Introduction
We are back with another Cryptography based article, i.e., Session attacks and Hijacking in Cryptography. When you hear the word Hijacking, what comes to your mind?
It means getting access to something illegally, and This is what is similar to session hijacking in Cryptography.
A lot of things happen internally that a user is unaware of in general, Like for you to log in and log out on a website just a few clicks away, but Two different machines communicate on a network and share a few common communication parameters.

Before moving towards this in detail, let's gather some insights into what cryptography is.
What is Cryptography?
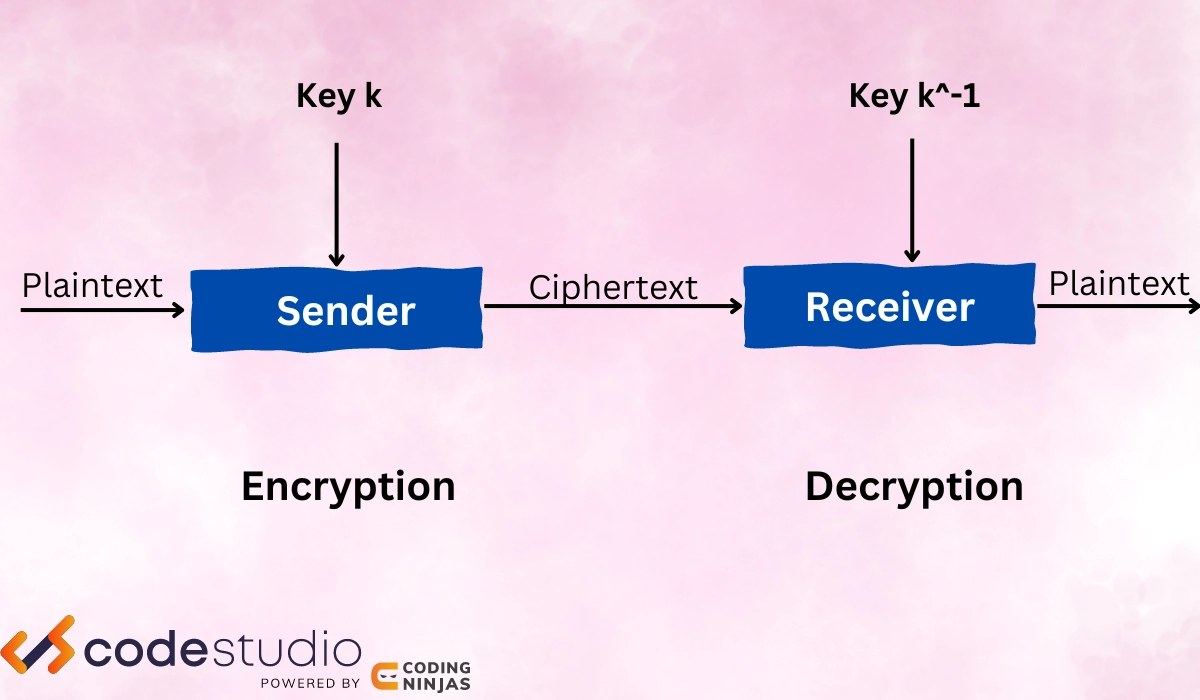
When people hear the word cryptography, the mind straightforwardly goes toward the encryption of data.
Cryptography is the art of protecting the Data and Information into an unreadable format and then retransmitting that message back to its original form. Cryptography allows you to store some sensitive information like passwords and addresses or send it through insecure networks like the Internet.
Moving forward, let's discuss Session Hijacking in Cryptography in detail.
Also read - active and passive attacks
Session Hijacking
As we discussed above, there are a lot of problems or parameters that go on while two users are communicating via the Internet, and what are those problems, what are their types, we will be discussing further in this particular article.

Session Hijacking means taking control or Hijacking someone's ongoing session in between; this means when two systems are communicating when their connection is established, then both will have some unique session id(It is a unique number or an ID that is assigned to the user by the web server for the duration of that user's session). And if the attacker guesses that session id while communicating, then it is known as Session Hijacking.
Through this process, the attacker will be able to access the personal information that might have been protected using a passkey by the user.
There are some network protocols that are attacker's favourite because of the session-oriented nature of their connections like FTP, and Telnet.
