Introduction
The UGC NET, also known as the NTA-UGC-NET, is an examination used to determine eligibility for assistant professorships and Junior Research Fellowships at Indian universities and colleges. The National Testing Agency administers the exam on behalf of the University Grants Commission.
Now we will look at some of the questions that came in UGC NET June 2012 Paper III.
Also check June 2012 Paper III-Part 1 here.
Questions with Solutions
1. The equivalent grammar to the given grammar
G: S → aA, A → BB,
B → aBb | ∈ is
(A) S → aA, A → BB, B → aBb
(B) S → a|aA, A → BB, B → aBb | ab
(C) S → a | aA, A → BB | B, B → aBb
(D) S → a |aA,A→ BB | B, B→ aBb | ab
Solution) S → a |aA,A→ BB | B, B→ aBb | ab2
Explanation)

2. Which of the following assertions is not true?
(A) The cyclomatic complexity is proportional to the number of regions.
(B) The cyclometric complexity of a flow graph G is V(G) = N – E + 2, where E is the number of edges in the flow graph and N is the number of nodes.
(C) For a flow graph G, cyclomatic complexity is V(G) = E – N + 2, where E is the number of edges and N is the number of nodes in the flow graph.
(D) For a flow graph G, cyclomatic complexity is V(G) = P + 1, where P is the number of predicate nodes in G.
Solution) (B)
Explanation)
Cyclomatic complexity is a software statistic (measurement) that indicates a program's complexity.
E - N + P Equals cyclomatic complexity where,
E is the flow graph's edge count.
The number of nodes in the flow graph is denoted by N.
P is the number of nodes with exit points.
3. Consider a weighted undirected graph with positive edge weights, and consider (u, v) as a graph edge. The shortest path from source vertex s to you weighs 53, while the shortest path from s to v weights 65. Which of the following statements is always true?
(A) Weight (u, v) < 12
(B) Weight (u, v) = 12
(C) Weight (u, v) > 12
(D) Weight (u, v) > 12
Solution) Weight (u, v) > 12
Explanation)

The minimum weight happens when (S,U) + (U,V) = (S,V)
Else (S,U) + (U,V) >= (S,V)
Given (S,U) = 53, (S,V) = 65
53 + (U,V) >= 63
(U,V) >= 12
4.Take the regular expression (a + b)(a + b) … (a + b) (n-times). In finite automata, the smallest number of states that recognize the language represented by this regular expression is
(A) n states
(B) n + 1 states
(C) n + 2 states
(D) 2n states
Solution) n + 1 states
Explanation)

5.The total number of binary trees with 5 nodes is
(A) 32
(B) 36
(C) 120
(D) 42
Solution) 42
Explanation)
No of Binary Tree Possible with 5 Nodes is
2nCn / n+1 ===> 10C5 / 6 ===> 10! / 5!*5!*6==>10! / 5!*6! ===>42
6. Is the product we're making the right one?
This remark is about
(A) Verification
(B) Validation
(C) Testing
(D) Software quality assurance
Solution) Validation
Explanation)

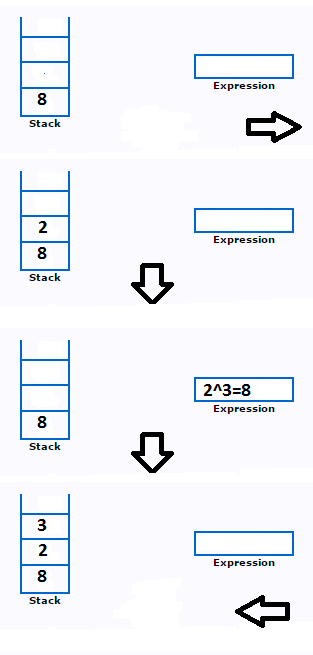
7. A stack is used to evaluate the following postfix expression: 823/23* + 51* –
After the initial *, the top two components of the stack are evaluated.
(A) 6, 1
(B) 5, 7
(C) 3, 2
(D) 1, 5
Solution) 6, 1
Explanation)


