
Introduction
The NET(National Eligibility Test) is executed on behalf of the University Grants Commission (UGC) to decide the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Colleges and Universities.
This article discusses the previous year's UGC-NET computer science questions of June 2019 Paper II. We will see these questions along with their answers and explanation.
Questions
1. Let Aα0 denote the α-cut of a fuzzy set A at α0. If α1 < α2, then
(a) Aα1 ⊇ Aα2
(b) Aα1 ⊃ Aα2
(c) Aα1 ⊆ Aα2
(d) Aα1 ⊂ Aα2
Answer: (a)
Explanation:
P = {(C,0.7), (D, 0.8)}
Let's take α-cut A0.3, i.e., α1,
then,
A0.3 = {(C, 1), (D, 1);
Now take α- cut A0.6, i.e., α2
A0.6 = {(C,1), (D, 1)}
A0.6 ⊆ A0.3 when α1 < α2
Aα1 ⊇ Aα2
2. Suppose a computer program takes 100 seconds of execution time on a computer with multiplication operation accountable for 80 seconds of this time. How much do we have to improve the speed of multiplication operation if we are asked to execute this program four times faster?
(a) 14 times faster
(b) 15 times faster
(c) 16 times faster
(d) 17 times faster
Answer: (c)
Explanation:
Total execution time of a program = time required to execute multiplication operation + time required to perform other operations 100 = 80 + time to execute some other operations.
Time required to perform some other operations = 20
Now, improve the speed of multiplication operation to execute this program four times faster, i.e.,
The new total execution time of a program = 100/4 = 25
According to the question, we have to keep the time to perform some other operations as it is, i.e., 20.
Hence the time to perform multiplication operation after modification = (New Total execution time of the program - time to perform some other operations)
= 25 - 20
= 5
So, the speed of the multiplication operation is improved by 80/5 times = 16 times.
3. Which of the subsequent statements is/are true?
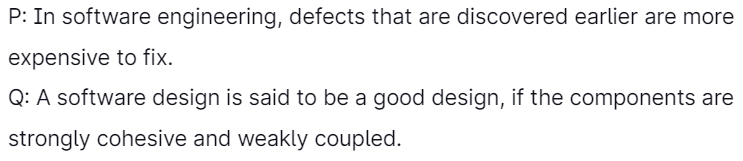
Select the correct answer from the subsequent options:

Answer: (b)
Explanation: The earlier the defect is found, the lesser the cost of the defect. For example, it is somewhat cheap to fix if the error is located in the requirement specifications during requirements gathering and analysis. We can correct the requirement specification, and then it can be re-issued.
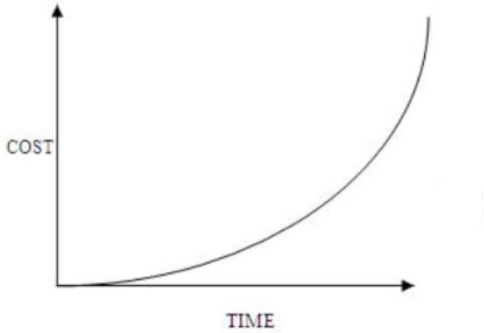
4. Consider double hashing of the form
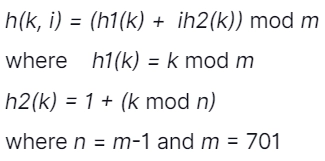
What is the difference between first & second probes for k = 123456 in terms of slots?
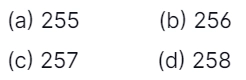
Answer: (c)
Explanation:
h(k,i) = h1(k) + ih2(k)
Where h1(k) = k mod m
h2(k) = 1+k mod n
Where m = 701 and n = m - 1.
For, k = 123456
h1(k) = 123456 mod 701
h1(k) = 80
h2(k) = 1 + (123456 mod 700)
h2(k) = 1 + 256=257
1st probe: i = 1
h(k,i) = h1(k)+ih2(k)
h(k,1) = h1(k)+ih2(k)
h(k,1) = 80+257=337
h(k,1) = 337
2nd probe: i = 2
h(k,2) = 80 + 2257
h(k,2) = 80 + 514
h(k,2) = 594
Therefore, the difference
h(k,2) - h(k,1)
= 594 - 337
= 257
5. Which among the following statements is/are true?
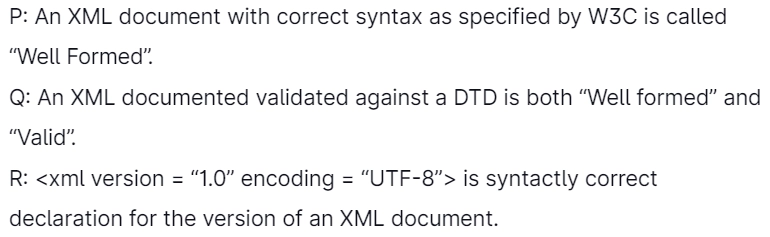
Select the correct answer from the following options:

