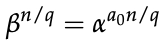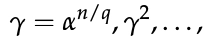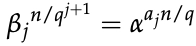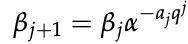Introduction
Discrete logarithms are set-theoretic counterparts of regular algorithms in mathematics, notably in abstract algebra and its applications. A solution of the equation ax = b over the real or complex number is an ordinary algorithm loga(b). This article's blog incorporates information about how Pohlig and Hellman joined forces for the Pohlig–Hellman algorithm. Let's get started.

Know the minds behind the force:
Albert Einstein rightly said, "Everybody knows that something cannot be done until somebody shows up not knowing this and does it." To solve discrete logarithm problems like finding x in h=gx, utilize Pohlig-Logarithm Hellman's algorithm. The great minds of Stephen Pohlig and Martin Hellman came together to make this algorithm.
Stephen Pohlig

Stephen Pohlig, born on April 14, 1953, was an MIT Lincoln Laboratory electrical engineer. As a doctoral student of Martin Hellman at Stanford University, he helped create the principles of Diffie-Hellman key exchange, such as the Pohlig-Hellman exponentiation cipher and the Pohlig-Hellman algorithm for calculating discrete logarithms. That cipher is a forerunner of RSA (Rivest, Shamir, and Adleman) because all that is required to convert it to RSA is to change the arithmetic from modulo a prime integer to modulo a composite number.
Martin Edward Hellman

Martin Edward Hellman, born on October 2, 1945, is a mathematician and cryptologist best known for his work on public key cryptography alongside Whitfield Diffie and Ralph Merkle. Hellman has long been involved in the computer privacy debate and has used risk analysis to predict the breakdown of nuclear deterrence. Hellman was elected to the NAE in 2002 for his contributions to cryptography theory and practice.