Principles of Security Testing
- Confidentiality: A security process protects the data from any leakage.
- Authentication: It's a security process that is concerned with checking the user’s individuality and making sure that only the data that is permissible to them is accessed.
- Availability: It's a security process that ensures that data is available to the user whenever they need it.
- Integrity: It's a security process that protects the data from being modified by any unknown sources.
- Authorization: A security process determines that clients can create, update, or modify their data.
- Non-repudiation: It's a security process used to ensure that the exchange of information is done correctly.
Types of Security Testing
Security Scanning
Security scanning can be used for both manual and automation testing. This scanning helps in finding the weak points or unwanted modifications in the web application. The results obtained makes it easier for developers to solve those ambiguities.
Risk Assessment
Risk Assessment is concerned with testing the security risks within an application. The risk can be divided into three parts: low, medium, and high. The purpose of risk management is to control significant threats.
Vulnerability Scanning
It is done through automated software to scan applications' vulnerabilities and identify systems with security vulnerabilities.
Penetration Testing
In penetration testing, developers try to identify the weakness and loopholes in the application to secure the users' data.
Security Auditing
Security auditing is concerned with an internal application inspection, which can be done via a line-by-line review of code. It is a structured method used to evaluate the security measure of an organization.
Ethical Hacking
Ethical hacking helps an organization increase its security by detecting loopholes in the application by imitating the same procedure, tricks, and techniques as malicious hackers.
Posture Assessment
Posture Assessment combines risk assessment, ethical hacking, and security scanning, which helps display the complete security posture for an organization.
Possible Attacks in a web application
The application needs to be protected from the following attacks:
-
Password Cracking: One of the most common methods hackers use to steal data from an application is by guessing, stealing, or using the stored login credentials of a user in unencrypted cookies.
-
URL manipulation through HTTP GET methods: HTTP GET requests user information passed to the server for authentication or fetching data. The attacker can manipulate the input passed from the GET request to a server to corrupt the data
-
SQL Injection: Insertion of malicious code in the application by attackers to manipulate an application. If the system fails to respond to such malicious code, it can be submitted to the database, leading to changing, deleting, or revealing data to the attacker.
-
Cross-site Scripting: Any scripting language like HTML or script should not be allowed in the application as they make the application prone to attacks. In this type of attack, the attacker uploads a piece of malicious script code on the user’s website, which can be used to steal information. This type of attack is quite common and can do significant damage.
-
Client-side attacks - It involves data spoofing(manipulating user’s data and creating duplicate copies) and implementation of external code in the web application by malicious users.
-
Authentication -It involves authenticating users’ information and ensuring that any malicious user cannot steal sensitive data.
-
Authorization - It is used to determine that users can create, update, modify and delete the data authorized to them.
-
Command execution- It is used when malicious attackers control the web application.
-
Logical attacks - This restricts application usage when attacks like DOS outbreaks. DOS attacks happen when an attacker bombards the server with requests which paralyze the server and prevent the users from gaining access to the services.
- Information disclosure - It is used to show sensitive data to attackers. Here the leakage happens when the application displays sensitive data like an error message that might help the attacker steal user information.
Steps to perform Security Testing

- Understand the goals for an organization by considering all the possible factors required to prepare a well-planned test.
- Gather all the information related to setup information used in developing the application.
- Identify the possible vulnerabilities and threats to the application.
- Prepare a plan according to the identified vulnerabilities.
- Prepare a list of all the tools that will be required while performing the tests.
- Execute the security test while correcting the defects during the testing process.
- Store a detailed report for the security testing conducted.
Security Testing Tools
- W3af: It is one of the most popular security testing frameworks developed using python. It allows the tester to find more than 200 types of vulnerabilities and is an easy tool to get started with.
- SonarQube: It is an open-source security testing tool that can also measure the quality of source code. Despite being written in java, it can analyze over 20 languages.
-
ZAP: It stands for Zed Attack Proxy. It is a multi-platform, open-source security testing tool. It is used for finding several vulnerabilities in an application during the development and testing phase. It is written in Java. Other than that, it can also be used as a scanner or to intercept a proxy for manually testing a webpage.
- Arachni: This is an open-source security testing tool used to identify security issues in a web application, including SQL/XSS Injection, Invalidate redirection, or local file inclusion. It is easily deployable and is supported on various platforms.
- IronWASP: It is also an open-source security testing tool that can uncover over 25 types of vulnerabilities. It is extensible via plugins written in Python, Ruby, C#, VB.Net.
Techniques for Security Testing
- Session Management: A web session is a sequence of HTTP requests and transactions linked to the same user. A tester can handle the sessions in a web application, for e.g.setting an idle time for session expiration, multiple simultaneous sessions, etc.
