
Introduction
The NET(National Eligibility Test) is executed on behalf of the University Grants Commission (UGC) to decide the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Colleges and Universities.
This article discusses the previous year's UGC-NET computer science questions of June 2009 Paper II. We will see these questions along with their answers and explanation.
Questions
1. If x & y are independent Gaussian random variables with an average value of 0 and with the same variance, their joint probability density function is given by:
(A) p(x,y) = p(x).p(y)
(B) p(x,y) = p(x)+p(y)
(C) p(x,y) = p(x+y)
(D) p(x,y) = p(x).p(y)+p(x)
Answer: C
Explanation: Since they are Independent, Answer could be option A, though it needs to be checked with zero average.
Note: Original key has option C as correct.
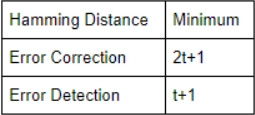
2. In order for a code is ‘t’ error-correcting, the minimum Hamming distance should be:
(A) t
(B) 2t - 1
(C) 2t
(D) 2t + 1
Answer: D
Explanation:
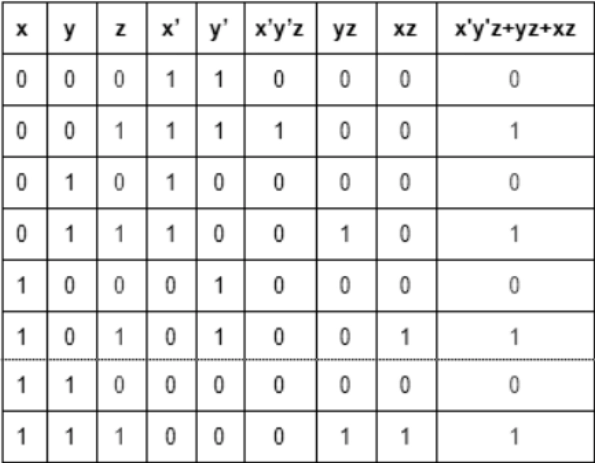
3. The following Boolean expression is equivalent to:
x’y’z + yz + xz
(A) x
(B) y
(C) z
(D) x + y + z
Answer: C
Explanation:
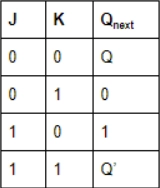
4. The characteristic equation of the JK flip flop is:
(A) Qn+1 = J.Qn+K.Qn
(B) Qn+1 = J.Q’n+K’.Qn
(C) Qn+1 = QnJ.K
(D) Qn+1 = (J+K)Qn
Answer: B
Explanation: The characteristic equation of JK flip flop is Qn+1 = J.Q’n+K’.Qn.
5. To implement an n variable switching function, a MUX must have:
(A) 2n inputs
(B) 2n + 1 input
(C) 2n - 1 input
(D) 2n - 1 input
Answer: A
Explanation: To implement an n variable switching function, a MUX must have 2n inputs.
6. The throughput of a pure ALOHA is given by:
(A) S = G
(B) S = e2G
(C) S = Ge2G
(D) S = Ge-2G
Answer: D
Explanation: The throughput value of pure ALOHA is given by S = Ge-2G
7. The Fiber Distributed Data Interface uses:
(A) single-mode fibers and LEDs
(B) multimode fibers and LEDs
(C) single-mode fibers and ILDs
(D) multimode fibers and ILDs
Answer: B
Explanation: The FDDI uses a multimode fiber because single-mode fiber costs are not justified for networks running at only 100 Mbps.
It also uses LEDs Instead of lasers because of the lower cost. We sometimes may use FDDI to connect directly to the user workstations, and safety against exposure to the LASER radiation is difficult to maintain.
8. To use multi-access in GSM, users are given differently:
(A) time slots
(B) bandpass filters
(C) handsets
(D) frequency bands
Answer: D
Explanation: To utilize multi-access in GSM, users are given different frequency bands.
9. With four programs in memory and with an 80% average I/O wait, the CPU utilization is?
(A) 60%
(B) 70%
(C) 90%
(D) 100%
Answer: A
Explanation: Given data:
Average I/O wait = 80%
Total programs in memory = 4
CPU utilization =?
