Introduction
UGC NET Exam is a very popular exam in India for people interested in research. Previous Year Questions are an excellent option to learn about the exam pattern. By solving the PYQs, you will get a basic idea about your preparation.
Refer to Dec 2019 Paper II Part 2 here.
Refer to Dec 2019 Paper II Part 3 here.
Refer to Dec 2019 Paper II Part 4 here.
You can evaluate your weak areas and work on them to perform better in the examination. In this article, we have given the questions of UGC NET Dec 2019 Paper II. We have also explained every problem adequately to help you learn better.
Dec 2019 Paper II Part 1
1. Consider the language L = {anbn-3 | n>2} on Σ = {a, b}. Which one of the following grammars generates the language L?
(1) S → aA | a, A → aAb | b (2) S → aaA | λ, A → aAb | λ
(3) S → aaaA | a, A → aAb | λ (4) S → aaaA | λ, A → aAb | λ
Answer: 4
Language L={aaa,aaaab,aaaaabb,aaaaaabbb……..}
Options 1 and 3 are not correct because they generate the string ‘a’ which doesn’t belong to L.
Option 2 is not correct because the grammar generates the string lambda which doesn’t belong to L.
Hence option 4 is the correct answer.
The language generated by the grammar of option 4 is
L={a3.anbn | where n>=0} = {an+3bn | where n>=0}
Where {anbn | n>=0} is generated by the variable A.
So the language generated by grammar is equal to the given grammar.
2. A computer uses a memory unit of 512 K words of 32 bits each. A binary instruction code is stored in one word of the memory. The instruction has four parts: an addressing mode field to specify one of the two-addressing modes (direct and indirect), an operation code, a register code part to specify one of the 256 registers and an address part. How many bits are there in the addressing mode part, opcode part, register code part and the address part?
(1) 1, 3, 9, 19 (2) 1, 4, 9, 18
(3) 1, 4, 8, 19 (4) 1, 3, 8, 20
Answer: 3
So we need ⌈log22⌉=1 bit for addressing the mode part.
There are 256 registers.
So we need ⌈log2256⌉=8 bits for identifying a register. i.e register code part needs 8 bits.
There are 512K words. i.e
512∗210=219 words
So we need ⌈log2219⌉=19 bits for identifying a word. i.e, the address part needs 19 bits.
So remaining bits of 32 bits are used to identify an instruction. i.e opcode.
So opcode has 32−(1+8+19)=32−28=4 bits
Hence the computer can support up to 16 instructions.
So option 3 is the correct answer.
3. What is the output of following C program?
# include<stdio.h>
main( )
{
int i, j, x = 0;
for (i = 0; i < 5; ++i)
for (j = 0; j < i; ++j)
{
x + = (i + j – 1);
break;
}
printf (“%d”,x) ;
}
(1) 6 (2) 5 (3) 4 (4) 3
Answer: 1
The output of the above program will be 6.
4. Consider the following languages:
L1 = {anbncm} ∪ {an bm cm}, n, m ≥ 0
L2 = {ωωR | ω∈{a, b}*} Where R represents reversible operation.
Which one of the following is (are) inherently ambiguous language(s)?
(1) only L1 (2) only L2
(3) both L1 and L2 (4) neither L1 nor L2
Answer: 1
L1 is an inherently ambiguous language because we cannot have any unambiguous grammar for this language.
Specifically, ( Hopcroft & Ullman (1979) gives proof) that there is no way to unambiguously parse strings in the (non-context-free) common subset {anbncn}.
L2 is Not inherently ambiguous and one unambiguous grammar for this language is :
S→aSa|bSb|∈
S→aSa|bSb|∈
It is not hard to show that the above grammar is unambiguous. (Hint : At every symbol, while reading the string from the left, you only have one choice of production rule in the parse tree.)
