
Introduction
The NET(National Eligibility Test) is executed on behalf of the University Grants Commission (UGC) to decide the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Colleges and Universities.
This article discusses the previous year's UGC-NET computer science questions of June 2019 Paper II. We will see these questions along with their answers and explanation. Before going through the article, refer to June 2019 Paper II - Part 1. Also read June 2019 Paper II - Part 3 & June 2019 Paper II - Part 4.
Questions
26. In the context of 3-D computer graphics, which of the below statements is/are true?
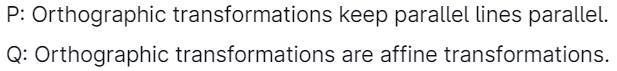
Select the correct answer from the options below:

Answer: (a)
Explanation: Orthographic projections are parallel projections. Each line that is initially parallel will be similar after this transformation.
Orthographic projection is a means of describing 3-D objects in two dimensions. It is a state of parallel projection in which every projection lines are orthogonal to the projection plane,
In Euclidean geometry, an affine transformation, or an affinity, is a geometric transformation that preserves lines and parallelism (but not necessarily distances and angles).
27. How many distinct Boolean functions of degree n are there?

Answer: (a)
Explanation: There are 2n distinct n-tuples of 0s and 1s.
The Boolean function is an assignment of 0 or 1 to each of these 2n different n-tuples. Therefore, there are 22^n different Boolean functions.
28. Which of the subsequent key constraints is required to function foreign keys in the context of relational databases?
(a) Unique key
(b) Primary key
(c) Candidate key
(d) Check key
Answer: (b)
Explanation: The foreign key is a key whose values depend on the primary key. Hence, for the functioning of a foreign key in a relational database, we need a primary key.
29. How many operations are required to translate the expression below into quadruple representation?
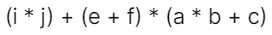
(a) 5
(b) 6
(c) 3
(d) 7
Answer: (b)
Explanation:
T1 = (i*j)
T2 = (e+f)
T3 = (a*b)
T4 = (T3+c)
T5 = T2 * T4
T6 = T1 + T5
Hence 6 operations are required.
30. Consider the game tree given below:
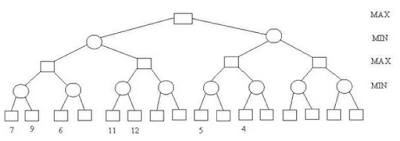
 describes Min and Max nodes, value of the root node of a game tree is?
describes Min and Max nodes, value of the root node of a game tree is?

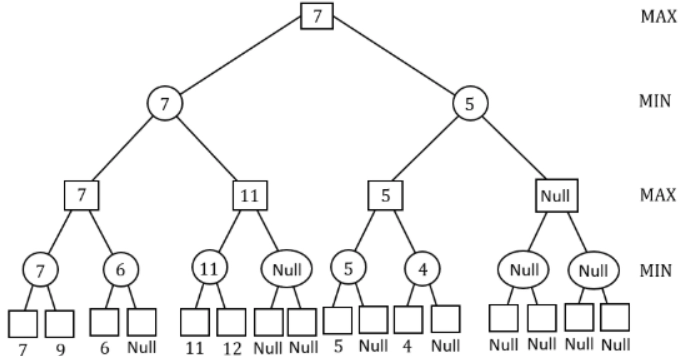
Answer: (b)
Explanation:
31. Which of the below statements is/are TRUE?
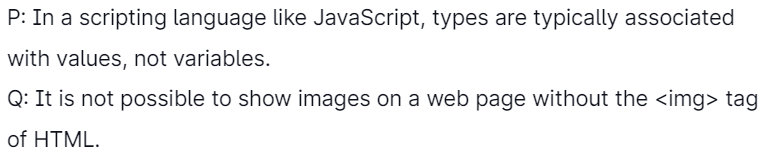
Select the correct answer from the options below:

Answer: (a)
Explanation: P: True. Variables are typically not declared in a scripting language, so there is no opportunity to assign them a type.
32. Consider the following steps:

Which of the below step(s) is/are common to both the dynamic programming and greedy algorithms?

