Introduction
The National Eligibility Test (NET) is conducted on behalf of the University Grants Commission (UGC) to determine the eligibility of Indian nationals for the Eligibility of Assistant Professorship, Junior Research Fellowship, or both for Indian Universities and Colleges. In this blog, we will go through the questions and solutions of June 2014 Paper-II of UGC - NET EXAM. In this blog, we have covered questions from 26-50. For questions from 1-25 refer to Nov 2017 Paper III Part 1 and from 51 - 75 refer to Nov 2017 Paper III Part 2.
Questions
51. User-level threads are threads that are visible to the programmer and are unknown to the kernel. The operating system kernel supports and manages kernel-level threads. Three different types of models relate to the user and kernel-level threads.
Which of the following statements is/are true?
(a) (i) The Many - to - one model maps many user threads to one kernel thread
(ii) The one-to-one model maps one user thread to one kernel thread
(iii) The many-to-many model maps many user threads to smaller or equal kernel
threads
(b) (i) Many-to-one model maps many kernel threads to one user thread
(ii) One-to-one model maps one kernel thread to one user thread
(iii) Many-to-many model maps many kernel threads to smaller or equal user
threads
Code :
(1) (a) is true; (b) is false
(2) (a) is false; (b) is true
(3) Both (a) and (b) are true
(4) Both (a) and (b) are false
Answer - 1
Solution -
(a) (i) The many–to–one model maps many user threads to one kernel thread; (ii) The one–to–one model maps one user thread to one kernel thread; (iii) The many–to–many model maps many user threads to smaller or equal kernel threads; (iv) The many – to – many models maps many user threads to a smaller or equal kernel thread
(b)
(i) The many-to-one model translates multiple kernel threads to a single user thread.
(ii) The one-to-one paradigm assigns a single kernel thread to a single user thread.
(iii) The many-to-many model translates a large number of kernel threads to lesser or equal numbers of user threads.
Every statement is correct.
Option (1) is therefore correct.
52. Consider a system with five processes P0 through P4 and three resource types A, B, and C. Resource type A has seven instances, resource type B has two instances and resource type C has six instances suppose at time T0 we have the following allocation.
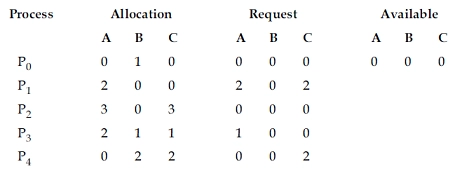
If we implement the Deadlock detection algorithm we claim that system is ..................
(1) Semaphore
(2) Deadlock state
(3) Circular wait
(4) Not in a deadlock state
Answer - Marks to all
Solution - The deadlock detection algorithm looks at all conceivable allocation sequences for the remaining processes.
The total amount of resources allocated to all resource type B processes does not match the amount specified in the query. If we disregard the statement and assume that the tables are correct, the solution is as follows:
Processes P0 and P2 have been given all of their resources and will so run until they are finished. They will hand up the resources they were given. This is the current situation:
A = 3 B = 1 C = 3 are the options.
P1 P3 P4 are the remaining processes.
P1 requires the following: A = 2 B = 0 C = 2
We are capable of fulfilling its request. It will be given all of the resources it requires and will run until it is completed. It will then hand over all of its assets. This is the situation now:
A = 5 B = 1 C = 3 are the options.
P3 and P4 are the remaining processes.
Similarly, P3 will be done first, followed by P4.
53. Consider a disk queue with requests for I/O to blocks on cylinders 98, 183, 37, 122, 14, 124, 65, 67. Suppose the SSTF disk scheduling algorithm is implemented to meet the requests then the total number of head movements is................... if the disk head is initially at 53.
(1) 224
(2) 248
(3) 236
(4) 240
Answer - 3
Solution - add all seek time:
12+2+30+23+84+24+2+59=236
So, option (C) is correct.