5. A fuzzy conjunction operators, t(x,y), and a fuzzy disjunction operator, s(x,y), from a pair if they satisfy:
t(x,y) = 1 - s(1 - x, 1 - y).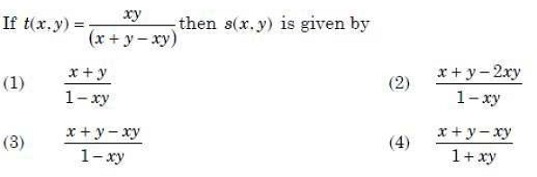
Answer: 2
According to Principle of Duality between Fuzzy Conjunction operator (AND / here t(x,y)) and fuzzy disjunction operator(OR / here s(x,y) ) , they form a dual pair if they satisfy the following condition:
1-t(x,y) = s(1-x, 1-y)
From this condition we'll get t(x,y)=1-s(1-x,1-y)
6. Which of the following statements are true regarding C++?
(a) Overloading gives the capability to an existing operator to operate on other data types.
(b) Inheritance in object oriented programming provides support to reusability.
(c) When object of a derived class is defined, first the constructor of derived class is executed then constructor of a base class is executed.
(d) Overloading is a type of polymorphism.
Choose the correct option from those given below:
(1) (a) and (b) only (2) (a), (b) and (c) only
(3) (a), (b) and (d) only (4) (b), (c) and (d) only
Answer: 3
Statement (a): Overloading gives the capability to an existing operator to operate on other data types.
This statement is incorrect. Operator overloading is a type of polymorphism in which an operator is overloaded to give a different meaning or user defined meaning. It allows to change the way an operator can work. It gives the capability to an existing operator to operate on other data types.
Statement (b): Inheritance in object-oriented programming provides support to reusability.
This statement is correct. When a class acquires the properties of another class, this is known as inheritance. The class which acquire the properties and method is known as derived class and other one is parent or base class. Inheritance another name for reusability.
Statement (c): When object of a derived class is defined, first the constructor of derived class is executed then constructor of a base class is executed.
This statement is incorrect Constructor is a special member function of class that is automatically executed or called when objects of that class will be created. As when object of derived class is defined, automatically derived class constructor and base class constructor will execute inside them.
Statement (d): Overloading is a type of polymorphism.
This statement is correct. Operator is a type of polymorphism in which an operator is overloaded to give a different meaning or user defined meaning. It allows to change the way an operator can work.
7. Which of the following class of IP address has the last address as 223.255.255.255?
(1) Class A (2) Class B
(3) Class C (4) Class D
Answer: 3
Class C (192.0.0.0 to 223.255.255.255) for general use. Class C addresses have only 8 bits for the host address, limiting the number of devices to 256. There are 24 bits for the network address.
8. Let A = (001, 0011, 11, 101} and B = (01, 111, 111, 010}. Similarly, let C = {00, 001, 1000} and D = {0, 11, 011}.
Which of the following pairs have a post-correspondence solution?
(1) Only pair (A, B) (2) Only pair (C, D)
(3) Both (A, B) and (C, D) (4) Neither (A, B) nor (C, D)
Answer: 1
Concept:
Post correspondence problem (PCP): It defines the un-decidability of strings. For the solution of PCP , we have to check whether there is a finite sequence (i1,….ip) with ij belongs to {1,….,m} for j = 1,….p so that ui1ui2…uip = vi1vi2………vip.
Explanation:
CASE: for pair (A, B)
A = {001, 0011, 11, 101}
B = {01, 111, 111, 010}.
Consider it as: A1 = 001, A2 = 0011, A3 = 11, A4 = 101
B1 = 01, B2 = 111, B3 = 111, B4 = 010
Here A3A4 = B2B1 or A3A4 = B3B1
i.e. 11101= 11101
So, pair (A, B) has a PCP solution.
CASE 2: Consider pair (C, D)
C = {00, 001, 1000}
D = {0, 11, 011}.
There does not exist any such combination of strings which satisfy the property for PCP solution. So, Pair (C, D) does not have PCP solution.