Answer: (a)
Explanation: Dynamic Programming will satisfy both the properties, but greedy will not any properties.
Greedy algorithm |
Dynamic Programming |
| 1. It will always run polynomial time. | 1. It will run either polynomial or exponential time. |
| 2. It is not optimal. | 2. It will always give the optimal result. |
33. The STRIPS representation is
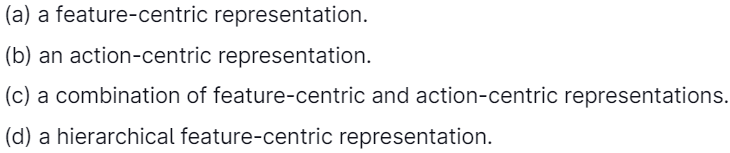
Answer: (b)
Explanation: The STRIPS representation for action consists of
The precondition is a set of assignments of values to features that must be true for the action to occur.
The effect is a set of assigning values to those primitive features that change due to the action.
34. How can the decision algorithm be made for deciding whether context-free language L is finite?
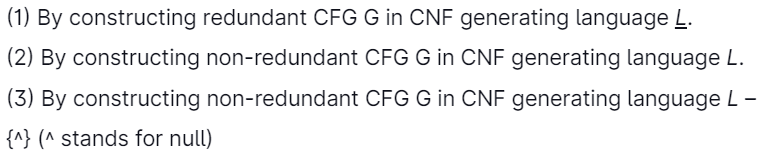
Which of the following is correct?

Answer: (c)
Explanation: To test if L(G) is finite, use the CNF conversion method to find CFG G'=(V', T, P,' S) in CNF with no useless symbols yielding L(G)-{E}.
L(G') is finite if only if L(G) is finite. An easy test for the finiteness of a CNF grammar with no useless symbols is to make a directed graph with a vertex for all variables and an edge from A & B if there is a show of the form A-BC or A- CB for any C. Then the language generated is finite if & only if this graph has no cycles.
35. A fully connected network topology is a network topology with a direct link between all the pairs of nodes. A fully connected network with n nodes is given, and the number of direct links can be expressed as a function of n?

Answer: (d)
Explanation: In a fully connected network having n nodes, each node is connected with the remaining (n-1) nodes. So this way, the total number of links will be n(n-1). And since we don't need two links for communication between any two nodes, they can communicate using a single link between them the same way we need (n(n-1)]/2 links in a fully connected network.
Ex: Take n = 5
n(n-1)/2
= 5(5-1)/2
= 20/2
= 10
36. In a relational database management system, which of the below is/are property/properties of candidate key?
P: Irreducibility
Q: Uniqueness
(a) P only
(b) Q only
(c) Both P and Q
(d) Neither P nor Q
Answer: (c)
Explanation: Let K be the subset of the heading of relvar R. Then the K is a candidate key (or just key for short) for R if and only if it has both of the following properties:
Uniqueness: No valid value for R includes two distinct tuples with the same value for K.
Irreducibility: No proper subset of K has the uniqueness property.
37. Match List-I with List-II:

Choose the correct option from below:
(a) A-1, B-2, C-3
(b) A-3, B-2, C-1
(c) A-1, B-3, C-2
(d) A-2, B-3, C-1
Answer: (d)
Explanation: A* is a declared search algorithm or a best-first search; it desires to find a path to the given goal node having the smallest cost. A* selects the path that minimizes
f(n) = g(n) + h(n)
where n is next node on the path, g(n) is path's cost from the start node ton, and h(n) is a heuristic function that estimates the cost of the cheapest path from n to the goal.
Greedy Best First Search tries to expand the node closest to the goal because this is likely to lead to a solution quickly. Thus, it evaluates nodes by using just the heuristic function
f(n) = h(n).
38. A Web application and its support environment have not been fully fortified against attack. Web engineers evaluate that the likelihood of repelling an attack is only 30 percent. This application does not contain sensitive or controversial information, so the threat probability is 25%. What is the integrity of web applications?

Answer: (d)
Explanation: Threat = Probability that attack will occur = 0.25 or 25 percent
Secruity = Probability of repelling an attack = 0.30 or 30 percent
Integrity = (1-threat*(1-security))
= (1 - 0.25(1 - 0.30))
= 1 - 0.175
= 0.825
39. Replacing the expression 4 * 2.14 by 8.56 is known as

Answer: (a)
Explanation: Take variable i = 4*2.14
We are simply folding the value into 8.56 to avoid costly multiplication operations.
40. Consider the following properties concerning a flow network G = (V, E) in which a flow is a real-valued function f: VxV → R:
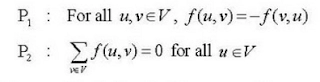
Which one of the below is/are correct?