The standard formula for finding CPU utilization is 1-pn,
Where n is the number of processes and p is the waiting time for I/O.
CPU utilisation = 1 - 0.84
= 1 - 0.4096
= 0.5904
10. Assume N segments in memory & a page size of P bytes. The wastage on the account of internal fragmentation is:
(A) NP/2 bytes
(B) NP bytes
(C) N/2 bytes
(D) P/2 bytes
Answer: A
Explanation: NP/2 Bytes is the wastage on account of internal fragmentation.
Where N segments in memory and P Bytes is the page size.
11.
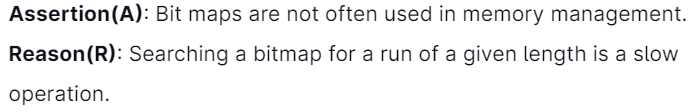
(A) Both (A) & (R) are true, and (R) is the correct explanation for (A)
(B) Both (A) & (R) are true, but (R) is not the correct explanation for (A)
(C) (A) is true, (R) is false
(D) (A) is false, (R) is true
Answer: A
Explanation: We do not often use Bitmaps in memory management since searching a bitmap for a run of a given size is a slow operation.
12. The complete graph with four vertices contains k edges where k is:
(A) 3
(B) 4
(C) 5
(D) 6
Answer: D
Explanation: The standard formula to find the number of edges in a complete graph is n(n-1)/2.
Since, n = 4
= 4(4 - 1)/2
= (4*3)/2
= 12/2
= 6
13. The octal equivalent of hexadecimal (A.B)16 is:

Answer: B
Explanation:
Converting into binary: (1010.1011)16
Converting into octal: (12.54)8
14. A reduced state table contains 18 rows. The minimum amount of flip flops needed to implement the sequential machine is:
(A) 18
(B) 9
(C) 5
(D) 4
Answer: C
Explanation: The Mod value of a counter is the number of unique states.
Let K = Number of states = 18.
The number of flip-flops is the least number which is greater than or equal to L log2K
log218 = 4.1
L=5>=4.1
So the number of flip-flops needed is 5.
15. After executing the subsequent code statements, what is the value of 'b'?
C=10;
B=++c+++c;
(A) 20
(B) 22
(C) 23
(D) None
Answer: D
Explanation: It will give an error message because they are not given in proper syntax. Suppose when we are taken (++C)+(++C);
It will result in 23 because pre/post increment will evaluate from right to left.
(++C)+(++C); /* Increments by one, it means 11 */
(++C)+(++C); /* earlier c=11 and now incrementing by 1. It will become 23. */
16. Which of the below does not represent a valid storage class in ’c’?
(A) automatic
(B) static
(C) union
(D) extern
Answer: C
Explanation: Storage classes auto, static, register, and extern. Union is not a storage class.
17. A friend function is used in situations where:

Answer: C
Explanation: The friend function of a class is determined outside that class scope, but it has the right to access all protected and private components of the class. Though the prototypes for friend functions occur in the class definition, friends are not member functions.
- A function can only be declared as a friend by a class itself.
- It can access all class members, even private ones.
18.
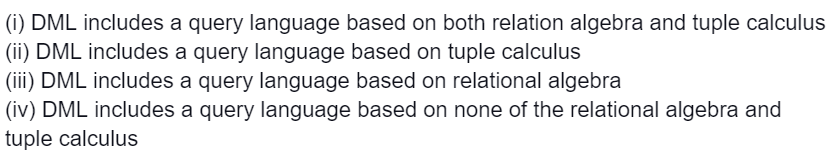
Which one is correct?
(A) (i) only
(B) (ii) only
(C) (iii) only
(D) (iv) only
Answer: A
Explanation: DML(Data manipulation language ) performs SELECT, UPDATE, INSERT and DELETE operations.
DML contains a query language based on both relation algebra and tuple calculus.
19. Suppose it takes about 100 ns to access a page table and 20 ns to access the associative memory with a 90% hit rate, the average access time equals:
(A) 20 ns
(B) 28 ns
(C) 90 ns
(D) 100 ns
Answer: B
Explanation: Given data,
- Access page table time = 100 ns
- Associate memory = 20 ns
- hit ratio = 90% = 0.9
- Miss ratio = 1 - hit ration
= 10% = 0.1
- Average Access Time = ?
