Introduction
UGC NET Exam is a very popular exam in India for people interested in research. Previous Year Questions are an excellent option to learn about the exam pattern. By solving the PYQs, you will get a basic idea about your preparation.
Refer to Dec 2019 Paper II Part 1 here.
Refer to Dec 2019 Paper II Part 3 here.
Refer to Dec 2019 Paper II Part 4 here.
You can evaluate your weak areas and work on them to perform better in the examination. In this article, we have given the questions of UGC NET Dec 2019 Paper II. We have also explained every problem adequately to help you learn better.
Dec 2019 Paper II Part 2
26. The weight of the minimum spanning tree in graph G, calculated using Kruskal’s algorithm is:
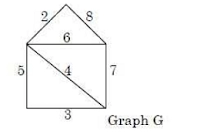
(1) 14 (2) 15 (3) 17 (4) 18
Answer: 2
To find MST of a given graph using Kruskal’s algorithm we can follow
2 steps process:
- Sort all the edges in increasing order of their weights.
- select the smallest edges and check if it forms a cycle with the spanning tree formed so far. if the cycle is not formed then include this edge, else discard it.
Step 1) Sort the edges of the given graph in increasing order of weight. so correct order is :
(2,3,4,5,6,7,8)
(2,3,4,5,6,7,8)
Step 2) Draw the MST by selecting sorted edges one by one.
We know that for n vertices, the number of edges should be (n−1) in MST. so for a given graph having 5 vertices should have 4 edges in MST.
- we can select an edge having a weight 2
- we can also select an edge having a weight 3
- we can select edge having wight 4
- we can’t select an edge having a weight of 5 because it forms a cycle.
- next, we can select an edge having a weight 6
our MST is done here. we can not take the edge with the weight of 7,8 because it forms a cycle.
MST is as follows:
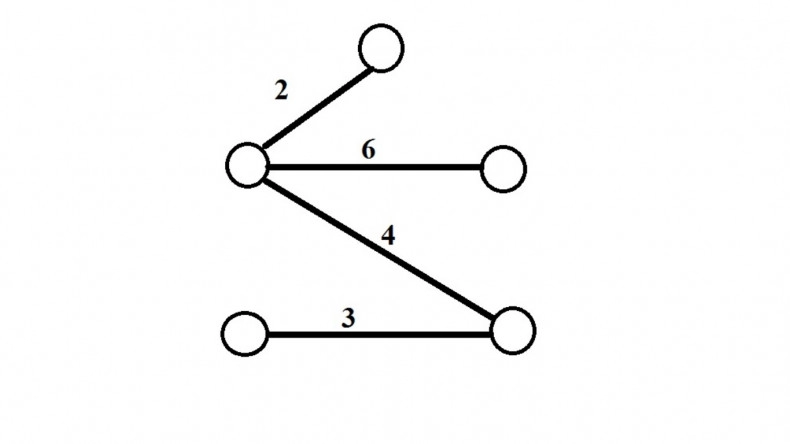
So Total cost of the minimum spanning tree is
(2+3+4+6)=15
Option (B) is correct.
27. The reduced Instruction Set Computer (RISC) characteristics are:
(a) Single-cycle instruction execution
(b) Variable length instruction formats
(c) Instructions that manipulate operands in memory
(d) Efficient instruction pipeline
Choose the correct characteristics from the options given below:
(1) (a) and (b) (2) (b) and (c)
(3) (a) and (d) (4) (c) and (d)
Answer: 3
Instructions are of fixed length and can’t manipulate operands in memory.i.e, they have to be brought into registers for any operation.
28. Let the population of chromosomes in the genetic algorithm is represented in terms of a binary number. The strength of fitness of a chromosome in decimal form, x, is given by
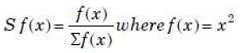
The population is given by P where:
P = {(01101), (11000), (01000), (10011)}
The strength of fitness of chromosome (11000) is ……………..
(1) 24 (2) 576 (3) 14.4 (4) 49.2
Answer: 4
The population of chromosomes in the genetic algorithm is represented in terms of binary numbers.
The strength of fitness of chromosome in decimal form of x
The population is given by P={(01101),(11000),(01000),(10011)}
| P | X -Value | f(x)=X^2 | |
| 01101 | 13 | 169 | |
| 11000 | 24 | 576 | |
| 01000 | 8 | 64 | |
| 10011 | 19 | 361 | |
| Sum | 1170 |
S f(x)= f(x)/ Σ f(x) where f(x)=x^2
Strength of fitness of chromosome (11000) is
= f(11000) / f(01101)+f(11000)+f(01000)+f(10011)
= 576/169+576+64+361
=576/1170
=0.492
so option 4 ) 49.2 is correct
29. Consider the following statements:
(a) The running time of the dynamic programming algorithm is always θ(ρ) where ρ is
a number of subproblems.
