
Introduction
The NET(National Eligibility Test) is executed on behalf of the University Grants Commission (UGC) to decide the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Colleges and Universities.
This article discusses the previous year's UGC-NET computer science questions of July 2018 Paper II. We will see these questions along with their answers and explanation.
Questions
1. The definition in an XML document is .............. when the tagging system and descriptions in the DTD are all in compliance.
(1) well-formed
(2) reasonable
(3) valid
(4) logical
Answer: 3
Explanation: An XML document is said to be well-formed if it has correct syntax, like tags being case sensitive; elements must have closing tags, elements must be nested appropriately, etc.
But when we associate a well-formed XML document with a DTD, we define the structure of a document. If that XML document validates each of the definitions defined in DTD, then that XML document is called a "valid" XML document.
Note that a "valid” XML document is a "well-formed” XML document but a "well-formed" XML document is not necessarily a "valid” XML document. In question, it is mentioned that the XML document validates the definitions in the DTD. Hence the correct answer is option (3).
2. Consider the JavaScript Code :
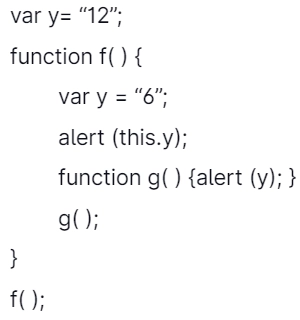
Let M is the number of alert dialog boxes generated by this JavaScript code and D1, D2, ............, DM denotes the content displayed in each of the M dialog boxes, then:
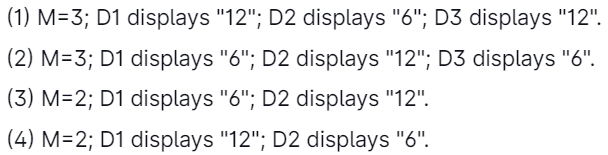
Answer: 4
Explanation:
The "this" keyword in JavaScript refers to the object it belongs to.
It includes different values depending on where it is used:
In a method, this refers to the owner's object.
Alone, "this" refers to a global object.
In the function, "this" also refers to the global object.
Methods like apply() and call() can refer to "this" to any object.
Inside an event, the "this" keyword refers to the element that obtained the event.
There are two alert boxes in a javascript code. So we will display two messages.
The first message, alert(this.y) here this.y is a global variable whose value is 12. So the first message is "12".
The second message is alert(y); here "y" local variable and value is 6, so the second message displays a value of "6."
3. What is the output of the subsequent JAVA program?


Answer: 4
Explanation: Firstly, we will create the object of a simple class.
By using an object, we call the function start().
In the start() function definition, the first statement is an integer array with three elements 3, 4, & 5.
In long [ ] Q = method(P); Again function method(p) is called.
In the description of the method function, we are changing the second element of the array to value seven and returning the updated array to array Q.
We are passing the address of P as an argument to the method, so Modifications that happened in the method are automatically reflected in array P.
Both the array P and Q consists of values {3,7,5}
The sum of the three values is 15.
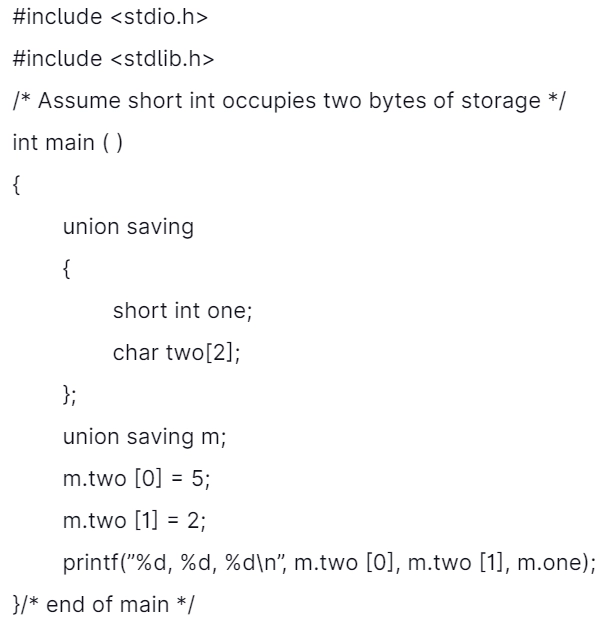
4. What is the output of the subsequent 'C' program? (Assuming little-endian representation of multi-byte data in which Least Significant Byte (LSB) is stored at the lowest memory address.)
