
Introduction
The application layer is at the top of the OSI, and TCP/IP layered models. Because of the importance of engaging with users and user applications, this layer is included in both tiered Models. This layer is used by apps that are part of a communication system.
The apps may or may not be directly interacted with by the user. The actual communication is started and reflected at the application layer. This layer does not service any other layers since it is at the top of the stack. To communicate or send data to a distant host, the Application layer uses Transport and all layers below it. The Application Layer comprises several protocols that consumers often need. HTTP (HyperText Transfer Protocol), the foundation for the World Wide Web, is one of the most frequently used application protocols. When a browser requests a web page, it uses HTTP to deliver its name to the server. The page is then returned to the client by the server.
File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP), Simple Mail Transfer Protocol (SMTP), TELNET, Domain Name System (DNS), and other application protocols are utilized.
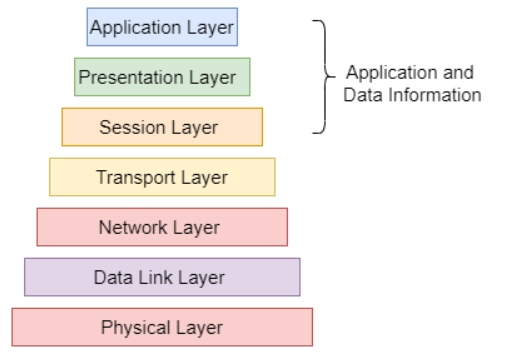
Different layers below the application layer
-
Physical Layer: The application's communication service refers to an application that connects with other computers.
-
Data Link Layer: It specifies how data is sent across a single connection.
-
Network Layer: This layer specifies the end-to-end packet transmission and the logical addresses that identify all the nodes and the methods for implementing and learning routes.
-
Transport Layer: This layer's duties include determining whether to use the error recovery protocol or the error-free recovery protocol, multiplexing the input of various application data streams on the same host, and reordering incoming packets out of order.
-
Session Layer: It describes how to initiate, control, and stop a session, as well as the control and administration of numerous bidirectional messages, allowing applications to be alerted when just a part of a continuous message has been finished and ensuring that the data viewed by the presentation layer is contiguous. If the presentation layer has received all of the data, the data may represent the presentation layer in certain instances.
-
Presentation Layer: The primary purpose of the Presentation Layer is to determine the data format and encryption.
- Application Layer: The application layer relates to the application's communication service and connects with other computers.
The Application Layer
-
The Application Layer offers a capability for users to forward multiple emails and a storage facility. Using this layer, users may access, retrieve, and manage files on a distant computer.
-
It enables users to access the system as a remote host. This layer gives users access to worldwide data on various services and offers services such as email, file transfer, results in distribution, directory services, network resources, and so on.
-
It defines protocols that enable software to communicate and receive data and display it to users in a meaningful way. It also deals with network transparency and resource allocation, among other things.
-
This layer plays a role as a portal via which users and application processes access network resources.
-
The application layer acts as an abstraction layer that defines the standard protocols and interface methods that hosts in a communication network employ.
-
Users may interact with other software programs via this layer.
-
Data is visualized in this layer, therefore allowing people to comprehend rather than memorize or see it in binary format (1s or 0s)
-
This application layer interacts with the OS and ensures appropriately preserved data.
-
This layer also receives and saves data from the Presentation Layer, which comes before it (which carries the syntax and semantics of the information transmitted).
- The protocols employed in this application layer are determined by the kind of data that users want to transmit or receive.
Working of Application layer in OSI Model
This application layer has a smaller scope in the OSI paradigm.
The application layer functions primarily as an interface for connecting with host-based and user-facing programs in the OSI model. This is in contrast to the TCP/IP protocol, which combines the layers below the application layer, namely the Session Layer and the Presentation Layer, to form a single superficial layer responsible for performing functions such as controlling computer dialogues, establishing, maintaining, and terminating a particular session, providing data compression and encryption, and so on.
The client transmits an instruction to the server, and when the server receives it, it assigns a port number to the client. Following that, the client sends an initial connection request to the server, and when the server receives it, it responds with an acknowledgment (ACK) that the client has successfully established a connection with the server. As a result, the client can now has access to the server and can either ask the server to send any file or other document or upload files or documents to the server itself.
Application layer Protocols
There is a total of 10 application layer protocols:
Telnet
The TELetype NETwork is the full form of Telnet. It is beneficial for terminal emulation. It enables Telnet clients to use the Telnet server's resources. It's a program for storing and managing files over the internet. It's used to set up devices such as switches for the first time. The telnet command communicates with a remote device or system using the Telnet protocol. Telnet's port number is 23.
Command:
telnet [\\RemoteServer]
\\RemoteServer: The name of the server to which you wish to connect is specified here.
FTP
The file transfer protocol is also know as FTP. It is the protocol that allows user to send and receive files. This may be done between any two computers that use it. On the other hand, FTP is both a protocol and an application. FTP allows its users to share files over the internet using a very secure and efficient data transfer protocol. The Data port is given as 20, and the control port is 21 for FTP.
Command:
Ftp machinename
TFTP
The Trivial File Transfer Protocol (TFTP) is a stock version of FTP that you should use if you exactly know what you're looking for and where to find it. It's a simplified version of FTP that allows you to transfer files between network devices. The TFTP port number is 69.
Command:
tftp [ options... ] [host [port]] [-c command]
NFS
A network file system is what it's called. It allows remote hosts to mount file systems across a network and interact with them as if they were locally mounted. This enables system administrators to consolidate resources on the network's centralized servers. The NFS port number is 2049.
Command:
service nfs start
SMTP
SMTP is an acronym for Simple Mail Transfer Protocol. The TCP/IP protocol includes it. SMTP moves user email's on and across networks using a process known as "store and forward." In this it collaborates with the Mail Transfer Agent (MTA) to deliver your message to the correct computer and email mailbox. The SMTP port number is 25.
Command:
MAIL FROM:<mailer@codingninjas.com?
LPD
The LPD stands for Line Printer Daemon. It's made for sharing devices like printers, scanners, etc. A server or agent is known as a "daemon." The LPD port number is 515.
Command:
lpd [ -d ] [ -l ] [ -D DebugOutputFileName]
X window
It specifies a protocol for developing client/server applications with a graphical user interface. The concept is to execute a client application on a single machine. It's primarily utilized in linked mainframe networks. For each server, the port number for the X window begins at 6000 and grows by one.
Command:
Run xdm in runlevel 5
SNMP
SNMP is used for Simple Network Management Protocol. It collects data by polling network devices at specified or random intervals from a management station, compelling them to provide certain information. It's a mechanism for servers to communicate information about their present status and a way for administrators to change and modify pre-defined settings. The given SNMP port numbers :
- 161 (TCP)
- 162 (UDP) (UDP).
Command:
snmpget -mALL -v1 -cpublic snmp_agent_Ip_address sysName.0
DNS
DNS is used for Domain Name System. As a result, every time you use a domain name, a DNS provider must convert the character into an IP address. The domain name www.abc.com, for example, maybe translated as 198.105.232.4.
The DNS port number is 53.
Command:
ipconfig /flushdns
DHCP
DHCP is an acronym for Dynamic Host Configuration Protocol (DHCP). It assigns IP addresses to servers. When a computer registers for an IP address with a DHCP server, the DHCP server may offer much information to the host. The DHCP port numbers are 67 and 68.
Command:
clear ip dhcp binding {address | * }
You can also read about mime protocol.




