Introduction
Compute Engine VMs operate with their memory encrypted with Google Cloud's Confidential Virtual Machine (Confidential VM) service, giving extra security against accidental data access while in operation. Confidential VMs are more trustworthy than normal VMs for various threat models, allowing them to be utilized for sensitive tasks.
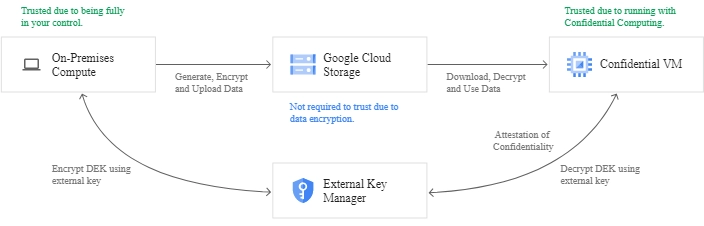
Let us understand these Confidential VMs in depth.
Creating a Confidential VM instance
Considerations
- Confidential VM does not support live migration.
- Confidential Computing can only be enabled on a VM when it is first created.
- Check to see whether regions and zones are compatible with Confidential VM.
Before you Start
- Create an account if you're new to Google Cloud to see how our products function in real-world circumstances. In addition, new clients receive $300 in free credits to run, test, and deploy workloads.
- Select or create a Google Cloud project through the Google Cloud console's project picker page.
- Check that billing for your Cloud project is enabled.
- Enable the Compute Engine API.
Create a Confidential VM instance
Complete the following steps to establish a Confidential VM.
- Navigate to the VM Instances page in the console.
- Choose Create instance.
- Check the Confidential VM Service box.
-
Examine the modified parameters when you activate the service in the Enable Confidential Computing service window. If the following fields are set to incompatible values, they can be included.
- Series and Machine type.
- Region and zone.
- Boot disk image.
- On host maintenance.
- Network interface card.
- Click Enable.
-
Using the AMD EPYC Milan processor (optional).
- Go to the Machine setup area to configure your instance for the AMD EPYC Milan Processor.
- Select AMD Milan or later, after expanding CPU Platform and GPU.
- Check that you are OK with these options, then click Create.
You're taken back to the VM instances page, where you may check the status and information of your new instance. When you see a green checkmark next to Status, your new Confidential VM is ready to use.
Enabling higher network bandwidth for C2D machine types
High-bandwidth networking is supported by the three biggest C2D Compute Engine VM shapes (32, 56, and 112). When you choose a Tier 1 network capacity configuration, the egress bandwidth is increased from 32 Gbps to 50 or 100 Gbps. The instance must be running the gVNIC virtual network driver to attain the higher Tier 1 bandwidth speeds.
Verify AMD SEV is enabled
To confirm that AMD SEV is active for your VM, follow the steps below to login to your instance and then inspect the dmesg log.
- Navigate to the VM Instances page in the console.
- Locate the row for your new Confidential VM instance in the table on the Instances page.
- Click SSH in the same row to open a terminal window for dealing with your Confidential VM instance.
-
Running the dmesg command in the terminal window on various Linux distributions may allow you to confirm that the Confidential VM instance is utilizing AMD SEV.
dmesg | grep SEV | head
You should get a response indicating that AMD Secure Encrypted Virtualization (SEV) is active.
Verify the identity token of a Confidential VM
Your applications can request the VM's unique identity token from the metadata server before transferring any sensitive information to the VM instance. The identity token contains instance-specific information such as the instance ID, creation time, and licensing codes for the instance's pictures. The token also includes a claim that may be used to determine whether the VM is secret. The instance confidentiality claim for a Confidential VM has a value of 1.