54. The Bounded buffer problem is also known as ..................
(1) Producer - consumer problem
(2) Reader - writer problem
(3) Dining Philosophers' problem
(4) Both (2) and (3)
Answer - 1
Solution - A famous example of concurrent access to a shared resource is the bounded-buffer problem (also known as the producer-consumer problem). Multiple producers and consumers can share a single buffer using a bounded buffer. Data is written to the buffer by producers, and data is received from the buffer by consumers.
If the buffer is filled, producers must block.
If the buffer is empty, consumers must block it.
55. In Artificial Intelligence (AI), which agent deals with the happy and unhappy states?
(1) Simple reflex agent
(2) Model-based agent
(3) Learning agent
(4) Utility-based agent
Answer - 4
Solution - In AI, a Utility-based agent deals with the happy and unhappy states.
56. If b is the branching factor and m is the maximum depth of the search tree, what is the space complexity of the greedy search?
(1) O(b+m)
(2) O(bm)
(3) O(bm)
(4) O(mb)
Answer - 3
Solution - The branching factor in a binary tree is 2 and the space complexity for height n is O(2n).
The branching factor in a ternary tree is 3 and the space complexity for height n is O(3n).
Similarly,
The space complexity of the greedy search is O if the branching factor is b and the height of the search tree is O(bm).
57. Let P, Q, R and S be Propositions. Assume that the equivalences P⇔(Q∨¬Q) and Q⇔R hold. Then the truth value of the formula (P∧Q)⇒((P∧R)∨S) is always :
(1) True
(2) False
(3) Same as truth table of Q
(4) Same as truth table of S
Answer - 1
Solution - P ⇔ (Q ∨ ¬ Q) "P should be true because RHS will always be TRUE."
Q ⇔ R "When Q is true, R is true," and "when Q is false, R is false," respectively.
(P∧Q)⇒((P∧R)∨S)
There can only be two cases. (the value of S is irrelevant)
1) P, Q, and R all equal True.
(T∧T)⇒((T∧T)∨S)
As a result, this case is correct.
2) P = True, Q = False, R = True
(T∧F)⇒((P∧R)∨S)
If one of the premises is untrue, the entire assertion is false.
This is also the case.
In both circumstances, the supplied expression is True.
58. “If X, then Y unless Z” is represented by which of the following formulae in propositional
logic?
(1) (X ∧ Y) → ¬ Z
(2) (X ∧ ¬ Z) → Y
(3) X → (Y ∧ ¬ Z)
(4) Y → (X ∧ ¬ Z)
Answer - 2
Solution - If Z does not occur, the sentence "If X then Y except Z" states that if Z does not occur, X implies Y, i.e. Z→(X→Y), which is identical to Z ∨ (X→Y).
(because P→Q ≡ ¬P ∨ Q), which is thus similar to Z ∨ (¬X ∨ Y).. Now we may investigate which choices are compatible with this.
Option (a) is (X∧¬Z)→Y = ¬( (X∧¬Z) ) ∨ Y = (¬X∨Z) ∨ Y, which is the same as our formula. As a result, option (A) is correct.
59. Consider the following two well-formed formulas in prepositional logic.
F1 : P ⇒ ¬ P
F2 : (P ⇒ ¬ P) ∨ (¬ P ⇒ P)
Which of the following statements is correct?
(1) F1 is Satisfiable, F2 is valid
(2) F1 is unsatisfiable, F2 is Satisfiable
(3) F1 is unsatisfiable, F2 is valid
(4) F1 and F2 both are Satisfiable
Answer - 1
Solution - F1:P→¬P
=¬P∨¬P
=¬P. can be true when P is false ( Atleast one T hence satisfiable)
F2:(P→¬P)∨(¬P→P)
=¬P∨(P∨P)
=¬P∨P
=T.
VALID
60. Standard planning algorithms assume environment to be .................
(1) Both deterministic and fully observable
(2) Neither deterministic nor fully observable
(3) Deterministic but not fully observable
(4) Not deterministic but fully observable
Answer - 1
Solution - Standard planning algorithms assume the environment to be both deterministic and fully observable.
