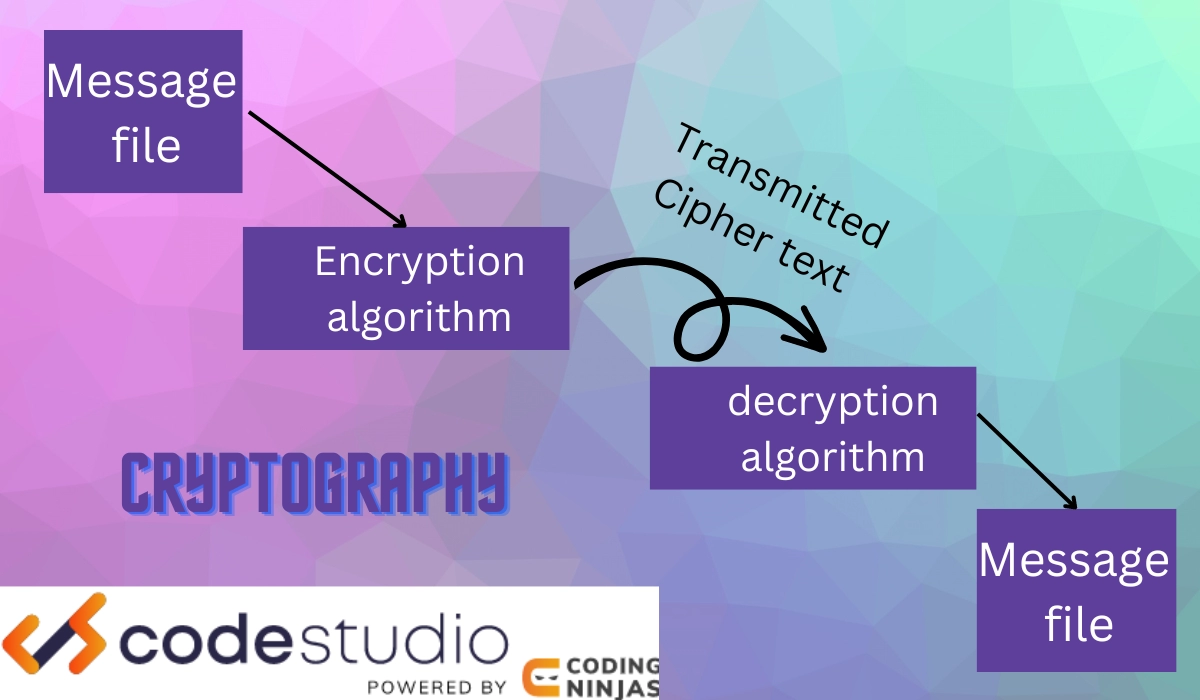
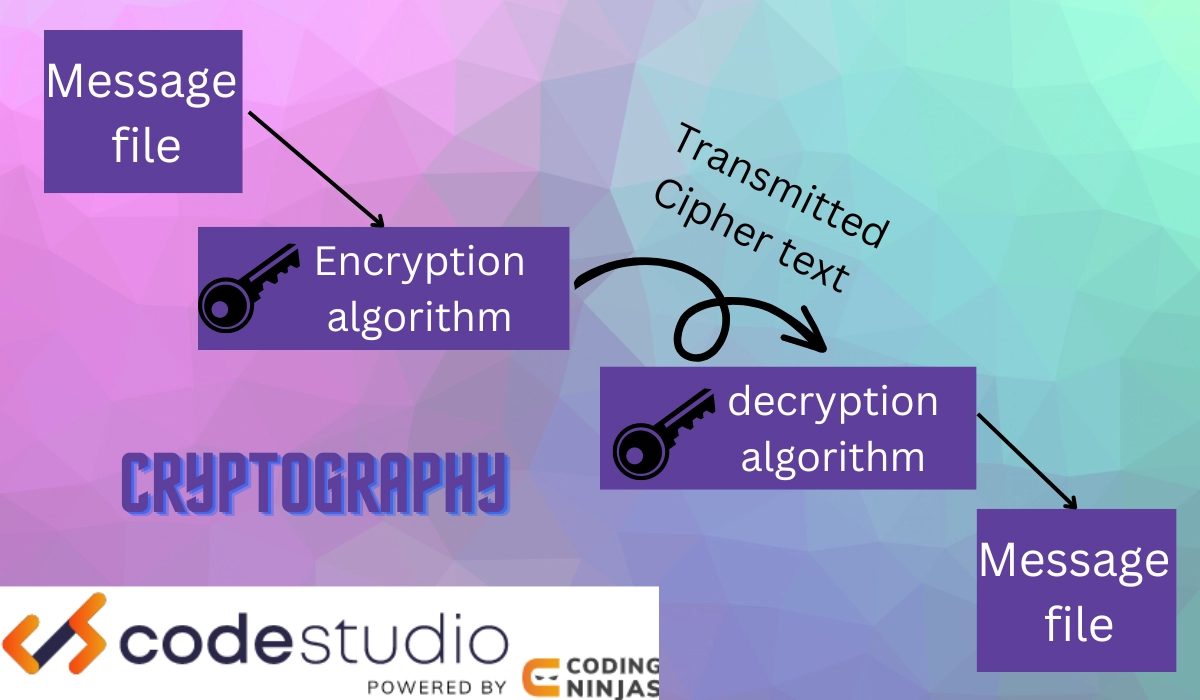
Hash Functions
Hash functions in cryptography are used to create authentic and confidential messages.
