Introduction
Are you planning to interview for the Security Engineer position at top MNCs??!! This blog will help you tackle Network Security interview questions immensely. Big software corporations have begun to ask some network security interview questions as a part of their hiring process. Therefore it becomes critical to have in-depth knowledge of network security interview questions. Network security plays a crucial role in protecting data, systems, and networks from unauthorized access, cyberattacks, and potential threats. It involves implementing measures such as firewalls, encryption, and intrusion detection systems to safeguard sensitive information and ensure safe communication across networks.
The most vital and likely Network Security Interview Questions will be covered in this article. For your better understanding, we have divided this article into two sections Freshers and Experienced.
Here is a complete list of the top 30 Network Security Interview Questions that will assist you to ace your upcoming Interview. Let's start with some basic questions.

Here is a complete list of the top most asked 30 Network Security Interview Questions that will assist you to ace your upcoming Interview. Let's start with some basic questions.
Network Security Interview Questions for Freshers
This section will get the basic network security interview questions to build a solid foundation. This section is crucial since it establishes a strong base.
1. What is Network Security?
Ans: Network Security is a paradigm that covers establishing and maintaining a secure network and data. It comprises various hardware and software technologies to protect the network against threats. Network protocols play an essential role in maintaining network security. The main aim of network security is to allow authorized users and deny access to unauthorized attackers.
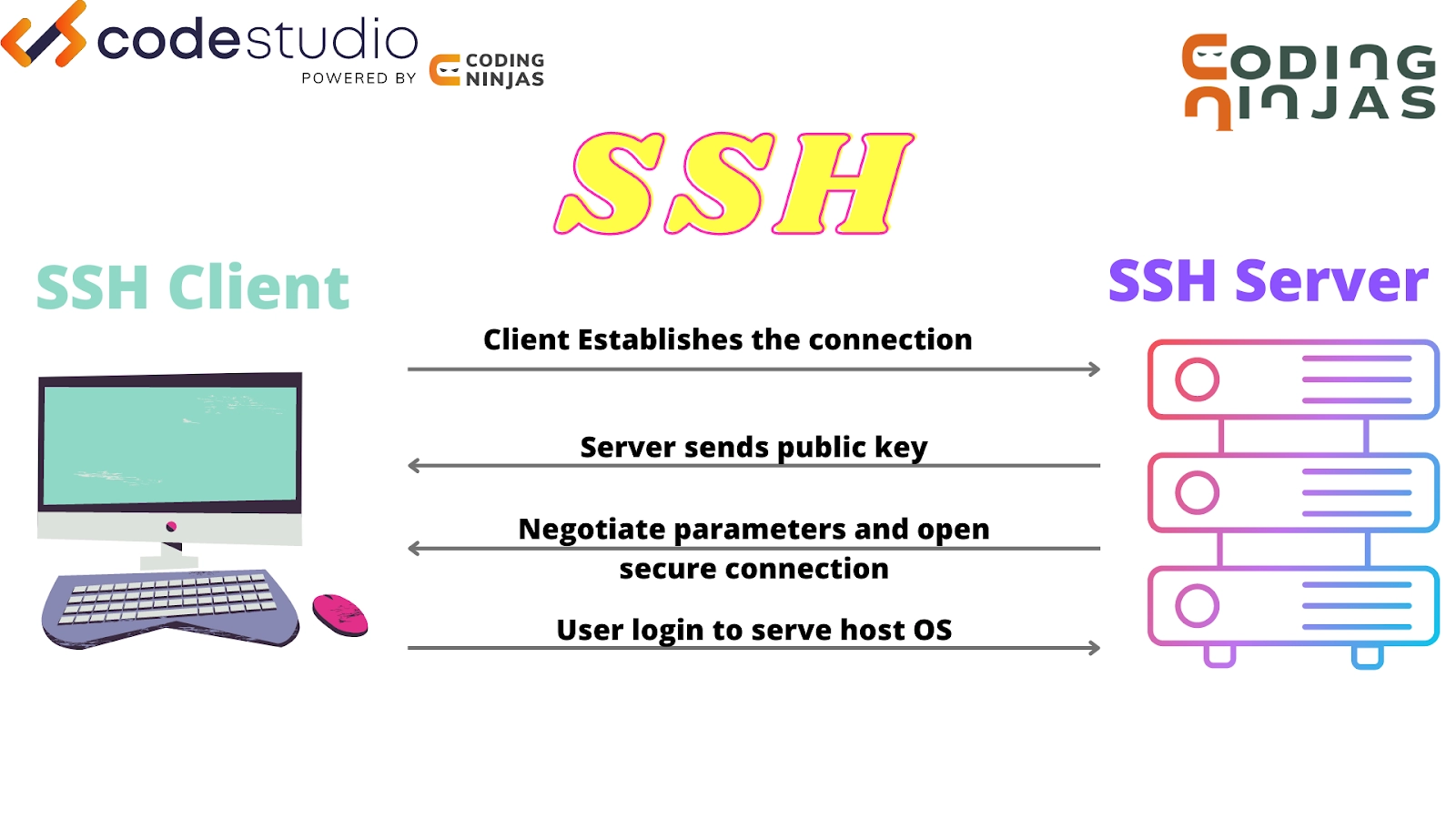
2. What is a Network Protocol?
Ans: A network protocol is a set of standard rules that define how data is transmitted between nodes in the same network. These protocols work regardless of machines internal architecture being different. For example, HTTP, TCP, FTP etc., are commonly used network protocols.