Answer: (a)
Explanation: An XML document is well-formed if it has correct syntax like tags are case sensitive, components must have closing tags, elements must be nested appropriately, etc.
But when we associate a well-formed XML document with a DTD(in which we represent the structure of a document) and if the XML document validates all the definitions described in DTD, then that XML document is called a "valid" XML document.
Always keep in mind that a "valid" XML document is also a "well formed" XML document but not vice-versa.

is syntactically accurate declaration for the version of an XML document.
6. Which of the subsequent features is supported in the relational database model?

Answer: (c)
Explanation:
Composite data types:
Composite data types are composed of other existing data types such as date, time, images, etc. They are used as objects. They are not allowed in RDBMS, so we store them in LOB; we cannot access them directly in RDBMS.
Multivalued attributed:
It is an attribute that holds more than one value. It is not allowed in RDBMS. An attribute can have only one value at one time.
Association with multiplicities:
Multiplicity denotes the cardinality of a particular entity associated with other entities. In terms of database, this means participation and cardinality of the relation. It is allowed in RDBMS.
Generalization relationship:
Generalization means the combination of lower entities to form a higher entity. Entities are combined and have common attributes.
7. A fuzzy conjunction operator represented as t(x, y) and a fuzzy disjunction operator represented as s(x, y) make a dual pair if they satisfy the condition:
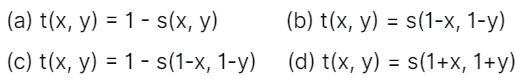
Answer: (c)
Explanation: There is a duality between t-norms(conjunction) and t-conorms(disjunction) operators mediated by the negation operator, x' = 1 - x. The fuzzy conjunction t(x,y) and disjunction s(x,y) operators form a dual pair if they satisfy the following condition:
1- t(x, y) = s(1 - x, 1- y)
and
1 - s(x, y) = t(1 - x,1 - y),
which in the classical sets theory corresponds to the De Morgan's laws: (AUB)' = A'∩B'
and
(A∩B)' = A'UB'
So, the choice of a fuzzy disjunction operator determines the choice of the fuzzy conjunction operator, and vice versa, if it is wished that the operators are dual.
8. Suppose a connected planar graph has six vertices, each degree four. How many regions does a planar representation of this graph divide the plane?
(a) 6
(b) 8
(c) 12
(d) 20
Answer: (b)
Explanation: We apply Euler's formula where r = e - V + 2.
Since each vertex has a degree of 4, the sum of the degrees is 24.
By the handshaking theorem, 2e = 24.
So, e = 12.
r = 12 - 6 + 2
r = 8
Hence we have 8 regions in this planar graph.
9. The M components in the MVC are responsible for
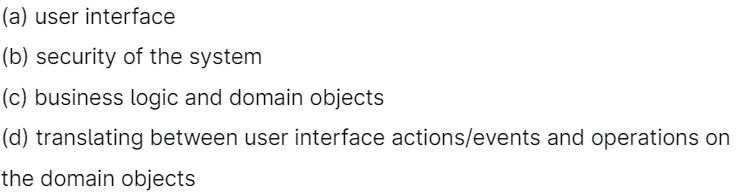
Answer: (c)
Explanation: "MVC" stands for "Model-View-Controller" and directs to three different realms of responsibility in designing a graphical user interface. The MVC pattern is laid to a component; the model consists of the data representing the component's current state. The view is just the visual representation of the component on the screen.
And the controller is the aspect of the component that carries out actions in response to events caused by the user (or by other sources such as timers).
The idea is to allocate responsibility for the model, the view, and the controller to different objects.
10. Software reuse is