Hash Functions in cryptography generate a code to check the message's authenticity. In layman's language, we say that any document is hashed (passes through a hash function) to develop a hash value(code) using a hash function in cryptography.
The hash value is also called a message digest.
As discussed in the previous section, we require a message, keys, and function in general to perform any type of authentication. Hash functions are a bit different.
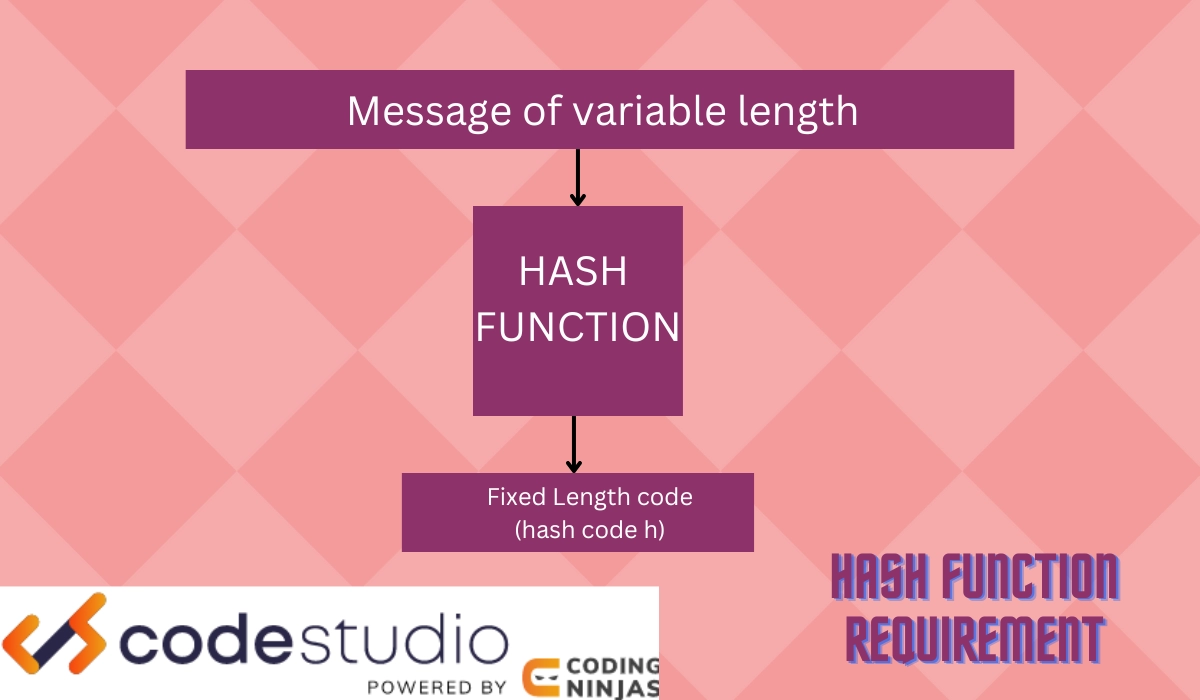
H(M)= fixed length code (hash code h)
Where “H” is the hash function,
“M” is the message,
“h” is the hash value or code(message digest).
Working of Hash Functions
The working of a hash function depends on three main elements.
- Hash function
Functions that create hash codes for senders and receivers to access data files for transferring are called hash functions.