8. The following CFG
S → aB | bA,
A → a | as | bAA,
B → b | bs | aBB
generates strings of terminals that have
(A) odd number of a’s and odd number of b’s
(B) even number of a’s and even number of b’s
(C) equal number of a’s and b’s
(D) not equal number of a’s and b’s
Solution) equal number of a's and b's
Explanation) S → aB | bA,
A → a | as | bAA,
B → b | bs | aBB
generates strings of terminals that have equal number of a's and b's .
9.Take a look at the following pseudo-code:
If (A > B) and (C > D)
then A = A + 1
B = B + 1
Endif
The pseudo-cyclomatic code's complexity is
(A) 2
(B) 3
(C) 4
(D) 5
Solution) 3
Explanation)
The number of decision points (i.e., "if" statements or conditional loops) contained in every structured programme with just one entrance point and one exit point is equal to the number of decision points (i.e., "if" statements or conditional loops) plus one. This is only true for decision points counted at the lowest level of machine instructions. Decisions involving compound predicates, such as those found in high-level languages like IF cond1 AND cond2 THEN..., should be counted in terms of the predicate variables involved, i.e., in this example, two decision points should be counted, because it is equivalent to IF cond1 THEN IF cond2 THEN....
Cyclomatic complexity can also be applied to a programme having numerous exit points, in which case it equals:
s + 2, where s is the number of exit points and d is the number of decision points in the programme.
10. The ICMP (Internet Control Message Protocol) is used by which layer of the OSI reference model?
(A) Transport layer
(B) Data link layer
(C) Network layer
(D) Application layer
Solution) Network layer
Explanation)

11.The regular expression for the following DFA is

(A) ab*(b + aa*b)*
(B) a*b(b + aa*b)*
(C) a*b(b* + aa*b)
(D) a*b(b * + aa*b)*
Solution) a*b(b * + aa*b)*
Explanation)
Option 1: (a, ba)* b
string 'b' is accepted by regular expression (a, ba)* b which is not ending with aa. Therefore, it is not ending with aa.
Option 2: (a, b)* aa
L = {aa, aaa, baa, aaaa, abaa, baaa, bbaa ... }
Every string in language is ending with aa. Therefore, it is ending with aa.
Hence option 2 is correct.
Option 3: (a, b) + b
string 'b' is accepted by regular expression (a, b) + b which is not ending with aa. Therefore, it is not ending with aa
Option 4: (aa, ab) * a
string 'a' is accepted by regular expression (a, b) + b which is not ending with aa. Therefore, it is not ending with aa.
12. A computer system can support both virtual and physical addresses of 32 bits. Which of the following is true if we want to remove virtual memory since the virtual address space is the same size as the physical address space?
(A) Efficient implementation of multi-user support is no longer possible
(B) The processor cache organization can be made more efficient now
(C) Hardware support for memory management is no longer needed
(D) CPU scheduling can be made more efficient now
Solution) Hardware support for memory management is not needed.
Explanation)
Virtual memory provides-
- increased address space for processes
- memory protection
- relocation
So, even if we eliminate virtual memory because we don't require extra address space, we still need hardware support for the other two. We can create a system without hardware support for memory protection and relocation (by implementing them in software or partitioning the memory for separate users), but those are wasteful approaches. That is, we must split the physical memory equally among all users, limiting memory usage per user while simultaneously limiting the maximum number of users.
13.The feasible region represented by the constraints
x1 – x2 < 1,
x1 + x2 > 3,
x1 > 0, x2 > 0
of the objective function Max Z = 3x1 + 2x2 is
(A) A polygon
(B) Unbounded feasible region
(C) A point
(D) None of these
Solution) Unbounded feasible region
Explanation)



