
Introduction
What is Telnet?
Telnet is a command-line tool to access remote systems. It is text-oriented, and there isn't any graphical user interface. Telnet is the acronym for teletype network protocol. It was developed way back in 1969, which means it is even older than the internet.
Telnet follows a client-server protocol, and the traffic is entirely bi-directional. Telnet uses port 23, which means it is needed to ensure that port 23 is open in the remote system in order to access it. If port 23 is not opening the remote system, we won't be able to access it using Telnet. Let's discuss why Telnet was made.
Why Telnet?
Telnet is a command-line tool used to access remote computer systems. If a telnet service is running on a remote system, we can pretty much access that system with a straightforward command, i.e.,
TELNET SPACE (The IP address of the remote system)This will open up a Telnet session right in front of us and not only that once the connection is established. The files can be edited, and programs can be run on the remote system from the system right in front of us. But all these activities can only be performed when the required permissions are given to the accessing system.
Telnet can also check the open network ports on a remote system. A port is a communication endpoint that is used to connect an external device to the computer. It is a 16-bit unsigned integer number from 1 to 65535.
So if the user wants to check whether a specific port is open on the remote system, the user can use Telnet. The user has to execute a very simple command, i.e.,
TELNET SPACE (The IP address of the remote system) SPACE (The port that the user wants to check).The user will get a blank screen if the port is open on the remote system.
Telnet can also configure the network devices like routers, switches and more. Suppose the user wants to configure an IP address to a particular port on a router, then the user can pretty much do it with the help of Telnet. In the next section, we’ll discuss how Telnet works.
How does Telnet work?
The following diagram shows the essential operation of Telnet.
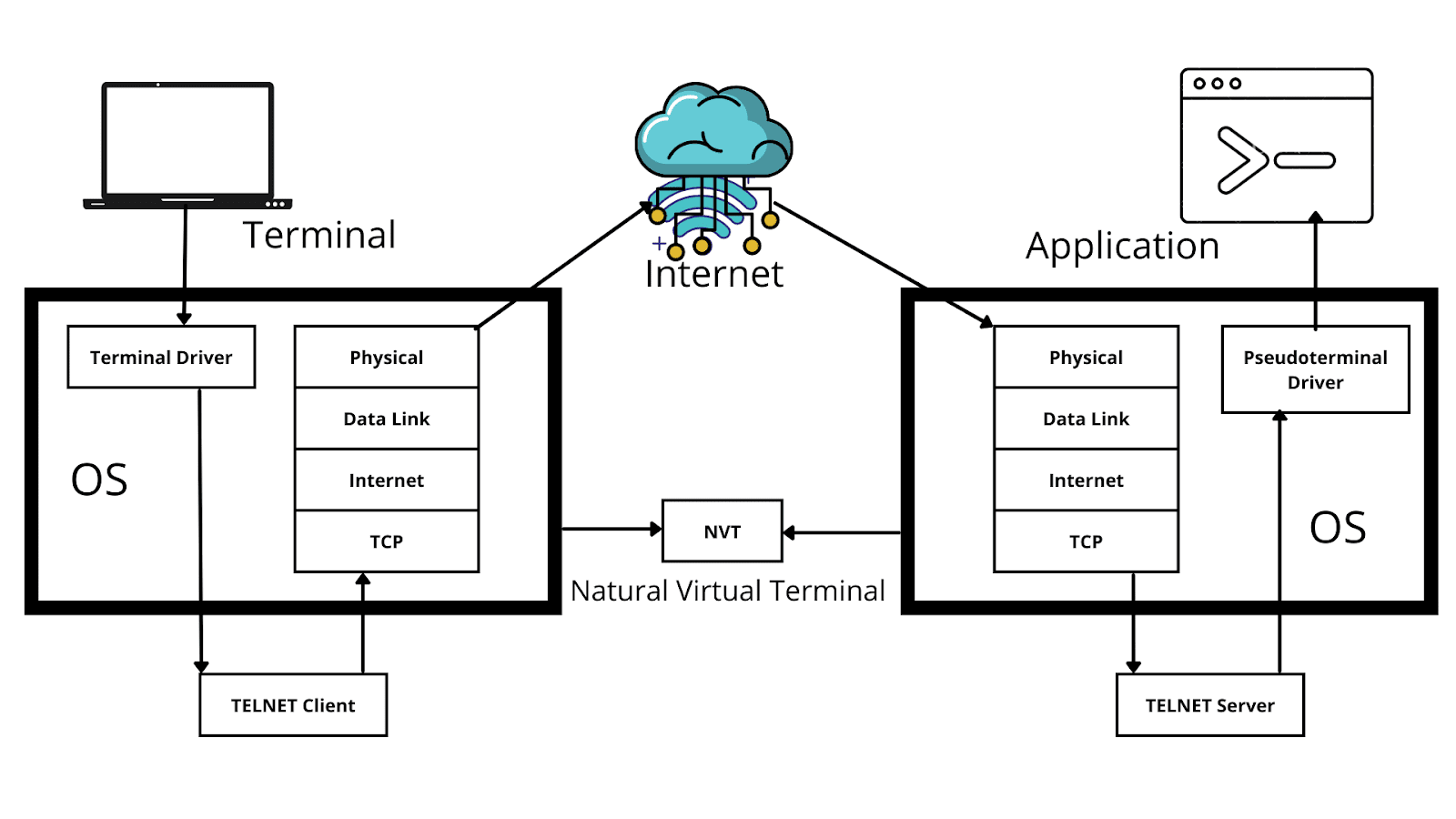
It may look a bit complex, but it will be effortless to understand with the upcoming explanation. Everything here starts with the terminal. Whatever the input is given by the user or whatever the user provides the command, it will be through the terminal. The terminal driver captures all the keystrokes from the user and will forward them to the telnet client. Now the telnet client converts those characters into a universal language. The input is converted into the universal language for the ease of data transmission.
Suppose the operating system used by the client may be Windows, and the operating system used by the server may be Linux. Still, irrespective of the operating system used, it should communicate. It should establish a proper connection so it is converted into a universal language. After the conversion, it will be forwarded to a TCP/IP stack. Telnet follows the TCP/IP protocol for communication. After that, it will be sent to the end system or the server. It is now coming to the Network Virtual Terminal or NVT.
NVT sets a standard for both systems to communicate. It ensures how the data is transferred, the format of data transmission, or the rate of transmission.
NVT controls everything, and at the end, it will be forwarded into the TCP/IP stack of the end system. After that, it will be passed to a telnet server. Telnet server performs a reverse operation of Telnet client. It converts the universal language information into a system understandable language.
Finally, information will be forwarded to a pseudo-terminal driver. Pseudo-terminal is a pseudo-device pair that provides a text terminal interface without an associated virtual console, computer terminal or serial port hardware.
Pseudo-terminal driver invokes the application based on the user input. Suppose that if the user has requested to delete a file, it will be done through the pseudo-terminal driver.
So this is the basic operation of Telnet, and this is the work of Telnet. Since a coin has two sides, similar is the case for Telnet.
Must Read Subnetting in Computer Networks