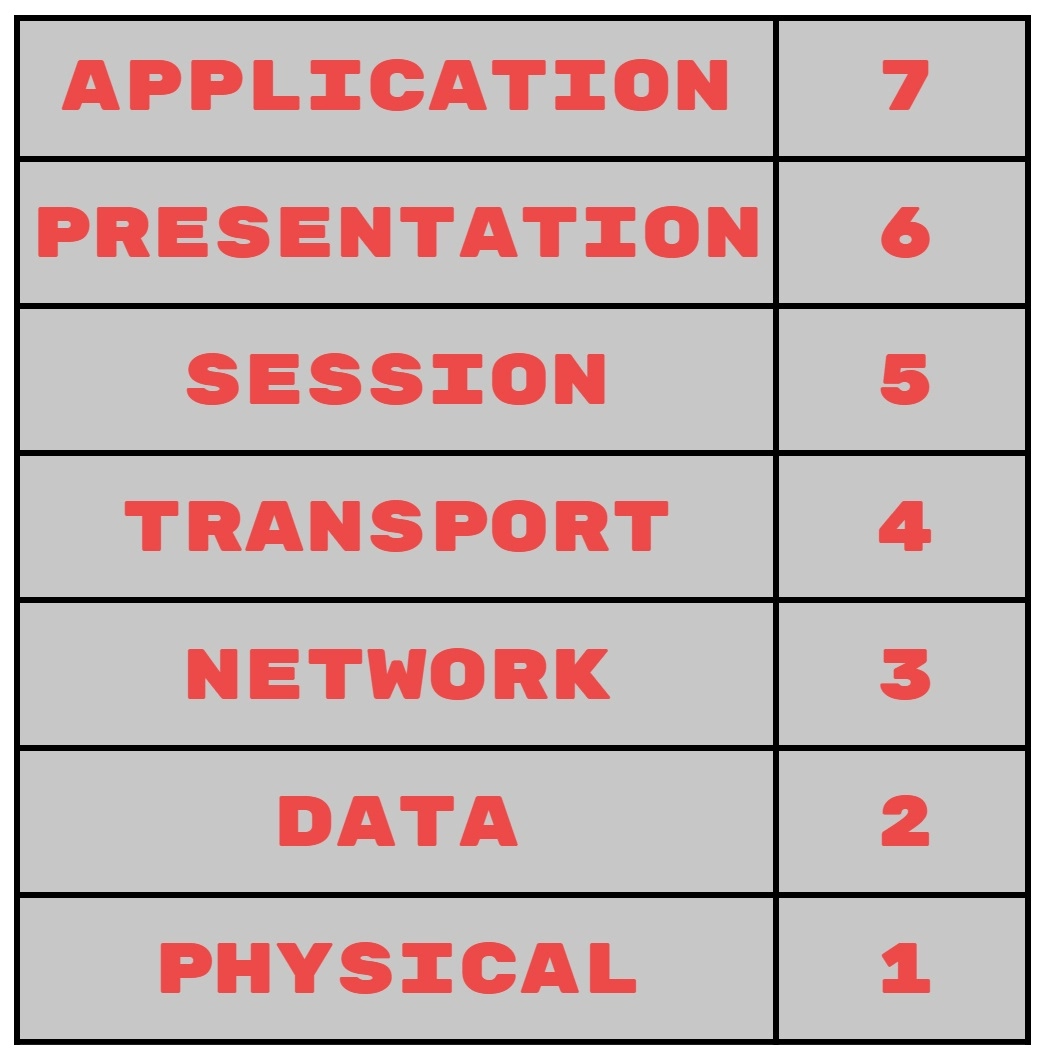
3. What are the various layers of the OSI model?
Ans: The various layers of the OSI model are:
4. How does HTTP handle states?
Ans: HTTP does not handle states. But there is another way around using cookies to manage states.
5. What is a Firewall?
Ans: A firewall is a hardware or software entity that monitors and manages the incoming traffic based on pre-established security policies. It acts as a barrier between the intranet and the public internet.
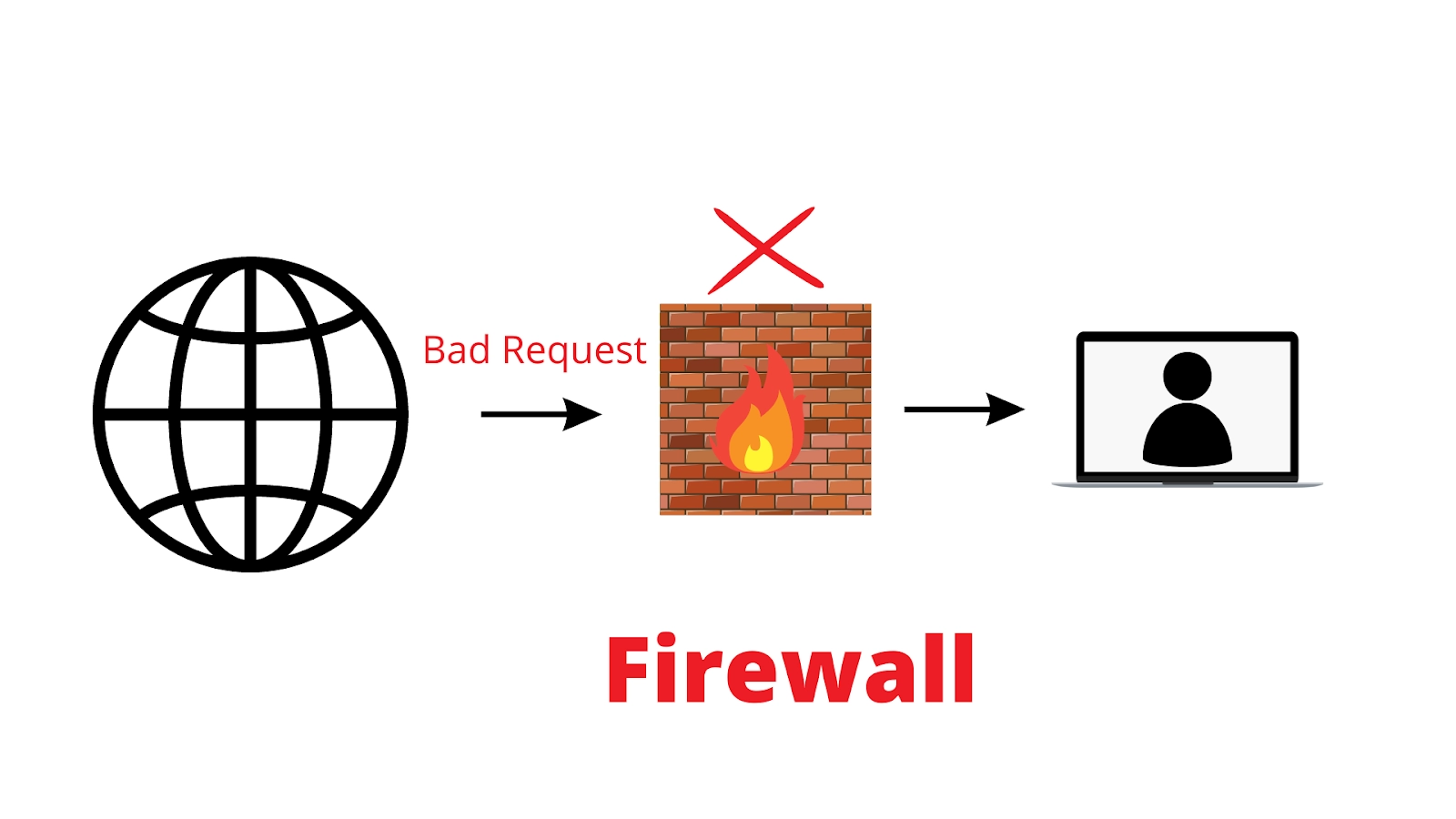
6. What is a proxy firewall?
Ans: A proxy firewall is a network security tool that protects network resources by filtering messages at the application layer. A proxy firewall is also known as an application firewall or gateway firewall.
7. What is a three-way handshake?
Ans: It is a method to create a TCP/IP connection between the host and the client. It involves three steps:
Step - 1: The client sends an SYN packet to the server to check for open ports
Step - 2: The server sends an SYN-ACK back to the client, acknowledging the request
Step - 3: The client sends the final acknowledgment that it has received the response
8. What is an Integrated Circuit Card (ICC)?
Ans: It is an Integrated Circuit (Smart Card) of pocket-size design to fit in small spaces. It can receive input and give the output.
9. What is the difference between simplex and duplex?
Ans: Simplex is a one-way communication, i.e. only one party can send messages. Duplex allows for proper communication where both parties can communicate flawlessly. An example of simplex communication is TV channels; for duplex, it is a telephone call.
10. What is RIP?
Ans: RIP extends to Routing Information Protocol, a simple protocol that exchanges information between the routers.
11. What is encryption?
Ans: Encryption is a method by which plaintext information is converted into unreadable form. The idea is to hide information while transmitting for security purposes. In simpler terms, encryption alters the original data and makes it appear random. It is based on a cryptographic key: a rule agreed upon by both sender and receiver. The study of encryption is called cryptography.
