Introduction
Before starting the discussion, let us first grasp some important concepts to understand things better. In cryptography or Information Security, to secure your information from a third party, many applications use cryptography algorithms to encrypt information or messages.
For instance, let us say you and your friend Alie are talking to each other via some social application. The information you people are sharing might contain personal information that is not intended to be read by any other person.
Since Alie is scared of being caught, you people talk in some codes that only you guys know.
So, by this, if someone tries to read your conversation, he will get confused and, as a result, won’t understand anything.
Using the same approach, crypto algorithms are made. In simple words, Cryptography is the study of encrypting and decrypting data using mathematics. Cryptography allows you to store sensitive information or send it through insecure networks (such as the Internet). It uses codes to secure information and communications so that only those who are supposed to read and process it may do so.
So, that’s a brief introduction to Cryptography. Today, we will discuss the concepts a little more advanced and in-depth. Before we start, let us understand the meaning of today’s topic.
“ The Partial Information Concerning Plaintext Bits for obtaining semantic security. “
To understand the topic, we must know the keywords in it. We will start with semantic security.
So, what is security in general?
Security refers to both safety and the precautions taken to protect oneself. Here, what to secure? The information is shared over the public Internet, where hackers sit in the middle of the conversation to steal confidential data. Security is important everywhere. Due to the evolution of the Internet, everything is converging to Digital, which has its advantages and disadvantages. To protect the information from adversaries, we need to have high security over the data.
How do we protect our data from third parties by using cryptography?
Let us understand it:
Cryptography is closely related to encryption, converting plain text into ciphertext before sending it and then back again after receiving it.
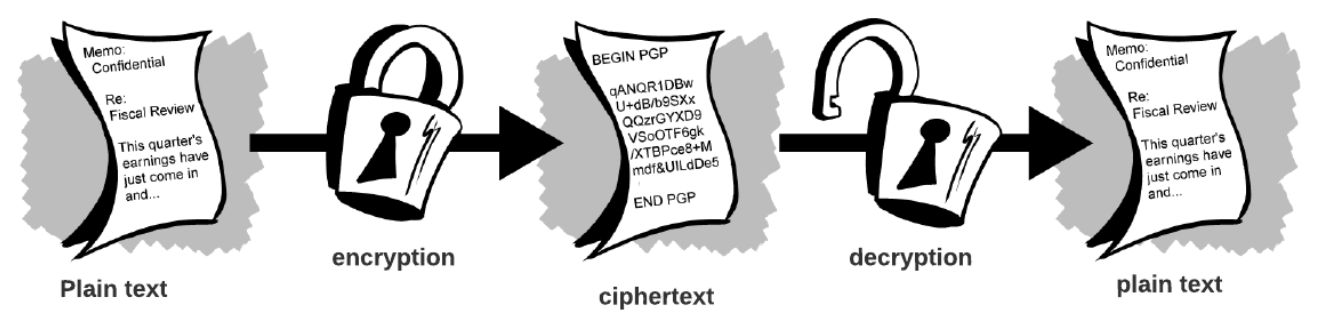
Now, let us discuss what Semantic Security is.
Semantic Security
Cryptography can be powerful or weak. The time and resources required to retrieve the plaintext are used to determine cryptographic strength. Strong cryptography produces ciphertext that is extremely difficult to decode without the proper decoding software. It is impossible to decrypt the output of strong cryptography until the end of the universe, even with all of today's computing power and available time—even a billion computers performing a billion checks every second.
