
Introduction
The NET(National Eligibility Test) is executed on behalf of the University Grants Commission (UGC) to decide the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Colleges and Universities.
This article discusses the previous year's UGC-NET computer science questions of June 2010 Paper II. We will see these questions along with their answers and explanation. Before going through the article, refer to June 2010 Paper II - Part 1.
Questions
26. The …………… field is the SNMP PDV registers an error in a response message.
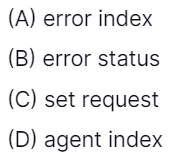
Answer: B
Explanation: SNMP PDU stands for Simple network management protocol protocol data units
Have many fields.

- Error status: Indicates one of several errors and error types. Only the response operation sets this field. Other operations set this field to zero.
- Error index: Associates an error with a particular object instance. Only the response operation sets this field. Other operations set this field to zero.
27. What does the URL require to access documents?
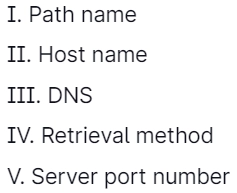

Answer: B
Explanation: The URLs need to access documents are Path name, DNS, and server port number.
28. End-to-End connectivity is supplied from Last-to-Last in

Answer: C
Explanation:
- Data link layer - Process to Process connectivity
- Network layer - Host to Host connectivity
- Transport layer - End to End connectivity
- Presentation layer - Encryption and Decryption
29. What services does the internet layer deliver?

(A) 1, 2, 3
(B) 2, 3, 4
(C) 1, 3, 4, 5
(D) 2, 3, 4, 5
Answer: A
Explanation: Internet Protocol provides Quality of Service, Routing, and Addressing. It does not provide a Connection-oriented service, and Framing is the responsibility of the data link layer.
30. What is the highest operating rate of a wireless LAN using infrared communication?

Answer: A
Explanation: The highest operating rate of a wireless LAN utilizing infrared communication is 1 Mbps.
31. In a whole loading scheme, which loader accomplishes the loader function?
(A) Re-allocation
(B) Allocation
(C) Linking
(D) Loading
Answer: D
Explanation: The loader loads the executable code into memory, the program and data stack are created, register gets initialized.
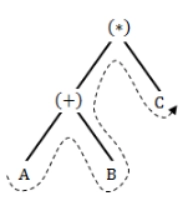
32. Which of the subsequent expression is represented by the parse tree?


Answer: A
Explanation: The parse tree is always following inorder traversal. It visits left, root and right.
33. Consider the following left-associative operators in decreasing order of precedence:

