
Introduction
The NET(National Eligibility Test) is executed on behalf of the University Grants Commission (UGC) to decide the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Colleges and Universities.
This article discusses the previous year's UGC-NET computer science questions of June 2009 Paper II. We will see these questions along with their answers and explanation. Before going through the article, refer to June 2009 Paper II - Part 1.
Questions
26. Queue is a ............. list.
(A) LIFO
(B) LILO
(C) FILO
(D) FIFO
Answer: D
Explanation: The queue is FIFO(First In First Out), and the stack is LIFO(Last In First Out).
27. In a full binary tree of height h, there are ................. internal nodes.
(A) 2h-1
(B) 2h-1
(C) 2h
(D) 2h+1
Answer: A
Explanation:
- In a full binary tree of height h, there are 2h-1 internal nodes.
- A Binary Tree is full if each node has zero or two children.
- In a Full Binary, the number of leaf nodes is one of the internal nodes plus 1.
L = 1 + 1
Where,
L = Number of leaf nodes,
I = Number of internal nodes.
28. A binary tree has heap property if the elements along any path:
(A) from leaf to root are non-increasing
(B) from leaf to root are non-decreasing
(C) from root to leaf are non-decreasing
(D) from root to leaf are non-increasing
Answer: D
Explanation: A heap tree is a complete binary tree. A binary is said to have heap property if the elements along any path from the root to leaf are non-increasing.
29. X.25 protocol consists of:
(A) Physical and Frame levels
(B) Frame and Packet levels
(C) Physical, Frame, and Packet levels
(D) None of the above
Answer: C
Explanation:
- X.25 initially defined three basic protocol levels of architectural layers.
- Physical layer(bits)
- Data-link layer(frames)
- Network layer(packet)
- X.25 protocol has Physical, Frame, and Packet levels.
30. GSM/CDMA systems:
(A) are limited to very low-speed data
(B) require no local loop wires
(C) are predominantly used for voice
(D) all of the above
Answer: C
Explanation: GSM offers a very low-speed data service because mobility management in a vast area network is the main focus of GSM. GSM/CDMA systems are primarily used for voice.
31. Generally, information security in a network is achieved by:

Answer: B
Explanation: Usually, the information security in a network is achieved by cryptography because very difficult to decrypt messages.
32. The linker:
(A) is similar to an interpreter
(B) uses source code as its input
(C) is required to create a load module
(D) none of the above
Answer: C
Explanation: The linker is needed to create a load module. Object modules generated by the assembler that contains unresolved external references are resolved for two or more object modules by a Linker.
33. In which addressing mode is the operand given explicitly in the instruction?
(A) Absolute mode
(B) Immediate mode
(C) Indirect mode
(D) Index mode
Answer: B
Explanation: The operand is given explicitly in the instruction in immediate addressing mode.
34. A compiler that runs on a machine and produces code for a separate machine is called:
(A) Cross-compilation
(B) One pass compilation
(C) Two-pass compilation
(D) None of the above
Answer: A
Explanation: Cross compiler: The compiler is used to compile a source code for different platforms.
Note: We have one and two pass assemblers but not compilers.
35. Any syntactic construct that a regular expression can describe can also be characterized by a:
(A) Context-sensitive grammar
(B) Non-context-free grammar
(C) Context-free grammar
(D) None of the above
Answer: C
Explanation: The Context-free Grammar (CFG) can be recognized by finite-state Automata and linear bounded automata(LBA).
36. Find the odd man out:
(A) tail
(B) cut
(C) wart
(D) sed
Answer: C
Explanation: The tail, cut, and sed belongs to one category. A virus causes the wart. So, it is an odd one.
37. Which of the below changes permission to deny write permission to group and others?
(A) Chmod go-w filex
(B) Chmod go w filex
(C) Chmod go=w filex
(D) None of the above
Answer: A
Explanation: Key terms in chmod command:
'+' to add permissions.
'-' to remove permissions.
'=' to assign permissions absolutely.
'r' to read permission
'w' to write permission
'x' to execute permissions
'g' to group permissions
'o' to others permissions
chmod go -w filex - Removing write permission to group and others.
chmod go=w filex - Giving all rwx permissions to groups and others.
38.
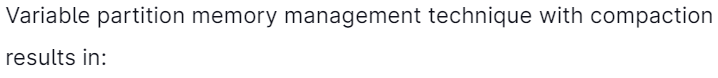

Answer: A
Explanation: Variable partition memory management technique with compaction results in reducing fragmentation.
39. Capability Maturity Model is meant for:
(A) Product
(B) Process
(C) Product and Process
(D) None of the above
Answer: B
Explanation: CMM stands for Capability Maturity Model, a process model that specifies the process improvement approach in software development.
CMM levels:
1. Initial
2. Repeatable
3. Defined
4. Managed
5. Optimizing
40. 