Answer: (b)
Explanation: Software Reuse is a process of existing software artifacts and knowledge to build new software.
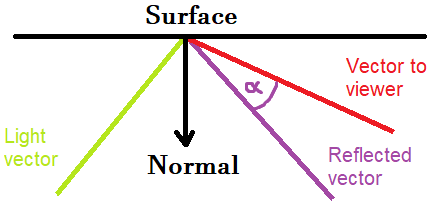
11. In the phong reflectance model, the strength of the specular highlight is defined by the angle between

Answer: (d)
Explanation: Specular highlights appear on objects because the light reflected from the object hits the viewer. Occasionally, we are hit directly by the light, and the highlight seems to be very intense, and sometimes we are hit so slightly that we don't see the specular highlight. The strength of this highlight depends on the cosine of the angle between the reflected vector and the vector taken from the point at the object to the viewer's position:
12. Suppose that register A and register K have the bit configuration. The three leftmost bits of A are only compared with memory words since K has 1’s in these positions. This type of memory uniquely suits parallel searches by data association because of its organization. This type of memory is called?
(a) RAM
(b) ROM
(c) Content addressable memory
(d) Secondary memory
Answer: (c)
Explanation: Content-addressable memory (CAM) is a particular computer memory used in specific very-high-speed searching applications. It is also known as an associative memory or associative storage. It compares input search data against a table of stored data and yields the address of matching data (or, in associative memory, the matching data).
13. Consider a raster system with a resolution of 640 by 480. What size is the frame buffer (in bytes) for this system to store 12 bits per pixel?
(a) 450 kilobytes (b) 500 kilobytes
(c) 350 kilobytes (d) 400 kilobytes
Answer: (a)
Explanation: 8 bits = 1 byte.
A frame-buffer size of the systems are as follows:
= (640 x 480 x 12) bits / 8
= 450KB
14. Consider the following:

Which of the below are found in genetic algorithms?
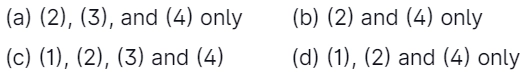
Answer: (c)
Explanation: Five phases are considered in the genetic algorithm.
1. Initial population
2. Fitness function
3. Selection
4. Crossover
5. Mutation
15. Match List-I with List-II:

Choose the correct option from the following:

Answer: (d)
Explanation:
Waterfall model -> Automate the manual system for student record maintenance in a school.
Incremental development -> e-business that starts with only the basic functionality and then moves on to more advanced features.
Prototyping -> A virtual reality system for simulating vehicle navigation on a highway.
RAD -> An inventory control system for a supermarket to be developed on a highway.
16. The minimum amount of page frames that must be allocated to a running process in a virtual memory(VM) environment is determined by

Answer: (c)
Explanation: Based on Instruction Set Architecture, every process can be needed a minimum no. of pages.
An ISA permits multiple implementations that vary in performance, physical size, and monetary cost.
17. For a statement
A language L ⊆ Σ* is recursive if some Turing machine M exists.
Which of the below conditions is satisfied for any string ω?