(b) When a recurrence relation has a cyclic dependency, it is impossible to use that
recurrence relation (unmodified) in a correct dynamic program.
(c) For a dynamic programming algorithm, computing all values in a bottom-up fashion
is asymptotically faster than using recursion and memorization.
(d) If a problem X can be reduced to a known NP-hard problem, then X must be NP-hard.
Which of the statement(s) is (are) true?
(1) Only (b) and (a) (2) Only (b)
(3) Only (b) and (c) (4) Only (b) and (d)
Answer: 2
(a) The running time of dynamic programming algorithm is always θ (ρ) where ρ is a number of subproblems.
This statement is incorrect. Running time for a dynamic algorithm is the number of subproblems multiplied by the time for each subproblem. It means the running time of the dynamic programming algorithm is O(1).
(b) When a recurrence relation has a cyclic dependency, it is impossible to use that recurrence relation (unmodified) in a correct dynamic program.
Cyclic dependency is the relation between two or more modules which depends on each other indirectly or directly, these are mutually recursive. So, the given statement is correct.
(c) For a dynamic programming algorithm, computing all values in a bottom-up fashion is asymptotically faster than using recursion and memorization.
This statement is incorrect. For a dynamic programming algorithm, computing all values using recursion and memorization takes less time than computing in a bottom-up fashion.
(d) If a problem X can be reduced to a known NP-hard problem, then X must be NP-hard.
If a problem X can be reduced to a known NP-hard problem, then X must be NP-complete, not NP-hard. SO, the given statement is incorrect.
30. Which of the following are legal statements in the C programming language?
(a) int *P = &44;
(b) int *P = &r;
(c) int P = &a;
(d) int P = a:
Choose the correct option:
(1) (a) and (b) (2) (b) and (c)
(3) (b) and (d) (4) (a) and (d)
Answer: 3
Legal Statements:
- int *P = &r; Here, Pointer variable P is storing address of variable r.
- int P = a; Here, P will hold the value assigned by a.
Illegal Statements:
- int *P = &44; Here, the Pointer variable is storing the address of the number. This is not a legal statement. First, it's needed to assign the value 44 in some variable and then the address of that variable can be stored by the Pointer variable P.
- int P = &a; Here, the P variable tries to store the address of the variable. It's illegal. It should be a pointer in place of the int P variable.
So, option 3 is the correct answer.
31. Let P be the set of all people. Let R be a binary relation on P such that (a, b) is in R if a is a brother of b. Is R symmetric transitive, an equivalence relation, or a partial order relation?
(1) NO,NO,NO,NO (2) NO,NO,YES,NO
(3) NO, YES, NO, NO (4) NO, YES, YES, NO
Answer: 3
Symmetric: aRb => bRa
x is a brother of y. So x should be the brother of x which is not necessary. y might be a sister of x.
Therefore, R is not symmetric relation.
Transitive: aRb and bRc imply aRc
x is a brother of y, y is a brother of x, but x is not a brother of x.
Therefore, R is not a transitive relation.
Equivalence: The relation must be reflexive, transitive, and symmetric.
But, R is not satisfied with any of the 3 relation properties.
Therefore, R is not an equivalence relation.
Partial Order: The relation must be reflexive, transitive, and anti-symmetric.
But, the R is neither reflexive nor transitive.
Therefore, R is not a partial order relation.
So, the correct answer is NO, NO, NO, NO.
32. Which of the following algorithms is not used for line clipping?
(1) Cohen-Sutherland algorithm (2) Sutherland-Hodgeman algorithm
(3) Liang-Barsky algorithm (4) Nicholl-Lee-Nicholl algorithm
Answer: 2
Southerland Hodgeman algorithm is a polygon clipping method.
33. The following multithreaded algorithm computes the transpose of a matrix in parallel:
p Trans (X, Y, N)
if N = 1
then Y[1, 1] ← X[1, 1]
else partition X into four (N/2) × (N/2) submatrices X11, X12, X21, X22
partition Y into four (N/2) × (N/2) submatrices Y11, Y12, Y21, Y22
spawn p Trans (X11, Y11, N/2)
spawn p Trans (X12, Y12, N/2)
spawn p Trans (X21, Y21, N/2)
spawn p Trans (X22, Y22, N/2)
What is the asymptotic parallelism of the algorithm?