What is the result of the subsequent expression?
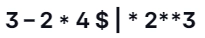
(A) – 61
(B) 64
(C) 512
(D) 4096
Answer: D
Explanation: They are given in the wrong order.
But according to given question, the giving precedence is
(((3 - 2) *) 4 $ / * (2**3))
Step 1: 3 - 2 = 1
Step 2: 1 * 4 = 4
Step 3: 2 * 3 = 6
Step 4: 46 = 4096
Note: When we assume ** is single(*) and there is no l* are useless symbols.
34. Which of the below is the most general phase of structured grammar?
(A) Regular
(B) Context-sensitive
(C) Context-free
(D) None of the above
Answer: B
Explanation: Phrase structure grammar is also known as constituency grammar. Therefore, the defining trait of phrase structure grammars is their adherence to the constituency relation, as objected to the dependency relation of dependency grammars.
The most general phase of structured grammar is context-sensitive grammar.
35. Which of the below is used to group characters into tokens (in a computer)?
(A) A parser
(B) Code optimizer
(C) Code generator
(D) Scanner
Answer: D
Explanation: Lexical analysis(or Scanner) is used for grouping characters into tokens.
36. Match the following:
Set-I
(a) Disk scheduling
(b) Batch processing
(c) Time sharing
(d) Interrupt processing
Set-II
1. Round-robin
2. SCAN
3. LIFO
4. FIFO
Codes :
(a) (b) (c) (d)
(A) 3 4 2 1
(B) 4 3 2 1
(C) 2 4 1 3
(D) 1 4 3 2
Answer: C
Explanation:
Disk Scheduling - SCAN
Batch Processing - FIFO
Time-Sharing - Round-robin
Interrupt Processing - LIFO
37. ………….. synchronizes critical resources to prevent deadlock.
(A) P-operator
(B) V-operator
(C) Semaphore
(D) Swapping
Answer: C
Explanation: The semaphore synchronizes critical resources to prevent deadlock.
38. …………….. is one of the pre-emptive scheduling algorithms.
(A) RR
(B) SSN
(C) SSF
(D) Priority-based
Answer: A
Explanation: Round Robin(RR) is a preemptive scheduling algorithm. Priority-based scheduling is non-preemptive.
39. To allow only one process to enter its critical section, binary semaphores are initialized to
(A) 0
(B) 1
(C) 2
(D) 3
Answer: B
Explanation: To allow just one process to enter its critical section, binary semaphores are initialized to 1. It will change its state after entering the vital area. It will be 0.
40. Remote Computing Service implicates the use of time-sharing and …………..
(A) multi-processing
(B) interactive processing
(C) batch processing
(D) real-time processing
Answer: C
Explanation: The Remote Computing Service involves using time-sharing and batch processing.
41. Software engineering primarily aims at
(A) reliable software
(B) cost-effective software
(C) reliable and cost-effective software
(D) none of the above
Answer: C
Explanation: Software engineering primarily aims at reliable and cost-effective software.
42. Top-down design does not require
(A) step-wise refinement
(B) loop invariants
(C) flow charting
(D) modularity
Answer: B
Explanation: The top-down design does not require loop invariants.
The loop invariant is a condition that is necessarily true immediately before and immediately after each iteration of a circle.
43. Which model is the simplest in Software Development?
(A) Waterfall model
(B) Prototyping
(C) Iterative
(D) None of these
Answer: A
Explanation: The waterfall model is the simplest and oldest software development life cycle model.
44. Design phase will usually be
(A) top-down
(B) bottom-up
(C) random
(D) center fringing
Answer: A
Explanation: The design phase will usually be in the top-down approach.
45. Applications-software
(A) is used to control the operating system
(B) includes programs designed to help programmers
(C) performs a specific task for computer users
(D) all of the above
Answer: C
Explanation: Applications software performs a special task for computer users.
46. The cost of a network is usually determined by

Answer: B
Explanation: The cost of a network is usually determined by switching complexity.
47.

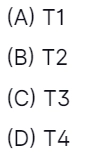
Answer: A
Explanation:
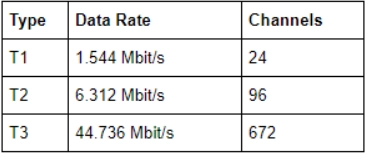
48. CDMA Cell utilizes …………… carriers of 1.25 MHz.
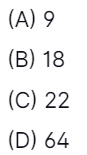
Answer: A
Explanation: A CDMA system has a 1.25 MHz wideband carrier.
- Carrier bandwidth in AMPS is 30 kHz
- Carrier bandwidth in GSM is 200 kHz
- Carrier bandwidth in IS - 95 is 1.23 MHz
- 1.25MHz with a guard band
- The recommended guard band between the CDMA carrier band edge and an AMPS or TDMA carrier is 270 KHz= 9 AMPS channels of 30 kHz.
49. At any given time, PVM (Parallel Virtual Machine) has ……………. send buffer and …………… receive buffer.

Answer: B
Explanation: PVM(Parallel Virtual Machine): It is a software package that lets a heterogeneous collection of workstations (host pool) function as a single high-performance parallel machine (virtual). A parallel Virtual Machine (PVM) has one send buffer and two receive buffers at any time.
50. Data Mining uses ………….., …………….. and …………….. to build an effective predictive model.
(i) Data set
(ii) Information set
(iii) Input set
(iv) Process set
(v) Output set
(vi) Test set
(A) (i), (ii) and (iv)
(B) (ii), (iv) and (v)
(C) (i), (v) and (vi)
(D) (ii), (iii) and (v)
Answer: A
Explanation: Data Mining utilizes data set, information set, and process set to build an effective predictive model.