61. Which of the following statements is not correct?
(1) Every recursive language is recursively enumerable.
(2) L = {0n 1n 0n | n=1, 2 , 3, ....} is recursively enumerable.
(3) Recursive languages are closed under intersection.
(4) Recursive languages are not closed under intersections.
Answer - 4
Solution - Recursive languages are closed under intersection.
62. Context-free grammar is not closed under :
(1) Concatenation
(2) Complementation
(3) Kleene Star
(4) Union
Answer - 2
Solution - CFG is not closed under complementation, set difference and intersection, but instead it is closed under union, concatenation, Kleen closure, reversal, product etc.
63. Consider the following languages :
L1 = {am bn | m ≠ n}
L2 = {am bn | m = 2n+1}
L3 = {am bn | m ≠ 2n}
Which one of the following statement is correct?
(1) Only L1 and L2 are context-free languages
(2) Only L1 and L3 are context-free languages
(3) Only L2 and L3 are context-free languages
(4) L1, L2, and L3 are context-free languages
Answer - 4
Solution - In L1, we must ensure that m does not equal n. There are an endless number of nodes that fall into this category, but we only have one comparison with m and n. As a result, it is a context-free language.
In L2, one comparison with unlimited m and n possibilities is also a CFL.
In L3, one comparison with unlimited m and n possibilities is also a CFL.
64. A 4×4 DFT matrix is given by :
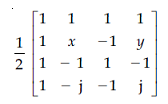
(j2=−1)
Where values of x and y are ..........., ............. respectively.
(1) 1, −1
(2) −1, 1
(3) −j, j
(4) j, −j
Answer - 4
Solution -
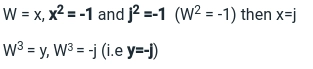
Hence the answer is j, -j.
65. Entropy of a discrete random variable with possible values {x1, x2, ..., xn} and probability density function P(X) is :
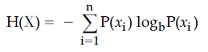
The value of b gives the units of entropy. The unit for b=10 is :
(1) bits
(2) bann
(3) nats
(4) deca
Answer - Marks to all
Solution - bits is units of entropy for b = 2
66. For any binary (n, h) linear code with minimum distance (2t+1) or greater
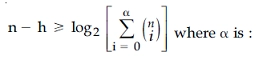
(1) 2t+1
(2) t+1
(3) t−1
(4) t
Answer - 4
Solution - The correct answer for alpha is t, for any binary (n, h) linear code with minimum distance (2t+1) or greater than the given equation.
67. Which of the following is a valid reason for causing degeneracy in a transportation problem? Here m is no. of rows and n is no. of columns in the transportation table.
(1) When the number of allocations is m+n−1.
(2) When two or more occupied cells become unoccupied simultaneously.
(3) When the number of allocations is less than m+n−1.
(4) When a loop cannot be drawn without using unoccupied cells, except the starting cell of the loop.
Answer - 3
Solution - When the number of allocations is smaller than m+n1, the transportation problem degenerates.
Option (C) is thus correct.
68. Consider the following LPP :
Max Z=15x1+10x2
Subject to the constraints
4x1+6x2 ≤ 360
3x1+0x2 ≤ 180
0x1+5x2 ≤ 200
x1, x2 ≥ 0
The solution of the LPP using Graphical solution technique is :
(1) x1=60, x2=0 and Z=900
(2) x1=60, x2=20 and Z=1100
(3) x1=60, x2=30 and Z=1200
(4) x1=50, x2=40 and Z=1150
Answer - 2
Solution - The correct answer is x1=60, x2=20 and Z=1100.