(1) 5, 2, 1282
(2) 5, 2, 52
(3) 5, 2, 25
(4) 5, 2, 517
Answer: 4
Explanation: m.two[o] holds the value 5, and m.two[1] has the value 2; hence it will print 5 and 2 values.
The size of the short integer is 2 bytes. Saving is a union variable, we will access one variable at a time, and only one memory location is shared with every member. So the values 5 and 2 (two bytes of the data) will store in the little-endian format in the variable m.one.
Endianness is the sequential ordering in which bytes are arranged into larger numerical values stored in memory or transmitted over digital links.
In the big-endian format, whenever addressing memory or sending/storing words bytewise, the most significant byte—the byte containing the most considerable bit-is held first (has the lowest address) or sent first, then the following bytes are stored or transmitted in decreasing significance order,
The Little-endian format reverses this order: the sequence addresses/sends/stores least significant byte at first (lowest address) and most significant byte at last (highest address). The
The first 5 will store at the lowest address, and 2 will keep at the following highest address. Hence the binary representation 5 and 2 in little-endian format is 00000010 00000101. So, the binary number of the above is 517
5. Given below are three C++ implementations of the swap( ) function:
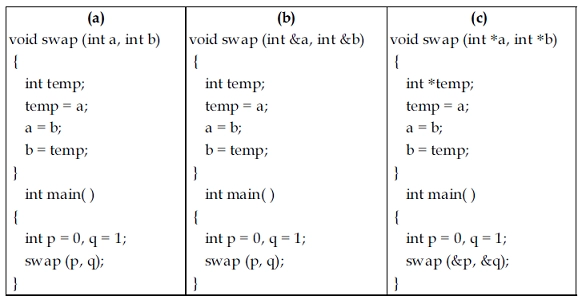
Which would swap the contents of the two integer variables p and q?
(1) (a) only
(2) (b) only
(3) (c) only
(4) (b) and (c) only
Answer: 2
Explanation: Module -(a) is called by value, so using that code, w can not swap the contents.
Module -(b) is called by reference; hence the modification of content in the function mirrors the changes in the main program. The swap operation is done in module -(b).
Module -(c) passes addresses as parameters, but in the function description, We are changing the addresses, not the content; hence swapping the values can't be done.
6. In Java, which of the subsequent statements is/are True?

Code:
(1) S1 and S2 only
(2) S1 and S3 only
(3) S2 and S3 only
(4) All of S1, S2, and S3
Answer: 1
Explanation: If a class has multiple methods with the same name but different parameters, it is called Method Overloading. The Method Overloading feature allows a class with more than one method containing the same name if the argument lists are different. So option 3 is False.
Java uses the final keyword to restrict the user. We can use the final java keyword in any context. The Final can be method, variable, and class.
A Java class can only spread one parent class. Multiple inheritances (extends) are not allowed. However, interfaces are not classes, and a class can implement more than one interface.
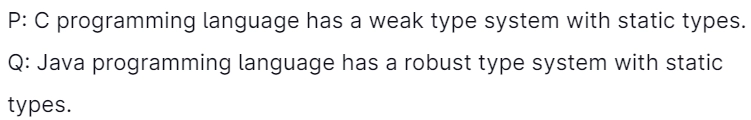
7. Which of the subsequent statements is/are True?
Code:
(1) P only
(2) Q only
(3) Both P and Q
(4) Neither P nor Q
Answer: 3
Explanation: A strongly typed language contains stricter typing rules at compile-time, implying errors and exceptions are more likely to happen during compilation. These rules affect variable assignment, function calls, and return values.
A weakly typed language includes looser typing rules and produces unpredictable results or may act as implicit type conversion at runtime.
C#, Java, Ada, and Pascal are sometimes said to be more strongly typed than C language. This claim is probably because C supports more implicit conversions, and C also allows pointer values to be explicitly cast while Pascal and Java do not.
Java is considered more strongly typed than the Pascal language. The manner of evading the static type system is controlled by the Java virtual machine's type system.
