Types Of Network Attacks
Network attacks come in a variety of shapes and sizes. To protect their assets from increasingly complex cyber-attacks, businesses must maintain the highest cybersecurity standards, network security rules, and employee training.
Here are some of the common network attacks:
- DDoS (Distributed Denial of service)
- MITM (Man in the middle)
- Unauthorized Access
- SQL Injection
- RootKit
- Phishing
- IP Spoofing
-
Ransomware
DDoS
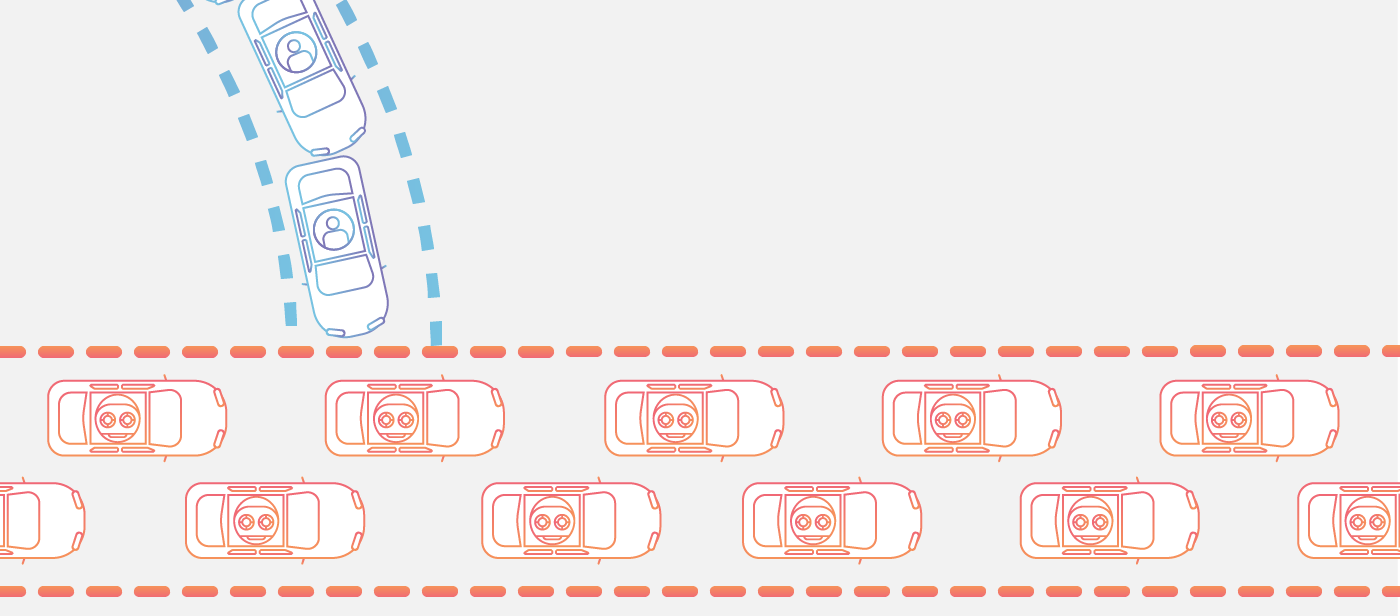
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic to a targeted server, service, or network by flooding the target or its surrounding infrastructure with Internet traffic.
DDoS attacks are effective because they use numerous hacked computer systems as attack traffic sources. Computers and other networked resources, like IoT devices, can act as exploited machines.
A DDoS assault is analogous to an unforeseen traffic jam filling up the roadway, preventing regular traffic from reaching its destination.
Source
You can read related articles such as Congestion Control in Computer Networks here.
MITM
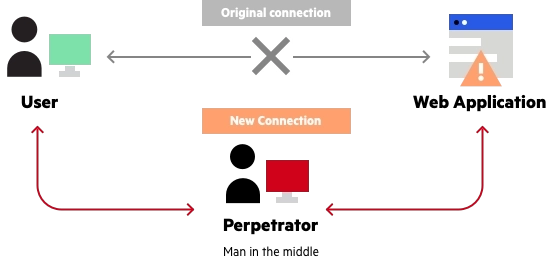
A man in the middle (MITM) attack occurs when a perpetrator inserts himself into a dialogue between a user and an application, either to spy or to fake one of the parties, giving the impression that a regular flow of information is taking place.