Answer: (a)
Explanation: A pseudo-flow is a function f: VxV → R: that satisfies the below two constraints for all the nodes u and v: Skew symmetry: Only encode the net flow of units between a pair of nodes u and v, that is: f(u, v) = -f(v, u).
Capacity constraint: An arc's flow cannot surpass its capacity, that is: f(u, v) ≤ c(u, v).
Given a pseudo-flow fin a flow network, it is often helpful to consider the net flow entering a given node v, the sum of the flows entering.
The excess function Xf: V→R is defined by Xf(u) = Σv∈vf(v, u). A node u is active if xf(u) > 0, deficient if xf(u) <0 or conserving if xf (u) = 0.
These final definitions lead to two strengthenings of the definition of a pseudo-flow:
A pre-flow is a pseudo-flow that, for all v∈V\{s}, fulfills the additional constraint:
Non-deficient flows: The net flow entering the node v is non-negative, besides from the source, which "produces" flow. That is: Xf(v) ≥ 0 for all v∈V\{s}.
A feasible flow, or just a flow, is a pseudo-flow that, for all v∈V\{s, t}, meets the additional constraint:
Flow conservation: The net flow entering the node v is o, besides from the source, which "produces" flow, and the sink, which "consumes" flow.
That is: Xf (V)=0 for all v∈V \{s, t}.
The value of a possible flow f denoted [f] is the net flow into the sink t of the flow network. That is,|f| = Xf (t).
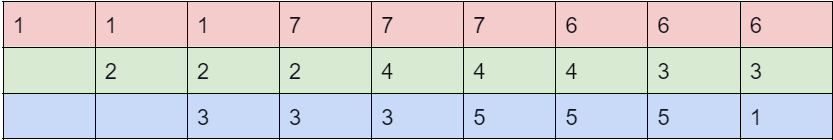
41. Consider that a process has been assigned 3 frames and includes a page referencing sequence as: 1, 2, 1, 3, 7, 4, 5, 6, 3, 1
What will be the difference in page faults for the above string using the algorithms of LRU & optimal page replacement for referencing the string?

Answer: (a)
Explanation:
LRU:
Optimal:
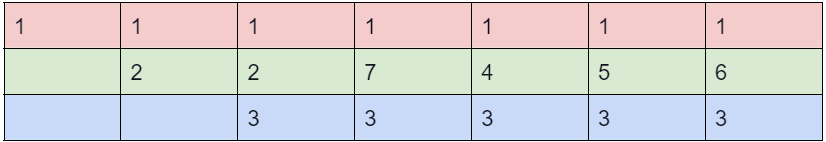
LRU = 9 page faults and
Optimal = 7 page faults
Difference = 2
42. There are numerous sorting algorithms based on the comparison. The running time of the heapsort algorithm is O(nlog n). Like P, but unlike Q, the heapsort sorts in the place where (P, Q) is equal to
(a) Merge sort, Quicksort
(b) Quicksort, Insertion sort
(c) Insertion sort, Quicksort
(d) Insertion sort, Merge sort
Answer: (d)
Explanation:
Method 1:
Mergesort has best, average, and worst-case time complexity is O(nlogn) like hep sort. Quicksort is also the same as heap and merge, except worst-case time complexity is O(n2). P is merge sort, and Q is quicksort according to the question.
Method 2:
Heapsort and insertion sort is not following the divide and conquer technique. So, it is the same as P. Merge sort follows Divide and Conquer. So, it is not like Q.
43. Which of the below has the same expressive power regarding relational query language?
(1) Relational algebra and domain relational calculus.
(2) Relational algebra and tuples relational calculus.
(3) Relational algebra and domain relational calculus are restricted to safe expression.
(4) Relational algebra and tuples relational calculus are restricted to safe expression.

Answer: (b)
Explanation: Relational algebra, Domain relational calculus limited to safe expression, and Tuple relational calculus restricted to safe expression have the same expressive power.
44. Consider the equation (146)b + (313)b-2 = (246)8 . Which of the following is the value of b?

Answer: (b)
Explanation: (146)7 + (317)7-2 = (246)8
Substitute 7 in b,
(146)7 + (317)7-2 = (246)8
(146)7 + (317)5 = (246)8
(146)7 = 1*72 + 4*71 + 6*70
= 49 + 28 + 6
= 83
(317)5 = 3*52 + 1*51 + 7*50
= 75 + 5 + 7
= 87
(246)8 = 2*82 + 4*81 + 6*80
= 128 + 32 + 6
= 166
(146)7 + (317)5 = (246)8
= 83 + 87
=166
166 = 166
LHS = RHS equal only if b is 7.
45. In the context of software testing, which of the subsequent statements is/are NOT correct?

