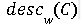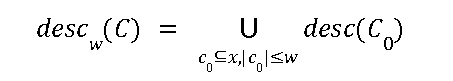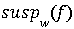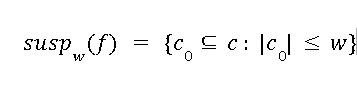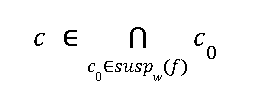Fingerprinting
We can use the fingerprint method to resolve the problem of illegal content redistribution. Suppose there is digital content with n bytes of data; we can avoid illegal content redistribution by adding hidden special bits in the data known as a fingerprint. We can also call this process of identifying confidential data or watermarking.
Let's try to understand fingerprinting with a precise mathematical example. Suppose a content C of X-bits and F fingerprints of size Y-bits; then, we will get D = (C, F). Assuming multiple copies of the content, each with unique fingerprint data D1 = (C,F1), D2 = (C,F2), and so on.
There are two things you should take care of when implementing this technique.
- First, the fingerprint bits should be well hidden in the data and cannot be easily recognizable by the exploiter.
- The attacker should not have two copies of different owners because each user will have a unique fingerprint bit and can destroy or erase the fingerprint by comparing both.
With the help of two unique copies, an attacker can create a hybrid fingerprint by comparing the copies and replacing the fingerprint bits with the hybrid fingerprint. Now, whether these hybrid fingerprints can be traced if constructed validly. To answer this, we need to understand the definition of the descendant code.
The set desc(C0) has all the hybrid fingerprints that can be created from the fingerprints in C0; it is known as the descendant code of C0 here desc(C0) consists of all x-tuples f = (f1, . . . , fx ) such that, for all 1 ≤ i ≤ x, there exists a codeword c = (c1, . . . , cx) ∈ C0 such that fi = ci.
At last, for any c ∈ C0 and f ∈ desc(C0), we claim that c is a parent of f in the code desc(C0).
The w-descendant code of C is denoted as 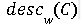 where w is the number of copies of data and w >=2 consists of the following tuples.
where w is the number of copies of data and w >=2 consists of the following tuples.
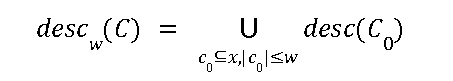
All hybrid fingerprints that can be created by attackers of size at most w are included in the w-descendant code.
Identifiable Parent Property
In identifiable parent property, our goal is to determine the attackers who constructed those hybrid fingerprints. We can call this process the inverse of fingerprinting. The main idea behind this process is to determine the coalitions with the help of the tracing methods.
Let's assume hybrid fingerprints, f ∈ 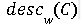 then
then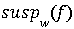 know as the suspect coalitions will be defined as
know as the suspect coalitions will be defined as
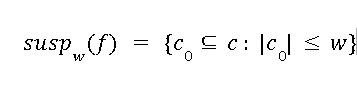
The 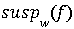 is a set that consists of all coalitions of size at most w that may have created the hybrid fingerprints. Normally
is a set that consists of all coalitions of size at most w that may have created the hybrid fingerprints. Normally 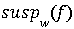 has only one set, and then we can claim that this subset is responsible for the hybrid fingerprints. There can be possibilities of more than one set in
has only one set, and then we can claim that this subset is responsible for the hybrid fingerprints. There can be possibilities of more than one set in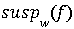 means there can be more the one group of coalitions. Consider the case where a codeword c ∈ C exists and c ∈ C0 for all C0 ∈
means there can be more the one group of coalitions. Consider the case where a codeword c ∈ C exists and c ∈ C0 for all C0 ∈ 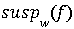 . Even if we cannot identify the entire guilty subset, any codeword can be identified as guilty.
. Even if we cannot identify the entire guilty subset, any codeword can be identified as guilty.
We can claim that the C is a w-identifiable parent property code if it is for all f ∈ 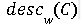 more in a w-IPP code if
more in a w-IPP code if
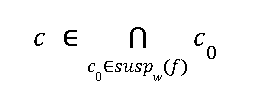
then c is an identifiable parent of f.
Frequently Asked Questions
What is copyright?
Copyright means only the owner who owns a product can make copies of it and publish it.
Is it illegal to copy someone else content?
It is illegal to copy someone else content without their permission and publish it.
What are fingerprint bits?
The hidden bits in the data or content to trace to its rightful owner are known as the fingerprint bits.
What do we mean by the coalition?
A coalition is a group of people to execute or work on a particular subject.
Conclusion
In this blog, we discussed copyright violations and how we can solve them. We have also discussed the fingerprinting method to create a secure copy to trace its rightful owner. The inverse process is the identifiable parent property to identify whether the traced user is valid.
To learn more about cryptography, check out the following articles.
To learn more about DSA, competitive coding, and many more knowledgeable topics, please look into the guided paths on Coding Ninjas Studio. Also, you can enroll in our courses and check out the mock test and problems available to you. Please check out our interview experiences and interview bundle for placement preparations.
Happy Coding!