So, a semantically secure cryptosystem in cryptography is one in which only negligible information about the plaintext can realistically be extracted from the ciphertext.
Now, a question may arise: How can some data be extracted from the ciphertext that can be used to decrypt the ciphertext into plaintext?
For example, we change every byte to encrypt an image. We either change the last bit or the last two bits. Every byte is 8 bits; we change the last two bits in the hope that no one will notice. So, for every byte( 8 bits), six are the regular image, and two are our secret message.
So, if we have a normal pixel, it will be 4 bytes long.
So, for each byte, we are talking about the last two digits mentioned below:
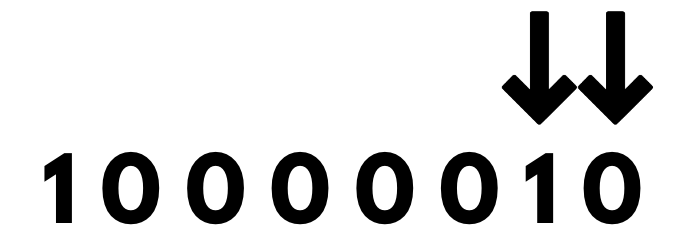
What are the possibilities of changing the last two bits? Since we only have 1 and 0 in a byte, we can toggle the bits or leave them both the same based on the message we have.
For example, the secret message is 100100.
So, we don't have to do anything to hide the initial two bits in the pixel.
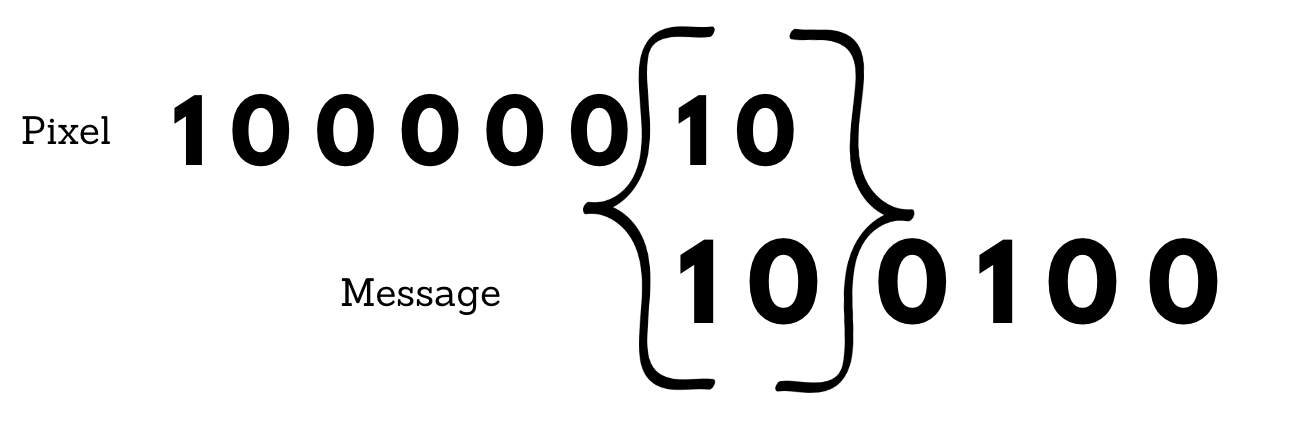
To hide the next two bits of the secret message, we use another byte of a pixel. To hide the next two bits of the secret message, we use another byte of a pixel. So, let us say the next byte is 0 1 1 0 1 1 1 1.
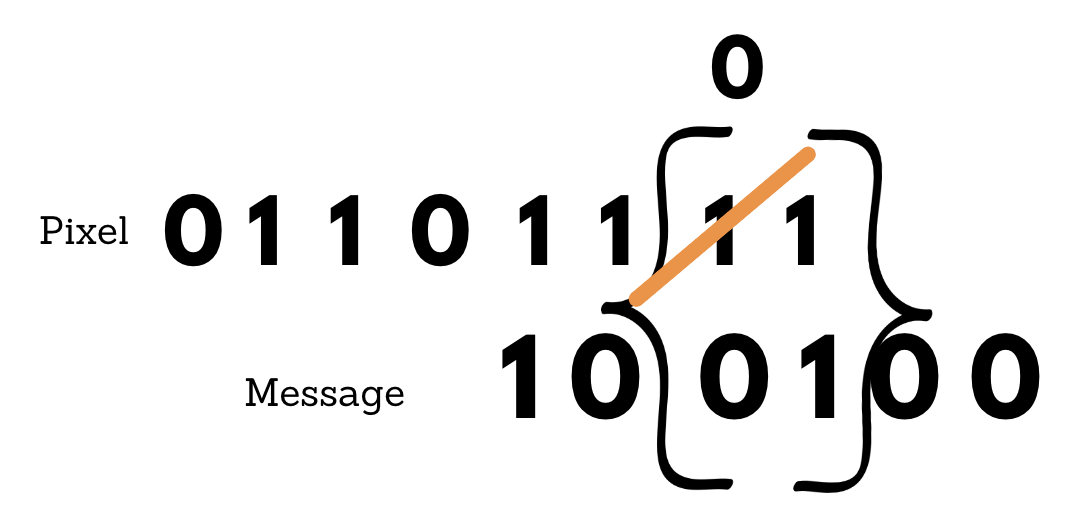
So, by changing that second least significant bit from 1 to 0, we can hide the secret message. In a huge image - changing by two levels is probably not noticeable.

The above image is about 3 megapixels in size. You will see little detail when you only change the last two significant bits of an 8 bits channel image.
But, if you do the subtraction on the images, you can see a difference.

Although, in general, it’s going to be pretty imperceptible. We understood from the example above that an adversary could extract the hidden message from the image. Hence, it is not semantically secure.
In cryptography, we have three classical cipher techniques. The Caesar cipher, the vigenere cipher, and the enigma machine. Each of these cipher techniques leaks information. For example, the Caesar cipher leaks information about the frequency of plaintext letters because that information is preserved in the ciphertext. On the other hand, the vigenere cipher also leaks information because the message is typically much longer than the key, and the key is applied to the message by repeating itself repeatedly. The enigma machine leaks information about what isn’t the plaintext.
Is it even possible to build a cipher that leaks no information?

That’s what we are going to learn today. So, the answer to this question is Yes.
We can achieve this by using a One-time Pad.