(1) T1/T∞ or θ(N2 / lg N) (2) T1/T∞ or θ(N / lg N)
(3) T1/T∞ or θ(lg N / N2) (4) T1/T∞ or θ(lg N / N)
Answer: 1
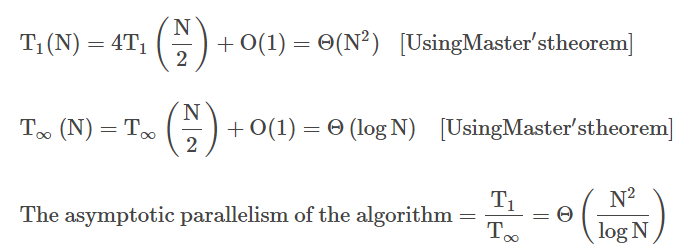
34. A non-pipelined system takes 30ns to process a task. The same task can be processed in a four-segment pipeline with a clock cycle of 10ns. Determine the speed up of the pipeline for 100 tasks.
(1) 3 (2) 4 (3) 3.91 (4) 2.91
Answer: 4
Speed up ratio (S):
It is defined as the speedup of pipeline processing with respect to the equivalent non-pipeline processing.
The formula for calculating Speed up ratio is: ntn/(n+k-1)tp
Number of tasks, n = 100
For Non-pipeline:
Time is taken by non-pipeline to process a task, tn = 30 ns
Total time is taken by non-pipeline to process 100 tasks = ntn
= 100 * 30
= 3000 ns
For Pipeline:
Number of segment pipeline k = 4
Time period of 1 clock cycle, tp = 10 ns
Total time requires to complete n tasks in k segment pipeline with tp clock cycle time:
= (n + k - 1)tp
= (100 + 4 -1)10
= 1030
Speed up Ratio:
When the total time taken by the pipeline to process 100 tasks is divided by the total time requires to complete n tasks in k segment pipeline with tp clock cycle time then the speed up ratio is obtained.
= 3000/1030
= 2.9161
So, option 4 is the correct answer
35. Given a CPU time slice of 2ms and the following list of processes.
Process Burst time Arrival time
(ms)
P1 3 0
P2 4 2
P3 5 5
Find average turnaround time and average waiting time using round-robin CPU scheduling?
(1) 4, 0 (2) 5.66, 1.66
(3) 5.66, 0 (4) 7, 2
Answer: 2
Gantt Chart with time slice of 2ms
| p1 | p2 | p1 | p2 | p3 | p3 | p3 |
0 2 4 5 7 9 11 12
Process Table: (time in milliseconds)
| Process |
Burst time (BT) |
Arrival time (AT) |
Completion time (CT) |
Turn Around Time (TAT) = (CT - AT) |
Waiting time (WT) = (TAT - BT) |
| p1 | 3 | 0 | 5 | 5 | 2 |
| p2 | 4 | 2 | 7 | 5 | 1 |
| p3 | 5 | 5 | 12 | 7 | 2 |
| Sum = 17 | Sum = 5 |
Average TAT = 17/3 = 5.66
Average WT = 5/3 = 1.66
36. Java Virtual Machine (JVM) is used to execute architectural neutral byte code. Which of the following is needed by the JVM for the execution of Java Code?
(1) Class loader only
(2) Classloader and Java Interpreter
(3) Classloader, Java Interpreter and API
(4) Java Interpreter only
Answer 2
Java Virtual Machine (JVM) is used to execute architectural neutral byte code. It has two parts Classloader and Java Interpreter. A class loader first reads the .class file and save the byte code in the method area. The Java interpreter Java translate a class file into code that can be executed natively on the underlying machine.
The Java Virtual machine (JVM) is the virtual machine that runs on the actual machine (your computer) and executes Java byte code. JVM makes java portable (write once, run anywhere). Each operating system has a different JVM, however, the output they produce after the execution of byte code is the same across all operating systems.
So, option 2 is the correct answer
37. In a system for a restaurant, the main scenario for placing order is given below:
(a) Customer reads the menu
(b) Customer places an order
(c) Order is sent to the kitchen for preparation
(d) Ordered items are served
(e) Customer requests a bill for the order
(f) Bill is prepared for this order
(g) Customer is given the bill
(h) Customer pays the bill
A sequence diagram for the scenario will have at least how many objects among whom the messages will be exchanged.
