Corresponding Key Lengths (List II) and choose the correct answer from the code given below:
List I List II
(a) Blowfish (i) 128 – 256 bits
(b) DES (ii) 128 bits
(c) IDEA (iii) 1 - 448 bits
(d) RC5 (iv) 56 bits
Code:
(1) (a)–(iv), (b)-(iii), (c)-(ii) , d-(i)
(2) (a)–(iii), (b)-(iv), (c)-(i) , d-(ii)
(3) (a)–(iii), (b)-(iv), (c)-(ii) , d-(i)
(4) (a)–(ii), (b)-(iii), (c)-(iv) , d-(i)
Solution) (a)–(iii), (b)-(iv), (c)-(ii) , d-(i)
Explanation)
(a) Blowfish
Blowfish is a symmetric-key block cypher created by Bruce Schneier in 1993 and found in a number of cypher suites and encryption products.
(b) DES
The Data Encryption Standard (DES) is a symmetric-key technique for digital data encryption. Although its small key length of 56 bits renders it insecure for applications, it has had a significant impact on cryptography development.
(c) IDEA
The International Data Encryption Algorithm, also known as the Improved Proposed Encryption Standard, is a symmetric-key block cypher that was first described in 1991 by James Massey of ETH Zurich and Xuejia Lai.
(d) RC5
RC5 is a symmetric-key block cypher known for its ease of use in cryptography. RC stands for "Rivest Cipher," or alternately, "Ron's Code," and was designed by Ronald Rivest in 1994. RC6 was based on RC5. RC5 is a symmetric-key block cypher known for its ease of use in cryptography. RC stands for "Rivest Cipher," or alternately, "Ron's Code," and was designed by Ronald Rivest in 1994. RC6 was based on RC5.
62. The four byte IP address consists of
(1) Network Address
(2) Host Address
(3) Both Network and Host Addresses
(4) Neither Network nor Host Addresses
Solution) Both Network and Host Addresses
Explanation) Both the Network and Host address is present in the four byte IP address.
63. Consider the ISO-OSI network architecture reference model. Session layer of this model offers dialog control, token management and .................. as services.
(1) Synchronisation
(2) Asynchronization
(3) Flow control
(4) Errors
Solution) Synchronisation
Explanation) Functions of Session Layer : Dialog Control, Managing Tokens, Synchronisation. Flow control and error corrections are managed at the Transport layer.
64. Suppose a cloud contains software stack such as Operating systems, Application softwares, etc. This model is referred to as ............ model.
(1) SaaS
(2) PaaS
(3) IaaS
(4) MaaS
Solution) SaaS
Explanation) Customers do not own the physical infrastructure in cloud computing, which is internet-based computing. All services are available via the internet. The following are some of the services available under the cloud computing model:
Software-as-a-Service Software (SaaS) as a service is what it stands for. The application is hosted as a service for consumers who use the internet to access it. It offers cloud-based packaged business process solutions. The cloud contains a stack, which includes things like an operating system and application software.
Infrastructure as a Service (IaaS) is an acronym for infrastructure as a service. It is in charge of delivering virtualized computing resources, network resources, and IaaS users creating their own virtual cluster on which they must install, maintain, and run their own software stack.
Platform as a Service (PaaS) is an acronym meaning platform as a service. It provides all of the resources needed to construct apps and services entirely over the internet, without the need to download or install any software. Design, development, and hosting are all included.
65. The Third Generation mobile phones are digital and based on
(1) AMPS
(2) D-AMPS
(3) CDMA
(4) Broadband CDMA
Solution) Broadband CDMA
Explanation) First generation supports AMPS.
Second generation supports D-AMPS and CDMA.
It is a third-generation wireless communication technology that enables wireless networks to offer broadband voice, data, and multimedia transmission.
66. Which of the following statement/s is/are true?
(i) Firewalls can screen traffic going into or out of an organization.
(ii) Virtual private networks can stimulate an old leased network to provide certain desirable properties.
Choose the correct answer from the code given below:
Code:
(1) (i) only
(2) (ii) only
(3) Both (i) and (ii)
(4) Neither (i) nor (ii)
Solution) Both (i) and (ii)
Explanation)
Statement 1 is correct because a firewall operates at the application layer and may thus monitor traffic entering and exiting the network.