VB.NET and C# are similar to Java, though they allow disabling of dynamic type checking by explicitly placing code segments in an "unsafe context."
Pascal's type system is described as "too strong" since the size of an array or string is part of its type, creating some programming tasks very difficult.
8. Graphic display system has a frame buffer 640 pixels wide, 480 pixels high, and a 1-bit color depth. If the access time on each pixel on the average is 200 nanoseconds, then the refresh rate of this frame buffer is approximate:
(1) 16 frames per second
(2) 19 frames per second
(3) 21 frames per second
(4) 23 frames per second
Answer: 1
Explanation: Given the data,
Width (or) wide = 640 pixels
Height (or) High = 480 pixels
Color depth = 1 bit/pixel
The access time of each pixel on the average = 200ns
The refresh rate of frame buffer =?
Step 1: Graphic display system = 640*480
= 307200
Step 2: Memory required for Graphic display system =640*480*1
= 307200
Step 3: Total screen access time = Memory required for Graphic display system * Access time of each pixel
= 307200*200 ns
= 61440000 ns
Step 4: Refresh rate of frame buffer per second = (10 -9 )/61440000
= 16.27604166 frames per second
[Note: 10 - 9 = 1000000000 ]
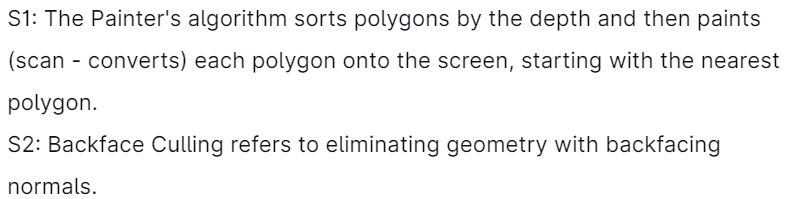
9. Which of the subsequent statements is/are True regarding the solution to the visibility problem in 3D graphics?
Code:
(1) S1 only
(2) S2 only
(3) Both S1 and S2
(4) Neither S1 nor S2
Answer: 2
Explanation: Visibility problem in 3D graphics
1. Painter's algorithm
- A depth sorting method.
- The surfaces are sorted in the order of decreasing depth.
- The surfaces are drawn in the sorted order and overwrite the pixels in the frame buffer.
- Subtle difference from the depth buffer approach: the entire face was drawn.
Two problems:
- It can be non-trivial to sort the surfaces.
- There is no solution for the sorting order.
2. Back Face Culling
- Back faces - faces of the opaque object "pointing away" from the viewer.
- Backface culling - removes back faces (supported by OpenGL).
How to detect back faces
- If we find a backface, do not draw; save rendering resources.
- There must be another forward face (s) closer to the eye.
- F is the face of the object we want to test if backface.
- P is a point on F -Form view vector, Vas (eye – P).
- N is normal to face F.
3. View-Frustum Culling
- Removes objects that are outside the viewing frustum.
- Done by 3-D clipping algorithm (e.g. Liang-Barsky).
4. Ray Tracing
- Ray tracing is another example of the image space method.
- Ray tracing: Cast a ray from the eye through each pixel to the world.
5. Z(Depth buffer algorithm)
10. Consider the matrix
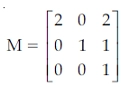
describing a set of planar (2D) geometric transformations in homogeneous coordinates. Which of the below statements about the matrix M is True?

Answer: 2
Explanation: Scale Matrix:
The scale matrix has all the exact zeros as the identity matrix, but it doesn't necessarily use the ones across the diagonal. We are trying to decide how to scale your coordinate, and you don't want the default scale value to be 1. Here is the scale matrix: {
Sx 0 0 0
0 Sy 0 0
0 0 Sz 0
0 0 0 1
}
The translation matrix examines the same as the identity matrix, but the last column slightly differs. The previous column applies an amount of change for the x, y, and z coordinates: {
1 0 0 Tx
0 1 0 Ty
0 0 1 Tz
0 0 0 1
}
11. Assume the below regarding the development of a software system P:
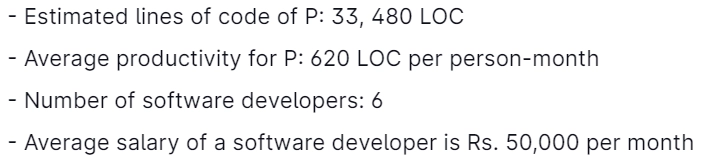
If E, D, and C be the estimated development effort (in person-months), development time (in months), and development cost (in Rs Lac), respectively, then (E, D, C) = ...............