14.The diffuse reflection coefficient of an object determines its colour in major part. What colour should the item be if Kd = (0.8, 0.4, 0) and the light used is blue and magenta?
(A) White and Red
(B) Red and Blue
(C) Black and White
(D) Black and Red
Solution) Black and Red
Explanation)
Kd is given a value ranging from 0.0 to 1.0.
0.0 – for a dark, drab surface that absorbs nearly all light.
1.0 – for a gleaming surface that reflects nearly all of the light.
You should have a good understanding of the kd range and what it means. There are three kd values for coloured surfaces: red, green, and blue. Consider the case of a polygon with a diffuse hue (1,0,0). It reflects all red light and absorbs all blue and green light that strikes it (because red has a value 1, and green and blue has a 0).
When a white light shines on this red polygon, it turns red. It will seem black if it is exposed to blue, green, or aqua light (as those lights have no red component).
If it is exposed to a yellow or purple light, it will turn red (as the polygon will reflect the red component of the light). The kd value in the equation is kd= (0.8,0.4,0)
If the light used is blue and magenta, what colour should the item be? That is the issue.
Let's start with the first colour. The thing is bathed in blue light. The blue component of kd, on the other hand, is 0. It signifies that the object's colour will be totally absorbed and it will seem black. As a result, when blue light strikes on an object, it appears dark. Let's have a look at the following colour. The object is bathed in magenta light. The colour magents is a violet-red or purplish-red. It's a colour that's halfway between red and blue. Because red has a high kd value, it will be reflected more, resulting in the object's colour becoming red. As a result, the object's colour will be Black and Red. D is the right answer.
15. A page fault takes an additional 'j' microseconds if an instruction takes I microseconds. If a page fault happens per k instructions on average, the practical instruction time is
(A) i + j/k
(B) i + j * k
(C) (i + j)/k
(D) (i + j) * k
Solution) i + j/k
Explanation)

16. If all members of the column in any simplex table corresponding to any negative j are negative or zero, the solution under test is
(A) degenerate solution
(B) unbounded solution
(C) alternative solution
(D) non-existing solution
Solution) unbounded solution
Explanation)

17. How many relations are there between a set of n symmetric items and a set of n reflexive and symmetric elements?
(A) 2n(n+1)/2 and 2n .3n(n–1)/2
(B) 3n(n–1)/2 and 2n(n–1)
(C) 2n(n+1)/2 and 3n(n–1)/2
(D) 2n(n+1)/2 and 2n(n–1)/2
Solution) 2n(n+1)/2 and 2n(n–1)/2
Explanation)

18. The strategy used to reduce the number of tree branches and the number of static evaluations applied in case of a game tree is
(A) Minmax strategy
(B) Alpha-beta pruning strategy
(C) Constraint satisfaction strategy
(D) Static max strategy
Solution) Alpha-beta pruning strategy
Explanation)

19. Match the following :
(i) Regular Grammar (a) Pushdown automaton
(ii) Context-free Grammar (b) Linear bounded automaton
(iii) Unrestricted Grammar (c) Deterministic finite automaton
(iv) Context Sensitive Grammar (d) Turing machine
(i) (ii) (iii) (iv)
(A) (c) (a) (b) (d)
(B) (c) (a) (d) (b)
(C) (c) (b) (a) (d)
(D) (c) (b) (d) (a)
Solution)
(i) (ii) (iii) (iv)
(c) (a) (d) (b)
Explanation)
- Context free grammar can be recognized using Push down automatan.
- Regular grammar can be recognized using Deterministic finite automaton
- Context sensitive grammar can be recognized using Linear bounded automaton.
-
Unrestricted grammar can be recognized using Turing machine
So, option (B) is correct.
20. Consider the circuit below and determine the output function f(x, y, z).

(A) x – z + xy + – yz
(B) x – z + xy + – y – z
(C) xz + xy + – y – z
(D) xz + x – y + – yz
Solution) 
Explanation)
Output from MUX 1=> Z’X+ZY’
Output from MUX2=> Y’(Z’X+ZY’)+YX
=>Y’Z+Y’Z’X+YX
=>Y’Z+X(Y’Z’+Y)
=>Y’Z+X(Y+Z’) USING A+A’B=(A+B)
=>Y’Z+XY+XZ’
21. Which diagram depicts a formal graphic notation representing items, classes, and interrelationships?
(A) Object diagram
(B) Class diagram
(C) Instance diagram
(D) Analysis diagram
Solution) Object diagram
Explanation)