Answer: (c)
Explanation: If language is recursive, then language has a Turing machine that will permanently halt in the final state (acceptable state) for strings that belong to language and always halt in the non-final state when the string is not in language. Hence option 3 is correct.
18. Consider the following statements:
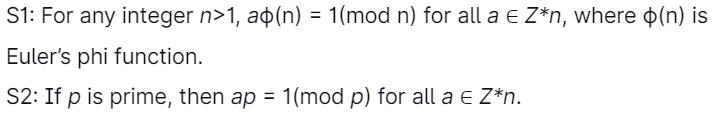
Which one of the following is/is correct?
(a) Only S1
(b) Only S2
(c) Both S1 and S2
(d) Neither S1 nor S2
Answer: (a)
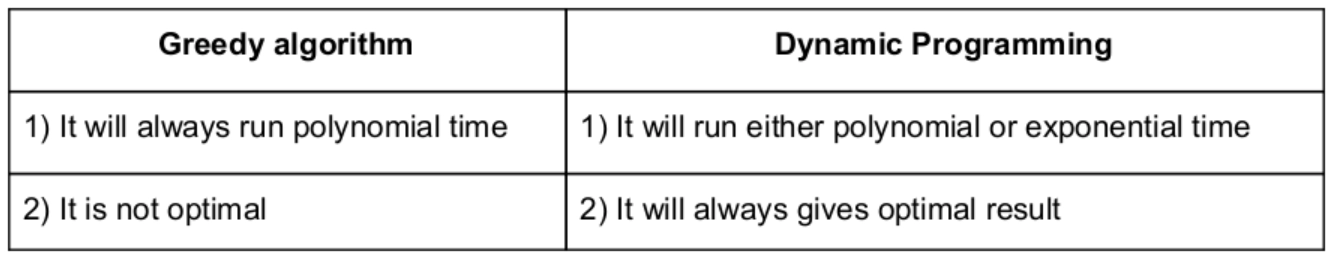
Explanation: Dynamic Programming will fulfill both properties, but greedy is not follow both properties.
19. Consider the Euler’s phi function given by
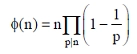
where p runs over all the primes dividing n. What is the value of ϕ(45)?
(a) 3
(b) 12
(c) 6
(d) 24
Answer: (d)
Explanation:
Φ(45) -> Φ(9*5)
-> Φ(32* 5)
-> Φ(32) * Φ(5)
-> Φ(32 - 3,(2-1)) * (5-1)
= 24
Remember Formula:
If p is prime, then Φ(p) = (p-1), and if p is not prime and it's in prime power k from then o(pk) = pk - p(k-1)
20. Consider the following pseudo-code fragment in which an invariant for the loop is “ m*xk = pn and k ≥ 0 ” (here, p and n are integer variables that have been initialized):
/* Pre-conditions: p ≥ 1 ᴧ n ≥ 0 */
/* Assume that overflow never occurs */
int x = p; int k = n; int m = 1;
while ( k<>0){
if (k is odd) then m = m*x;
x = x*x;
k = ⌊k/2⌋; /* floor(k /2) */
}
Which of the below must be true at the end of the while loop?
(a) x = pn
(b) m = pn
(c) p = xn
(d) p = mn
Answer: (b)
Explanation:
Option-1: It is not correct because x = plog n
Option-3 and 4: These two statements are not correct because they were given a left-side value that is much smaller than the right side. So, option-2 is correct.
21. Consider the following two statements concerning IPv4 in computer networking:

What can we say about the statements P and Q?

Answer: (b)
Explanation: The loopback(IP) address is the member of the class A network. We can use any address between the range 127.0.0.o to 127.255.255.255 as a loopback address, but we can't use 127.0.0.0 and 127.255.255.255 as loopback addresses.
We use the loopback(IP) address to send a packet from the host.
22. Which of the subsequent is the best running time to sort n integers in the 0 to n2 – 1?
(a) O(log n) (b) O(n)
(c) O(n log n) (d) O(n2)
Answer: (b)
Explanation: Using merge, heap sort will get the complexity of O(nlogn)
But using radix sort will get in linear time only. O(n)
23. How many address lines & data lines are needed to provide a memory capacity of 16K × 16?
(a) 10, 4
(b) 16, 16
(c) 14, 16
(d) 4, 16
Answer: (c)
Explanation: 16K x 16 means we have 214 address lines and 16 data lines.
To provide 214 address lines, we need 14 address lines, and to provide 16 data lines, we need 16 data lines.
24. You are designing a link-layer protocol for a link with a bandwidth of 1 Gbps (109 bits/second) over a fiber link with a length of 800 km. Assume the speed of light in the medium is 200000 km/second. What is the propagation delay in this link?
(a) 1 millisecond (b) 2 milliseconds
(c) 3 milliseconds (d) 4 milliseconds
Answer: (d)
Explanation: Tp = Distance/Time
= 800/200000
= 4*10-3 sec
= 4 milliseconds
25. Which of the below is an example of an unsupervised neural network?
(a) Back-propagation network
(b) Hebb network
(c) Associative memory network
(d) Self-organizing feature map
Answer: (d)
Explanation: A self-organizing feature map(SOFM) or self-organizing map(SOM) is a kind of Artificial Neural Network which is trained using unsupervised learning to create a low-dimensional (typically two-dimensional) discretized model of the input space of the training models is called a map. Therefore, a method to make dimensionality reduction. Self-organizing maps vary from other artificial neural networks to apply competitive learning instead of error-correction learning (such as backpropagation with gradient descent). They employ a neighborhood function to maintain the topological properties of the input space.