Answer: 2
Explanation: Estimated lines of code of P: 33480 LOC
Average productivity P: 620 LOC per person-month
Number of software developers: 6
The average salary of a software developer: 50000 per month
Step 1: Estimated development effort (in person-months) = 33480/620
E = 54
Step 2: Estimated development time in months) = 54/6
D = 9 months
Step 3: Estimated development cost (in Lac) = 50000*6*9
= 27 lacs
12. Match the following in Software Engineering:
List - I
(a) Product Complexity
(b) Structured System Analysis
(c) Coupling and Cohesion
(d) Symbolic Execution
List - II
(i) Software Requirements Definition
(ii) Software Design
(iii) Validation Technique
(iv) Software Cost Estimation
Code:
(a) (b) (c) (d)
(1) (ii) (iii) (iv) (i)
(2) (iii) (i) (iv) (ii)
(3) (iv) (i) (ii) (iii)
(4) (iii) (iv) (i) (ii)
Answer: 3
Explanation: Coupling & Cohesion are used in software design. Cohesion measures the strength of a module, while coupling measures interdependency between modules.
The software cost estimation must be done more diligently throughout the project life cycle such that there are fewer surprises & unforeseen delays in the release of a product in the future.
Validation Technique, Symbolic Execution
Software Requirements Definition- Structured System Analysis
13. Which one of the subsequent is not typically provided by Source Code Management Software?
(1) Synchronisation
(2) Versioning and Revision history
(3) Syntax highlighting
(4) Project forking
Answer: 3
Explanation: The Source Code Management Software is the management of changes to documents, computer programs, large websites, and other collections of information. The changes are usually identified by a number or letter code, termed the "revision number," "revision level," or simply "revision."
Source Code Management Software includes
1. Synchronisation
2. Versioning and Revision history
3. Project forking
14. Software system crashed 20 times in 2017, and each crash took 2 minutes to restart. Approximately, what was the software available in that year?
(1) 96.9924%
(2) 97.9924%
(3) 98.9924%
(4) 99.9924%
Answer: 4
Explanation: Software availability: Software ensures that systems are running and available. High availability is the high percentage of time that the system is functioning. It can be formally defined as (1 - (downtime/ total time))*100%. Although the minimum required availability varies by task, systems typically attempt to achieve 99.999% (5-nines) availability. This attribute is weaker than fault tolerance, which typically seeks to provide 100% availability, albeit with significant price and performance penalties.
Given data,
The software crashed 20 times in the year 2017
each crash = 2 minutes to restart.
Software availability=?
1 year = 365 days(Non leap) = 365*1440 minutes = 525600 minutes.
Crash time = 2*20 = 40 minutes
Software availability = (525600-40) / 525600
= 0.999924
= (0.999924 * 100)
= 99.9924%
15.
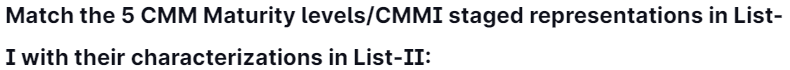
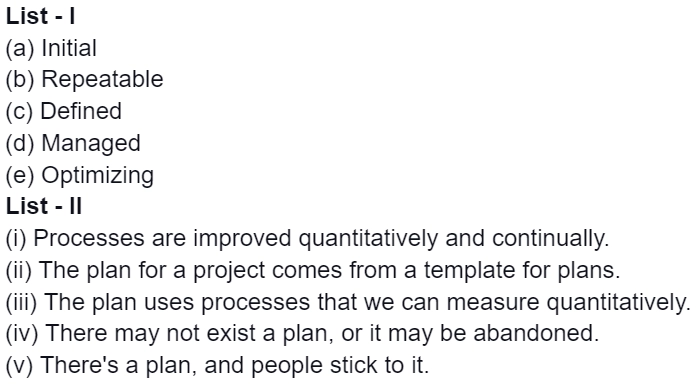
Code:
(a) (b) (c) (d) (e)
(1) (iv) (v) (i) (iii) (ii)
(2) (i) (ii) (iv) (v) (iii)
(3) (v) (iv) (ii) (iii) (i)
(4) (iv) (v) (ii) (iii) (i)
Answer: 4
Explanation:
Initial Stage: There may not exist, or it may be abandoned.
