A substitution cipher is a method of encryption where each letter in the plaintext is replaced with another letter. This technique has been used for centuries to secure messages, making it one of the oldest and simplest forms of cryptography. In a substitution cipher, the relationship between the plaintext and ciphertext is one-to-one, meaning each character in the plaintext corresponds to a unique character in the ciphertext.

Encryption is the process of concealing data. When ordinary text is encrypted, it becomes ciphertext, which is unreadable. A substitution cipher replaces any plain text character from a given fixed set of characters with another character from the same set based on a key. With a shift of one, for example, A would be replaced by B, B by C, and so on.
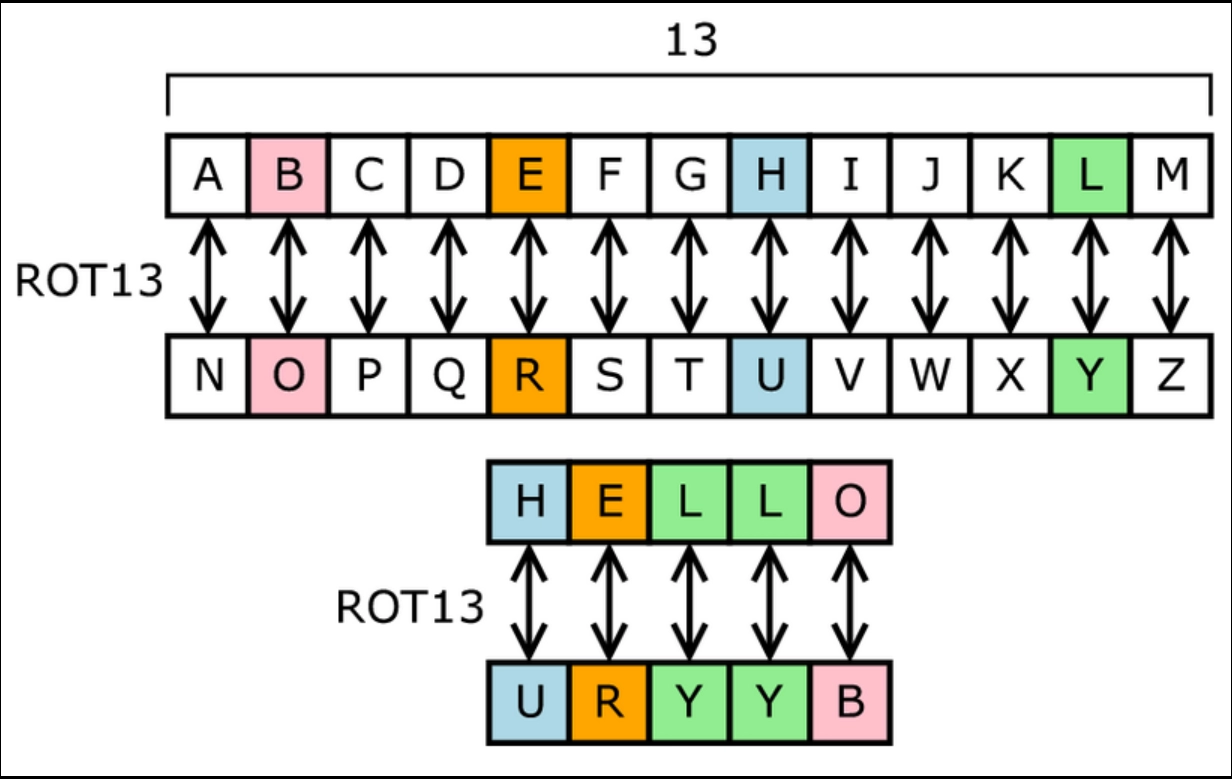
Figure: Substitution Cipher with key=13 (source)
Encryption in Substitution Cipher
Encryption replaces letters with corresponding letters after shifting all letters to the “key” number of positions to the right.
Example:
Plain text: My name is Anant Dhakad
Key: 4
Encrypted text: Qc reqi mw Ererx Hleoeh
Procedure
1. Iterate over all the letters in the input text and replace each letter with a letter “key” positions right to it.
2. Finally, print the encrypted text.
Implementation
Input
My name is Anant Dhakad
4Output
Input Text: My name is Anant Dhakad
Input Key: 4
Encrypted Text: Qc reqi mw Ererx HleoehDecryption Substitution Cipher
Decryption is done by replacing corresponding letters after shifting all letters to the “key” number of positions to the left.
Example:
Input Encrypted text: Qc reqi mw Ererx Hleoeh
Key: 4
Output Decrypted text: My name is Anant Dhakad
Procedure
1. Iterate over all the letters in the input ciphered text and replace each letter with a letter “key” positions left to it.
2. Finally, print the decrypted text.
Implementation
Input
Qc reqi mw Ererx Hleoeh
4Output
Input Encrypted Text: Qc reqi mw Ererx Hleoeh
Input Key: 4
Decrypted Text: My name is Anant Dhakad