Average access time = Hit Ratio*Access page table + Miss Ratio * Associate memory
= 0.9 * 20 + 0.1 * 100
= 28 ns
20. There exists a construct that returns a value ‘true’ if the argument subquery is:
(A) empty
(B) non-empty
(C) in error
(D) none of the above
Answer: B
Explanation: The existing construct returns the value true if the argument subquery is non-empty.
1. exists r ⇔ r = Φ
2. not exists r ⇔ r = Φ
21. Which construct in SQL tests whether a subquery has any tuples in its result?
(A) UNIQUE
(B) EXISTS
(C) GROUP BY
(D) EXCEPT
Answer: B
Explanation: EXISTS: We use this function in SQL to check whether the result of a correlated nested query is empty (includes no tuples) or not.
UNIQUE: UNIQUE(Q) returns TRUE if there are no duplicate tuples in the query result; otherwise, it returns FALSE. We can use this to test whether the result of a nested query is a set or a multiset.
GROUP BY: This clause specifies the grouping attributes, which should also appear in the SELECT clause. The resulting value from applying each aggregate function to a group of tuples seems along with the value of the grouping attribute(s).
EXCEPT: This query is like the set difference operation in SQL. The dissimilarity between EXCEPT and EXCEPT ALL is EXCEPT does not allow duplicates while EXCEPT ALL allows copies in the result of a query.
Hence the correct option is (B).
22. ORACLE supports:
(A) inner join and outer join only
(B) outer join and semi-join only
(C) inner join, outer join, semi-join only
(D) inner join, outer join, semi-join, and anti join
Answer: D
Explanation: Oracle supports all of the above joins, i.e., Inner join, outer join, semi-join, and anti join.
23. Which two below are equivalent for an undirected graph G?
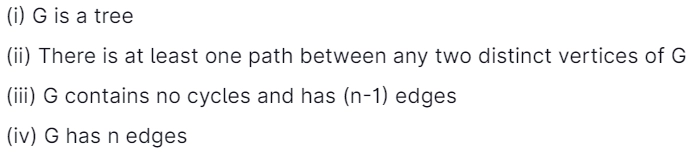
(A) (i) and (ii)
(B) (i) and (iii)
(C) (i) and (iv)
(D) (ii) and (iii)
Answer: D
Explanation:
Option-A: FALSE because the undirected graph will be a cycle also.
Option-B: TRUE since there is at least one path between any two distinct vertices of G. otherwise, we are not calling an undirected graph.
Option-C: TRUE. If G has no cycles and has (n-1) edges.
Option-D: FALSE
24. In a B tree of order m with p nodes, the average number of splits is at most:

Answer: B
Explanation: Leaf Nodes = p,
keys = m,
To split the node, assume that following the insertion of the new key, p has the format m, Ao,(K1,41), ... , (Km,Am), and Kii+1, 1<=i The node is split into two nodes, p and q, with the following formats:
node p: [(m/2)1-1, A.(K141</sub>), ..., (Kr(m/2)1-1, Ar(m/2)-1)
node q: m-[(m/2)], As(m/2)], (Kf(m/2)1+1, Af(m/2)1+1), ..., (Km,Am)
The remaining key, K (m/2),-1, and a pointer to the new node,q, from a tuple(K/(m/2)1,9).
This is to be inserted into the parent of p. Before attempting this, the nodes p and q are written to disk.
25. The tree gives the prepositional formula:
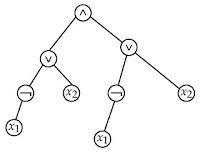
is:
(A) ˄˅x2˅x1¬x1¬x1
(B) (x2˅¬x2)˄(x1˅x2)
(C) (¬x1˅x2)˄(¬x1˅x2)
(D) None
Answer: C
Explanation: By default, we use inorder traversal for evaluation.
Inorder traversal starts from left, root, and right.
Inorder traversal = (¬x1˅x2)˄(¬x1˅x2)