An attack's purpose is to steal personal information such as login passwords, account information, and credit card numbers. Users of banking apps, SaaS enterprises, e-commerce sites, and other websites that require signing in are typical targets.
Information collected during an attack might be utilized for a variety of objectives, such as identity theft, unauthorized financial transfers, or unauthorized password changes.
Source
Unauthorized Access
Unauthorized access occurs when a person acquires unauthorized access to a computer network, system, application software, data, or other resources. Unauthorized access is defined as any access to an information system or network that violates the owner's or operator's specified security policy. Unauthorized access also occurs when legitimate users get access to a resource for which they do not have authority.
SQL Injection
SQL injection is a web security flaw that allows an attacker to interfere with database queries made by an application. It typically enables an attacker to examine data that they would not be able to retrieve. This might include data belonging to other users or any other data that the program has access to. In many circumstances, an attacker can alter or remove this data, resulting in long-term modifications to the application's content or behavior.
An attacker can escalate a SQL injection attack to compromise the underlying server or other back-end infrastructure or launch a denial-of-service attack in some cases.
RootKits
A rootkit is a malicious software package that allows unauthorized access to a computer or other applications. Rootkits are difficult to detect because they can hide their existence within an infected machine. Hackers employ rootkit software to remotely access, alter, and steal data from your computer.
When a rootkit infects your system, it behaves as if it were a zombie computer, and the hacker has complete control over your device via remote access. This aspect of rootkit definition is what makes them so dangerous.
Phishing
Phishing (pronounced "fishing") is an attack through which cybercriminals try to steal money or identity by tricking individuals into disclosing personal information – such as credit card numbers, bank account information, or passwords – on websites that appear to be legitimate. In a phishing mail, cybercriminals often pose as legitimate organizations, friends, or acquaintances and include a link to a phishing website.
IP Spoofing
Spoofing is a sort of cyber-attack in which someone attempts to fool other computer networks by posing as a genuine entity using a computer, device, or network. It's one of several techniques used by hackers to obtain access to computers in order to mine for sensitive data, convert them into zombies (computers taken over for malicious usage), or conduct Denial-of-Service (DoS) assaults. IP spoofing is the most prevalent of the several forms of spoofing.
Ransomware
Ransomware is a type of malware that employs encryption to keep a victim's data hostage in exchange for a charge. A person's or organization's important data is encrypted, making it hard for them to access files, databases, or apps. In order to get access, a ransom is demanded. Ransomware is usually designed to spread over a network and target database and file servers, thus disabling an entire organization in minutes. It is a growing threat that pays out billions of dollars to hackers while creating significant damage and expenditure for businesses and governments.
You can also read about the Layered Architecture in Computer Network.
Frequently Asked Questions
What is Virus?
To infect the user's device, malware needs human input. An email attachment containing dangerous executable code is a classic example. The virus is installed on the device unwittingly when a user gets and opens such an attachment.
What is Worm?
A kind of malware that may infiltrate a device without the user's knowledge. A user may, for example, be running a vulnerable network application to which an attacker could deliver malware. In rare situations, the program may take malware from the Internet and execute it without user involvement, resulting in the creation of a worm.
How to avoid network attacks?
These are some of the fundamental practices to avoid network attacks:
- Create strong passwords and change them regularly
- Delete suspicious emails and don't open those mails
- Use antivirus software
- Use data encryption
- Use a firewall on your network
- Use VPN (Virtual Private Network)
Conclusion
In this article, we discussed what network attacks are and discussed some of the common network attacks. After reading this article, I hope you must have gained some knowledge about different network attacks, which will surely help you prevent them if you ever encounter them.
Recommended Readings:
Check out some of the amazing Guided Paths on topics such as Data Structure and Algorithms, Competitive Programming, Basics of C, Basics of Java, Computer Networks, etc. along with some Contests and Interview Experiences only on Coding Ninjas Studio.
Do check out The Interview guide for Product Based Companies as well as some of the Popular Interview Problems from Top companies like Amazon, Adobe, Google, etc. on Coding Ninjas Studio.
Thank you for reading.