- Message
Message refers to the data information that is to be transferred.
- Hash code (message digest)
You can consider this as a password that the sender generates and encrypts within the message to be transferred. The receiver decrypts the code within the message and generates one separately. If both codes match, message authentication is received.
These three work together to provide authentication as follows.
- The message goes through a hash function.
- The function creates a hash code “h.”
- The hash code and messages are combined.
- We again use a hash function when the message is received to generate a hash code.
- If it matches the received hash code, the message is authentic.
- We might use encryption and decryption with or without keys to developing confidentiality and security.
A pictorial representation of this operation is given below.
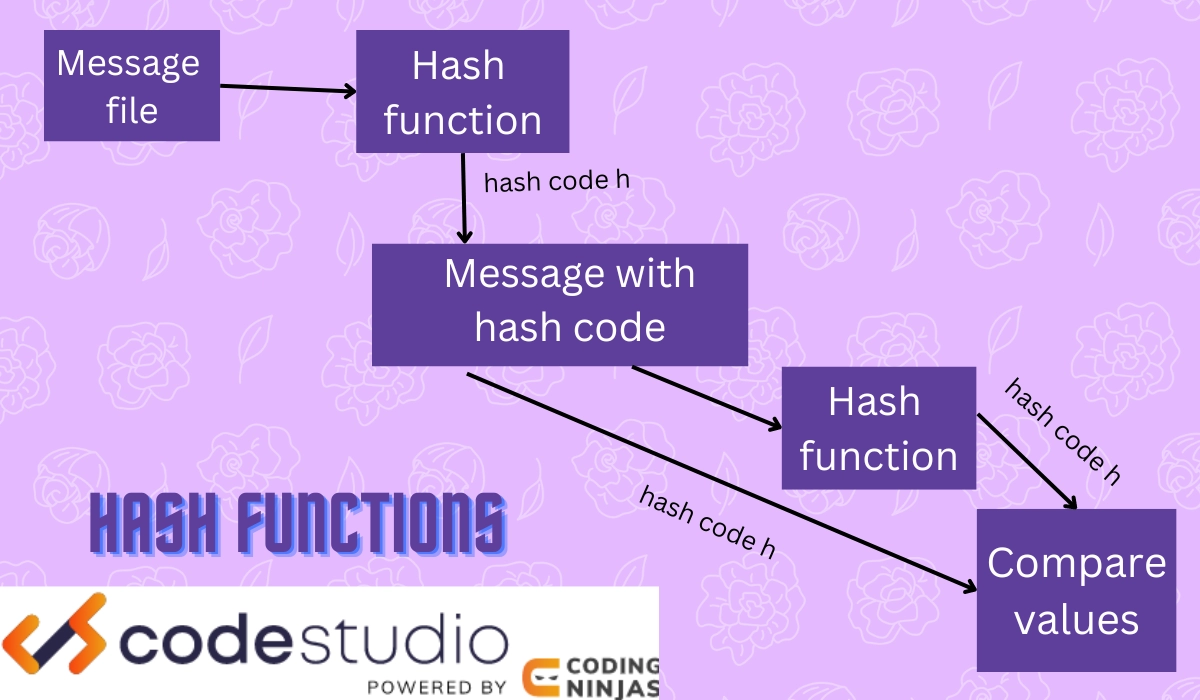
As you can decipher by now, we need a function to create a hash code for the message for authentication.
Properties of Hash Functions
A few essential properties of hash functions are crucial for the security of hash functions in cryptography.
These are as follows:
- Hash functions can take a message input of any length.
- The output of the hash function is always fixed-sized.
- You cannot infer the input with the help of output.
- Hash functions are one-way.
- It is highly efficient because computing H(M)=h is easy.
- Works for software and hardware both.
The above-given properties are a few basic properties that affect the security of hash functions in cryptography. We will further discuss how it can be achieved in detail.
System Security
System security of hash functions in cryptography is a crucial and essential task.
A system is never entirely secure even after such development of technology in today’s date. To transfer confidential messages, we need to ensure the security of hash functions in cryptography.
Two essential features that affect the system security of hash functions in cryptography are:
- Threat
These are caused when there is damage caused to the system due to a program like viruses.
- Attack
This is caused when a person tries to crack into the system unauthorized for ill purposes.
You need to make sure your system is free of any threats. A hash function is sufficient enough to keep your system free from attackers. This will ensure the system's security of hash functions in cryptography.