Statement 2 is correct since virtual networks can mimic an older leased network; the main difference is that VPNs include encryption and decryption, whereas leased networks do not.
67. Which of the following statements/s is/are true?
(i) Windows XP supports both peer-peer and client-server networks.
(ii) Windows XP implements Transport protocols as drivers that can be loaded and unloaded from the system dynamically
Choose the correct answer from the code given below:
Code:
(1) (i) only
(2) (ii) only
(3) Neither (i) nor (ii)
(4) Both (i) and (ii)
Solution) Both (i) and (ii)
Explanation)
(i) Both peer-to-peer and client-server networks are supported by Windows XP.
This assertion is correct. Both peer-to-peer and client-server networks are supported by Windows XP. The portability, security, multiprocessor support, extensibility, and other aims of the Windows XP system are all important. A microkernel architecture is used. It's a stacked module system. In this system, there are two modes: protected mode and user mode.
(ii) Transport protocols are implemented in Windows XP as drivers that can be dynamically loaded and uploaded from the system.
A firewall-protected network can be set up in Windows XP. Windows XP's peer-to-peer networking capability makes it simple to set up a working network without the need for a server. It uses transport protocols as drivers that can be dynamically loaded and uploaded from the system.
68. In the Linux operating system environment ............... command is used to print a file.
(1) print
(2) ptr
(3) pr
(4) lpr
Solution) lpr
Explanation) To print a file in Linux operating system, lp command followed by the name of the file that is to be printed is used.
From the given options, lpr is the command that is used to print a file in Linux.