9. The sequence diagram given in Figure 1 for the Weather Information System takes place when an external system requests the summarized data from the weather station.
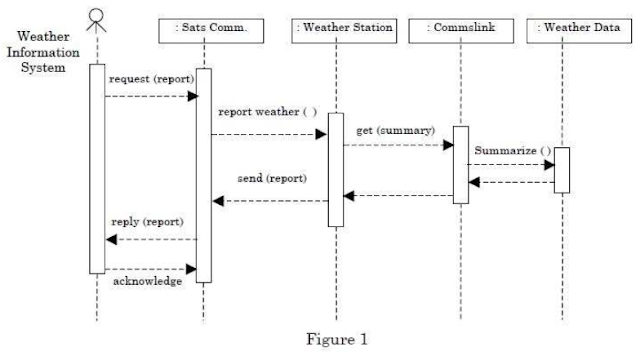
The increasing order of lifeline for the objects in the system are:
(1) Sat comms → Weather station → Comms link → Weather data
(2) Sat comms → Comms link → Weather station → Weather data
(3) Weather data → Comms link → Weather station → Sat Comms
(4) Weather data → Weather station → Comms link → Sat Comms
Answer: Marks to all
According to given UGC NET final key, question remains cancelled and marks awarded to all Page 1 candidates appeared in the test.
A connection is established in order to send and receive data between sender and receiver. And a link is disconnect after completion of data transfer.
Given diagram, Sat Comms requests data to whether station, whether station requests data to Comms link and comm link requests data from whether data.
Comm link gets data first from whether data then the link between comm link and whether data is smallest. Similarly lifetime if connection between Sat comms and whether station is largest.
Hence the increasing order of lifeline for the objects in the system are Weather data → Comms link → Weather station → Sat Comms.
Note: Most appropriate answer is option-C.
10. A counting semaphore is initialized to 8. 3 wait() operations and 4 signal() operations are applied. Find the current value of the semaphore variable.
(1) 9 (2) 5 (3) 1 (4) 4
Answer: 1
Initial size is 8.
And 3 wait() operations
4 signal() operations
= 8 – 3 + 4
= 5 + 4
= 9
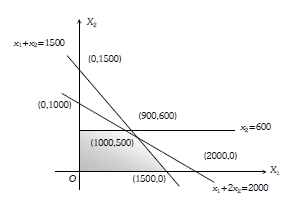
11. Consider the following Linear programming problem (LPP):
Maximize z = x1 + x2
Subject to the constraints:
x1+2x2 ≤ 2000
x1+x2 ≤ 1500
x2 ≤ 600
and x1, x2 ≥ 0
The solution of the above LPP is:
(1) x1=750, x2=750, z=1500 (2) x1=500, x2=1000, z=1500
(3) x1=1000, x2=500, z=1500 (4) x1=900, x2=600, z=1500
Answer: 3
The solution of the above LPP is:
Clearly point (2000, 0) is outside.
12. Which of the following CPU scheduling algorithms is/are supported by LINUX operating system?
(1) Non-preemptive priority scheduling
(2) Preemptive priority scheduling and time sharing CPU scheduling
(3) Time sharing scheduling only
(4) Priority scheduling only
Answer: 2
Pre-emptive priority scheduling and time sharing CPU scheduling algorithms both are supported by LINUX operating system.
13. Which tag is used to enclose any number of javascript statements in HTML document?
(1) <code> (2) <script>
(3) <title> (4) <body>
Answer: 2
< SCRIPT > tag is an extension to HTML that can enclose any number of Javascript statements.
< BODY > contains all the content of HTML document
<HEAD>contains meta data
< TITLE > defines the title of document.