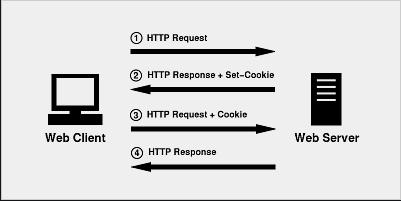
Source: Link
-
Access Management: It is used to control the access of applications to different users based on their roles. E.g., In a school, the principal is access to all the available data related to teachers or students. The teacher is given access to all the information related to the students, and all the students can access the data related to their marks, subjects, etc. Students aren't given access to teachers' related data because it's of no use to them in the given scenario. This is how we manage access in an application where every role has access to their modules, screens, and menus only.
- Data Protection: Three ways to protect data from invaders are:
- Access management
- Data stored in the database must be appropriately encrypted.
- Proper security measures must be taken when data flows in between different modules.
- Automated vulnerability scanning: These programs help in finding and analyzing vulnerabilities, often before actual attacks occur. Investing in these vulnerabilities is a cost-effective way to reduce the likelihood that these vulnerabilities will turn into cyber disasters.
- Brute-force attack: The invaders try to log in by guessing the password in this type of attack. A solution for such attacks can be limiting the number of guessing attempts in the application window and temporary timeout of the session window if any user fails to log in after multiple attempts. Testing for brute force attack can be divided into two parts:
-
Black Box Testing: This is concerned with testing the application when the software's functionality is unknown to the tester. The testing is done without knowing the internal structure of the web application.
-
Grey Box Testing: It combines black-box testing and white box testing. The internal structure is partially known to the tester.
-
White Box Testing: This testing analyzes the complete internal structure, code, and application working rather than just the functionality.
-
Web Application Firewalls: Firewalls operate on the application layer and use rules to restrict access to applications. Since they can access all the layers and protocols, WAFs are highly effective gatekeepers in shielding resources from outside attacks.
- SQL Injection: In this type of attack, the attacker can get information directly from the server's database. If a tester encounters a database error, the user's data is inserted in some query and then executed on some application. To prevent the insertion of the script in the query, the input length must be defined as small as possible.
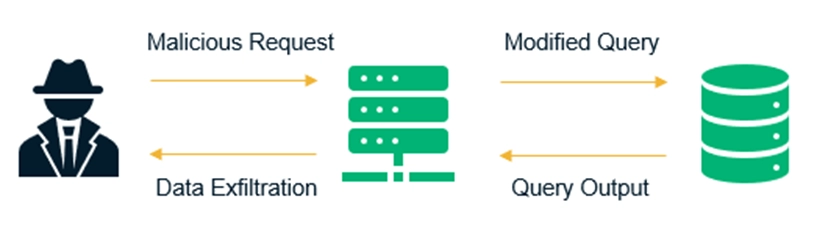
Source: Link
- Risky functionalities: Functionality such as payments and file uploads should be tested. Any unwanted file upload or test for injection vulnerability, cryptographic storage, password guessing, etc., must be restricted to ensure proper security of the sensitive information available.
-
Secure Development Testing: It provides information about the newest attack vectors. It helps establish a baseline and develop a practical approach to preventing websites from malicious attacks and minimizing the consequences.
Must Read, Locators in Selenium
Frequently Asked Questions
What are the main open-source security tools for a web application?
There are different security web tools available in the market to test the security of a web application, namely:
- Zed Attack Proxy(ZAP)
- Wfuzz
- Wapiti
- SQLmap
- Nogotofail
What is Kerberos key?
Kerberos is a computer network security protocol that authenticates service requests between trusted hosts across an untrusted network. It uses secret keys and a trusted third party to establish client-server applications and verify users' identities.
Kerberos is used in Posix authentication, Active Directory, NFS, and Samba. It's also an alternative authentication system to SSH, POP, and SMTP.
What do you mean by alpha and beta testing?
Alpha testing identifies bugs in an application before releasing it to the end-users. The internal employees of an organization usually perform it. It involves both black and white box testing. All the issues and fixes can be addressed immediately by the developer.
Beta testing is performed by real application users in a real environment. It commonly uses black-box testing. Data collected from the test will be implemented in the future version of the application.
Conclusion
Security Testing is the most important testing for an application to ensure that users’ data remain confidential. In this testing, the tester plays around with the system to find all the security-related bugs that might lead to the exploitation of the stored information.
This blog discussed security testing, its types, and its importance to develop a secure well-functioned application.
If you are a beginner interested in learning and exploring other fields, you can follow our guided path to understand the core subjects of computers and get a good grip on DSA concepts. In case of any suggestions, feel free to post them in the comments section.