69. Consider the following LPP :
Min Z=2x1+x2+3x3
Subject to :
x1−2x2+x3 ≥ 4
2x1+x2+x3 ≤ 8
x1−x3 ≥ 0
x1, x2, x3 ≥ 0
The solution of this LPP using Dual Simplex Method is :
(1) x1=0, x2=0, x3=3 and Z=9
(2) x1=0, x2=6, x3=0 and Z=6
(3) x1=4, x2=0, x3=0 and Z=8
(4) x1=2, x2=0, x3=2 and Z=10
Answer - 3
Solution - Method of "hit and run"
Put the following values in the options in the question's equations and see which option satisfies the equations; only one will meet the criteria.
x1-2x2+x3>=4
In this equation, enter the values for options c and d.
Put the values in other equations and you'll see that it satisfies.
Option c and d both satisfy in this question, however since the objective function is minimization, option c is the correct answer.
70. Consider a Takagi - Sugeno - Kang (TSK) Model consisting of rules of the form :
If x1 is Ai1 and ... and xr is Air
THEN y =fi(x1, x2, ..., xr) = bi0+bi1 x1+...+bir xr
assume, αi is the matching degree of rule i, then the total output of the model is given by:
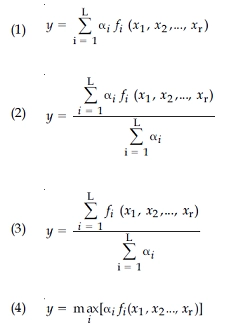
Answer - 2
Solution - The answer for the above question is option 2.
71. Consider a single perceptron with sign activation function. The perceptron is represented by weight vector [0.4 −0.3 0.1]t and a bias θ=0. If the input vector to the perceptron is X=[0.2 0.6 0.5] then the output of the perceptron is :
(1) 1
(2) 0
(3) −0.05
(4) −1
Answer - 4
Solution - P=1, if P>0
P=-1, if P<0
P=0, if P=0
since value of P is -0.05(<0), so output is -1
Where P represents perceptron and P=∑wi⋅xi.
72. The Sigmoid activation function f(t) is defined as :
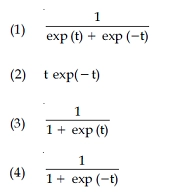
Answer - 4
Solution - A sigmoid function is a mathematical function with a distinctive "S"-shaped curve, sometimes known as a sigmoid curve. The logistic function, which is represented in the first graphic and defined by the formula:
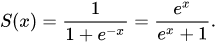
73. Consider the following statements :
(a) UNIX provides three types of permissions
* Read
* Write
* Execute
(b) UNIX provides three sets of permissions
* permission for owner
* permission for group
* permission for others
Which of the above statement/s is/are true?
(1) Only (a)
(2) Only (b)
(3) Both (a) and (b)
(4) Neither (a) nor (b)
Answer - 3
Solution - UNIX allows you to read, write, and execute files.
UNIX provides three permission sets.
permission for owner
permission for group
permission for others
74. Which of the following routing techniques/techniques is/are used in distributed systems?
(a) Fixed Routing
(b) Virtual Routing
(c) Dynamic Routing
Code :
(1) (a) only
(2) (a) and (b) only
(3) (c) only
(4) All (a), (b), (c)
Answer - 4
Solution - The distributed system uses a fixed routing technique. Dynamic and virtual routing is not used in a distributed system.
75. Match the following WINDOWS system calls and UNIX system calls with reference to process control and File manipulation.
Windows
(a) Create - process () system call
(b) WaitForSingleObject () system call
(c) CreateFile () system call
(d) CloseHandle () system call
UNIX
(i) Open () system call
(ii) Close () system call
(iii) fork() system call
(iv) Wait () system call
Code :
(a) (b) (c) (d)
(1) (iii) (iv) (i) (ii)
(2) (iv) (iii) (i) (ii)
(3) (iv) (iii) (ii) (i)
(4) (iii) (iv) (ii) (i)
Answer - 1
Solution -
Windows (system-call) |
Unix (system-call) |
| Create-Process() | Fork() |
| WaitForSingleObject() | Wait() |
| CreateFile() | Open() |
| CloseHandle() | Close() |