14. When using Dijkstra’s algorithm to find the shortest path in a graph, which of the following statement is not true?
(1) It can find the shortest path within the same graph data structure
(2) Every time a new node is visited, we choose the node with the smallest known
distance/cost (weight) to visit first
(3) Shortest path always passes through the least number of vertices
(4) The graph needs to have a non-negative weight on every edge
Answer: 3
Option (1) : TRUE : Dijkstra's algorithm is an algorithm for finding the shortest paths between nodes within the same graph data structure. Dijkstra's algorithm is a greedy algorithm to identify shortest path.
Option (2) : TRUE : Every time a new node is visited, we choose the node with the smallest known distance/cost (weight) to visit first
Option (3) : FALSE : It is false because Shortest path can have any number of vertices.
Option (4) : TRUE : Dijkstra's algorithm will support only positive weight edges.
So, option 3 is correct answer
15. Consider the following statements with respect to duality in LPP:
(a) The final simplex table giving the optimal solution of the primal also contains optimal
solution of its dual in itself.
(b) If either the primal or the dual problem has a finite optimal solution, then the other
the problem also has a finite optimal solution.
(c) If either problem has an unbounded optimum solution, then the other problem has no
feasible solution at all.
Which of the statements is (are) correct?
(1) only (a) and (b) (2) only (a) and (c)
(3) only (b) and (c) (4) (a), (b) and (c)
Answer: 4
Concept:
Duality in Linear programming problem (LPP) : It means a linear programming problem has another LPP which is derived from it. Original LPP is known as primal and derived LPP is known as Dual.
Explanation:
Some points about dual LPP:
1) The final simplex table giving optimal solution of the primal also contains optimal solution of its dual in itself.
2) If either the primal or the dual problem has a finite optimal solution, then the other problem also has a finite optimal solution.
3) If either problem has an unbounded optimum solution, then the other problem has no feasible solution at all
Example:
We have a set of equations as:
Maximize z = 10x1 + 20 x2
Subject to:
3x1 + 4x2 < =100
5x1 + 6x2 < = 150
X1, x2 >= 0
Dual of this will be:
Minimize z = 100 y1 + 150 y2
Subject to:
3y1 + 4y2 >=10
5y1 + 6y2 > = 20
y1, y2 <= 0
16. Given two tables EMPLOYEE (EID, ENAME, DEPTNO)
DEPARTMENT (DEPTNO. DEPTNAME)
Find the most appropriate statement of the given query:
Select count (*) ‘total’
from EMPLOYEE
where DEPTNO IN (D1, D2)
group by DEPTNO
having count (*) > 5
(1) Total number of employees in each department D1 and D2
(2) Total number of employees of departments D1 and D2 if their total is >5
(3) Display the total number of employees in both departments D1 and D2
(4) The output of the query must have at least two rows
Answer: 2
Breaking down the query, it groups the EMPLOYEE relation on distinct DEPTNO whose frequencies (row counts) are greater than 5 (i.e. no. of employees (hence no. of rows) for those dept. are greater than 5) and further filters only dept. D1 and D2 counts.
(DEPTNO in EMPLOYEE is not a key so multiple values will be present (Obviously))
Though this conclusion can be completely inferred from given option 2 only.
Still, upon critical evaluation of query,
If no. of employees are less than 5 in dept. D1 or D2, the HAVING clause will reject them. Hence, the number of rows my be 2 (for both), 1 (if any one fails >5 cond.) or even no o/p of the query! (when both fail >5 cond.) This rejects option 4 and 1.
Departments are grouped, hence result will contain counts corresponding to respective department. This won't be the sum of two departments hence option 3 is rejected.
17. In a B-Tree, each node represents a disk block. Suppose one block holds 8192 bytes. Each key uses 32 bytes. In a B-tree of order M there are M – 1 keys. Since each branch is on another disk block, we assume a branch is of 4 bytes. The total memory requirement for a non-leaf node is
(1) 32 M – 32 (2) 36 M – 32
(3) 36 M – 36 (4) 32 M – 36
Answer: 2
The size of non-leaf node =m(Pb)+(m−1)(key+Pr)
where Pb is the Block pointer and Pr is the record pointer.
