Introduction
SQL Injection is a technique to use malicious code in SQL statements via webpage input.SQL injection occurs when you ask the user to enter the input like name, id but they enter a SQL statement that will manipulate your database.
It is one of the most common web hacking techniques and contaminates the database’s data.
Example
- An application that stores customer records where any customer can access and view his and her records by entering his unique and customer ID
- The customer enters the following in the input field 13452245 or 1=1.
- As 1=1 holds true for all the records. Hence all the customer details are accessed irrespective of ID details which can be modified in the same way.
Consider the example given below:

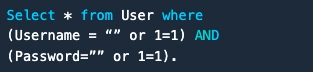
No matter if the password is right or wrong. The backend code will change because 1=1 always returns true. So when we execute the query, it can easily access and modify the private information which is not meant to display to users.
Recommended topics, Coalesce in SQL and Tcl Commands in SQL
Injection Types
There are three main types of Injection.
Error-based: Error-based injections are exploited by triggering errors in the database when invalid inputs are passed. In this method, attackers use error messages to return the entire query results or retrieve information on restructuring the query for further exploitation.
Union-based: Union-based SQL injection allows an attacker to extract information from the database by extending the results returned by the original query. Attackers can use the Union operator if the original or new queries have the same structure.
Blind-Based: Blind SQL injection is one of the most advanced types of Injection. These queries are performed carefully because they can overload a server through heavy automation.