Repeatable: There is a plan, and people stick to it.
Defined: Plan for a project comes from a template for plans.
Managed: Plan uses processes that we can measure quantitatively.
Optimizing: Processes are improved quantitatively and continually.
16. Coupling measures the strength of the interconnections between software modules. Which of the following are correct statements concerning module coupling?
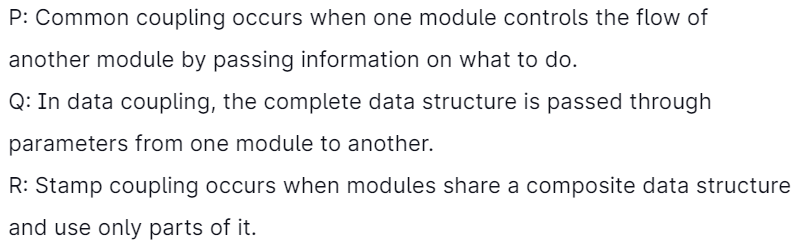
Code:
(1) P and Q only
(2) P and R only
(3) Q and R only
(4) All of P, Q, and R
Answer: 3
Explanation: Standard Coupling: Common coupling occurs if two modules share some global data.
Data Coupling: Data coupling happens when two modules communicate using elementary data items that are passed as parameters between two modules.
Stamp Coupling: Stamp coupling happens if two modules communicate using composite items such as records in Pascal or structure in C.
17. A software design pattern is often used to restrict access to an object is:
(1) adapter
(2) decorator
(3) delegation
(4) proxy
Answer: 4
Explanation: Proxy pattern is a class functioning as an interface to something else. In proxy, extra functionality can be provided, for example, caching when operations on the real object are resource-intensive or checking preconditions before operations on the real object are invoked.
Using a proxy object is similar to using the real thing for the client because both implement the same interface.
Proxy patterns solve the access to an object should be controlled, and functionality should be provided when accessing an object.
For example, when accessing sensitive objects, it should be possible to check that clients have the needed access rights.
18. Reasons to re-engineer a software include :

Code:
(1) P, R, and S only
(2) P and R only
(3) P, Q, and S only
(4) P, Q, and R only
Answer: 4
Explanation: Software re-engineering examines and alters a system to reconstitute it in a new form. We do it to improve the maintainability of the software.
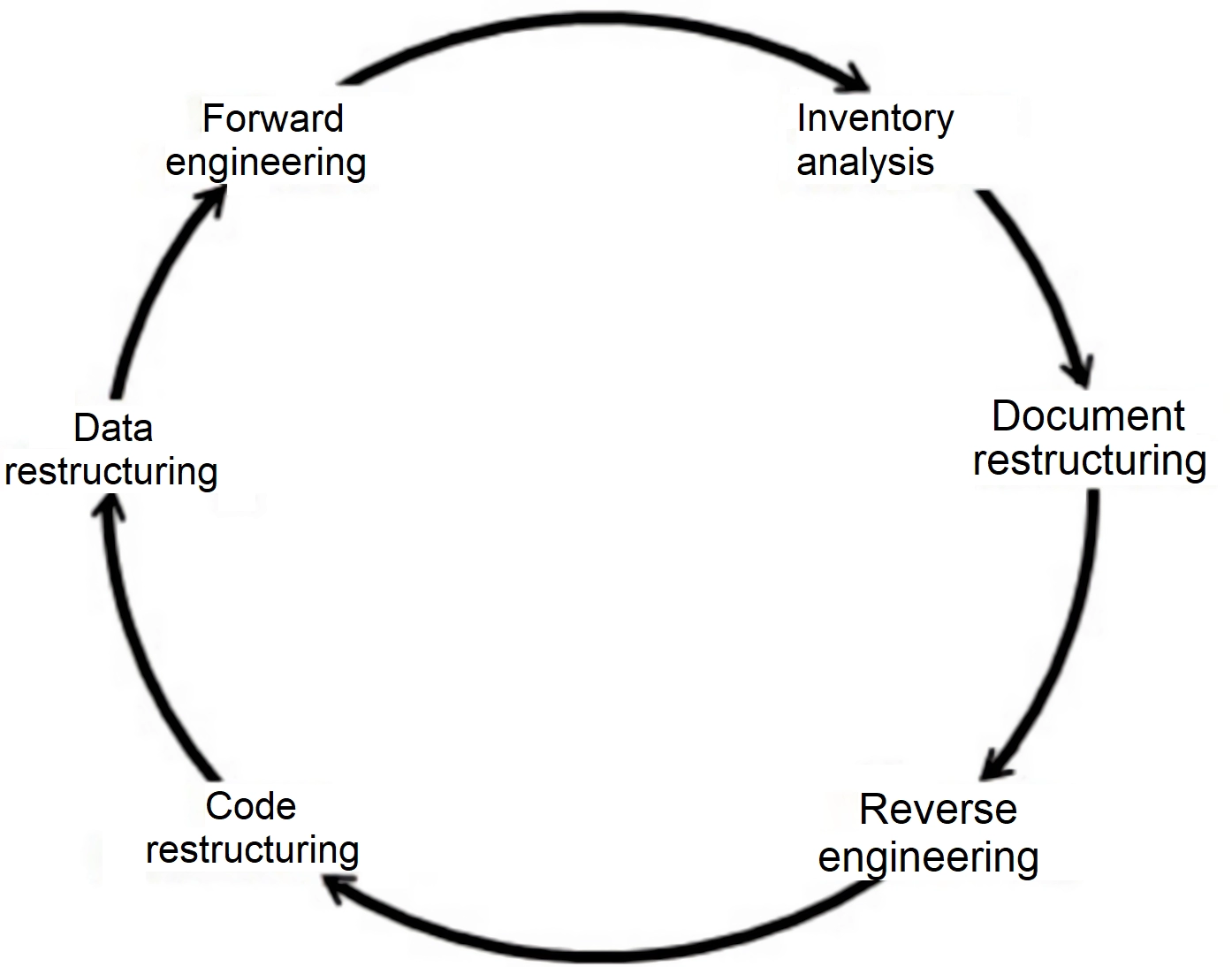
Software re-engineering encompasses inventory analysis, document restructuring, reverse engineering, program and data restructuring, and forward engineering. These activities intend to create versions of existing programs that exhibit higher quality and better maintainability.