System Security Goals
Just as we need goals in life to excel and succeed, similarly, we need to set some security goals to ensure the security of hash functions in cryptography.
Some significant goals are as follows:
- Integrity
This is achieved when no person other than the sender and receiver can access the data or information transferred.
- Secrecy
This is achieved when system files are accessible to a set of people and not common to view for all.
- Availability
This is achieved when the accessibility of data or information is for a set of people and not just one person or two.
Now that you have understood the meaning, importance, and goals of system security, let's discuss the ways to achieve the security of hash functions in cryptography.
Security of Hash Functions
There are, in total, three ways by which the security of hash functions in cryptography is achieved. We will learn and understand all of them one by one.
Preimage resistance
Hash functions provide preimage resistance. This concept says that the original function H(M)=h cannot resolve H(N)=h.
H(M)=h
h=! H(M)
Where M is the message input,
h is hash code,
H is a hash function.
This means it is practically impossible to obtain a message from a hash code as it is one-way.

This ensures the security of hash functions in cryptography by ensuring that no attacker can decode the message from the hash code(easily obtained by passing the message through a hash function).
Second Preimage Resistance
Hash functions provide second preimage resistance. This concept says that the original function H(M) can never be equal to H(N), where n and m are different messages.
H(M)!=H(N)
Where M and N are different message inputs,
H is a hash function.
This means it is practically impossible to obtain a different input message when we decode a hash value. The second preimage resistance works on the one-way principle of hash functions.
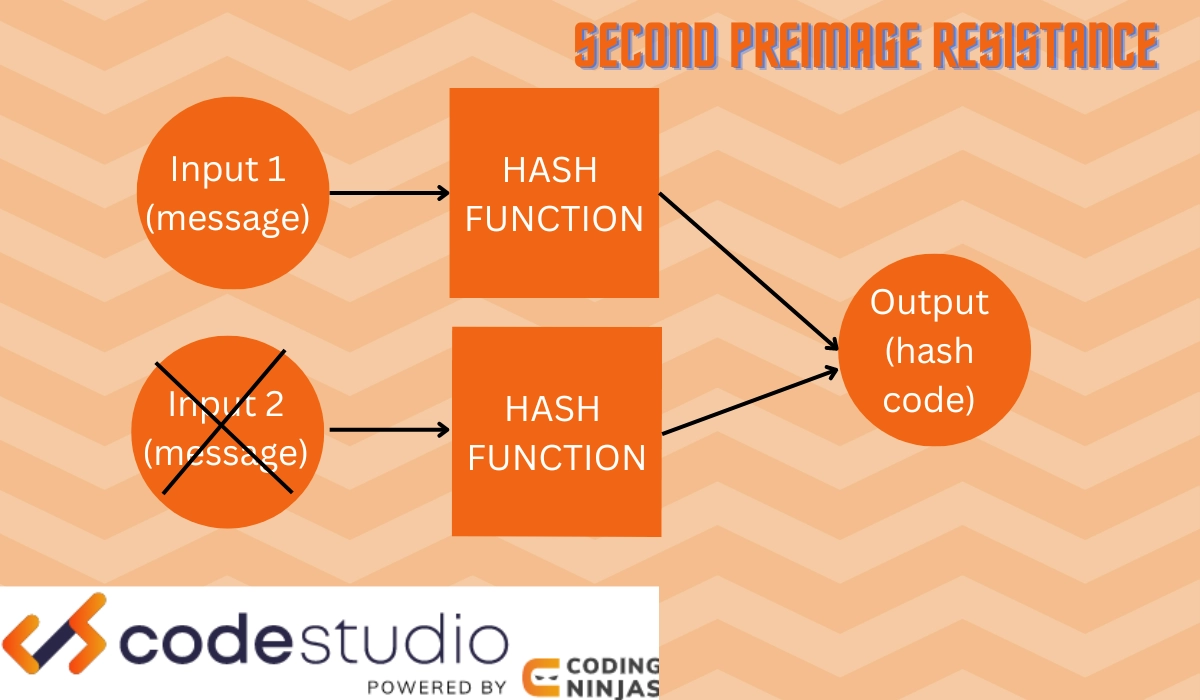
This ensures the security of hash functions in cryptography in the following ways:
- An attacker cannot read or observe data messages.
- An attacker cannot create a fake hash code for messages received in the absence of security.
- An attacker cannot generate an alternative message for the same hash codes.