Some of the vulnerabilities of session hijacking are:
-
When there is a TCP communication between two systems, then at the time of connection establishment, the session id is authenticated. So only at the start of the communication setup session ID is verified. If someone captures that session id, then there is no need for them to do the authentication again.
- All the traffic can be sniffed, and then the session id can be captured.
Why is Session Hijacking successful?
Here we will discuss why Session Hijacking is successful.
Invalid Session Id
This means that if someone enters the wrong password, then the account will not get locked.
Weak Session- Id Generation Algorithm
The algorithm used to generate the session id is quite weak, due to which attackers easily find out the session id used by the current user as well as the user who will come next.
Insecure session-Id
The handling of the session id is insecure as the session id is moving back and forth without encryption.
Indefinite Session Timeout
If two systems are communicating with each other, then they should have a session timeout after every five minutes, a new session id is to be generated, but this is not happening.
Most PC using TCP/IP
As we know, most PCs use TCP for communication between the two systems; we know that authentication of session Id is done at the very beginning of the connection establishment. So that is why it is vulnerable.
Working of Session Hijacking
The working process of Session Hijacking is as follows:
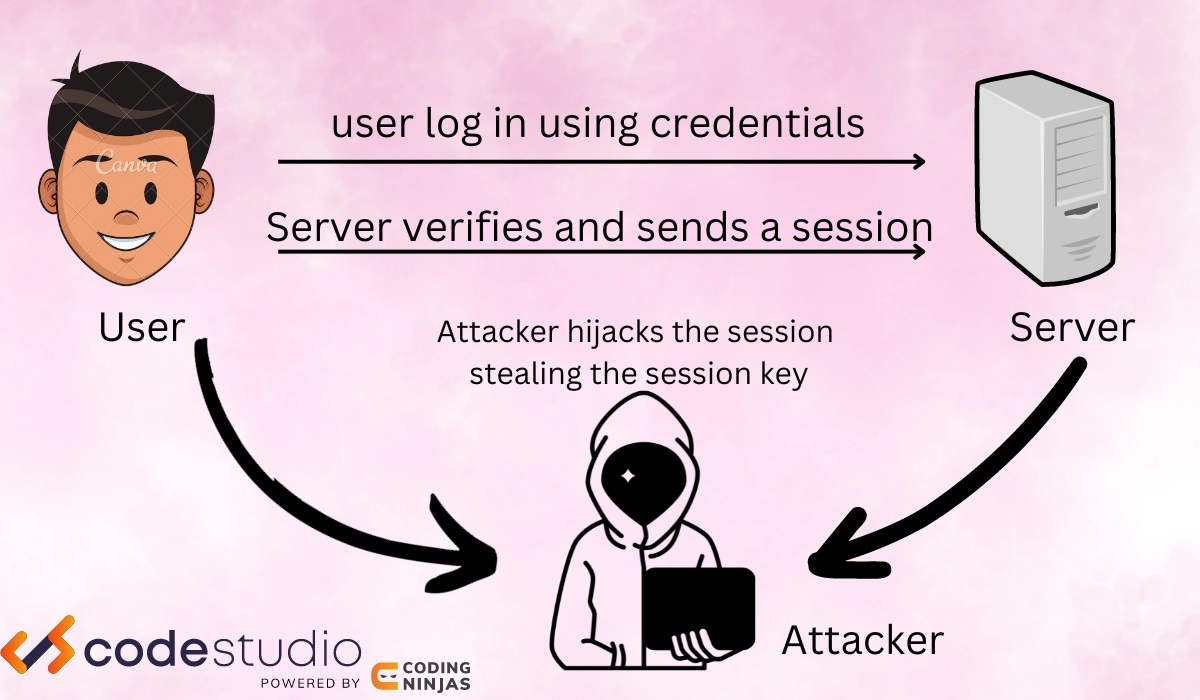
There are several methods to hijack a session, like XSS, Session sniffing, etc. Session Hijacking happens in two major important steps; when the user may open a website, which instantly installs a temporary cookie, known as a Session cookie.
These session cookies help to keep the user authenticated and track their activity, till the user remains active on the browser.
There are several methods that can be used by the hijackers to steal the session IDs. The process will be to use the session cookie to locate the session ID and the hijackers use the information needed to hijack the user’s session.
After gaining the access to the session they use the information according to their motive, they can use personal data to perform illegal activities.