Now, given Pb=4 and size of key =32 but size of
Pr is not given in the question.
∴ Assume it 0.
∴Total size=m(4)+(m−1)(32)=36M−32
18. Let G = (V, T, S, P) be any context-free grammar without any λ-productions or unit productions. Let K be the maximum number of symbols on the right of any production in P. The maximum number of production rules for any equivalent grammar in Chomsky's normal form is given by:
(1) (K – 1) |P| + |T| - 1 (2) (K – 1) |P| +|T|
(3) K |P| + |T| - 1 (4) K |P| + |T|
Where | | denotes the cardinality of the set.
Answer: 2
For any context-free grammar G=(V,T,P,S) without any λ-productions or unit-productions.
The maximum number of production rules are: (k−1)|P|+|T|
where k is the maximum number of the symbol on the right of production P.
19. Given following equation:
(142)b + (112)b-2 = (75)8. Find base b.
(1) 3 (2) 6 (3) 7 (4) 5
Answer: 4
(142)b + (112)b-2 = (75)8
b2 + 4 × b + 2 + 1 × (b – 2)2 + 1 × (b – 2) + 2 = 7×8 + 5
2b2 + b + 6 = 61
2b2 + b – 55 = 0
2b2 + 11b – 10b – 55 = 0
b(2b + 11 ) – 5(2b + 11) = 0
(b – 5).(2b + 11) = 0
∴ b = 5.
Alternate:
Option 1: b = 3
It has base 3 which is not possible because (142) having a digit 4 cannot exist in base 3.
Option 2: b = 6
(142)6 = (62)10
(112)4 = (22)10
62 + 22 = (84)10
(75)8 = (61)10
Therefore 6 is not the base
Option 3: b = 7
(142)7 = (79)10
(112)5 = (32)10
79 + 32 = (111)10
(75)8 = (61)10
Therefore 7 is not the base
Option_4: b = 5
(142)5 = (47)10
(112)3 = (14)10
47 + 14 = (61)10
(75)8 = (61)10
Therefore 5 is the base
Hence, (142)5 + (112)3 = (75)8
20. A microinstruction format has micro-operation field which is divided into 2 subfields F1 and F2, each having 15 distinct micro-operations, condition field CD for four status bits, branch field BR having four options used in conjunction with address field AD. The address space is 128 memory words. The size of micro instruction is:
(1) 19 (2) 18 (3) 17 (4) 20
Answer: 1
Micro instruction format: It consists of two fields of micro-operation. One field from conditions, one for branch field and one is address field.
| F1 | F2 | Condition | Branch | Address |
Explanation:
Micro operation field into two subfields containing 15 micro operations each.
Condition field: 4 status bits
Branch: 4 options in conjunction with address
So, bits required for microoperations = log215 + log215 = 4 + 4 = 8
Condition = log24 = 2
Branch in conjunction with address field = log2(4 × 128) = log2 512 = 9
| F1 (4 bits) | F2( 4 bits) | Condition( 2 bits) | Branch with address (9 bits) |
Size of micro – instruction = 8 + 2 + 9 = 19 bits
21. Consider the following statements with respect to network security:
(a) Message confidentiality means that the sender and the receiver expect privacy.
(b) Message integrity means that the data must arrive at the receiver exactly as they
were sent.
(c) Message authentication means the receiver is ensured that the message is coming
from the intended sender.
Which of the statements is (are) correct?
(1) Only (a) and (b) (2) Only (a) and (c)
(3) Only (b) and (c) (4) (a), (b) and (c)
Answer: 4
Message confidentially means that the sender and the receiver expect privacy.
Message integrity- it means the message is not altered.
Message integrity means that the data must arrive at the receiver exactly as they were sent.
Message authentication- to confirm that the message arrives from a specific sender and is read by a specific receiver.