22. What is the size of the Header length field in the IPV4 header (in bits)?
(A) 2
(B) 4
(C) 8
(D) 16
Solution) 4
Explanation) The size of the Header length field in the IPV4 header (in bits) is 4
23.Match the following with respect to java.util.* class methods :
(a) Bit Set (i) Time zone getTimezone( )
(b) Calendar (ii) int hashcode( )
(c) Time zone (iii) int nextInt( )
(d) Random (iv) Void setID(String tzName)
Solution)
(a) (b) (c) (d)
(ii) (i) (iv) (iii)
Explanation)
List 1 List 2
Bit set int hashcode()
Calendar Time zone getTimezone()
Time zone Void SetID(String tzName)
Random int nextInt()
24. Because the only way to manage kernel objects is through invoking methods on their handles, _____ is frequently referred to as object-oriented.
(A) Windows NT
(B) Windows XP
(C) Windows VISTA
(D) Windows 95/98
Solution) Windows NT
Explanation) Because the only way to manage kernel objects is through invoking methods on their handles, Windows NT is frequently referred to as object-oriented.
25. In Unix, a user-level process catches the Ctrl + C input signal and contains a signal handling procedure that saves suitable files before terminating the process. What mode does the signal handling function execute when a Ctrl + C input is delivered to this process?
(A) User mode
(B) Kernel mode
(C) Superuser mode
(D) Privileged mode
Solution) Kernel mode
Explanation)
- As it comes from a user, privileged mode cannot be used when an input is sent to the process, hence option D, privileged mode, is not an option.
- As you can see, kernel mode equals privileged mode.
- As a result, both options B and D are equal. Option B is also untrue because option D is not conceivable.
- Option C is clearly incorrect because there is no such thing as superuser mode.
- Exclusively option A remains; with a user input such as 'ctrl+c,' the signal handling method executes in user mode only, trapping the signal as a user level process in UNIX.
26. A CPU usually handles an interrupt by performing an interrupt service procedure.
(A) immediately after an interrupt is triggered
(B) at the end of the fetch cycle
(C) when the current instruction is completed
(D) at predefined time intervals
Solution) by checking the interrupt register after finishing the executing the current instruction
Explanation) Interrupts are detected immediately by hardware, but the CPU does not respond until it has completed its current instruction. This is done to guarantee that the instructions are accurate.
27. On the view plane z = d, where the center of projection is the origin (0, 0, 0), the perspective projection matrix shall be

Solution)

Explanation)

28. The following mechanisms govern the propagation of radio signals:
(A) Modulation, Amplification, Scattering
(B) Reflection, Diffraction, Scattering
(C) Amplification, Diffraction, Modulation
(D) Reflection, Amplification, Diffraction
Solution) Reflection, Diffraction, Scattering
Explanation) Reflection, Diffraction, Scattering govern the propagation of radio signals.
29. Identify the devices given below with their IC numbers :
(i) USART (a) 8251
(ii) Microcontroller (b) 8051
(iii) Interrupt controller (c) 8259
(iv) DMA controller (d) 8257
(i) (ii) (iii) (iv)
(A) (a) (b) (c) (d)
(B) (b) (a) (d) (c)
(C) (c) (d) (a) (b)
(D) (d) (a) (b) (c)
Solution)
(i) (ii) (iii) (iv)
(a) (b) (c) (d)
Explanation)