Answer: D
Explanation: It consists of programs, data, and documentation.
41. Which one of the following ISO standards is used for the software processes?
(A) ISO 9000
(B) ISO 9001
(C) ISO 9003
(D) ISO 9000-3
Answer: D
Explanation: The ISO 9003 is "Quality systems-Model for quality assurance in final inspection and test". ISO 9001 is a non-industry-specific certification. ISO 9000 series refers to the family of standards containing ISO 9000, ISO 9001, ISO 9004, and ISO 19011.
42. Which of the subsequent is used for test data generation?
(A) White box
(B) Black box
(C) Boundary-value analysis
(D) All of the above
Answer: C
Explanation: Boundary testing is a process of testing between extreme ends or boundaries between partitions of the input values. It is used to test data generation.
43. Reverse engineering is the process that deals with:
(A) Size measurement
(B) Cost measurement
(C) Design recovery
(D) All of the above
Answer: C
Explanation: Design recovery from source code is made during reverse engineering, re-engineering, and reusability.
44. The spacing between the character pairs is called:

Answer: A
Explanation: Kerning is the method of adjusting the spacing between characters in a proportional font, usually to achieve a visually pleasing result. It alters the space between individual letter forms, while tracking (letter-spacing) adjusts spacing uniformly over a range of characters.
45. When compared with the analog cellular systems, an advantage of the digital TDMA cellular system is that:
(A) it is less complicated
(B) it requires less computer memory
(C) it conserves spectrum bandwidth
(D) it costs less
Answer: C
Explanation: Compared with analog cellular systems, an advantage of the digital TDMA cellular system is that it conserves spectrum bandwidth.
46. E-commerce includes:
(A) B2C
(B) B2B
(C) C2C
(D) All of the above
Answer: D
Explanation: E-commerce includes:
Consumer-to-business (C2B) - is a business model in which consumers (individuals) create value, and businesses consume that value.
Business-to-government (B2G) (or) "public sector marketing" - This encloses marketing products and services to various government levels through combined marketing communications techniques such as strategic public relations, branding, marketing communications (Marcom), advertising, and web-based communications.
Customer-to-customer (C2C) - It markets provide an innovative way to allow customers to interact with each other.
Business-to-business (B2B) is when one business makes a commercial transaction with another.
47. A clustering technique that allows a convenient graphical display is:
(A) partition-based clustering
(B) probabilistic model-based clustering
(C) hierarchical clustering
(D) agglomerative clustering
Answer: C
Explanation: Hierarchical methods of cluster analysis permit a convenient graphical display in which the entire sequence of merging(or splitting), because of its tree-like nature, the display has the name the dendrogram.
Types:
1. Agglomerative: It is a "bottom-up" approach: each observation starts in its cluster, and pairs of clusters are combined as one progresses up the hierarchy.
2. Divisive: It is a "top-down" approach. All observations begin in one cluster and then splits are performed recursively as one moves down the hierarchy.
48. After sending the message, the sender should not be able to, at a later date, deny having sent the message, which is referred to as:
(A) Authenticity
(B) Non-Repudiability
(C) Auditability
(D) Repudiability
Answer: B
Explanation: After sending the message, the sender should not be able to deny having sent the message at a later date, which is referred to as Non-Repudiation.
49. The device which combines dissimilar LANs of different topologies using different sets of communication protocols so that the data can flow from one to another is called:
(A) Router
(B) Bridge
(C) Gateway
(D) Switch
Answer: C
Explanation: Gateway permits data to flow from one discrete network to another. They are distinct from routers or switches. They communicate using many protocols and can work at any of the seven layers of the open systems interconnection model (OSI).
50. We cannot delete the .................. icon, but we can make it invisible.
(A) Recycle
(B) My Computer
(C) Internet explorer
(D) None of the above
Answer: A
Explanation: We cannot delete the recycle icon, but we can make it invisible and delete my computer and internet explorer icon completely.
Must Read: Difference Between Compiler and Assembler