Message authentication means the receiver ensured that the message is coming from the intended sender.
22. Consider the following statements:
(a) Windows Azure is a cloud-based operating system.
(b) Google App Engine is an integrated set of online services for consumers to
communicate and share with others.
(c) Amazon Cloud Front is a web service for content delivery.
Which of the statements is (are) correct?
(1) Only (a) and (b) (2) Only (a) and (c)
(3) Only (b) and (c) (4) (a), (b) and (c)
Answer: 2
Microsoft Azure, commonly referred to as Azure, is a cloud computing service created by Microsoft for building, testing, deploying, and managing applications and services through Microsoft-managed data centers.
Google App Engine (often referred to as GAE or simply App Engine) is a Platform as a Service and cloud computing platform for developing and hosting web applications in Google-managed data centers.
Amazon CloudFront is a content delivery network (CDN) offered by Amazon Web Services. Content delivery networks provide a globally-distributed network of proxy servers which cache content, such as web videos or other bulky media, more locally to consumers, thus improving access speed for downloading the content.
Statement (b) is wrong because Google App Engine is a cloud computing platform for developing and hosting web applications in Google-managed data centers. It's not an online services for consumers to communicate and share with others.
Hence, Correct statements are only (a) and (c)
So, option 2 is correct answer
23. Two concurrent executing transactions T1 and T2 are allowed to update same stock item say ‘A’ in an uncontrolled manner. In such a scenario, following problems may occur:
(a) Dirty read problem (b) Lost update problem
(c) Transaction failure (d) Inconsistent database state
Which of the following option is correct if database system has no concurrency module and allow concurrent execution of above two transactions?
(1) (a), (b) and (c) only (2) (c) and (d) only
(3) (a) and (b) only (4) (a), (b) and (d) only
Answer: 4
Dirty Read problem: When a transaction is allowed to read a row that has been modified by an another transaction which is not committed yet that time Dirty Reads occurred. It is mainly occurred because of multiple transaction at a time which is not committed.
Lost Update Problem: In the lost update problem, update done to a data item by a transaction is lost as it is overwritten by the update done by another transaction.
Inconsistent Database State: Suppose If the transaction fails after completion of T1 but before completion of T2.( say, after write(X) but before write(Y)), then amount has been deducted from X but not added to Y. This results in an inconsistent database state. Therefore, the transaction must be executed in entirety in order to ensure correctness of database state.
24. Consider the following learning algorithms:
(a) Logistic repression (b) Back propagation (c) Linear repression
Which of the following option represents classification algorithms?
(1) (a) and (b) only (2) (a) and (c) only
(3) (b) and (c) only (4) (a), (b) and (c)
Answer: Marks to all
According to UGC NET Answer key.
This question remains cancelled and marks awarded to all candidates appeared in the test.
The classification learning algorithms are
- Logistic regression
- Back propagation
Note : They given spelling mistake in Logistic regression and Linear Regression instead of "repression".
25. Consider the following grammar:
S→0A|0BB
A→00A|λ
B→1B|11C
C→B
Which language does this grammar generate?
(1) L((00) * 0+(11)*1) (2) L(0(11)* + 1(00)*)
(3) L((00)*0) (4) L(0(11) *1)
Answer: 3
Given grammar is generating string of type: {0, 000, 00000,0000000…...}
1) L((00) * 0 + (11) * 1)
This language generates strings with a combination of 0’s and 1’s. But given grammar is not generating any string composed of 1’s.
2) L(0(11) * + 1(00) * )
This language is not generating a string which contains three 0’s together. Also, it is generating strings which contain 1 in it. So, it is not the correct option.
3) L((00) * 0)
It is generating strings of type: {0, 03, 05, 07,.}. This set of strings is similar to the one generated from given grammar. So, this language is generated by the given grammar.
4) L(0(11) * 1)
It is incorrect because it is generating strings which contain 1 which is not the case with given grammar.