30. Using the Hungarian technique, the best answer to the following assignment problem is

(A) (B) (C) (D)
(A) (I) (II) (III) (IV)
(B) (I) (III) (II) (IV)
(C) (I) (III) (IV) (II)
(D) (I) (IV) (II) (III)
Solution)
(A) (B) (C) (D)
(I) (III) (II) (IV)
Explanation) The Hungarian technique is a polynomial-time combinatorial optimization approach that foreshadowed later primal–dual methods.
31. Which of the following statements is true if a and b are the line's endpoints?
(A) If both endpoints are left, right, above or below the window, the line is invisible.
(B) If both end points are left, right, above or below the window, the line is completely visible.
(C) If both end points are left, right, above or below the window, the line is trivially visible.
(D) If both end points are left, right, above or below the window, the line is trivially invisible.
Solution) If both end points are left, right, above or below the window, the line is trivially invisible
Explanation) If both end points of a line are at one end, i.e. (both are left, right, above, and below), then they are clearly not visible or invisible (choices B and C are out). Now, because nothing needs to be done to them, such as clipping or reatining, we ignore them completely or they are trivial for us, so the line is trivially invisible.
32. Match the following with link quality measurement and handoff initiation :
(a) NetworkedControlled Handoff (NCHO) (i) MS connect to BS
(b) MobileAssisted Handoff (MAHO) (ii) Process via channel the target BS
(c) Forward Handoff (iii) First Generation Analog Cellular System
(d) Hard Handoff (iv) Second Generation Digital Cellular System
(a) (b) (c) (d)
(A) (iii) (iv) (ii) (i)
(B) (ii) (iii) (i) (iv)
(C) (ii) (i) (iv) (iii)
(D) (iv) (iii) (i) (ii)
Solution)
(a) (b) (c) (d)
(iii) (iv) (ii) (i)
Explanation)
List 1 List 2
Network- controlled Handoff (NCHO) First Generation analog cellular
Mobile-Assisted Handoff (MAHO) Cellular system Second generation digital
Forward Handoff BS Process via channel the target
Hard Handoff MS connect to BS
33. What is the frequency in the kilohertz of a signal with a period of 1000 milliseconds?
(A) 10–3 KHz
(B) 10–2 KHz
(C) 10–1 KHz
(D) 1 KHz
Solution) 10–3 KHz
Explanation) We know that:
frequency(f) = 1 / Timeperiod(T)
Given timeperiod(T) = 100 ms
f = 1 / 100ms
f = 1000 / 100000 ms
We know that 1000 ms = 1 sec and we can write 1000 as 1 k
i.e. f = 1k / 100s
f = 10-2 kHz (1 / s = Hz)
34. H's two cosets are a * H and b * H.
(i) a * H and b * H are either disjoint, or
(ii) a * H and b * H are identical.
Then,
(A) only (i) is true
(B) only (ii) is true
(C) (i) or (ii) is true
(D) (i) and (ii) is false
Solution) (i) or (ii) is true
Explanation) No explanation
35.HTML is based on SGML, an information processing-text and office systems (SGML) standard for text information processing.
(A) ISO – 8878
(B) ISO – 8879
(C) ISO – 8880
(D) ISO – 8881
Solution) ISO – 8879
Explanation) HTML is defined using SGML – an ISO – 8879 standard, information processing-text and office systems (SGML) for text information processing.
36. What does 'Hibernate' mean in Windows XP / Windows 7?
(A) Reboot the PCs into safe mode.
(B) Perform a routine restart of the PCs mode.
(C) Turn off the computer putting an end to all that is now running applications.
(D) Shutdown the computer without closing the running applications.
Solution) Shutdown the computer without closing the running applications.
Explanation) Hibernate mean in Windows XP / Windows 7, Shutdown the computer without closing the running applications.
37. Assume that we have constructor functions for the base and derived classes. Now consider the declaration in main( ). Base * P = New Derived; in what sequence will the constructor be called?
Derived class constructor followed by Base class constructor.
(B) Base class constructor followed by derived class constructor.
(C) Base class constructor will not be called.
(D) Derived class constructor will not be called.
Solution) Base class constructor followed by derived class constructor.
Explanation) Here A derived class object is created first, and then a base class pointer is allocated to it. The base class function Object() { [native code] } is called first, followed by the derived class function Object() { [native code] }, whenever a derived class object is produced.
38. In a UNIX system, which of the following choices is not a shell?
(A) Bourne Shell
(B) C Shell
(C) Net Shell
(D) Korn Shell
Solution) Net Shell
Explanation) Net Shell is not a shell in UNIX system.
39. Which file does the compiler utilize to manage the numerous objects in Windows programming?
(A) Control File
(B) Binary File
(C) Text File
(D) Obj File
Solution) Text File
Explanation) A.control file is a tiny binary file that records the database's physical structure.
B.A binary file is readable by computers but not by humans. Most numeric data files, as well as all executable programmes, are stored in binary files.
C.text files are stored in a human-readable format (typically ASCII).
The.obj file extension refers to an organised machine code file built by a compiler.
As a result, Ans should be a C text file.
40. Find the number of tracks the disc arm must move to satisfy all the requests in the disc queue on a disc with 1000 cylinders (0 to 999). Assume the head is heading toward track 0 and the previous request service was at track 345. Requests for the following tracks are in FIFO order in the queue:
123, 874, 692, 475, 105, 376.
(Assume SCAN algorithm)
(A) 2013
(B) 1219
(C) 1967
(D) 1507
Solution) 1219
Explanation)