Answer: (a)
Explanation: A minimal test set that acquires 100% statement coverage will generally detect more faults than one that achieves 100% branch coverage.
46. How many bit strings of length ten starts with a 1 bit or end with two bits 00?
(a) 320
(b) 480
(c) 640
(d) 768
Answer: (c)
Explanation:
Number of bit strings of length 10 starts with 1: 29 = 512.
Number of bit strings of length 10 ends with oo: 28 = 256
Number of bit strings of length 10 starts with 1 and ends with 00:27 = 128
Applying the subtraction rule, the number is 512+256-128 = 640
47. The following table has two attributes, Manager_id and Employee_id, where Employee_id is a primary key, and manager_id is a foreign key referencing Employee_id with on delete cascade:
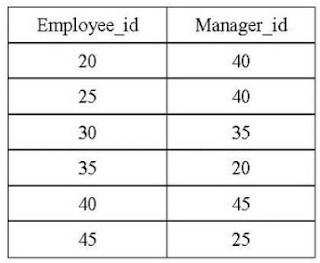
On deleting the table (20, 40), the set of other tuples that we must delete to maintain the referential integrity of the table is
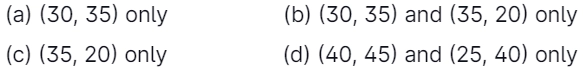
Answer: (b)
Explanation: If (20, 40) is deleted, the entry in manager_id having the 20 value will violate the referential integrity constraint, so entry (35,20) is deleted because of the deletion of (20,40).
Similarly, entry (30,35) is deleted because of the deletion of entry (35,20).
After entry deletion (30,35), referential integrity is maintained in the given relation, so no further deletions are made.
Hence correct option is option(2).
48. K-mean clustering algorithm has clustered the given 8 observations into 3 clusters after 1st iterations as follows:

What will be the Manhattan distance for observation (4, 4) from cluster centroid C1 in the second iteration?
(a) 2
(b) √2
(c) 0
(d) 18
Answer: (a)
Explanation: Manhattan distance is the absolute distance between two points by aggregating the pairwise difference between each variable. In contrast, Euclidean distance is the same by aggregating the squared difference in each variable.
So, the new position of cluster centroid C1 after the 1st iteration will be (13(3+5+7), 13(3+5+7)) = (5,5)
The Manhattan distance between (4,4) and (5,5) is |4-5|+|4-5| = 2.
49. Which of the subsequent problems is/are the decidable problem(s) (recursively enumerable) on Turing machine M?
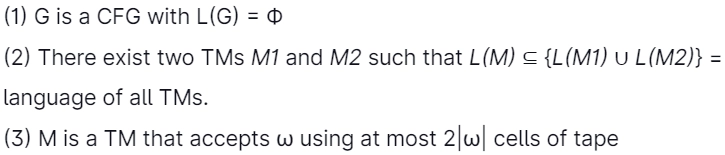

Answer: (c)
Explanation: (a): L(G)=ø is an emptiness problem, and the emptiness problem for context-free languages is decidable.
(b): Recursive: We can assume L(M2)=5*, and hence any TM (M1) will be a subset of L(M2). So we only need to see that Mi is a valid Turing machine, and there is no need to check whether it is a subset of L(M2) as it is a subset of L(M2)=3* Checking the validity of a Turing machine is always a halting process. Hence it is recursive.
(c): L={(M,w)|Mis a TM that accepts w using at most two wl squares of its tape}. Recursive: Let m be the number of states in M, k be the size of the alphabet that Muses, and r=[w]. If M uses at most two squares of its tape, there are at most Alpha=mK2r2r configurations(why?). If M runs on w for more than a step and does not use more than two squares of its tape, then M must be in the one configuration at least twice(pigeonhole principle), in which case M would enter an infinite loop on input w. Based on this, we design a machine M* that decides L that works as follows:
M* runs M on w for at most a+1 steps.
If M accepts w which steps using at most 24 squares, M* halts and accepts.
If M rejects w within a step using at most two squares, M* halts, and rejects.
If M goes beyond 25 squares, M* halts and rejects.
If M does not halt and does not go beyond two squares, M* rejects.
50. In the TCP/IP model, decryption and encryption are functions of ………….. layer.

Answer: (d)
Explanation: Decryption and encryption are functions of the presentation layer in the OSI reference model. Here, they were given the TCP/IP model. It combines Session, presentation, and Application layers into the Application layer.