Types of Session Hijacking Attacks
There are two types of Session Hijacking in cryptography: Active Session Hijacking and Passive Session Hijacking. To perform these types of Hijacking, the attackers use various attacks, which we will see now.
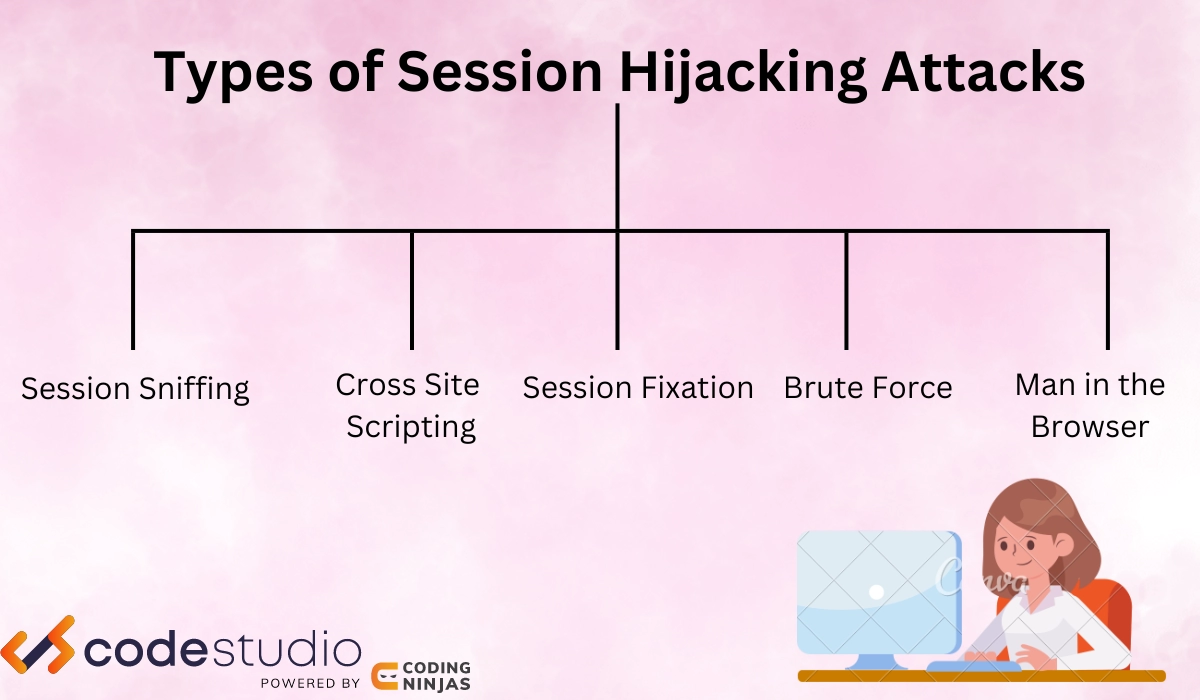
Session Sniffing
Session Sniffing or Session Side - Jacking, the hijacker tries to access the user's network traffic. To achieve this, the attacker uses a packet sniffing technique through which the network traffic can be read, and the cookies are stolen.
Cross - Site Scripting(XSS)
In this attack, the hijacker tries to find the weakest spot in the target server and injects its scripts into the web page. This page then loads this code, and once this code is loaded, the web browser reveals the user's session ID (session key) to the hijacker.
Session Fixation
In this type of attack, the hijackers create a duplicate session where the user can be tricked by using the session id set by the attackers. The session ID can be set via emails, which leads to the attacker's website and hijacker gaining access to the user's data.
Brute Force
In this, the attacker guesses the session id used by the user depending on the length. The attacker finds out the list of session ids from the browser with weak security measures.
Man in the Browser
Here the attacker infects the user's computer using the Trojan Horse virus, allowing them to hijack a session.
How to protect data against Session Hijacking
There are several ways using which a user can protect themselves from stealing their personal data.
-
One of the protection methods is to change the session id immediately after the authentication is completed. This is the way you can protect your data from the hijacker.
-
Users should avoid using public wifi while doing some work that involves personal information, like transactions processed using net banking. The attacker can sniff the packet to pick the user's session cookies.
-
Cybersecurity tool is DDoS Protection software for carefully logging in and out of every session to protect personal data.
- One of the protection techniques is to site the traffic to the database of the known attack signatures so that if a match is found, they will block that particular traffic and alert the owner. These are expensive but effective approaches.