Collision Resistance
Hash functions provide collision resistance. This concept says that the original function H(M) is not equal to H(N)
It is similar to the second pre-image resistance. The difference is that in collision resistance, you cannot have two messages that indicate the same output of hash values. Whereas in the second preimage resistance, a hash value cannot indicate a different input message.
H(M)!=H(N)
Where M and N are different message inputs,
H is a hash function.
This means that it is practically impossible to create a hash value that indicates two distinct message inputs.
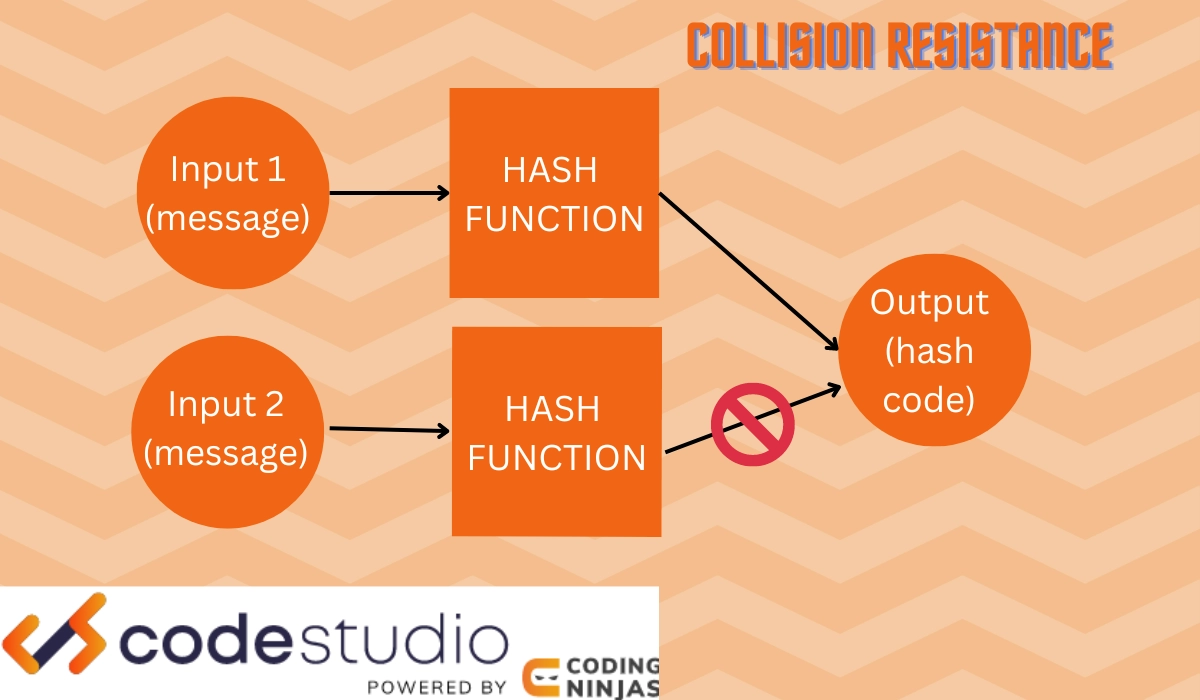
This ensures the security of hash functions in cryptography, not creating confusion and providing one message input that is authenticated.
Now it's time to discuss some FAQs.
Frequently Asked Questions
What is a session key?
A session key is a single-use key that can be sent with every message and encrypted with the recipient's public key. A session key protects communications between two computers, a user, a client, and a server.
Why should we update the keys on a regular basis?
There is a need to do so because of security reasons. Previously used keys can be less secure. Therefore they can be determined by unauthorized users easily.
What is a blind signature scheme?
This digital signature hides the message's content before it is signed. This is used when the message author and the signer are different parties. Blind signature schemes can be implemented using RSA and DSA.
What is the encrypted data called in cryptography?
The encrypted data is called the CipherText. Only the person who has access to the decryption key can decode and understand the plain text.
What distinguishes RSA from DSA?
While DSA is slower at verifying, it is faster at signing. DSA employs 1024 bits. RSA can handle 2048 bits or more. DSA can only be used for Encryption, whereas RSA can be used for Encryption and authentication.
Conclusion
In this article, we discussed what cryptography is and how hash functions work to provide authenticity. We also learned about the properties of hash functions that enable the security of hash functions in cryptography.
We hope this blog has helped you enhance your knowledge of Signing and Encrypting in Cryptography. Do not stop learning! We recommend you read some of our Cryptography articles: