Introduction
Securing data has become a top priority for individuals and organizations alike. Two key techniques often used to safeguard sensitive information are hashing and encryption. While both methods play vital roles in data protection, they serve distinct purposes and operate differently. Hashing is primarily used for verifying data integrity, while encryption focuses on maintaining data confidentiality. Understanding the difference between hashing and encryption is crucial for choosing the right approach to secure various types of data.

What is Hashing?
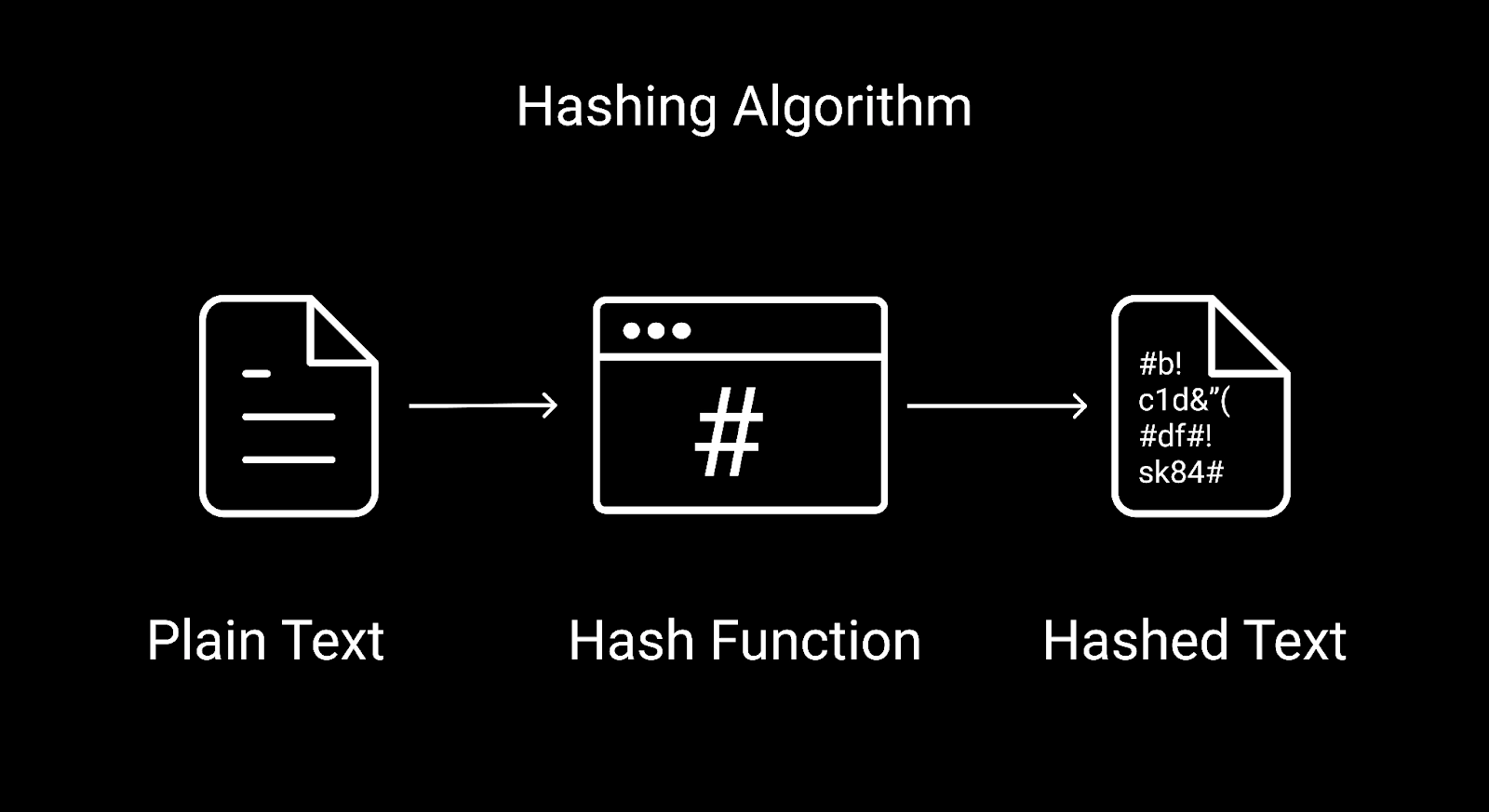
Using a hash function, hashing converts plain text or a key into a hashed value. The input length is greater than the output hash value in most cases. Hashing is a one-way encryption method in which the original plain data cannot be decrypted using the hash value. Hashing is a technique for encrypting data sent between two parties. PINs are safe because passwords are turned into hash values even if a security breach occurs.
In most cases, the hash keys are kept in the database and compared to see if the original information matches. They are typically used to store login passwords. MD5 and SHA256 are two examples of hashing algorithms.
Purpose Of Hashing
While comparing a massive amount of data, hashing is required. For different data, we can create different hash values. Hashes can also be compared.
The purposes of using hashing are:
- Keeping hash data and finding records in them becomes easy.
- The digital signature is a cryptographic application that uses hashing.
- Data duplication can be avoided by a random string generated by hashing.
- Computer graphics uses graphical hashing, which helps find proximity issues in planes.
Common Hashing Algorithms
MD5 (Message Digest Algorithm 5):
- Produces a 128-bit hash value (32-character hexadecimal number).
- Widely used in the past for checksums and data integrity verification.
- Considered insecure due to vulnerabilities like collision attacks.
SHA-1 (Secure Hash Algorithm 1):
- Generates a 160-bit hash value.
- Previously used in SSL certificates and digital signatures.
- Now deemed insecure due to known vulnerabilities and collision issues.
SHA-256 (Secure Hash Algorithm 256-bit):
- Part of the SHA-2 family, producing a 256-bit hash value.
- Commonly used in blockchain technology and digital signatures.
- Considered secure and widely adopted for cryptographic purposes.
SHA-512 (Secure Hash Algorithm 512-bit):
- Another variant of the SHA-2 family, producing a 512-bit hash value.
- Provides higher security and resistance to brute-force attacks.
- Often used for secure password storage and sensitive data hashing.
SHA-3 (Secure Hash Algorithm 3):
- The latest member of the Secure Hash Algorithm family.
- Designed to offer higher security than SHA-2 against potential vulnerabilities.
- Supports various output lengths, including 256-bit and 512-bit versions.
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest):
- Produces a 160-bit hash value.
- Considered an alternative to SHA-1 and MD5, with better security properties.
- Used less frequently compared to SHA algorithms but still in specific applications.