A software re-engineering process model:
19. Which of the subsequent is not a key strategy followed by the clean room approach to software development?
(1) Formal specification
(2) Dynamic verification
(3) Incremental development
(4) Statistical testing of the system
Answer: 2
Explanation: Basic principles of the cleanroom process are:
1. Software development based on the formal methods: Software tool aid based on mathematical formalism includes model checking, process algebras, and Petri nets. The Box Structure Method may be a means of specifying and designing a software product. Team review is achieved by verifying that the design correctly implements the specification, often with software tool support.
2. Incremental implementation under statistical quality control Cleanroom development utilizes an iterative approach, in which the product is developed in increments that slowly increase the implemented functionality. The quality of each increment is calculated against pre-established standards to verify that the development process is proceeding acceptably. A failure to meet quality standards will result in the cessation of testing for the current increment and returns to the design phase.
3. Statistically sound testing in the cleanroom process is a statistical experiment. A representative subset of the software input/output trajectories is selected and tested based on the formal specification. This sample is then statistically examined to produce an estimate of the reliability of software and a level of confidence.
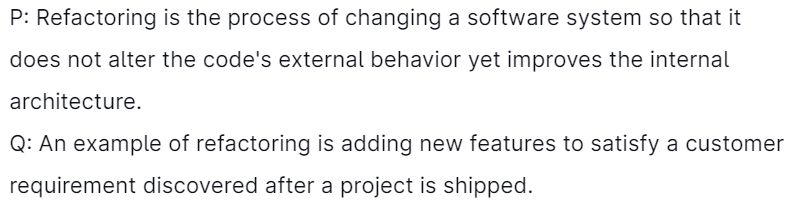
20. Which of the subsequent statements is/are True?
Code:
(1) P only
(2) Q only
(3) Both P and Q
(4) Neither P nor Q
Answer: 1
Explanation: Refactoring lets a software engineer improve the internal structure of a design (or source code) without changing the external functionality or behavior of the code yet improves the internal structure. We can use refactoring to improve a design's efficiency, readability, or performance or the code that implements a design.
