Introduction
This is where a firewall, being the sole point of defence between the external and internal network, comes into the picture. Even though firewalls have been around for nearly three decades, it is just recently that they’ve dramatically evolved to cater to the demands of the internet.
Diminishing boundaries between the physical and virtual worlds in the past decade, expedited by the latest technological advancements, has transformed the way we humans function in unprecedented ways. In 2020, India’s internet population has reached around 700 million users and is projected to reach a billion within the next 10 years.
With such a massive market yet to be tapped into, many large thriving businesses are trying to penetrate into the Indian markets and gain a monopoly while the barrier to entry is still low. While some are trying to make the internet more accessible or phones much cheaper, others are trying to build software or take their businesses online to leverage the opportunity provided by the internet.
However, these technological advancements, when provided to the ones who do not understand how easily this boon can turn into a bane, can have some serious ramifications. When someone connects their private network to the internet, not only do they provide the users in the network access to the Internet services, but also the outsiders the means to access the network’s private information.
What is a Firewall?
According to Cisco, ‘A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.’ It can either be implemented as a software, as hardware or as a combination of both or can even be hosted on the cloud.
Contrary to what its name might suggest, a firewall is not a wall that is on fire, but one that stands strong to protect the integrity, confidentiality and availability of the information in the network segment. Thus, a firewall analysis all the traffic that passes through it and filters out the ones which seem dangerous based on a certain set of predefined rules. Analogically, a firewall can be compared to a security guard of a society who analyses all the people who want to enter the society and bars those who seem like a potential threat.
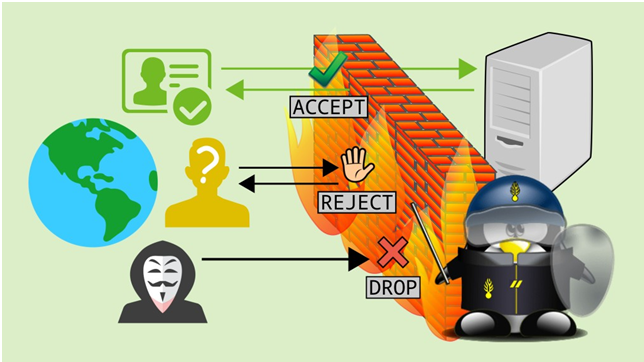 Source: Linux Kamarada
Source: Linux Kamarada
Based on the nature off the incoming traffic, a firewall either accepts the traffic, rejects it or drops it. By default, firewalls follow an “implicit deny” rule, wherein they deny all the requests against which the predefined rule doesn’t exist. Hence, configuring a firewall is a complicated task since a traffic stringency balance has to be maintained. If a firewall is very stringent with what it allows, it might lead to inaccessibility of useful resources. On the other hand, if the firewall is not very stringent, it might allow potentially dangerous traffic to flow.
Thus, a firewall extends many functionalities to the underlying network. It limits the points of entry into a network, controls the traffic flowing through it and maintains the privacy of the internal network. Due to the complexity and variety of use cases, a plethora of firewalls exist. One should assess their requirements before finalising upon which firewall would best suit their needs. But before diving deeper into the different types, let’s first understand what the components of a firewall are and how does it work.