41. Halftoning is defined as
(A) a technique to obtain increased visual resolution using multiple intensity levels.
(B) a technique for using minimum number of intensity levels to obtain increased visual resolution.
(C) a technique to obtain increased visual resolution using maximum number of intensity levels.
(D) a technique for using appropriate number intensity levels to obtain increased visual resolution.
Solution) a technique for using minimum number of intensity levels to obtain increased visual resolution.
Explanation) Halftoning is defined as a technique for using minimum number of intensity levels to obtain increased visual resolution.
42.G1 and G2 are two graphs as shown :

(A) Both G1 and G2 are planar graphs.
(B) Both G1 and G2 are not planar graphs.
(C) G1 is planar and G2 is not planar graph.
(D) G1 is not planar and G2 is planar graph.
Solution) G1 is not planar and G2 is planar graph.
Explanation)

43. Which of the following binary search trees is the best if the chances of a successful and failed search are equal?

Solution) (D)
Explanation) A rooted binary tree data structure whose internal nodes each hold a key higher than all the keys in the node's left subtree and fewer than those in the node's right subtree is known as a binary search tree.
44) If two fuzzy sets A and B are given with membership functions
µA (x) = {0.2, 0.4, 0.8, 0.5, 0.1}
µB (x) = {0.1, 0.3, 0.6, 0.3, 0.2}
Then the value of µ A∩B will be
(A) {0.9, 0.7, 0.4, 0.8, 0.9}
(B) {0.2, 0.4, 0.8, 0.5, 0.2}
(C) {0.1, 0.3, 0.6, 0.3, 0.1}
(D) {0.7, 0.3, 0.4, 0.2, 0.7}
Solution) (A)
Explanation) We will use the definition of sets to address this problem. Classical sets — an element is either a member of the set or it is not. Crisp sets are another term for classic sets (sets). Fuzzy set – allows for gradation, such as all shades of black and white. A graphical depiction of how the transition from one to another occurs is included in a fuzzy set. A membership function is the graphical representation of this information. We can now introduce fundamental operations on fuzzy sets now that we have a better understanding of what they are. We want to intersect, unify, and negate fuzzy sets in the same way as we want to intersect, unify, and negate crisp sets. Intersection, union, and complement are defined in Fuzzy Logic in terms of their membership functions.
In our case the fuzzy intersection of two fuzzy sets A and B on universe of discourse X: 𝜇𝐴∩𝐵(𝑥) = 𝑚𝑖𝑛(µ𝐴 (𝑥), µ𝐵(𝑥)). The most commonly adopted t-norm is the minimum. That is, given two fuzzy sets A and B with membership functions µ𝐴 (𝑥) and µ𝐵(𝑥). But here in our task, they are asking for complement of A intersection B and so the answer would be𝜇𝐴 (𝑥) = 1 − µ𝐴 (𝑥) or we can write 1 − 𝑚𝑖𝑛(𝐴(𝑥), 𝐵(𝑥)).
The minimum of µ𝐴(𝑥) = {0.2, 0.4, 0.8, 0.5, 0.1} and µ𝐵(𝑥) = {0.1, 0.3, 0.6, 0.3, 0.2} we can write {0.1,0.3,0.6,0.3,0.1}. The first value will be 1 − 0.1 = 0.9, the second value is 1 − 0.3 = 0.7, the third value will be 1 − 0.6 = 0.4, the fourth value is1 − 0.3 = 0.7, the last value is 1 − 0.1 = 0.9. We get {0.9, 0.7, 0.4, 0.7, 0.9}.
45) Consider the ways that processes P1 and P2 utilise to get to their critical sections. The initial values of the shared Boolean variables S1 and S2 are assigned at random.

Which one of the following statements describes the properties achieved ?
(A) Mutual exclusion but not progress
(B) Progress but not mutual exclusion
(C) Neither mutual exclusion nor progress
(D) Both mutual exclusion and progress
Solution) Neither mutual exclusion nor progress
Explanation) When mutual exclusion is satisfied, only one process can access the crucial area at any given moment. However, if S1=1 and S2=0, and process P1 is not interested in entering the critical section but process P2 is, progress will be hindered. In this case, P2 is unable to reach the critical area since only P2 can enter once P1 has completed execution (and the S1=S2 condition has been satisfied).
When a process that is not interested in entering the critical portion refuses to enable other processes that are interested to enter the critical area, progress will be stifled. When P1 wants to enter the crucial part, it may have to wait until P2 enters and exits the critical area (or vice versa), which may never happen, resulting in a violation of the progress condition.