(1) 3 (2) 4 (3) 5 (4) 6
Answer: 3
Option (3) 5
1. Customer
2. Order taking a person
3. Cook
4. Serving person
5. Bill generator
38. The full form of ICANN is
(1) Internet Corporation for Assigned Names and Numbers
(2) Internet Corporation for Assigned Numbers and Names
(3) Institute of Corporation for Assigned Names and Numbers
(4) Internet Connection for Assigned Names and Numbers
Answer: 1
Internet Corporation for Assigned Names and Numbers
39. The Data Encryption Standard (DES) has a function consisting of four steps. Which of the following is the correct order of these four steps?
(1) an expansion permutation, S-boxes, an XOR operation, a straight permutation
(2) an expansion permutation, an XOR operation, S-boxes, a straight permutation
(3) a straight permutation, S-boxes, an XOR operation, an expansion permutation
(4) a straight permutation, an XOR operation, S-boxes, an expansion permutation
Answer: 2
The correct order is an expansion permutation, an XOR operation, S-boxes, a straight permutation.
40. Given two tables R1(x, y) and R2(y, z) with 50 and 30 tuples respectively. Find the maximum number of tuples in the output of natural join between tables R1 and R2 i.e. R1 * R2? (* - Natural Join)
(1) 30 (2) 20 (3) 50 (4) 1500
Answer: 4
Natural Join: Natural Join: In this, the two join attributes must have the common attribute in both the relations.
41. Match List-I with List-II:
List-I List-II
(a) Frame attribute (i) to create link in HTML
(b) <tr> tag (ii) for vertical alignment of content in cell
(c) valign attribute (iii) to enclose each row in table
(d) <a> tag (iv) to specify the side of the table frame that display
border
Choose the correct option from those given below:
(1) (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv) (2) (a)-(ii), (b)-(i), (c)-(iii), (d)-(iv)
(3) (a)-(iv), (b)-(iii), (c)-(ii), (d)-(i) (4) (a)-(iii), (b)-(iv), (c)-(ii), (d)-(i)
Answer: 3
Frame attribute:
It specifies the side of the table frame that display border. The value frame = “hsides” indicates that the border should be drawn on the top and bottom of the table.
tr tag:
It is used to define the rows in the table. Tr tag contains one or more td tags. Td tags inside tr define the columns in a table.
valign attribute:
It vertically aligns the content in a cell. HTML valign attribute supports col, colgroup, tbody, td, tfoot, th, thead, tr elements.
<a> tag:
it is known as an anchor tag. It is used to create hyperlinks in the webpage. When we click on a hyperlink, it takes us to another webpage which is linked with it.
42. The time complexity to multiply two polynomials of degree n using the Fast Fourier transform method is
(1) θ(n log n) (2) θ(n2)
(3) θ(n) (4) θ(log n )
Answer: 1
The time complexity to multiply two polynomials of degree n using the Fast Fourier transform method is θ(n log n).
43. Let Wij represents the weight between node i at layer k and node j at layer (k – 1) of a given multilayer perceptron. The weight updation using the gradient descent method is given by
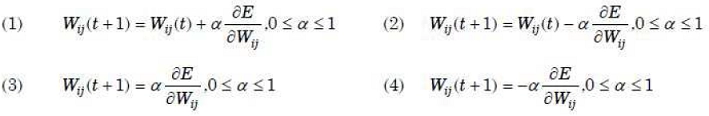
Where α and E represent learning rate and Error in the output respectively.
Answer: 2
Option 2 is correct answer
44. A clique in an undirected graph G = (V, E) is a subset V’ ⊆ V of vertices, such that
(1) If (u, v) ∈ E then u ∈ V’ and v ∈ V’
(2) If (u, v) ∈ E then u ∈ V’ or v ∈ V’
(3) Each pair of vertices in V’ is connected by an edge
(4) All pairs of vertices in V’ are not connected by an edge
Answer: 3
A set of vertices such that each edge of the graph is incident to at least one vertex of the set.
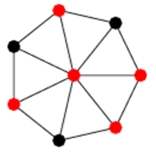
- Set consists of rest of nodes is called independent set.
-
Every planar graph has a vertex cover of size at most 3n/4
45. What is the worst-case running time of Insert and Extract-min, in an implementation of a priority queue using an unsorted array? Assume that all insertions can be accommodated.