Diagram of linux-
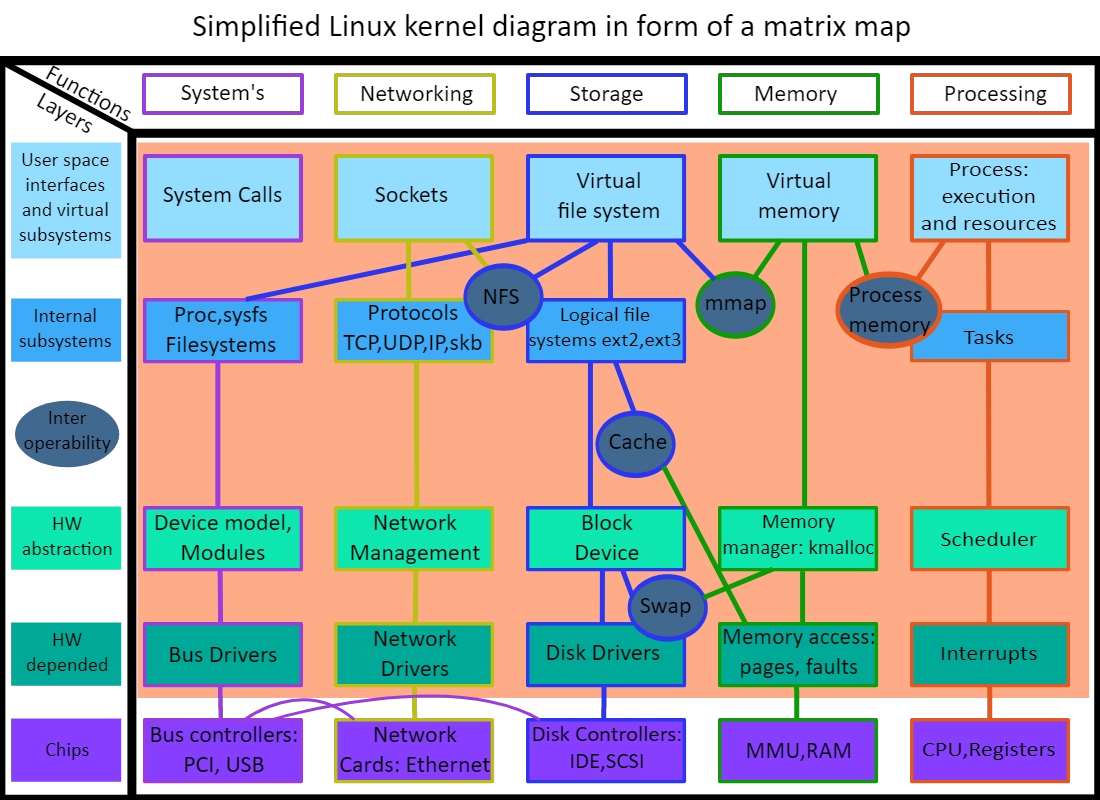
Source - Wikimedia
69. To overcome difficulties in Readers-Writers problem, which of the following statement/s is/are true?
(i) Writers are given exclusive access to shared objects
(ii) Readers are given exclusive access to shared objects
(iii) Both Readers and Writers are given exclusive access to shared objects
Choose the correct answer from the code given below:
Code:
(1) (i) only
(2) (ii) only
(3) (iii) only
(4) Both (ii) and (iii)
Solution) (i) only
Explanation) In the Reader-Writers problem, multiple readers can access at the same time, but when a writer is using a resource there should be no reader or writer in the critical section. So, writers are given exclusive access to shared resources.
70. Suppose a system has 12 instances of some resource with n processes competing for that resource. Each process may require 4 instances of the resource. The maximum value of n for which the system never enters into deadlock is
(1) 3
(2) 4
(3) 5
(4) 6
Solution) 3
Explanation)
Given,
Number of resources (R) = 12
Max need for each resource (N) = 3
Since deadlock-free condition is:
R ≥ P(N − 1) + 1
Where R is total number of resources,
P is the number of processes, and
N is the max need for each resource.
12 ≥ P(4 − 1) + 1
11 ≥ 3P
11/3 ≥ P
P ≤ 3.66
Therefore, the largest value of P that will always avoid deadlock is 3.
71. Dirty bit is used to show the
(1) wrong page
(2) page with corrupted data
(3) page with low frequency occurrence
(4) page that is modified after being loaded into cache memory
Solution) page that is modified after being loaded into cache memory
Explanation) Dirty bit of page is set when a page is modified after it is paged then.
72. Suppose for a process P, reference to pages in order are 1,2,4,5,2,1,2,4. Assume that main memory can accommodate 3 pages and the main memory has already 1 and 2 in the order 1 – first, 2 – second. At this moment, assume FIFO Page Replacement Algorithm is used then the number of page faults that occur to complete the execution of process P is
(1) 4
(2) 3
(3) 5
(4) 6
Solution) 5
Explanation)

73. Consider the following set of processes and the length of CPU burst time given in milliseconds:
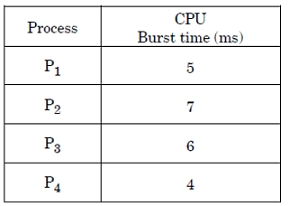
Assume that processes are scheduled with Round-Robin Scheduling Algorithm with time quantum 4 ms. The waiting time for P4 is .............. ms.
(1) 0
(2) 4
(3) 12
(4) 6
Solution) 12
Explanation) If all processes arrive at t=0, the time quantum is 4. When each process employs a single time quantum,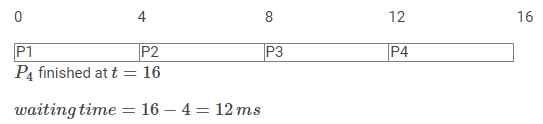
74. Suppose P, Q and R are co-operating processes satisfying Mutual Exclusion conditions. Then, if the process Q is executing in its critical section then
(1) Both ‘P’ and ‘R’ execute in critical section
(2) Neither ‘P’ nor ‘R’ executes in their critical section
(3) ‘P’ executes in critical section
(4) ‘R’ executes in critical section
Solution) Neither ‘P’ nor ‘R’ executes in their critical section
Explanation) Mutual execution means that only one process can be in the critical section at a time, therefore when Q is in the critical area, no other process can be.
75. A process residing in Main Memory and Ready and Waiting for execution, is kept on
(1) Execution Queue
(2) Job Queue
(3) Ready Queue
(4) Wait Queue
Solution) Ready Queue
Explanation) The ready queue stores a process that is running in main memory and ready to execute.