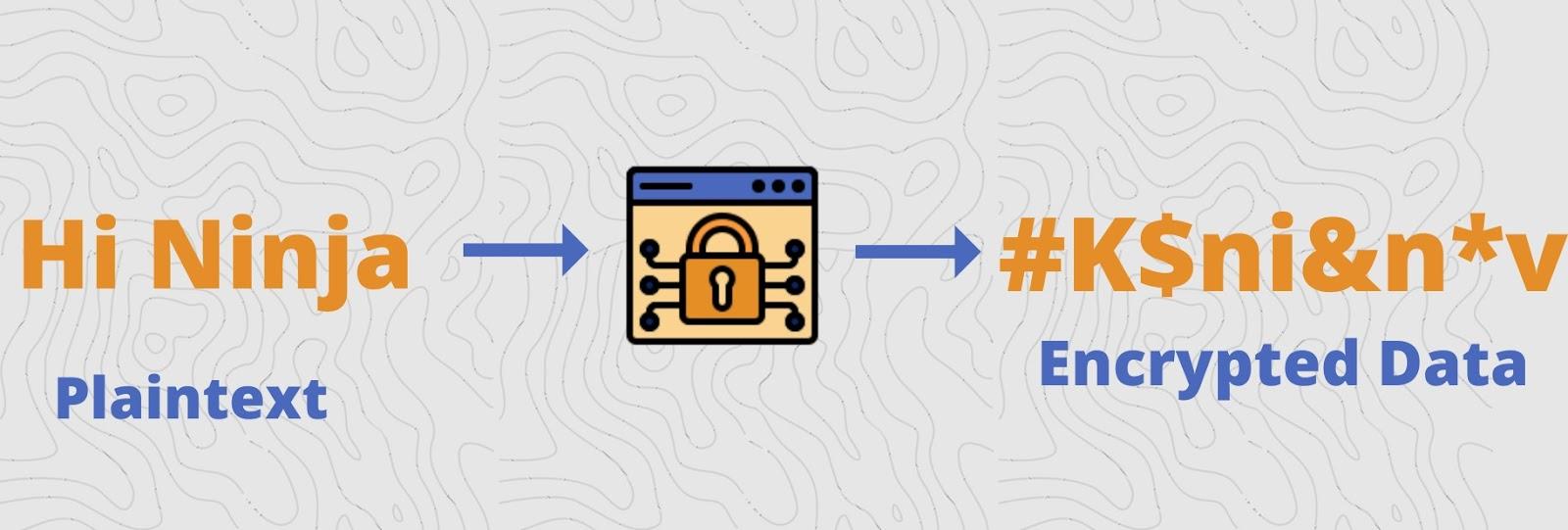
12. How is encryption different from hashing?
Ans: Both encryption and hashing convert readable data to a non-human format. Still, in the case of encryption, data can be converted back into the original form using a cryptographic key, whereas it is impossible in the case of hashing.
13. What is a socket?
Ans: A socket is an end-point of a communication link between two applications on a network. A socket is attached to a port number so that the TCP layer can identify the node that data is destined to be sent. The network API sets the properties of the socket.
14. What is cross-site scripting?
Ans: Cross-site scripting (XSS) is a web security vulnerability that allows attackers to compromise users' interaction with the website. It is done by injecting harmful javascript code by hiding behind the user and gaining control over the user's account on that platform.
15. What is cross-site request forgery?
Ans: Cross-site request forgery (CSRF) is a one-click attack where the website is compromised by unintentionally submitting malicious code by a trusted user. It allows an attacker to partly bypass the same origin policy, which is designed to prevent different websites from interfering with each other.
16. What is Two-Factor Authentication (2FA)?
Ans: Two-Factor Authentication (2FA) is a security process where users provide two different authentication factors to verify their identity. Typically, this involves something the user knows (password) and something they possess (e.g., a phone with an authentication app or a text message code). This adds an extra layer of security by reducing the risk of unauthorized access.
17. What is the role of a VPN in network security?
Ans: A Virtual Private Network (VPN) creates a secure connection between a user’s device and the internet, encrypting the data transmitted. It protects user information from hackers, especially when using public Wi-Fi networks, and helps maintain privacy by hiding the user’s IP address.
18. What is a Denial-of-Service (DoS) attack?
Ans: A Denial-of-Service (DoS) attack occurs when a hacker floods a network or server with excessive traffic, causing it to slow down or crash, making it inaccessible to legitimate users. It’s a form of cyberattack that disrupts normal operations of the system.
19. What is a security policy in a network?
Ans: A security policy is a document that outlines the rules, practices, and guidelines for securing network systems and data. It defines how to protect the network, control access, and respond to security incidents, ensuring the confidentiality, integrity, and availability of information.
20. What are vulnerabilities in network security?
Ans: Vulnerabilities are weaknesses or flaws in software, hardware, or network configurations that can be exploited by attackers to gain unauthorized access to a system. Identifying and fixing vulnerabilities is critical to strengthening network security and preventing attacks.