(1) θ(1), θ(n) (2) θ(n), θ(1)
(3) θ(1), θ(1) (4) θ(n), θ(n)
Answer: 1
Option 1 is the correct answer
46. Match List-I and List-II:
List-I List-II
(a) Isolated I/O (i) same set of the control signal for I/O and memory
communication
(b) Memory-mapped I/O (ii) separate instructions for I/O and memory
communication
(c) I/O interface (iii) requires control signals to be transmitted
between the communicating units
(d) Asynchronous data transfer (iv) resolve the differences in central computer and
peripherals
Choose the correct option from those given below:
(1) (a)-(ii), (b)-(iii), (c)-(iv), (d)-(i) (2) (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv)
(3) (a)-(ii), (b)-(i), (c)-(iv), (d)-(iii) (4) (a)-(i), (b)-(ii), (c)-(iv), (d)-(iii)
Answer: 3
Isolated i/o:In isolated I/O, devices are treated in a separate domain. There are separate instructions for I/O and memory communication. The device register size is 8 bit in case of isolated I/O. In this, common bus for I/O and memory but separate for reading and writing control lines for I/O.
Memory-mapped I/O: In this, the same set of the control signals for I/O and memory communication. Every bus is common due to which the same set of instructions works for memory and I/O. In this, I/O devices are treated as a part of memory only.
I/O interface: It resolves the differences in control computer and peripherals. It provides a method for transferring information between internal storage and external I/O devices.
Asynchronous data transfer: It is when internal timing in each unit is independent of others and when registers in interface and registers of CPU use their own private clock. It requires control signals to be transmitted between the communicating units.
47. A network with a bandwidth of 10 Mbps can pass only an average of 12,000 frames per minute with each frame carrying an average of 10,000 bits. What is the throughput of this network?
(1) 1,000,000 bps (2) 2,000,000 bps
(3) 12,000,000 bps (4) 1,200,00,000 bps
Answer: 2
Throughput is amount of data moved successfully from one place to another place.
i.e. 12,000 frames per minute. Each Frame is carrying 10,000 bits
So, 12,000 * 10,000 / 60 seconds.
= 2 * 1000000 bits / seconds.
= 2 Mbps.
So, option (B) is correct.
48. What are the greatest lower bound (GLB) and the least upper bound (LUB) of the sets A={3, 9, 12} and B={1, 2, 4, 5, 10} if they exist in poset (z*,/)?
(1) A(GLB – 3, LUB – 36); B(GLB – 1, LUB – 20)
(2) A(GLB – 3, LUB – 12); B(GLB –1, LUB – 10)
(3) A(GLB –1, LUB – 36); B(GLB – 2, LUB – 20)
(4) A(GLB – 1, LUB – 12); B (GLB – 2, LUB – 10)
Answer: 1
What is Least Upper Bound for given set?
Find a value u such that for every element s of set S, s <relation> u exists.
For {3,9,12} – Find the least (smallest) number (say M), for which 3, 9, 12 “divides” M. Because our relation is “/”, this is equivalent to finding LCM (Least Common Multiple) of 3, 9, 12. Thus we get LUB as 12x3=9x4=36. (3, 9 and 12 divide 36)
What is Greatest Lower Bound?
Find value l such that for every element s of set S, l <relation> s exists
For {3,9,12} – Find greatest number less than or equal to an element within {3,9,12}, which “divides” {3,9,12}
Thus GLB is 3 as 3 “divides” {3,9,12}. Because our relationship is “/”, this is equivalent to finding HCF (Highest Common Factor) of 3, 9, 12.
Option 1 is the valid option.
49. A basic feasible solution of an m x n transportation problem is said to be non-degenerate if a basic feasible solution contains exactly ………. a number of individual allocations in ………… positions.
(1) m+n+1, independent (2) m+n-1, independent
(3) m+n-1, appropriate (4) m-n+1, independent
Answer: 2
Definition: Non-Degenerate Basic feasible solution
A basic feasible solution to a (m x n) transportation problem is said to be a non-degenerate if,
(a) The total number of non-negative allocations is exactly m+n-1 and
(b) These m+n-1 allocations are in independent positions.
50. Consider the following language families:
L1 = The context-free languages
L2 = The context – sensitive languages
L3 = The recursively enumerable languages
L4 = The recursive languages
Which one of the following options is correct?
(1) L1 ⊆ L2 ⊆ L3 ⊆ L4 (2) L2 ⊆ L1 ⊆ L3 ⊆ L4
(3) L1 ⊆ L2 ⊆ L4 ⊆ L3 (4) L2 ⊆ L1 ⊆ L4 ⊆ L3
Answer: 3
Every regular language is context-free, every context-free language is context-sensitive, every context-sensitive language is recursive and every recursive language is recursively enumerable. These are all proper inclusions, meaning that there exist recursively enumerable languages that are not context-sensitive, context-sensitive languages that are not context-free and context-free languages that are not regular.