Refactoring is a disciplined way to modify/simplify/clean up code that minimizes the chances of introducing bugs. In essence, when we refactor, we improve the code's creation after it has been written.
Note: It won't add new features to satisfy customers' requirements. So, statement Q is false.
21. The solution of the recurrence relation
T(m) = T(3m/4) + 1 is:
(1) θ (lg m)
(2) θ (m)
(3) θ (mlg m)
(4) θ (lglg m)
Answer: 1
Explanation: Using Master Method:
a = 1, b = 4/3, p = 0, k = 0
Here, a = b k
Hence, T(m) = n log a/ log b log p+1 n
T(m) = θ(log m)
22.
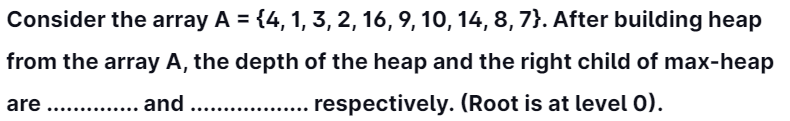
(1) 3, 14
(2) 3, 10
(3) 4, 14
(4) 4, 10
Answer: 2
Explanation:
The depth of the max-heap is 3
The right child of max-heap is 10
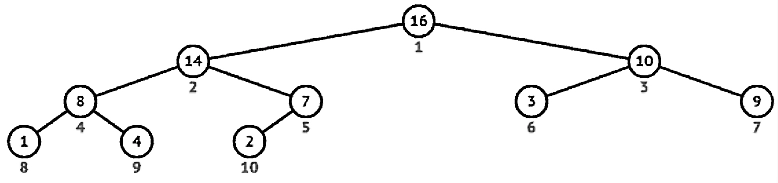
Max-heap from the array A = {4, 1, 3, 2, 16, 9, 10, 14, 8, 7}
23.

(1) 3
(2) 4
(3) 5
(4) 6
Answer: 3
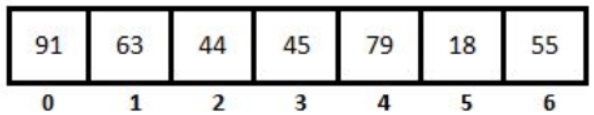
Explanation: The given hash function which uses linear probing is:
h(key) = key mod 7
h(44) = 44 mod 7 => 2
h(45) = 45 mod 7 => 3
h(79) = 79 mod 7 => 2 (collision)
h(79) = (79+1) mod 7 => 3 (collision)
h(79) = (79+2) mod 7 => 4
h(55) = 55 mod 7 => 6
h(91) = 91 mod 7 => 0
h(18) = 18 mod 7 => 4 (collision)
h(79) = (18+1) mod 7 => 5
h(63) = 63 mod 7 => 0 (collision)
h(63) = (63+1) mod 7 => 1
Now the array has keys 44, 45, 79, 55, 91, 18, and 63 at locations
24. Which of the below algorithms solves the single-source shortest paths?
(1) Prim's algorithm
(2) Floyd - Warshall algorithm
(3) Johnson's algorithm
(4) Dijkstra's algorithm
Answer: 4
Explanation: The Dijkstra's algorithm is a single source shortest path algorithm used to find the shortest path using the Greedy approach.
25. A text comprises the characters A, B, C, D, and E, each occurring with the probability of 0.08, 0.40, 0.25, 0.15, and 0.12, respectively. The optimal coding technique will have the average length of:
(1) 2.4
(2) 1.87
(3) 3.0
(4) 2.15
Answer: 4
Explanation:
A = 1000 (4-bits)
E = 1001 (4-bits)
D = 101 (3-bits)
C = 11 (2-bits)
B = 0 (1-bit)
Average length = ((0.08x4)+(0.12x4)+(0.15x3)+(0.25x2)+(0.40x1))/(0.08+0.12+0.15+0.25+0.40)
= 2.15/1.0
= 2.15





