Examples of OAuth
Smart home appliances, security systems, etc., sync using some login data called confidential authorization so that users can administer them from a single browser without having to log in repeatedly.
In the virtual world, one website using another’s login is the simplest example. If some application like Pinterest wants users to sign in, they can sign in by submitting their email, name and password or through Facebook. Since Facebook already has their login data, it will act as a service provider for the consumer app Pinterest and specifically share just the users’ login info (which OAuth manages in the background). In case the authorization fails to take place, Pinterest will show the following error message:
Source: Pinterest
SAML vs OAuth
Security Assertion Markup Language, also known as SAML, is an alternative authentication standard used by several enterprises for Single-Sign-On or SSO. It lets enterprises monitor who has access to corporate resources.
While OAuth uses JSON to pass messages, SAML uses XML. Users can expect a simpler mobile experience with OAuth, while SAML is inclined towards providing enterprise security. Despite a list of differences, the final one is the critical differentiator: Web apps, mobile applications, game consoles, and smart devices prefer OAuth as a better option because OAuth extensively uses API calls. On the other hand, SAML does not seem very convenient when users have to log in every day and only allows access to web pages by dropping a session cookie in a browser.
Working of OAuth
In an OAuth transaction, there is the user, the service provider and the consumer.
OAuth is not about authentication but authorization. While authorization means asking for permission to perform a task, authentication merely proves that the user is the correct person. OAuth only acts as an authorization token and does not pass any authentication data. The following steps take place when the authorisation has to take place:
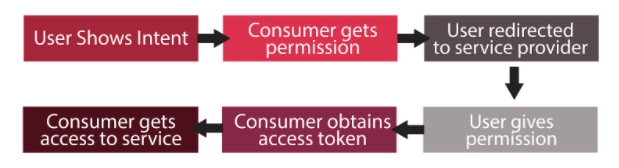
OAuth verifies the identity of users and grants permissions to a third party using tokens. Tokens are used by the third party to access resources on the user’s behalf. However, the tokens’ scope decides whether a particular resource is accessible to a user or not. Access tokens are like key cards for hotel rooms that let us access our rooms, gym, or spa. Just like key cards validate our identity, access tokens are presented to validate the users’ credentials, allowing them to enter.
OAuth 1.0 vs OAuth 2.0
OAuth 1.0 and OAuth 2.0 are incompatible. OAuth 1.0 used complex cryptography, supported just three flows and could not scale. On the other hand, OAuth 2.0 allows signed secret information over HTTPS and has the double, i.e., six flows for various kinds of apps. OAuth tokens do not need endpoint encryption as they are encrypted in the transit itself. Since OAuth 2.0 is a total redesign of OAuth 1.0, it only makes sense to use OAuth 2.0 in any new application that will be created from now on.
Frequently Asked Questions
Q1. Is OAuth 2 authentication or authorization?
Ans. OAuth 2.0 is a framework that allows users to give access to a website or app via a previously logged in authentication provider. Its purpose is, therefore, just for authentication.
Q2. What is the difference between bearer tokens and OAuth2?
Ans. After the users authenticate the consumer app, the authentication server generates a token. Bearer tokens are these predominant access tokens used with OAuth, while OAuth itself is an authentication framework.
Q3. What is JWT based authentication?
Ans. JSON Web Token can be used to transfer JSON encoded claims between two parties. These claims are signed digitally by the party issuing the token, and the receiving party can use this signature to prove the ownership of the claim.
Q4. Is JWT better than OAuth?
Ans. While JWT has a quick and straightforward implementation, OAuth is very flexible. OAuth is preferred if the application requires flexibility, but JWT must be preferred if that is not the case and users want to save up on time.
Key takeaways
In this article, we learned about OAuth in detail, its comparison with SAML and its working with the help of illustrative examples. We also learned how the new OAuth 2.0 is different from the older version while discussing how it is a significantly better choice today.
You can go to Coding Ninjas Studio to try and solve more problems for practice. Share this blog with your friends if you found it helpful! Until then, All the best for your future endeavours, and Keep Coding.







