Introduction
Hello Reader!!
The need for secure communication has become critical as the amount of sensitive information being shared over the internet continues to grow. One way to achieve this is through the use of cryptography. The station-to-station key agreement scheme is one standard method of establishing a secure communication channel. Today, we will learn about STS key agreement scheme, its uses, and its working with examples. We will also see how it helps in increasing our security.

So, let’s get started!
Station-to-station Key Agreement Scheme
The station-to-station key agreement scheme establishes a shared secret key between two parties (usually called "stations") over an insecure communication channel. This is often used in cryptography to secure communication between two parties.
What is STS key agreement Scheme?
In this scheme, the two parties first agree on a public key, which is typically a large number that is known to both parties. They then use this public key to generate a shared secret key, which is known only to the two parties and is used to encrypt and decrypt messages sent between them.
The security of this scheme relies on the difficulty of factoring large numbers. A mathematical problem considered difficult to crack for most attackers. As long as the public key is large enough, it should be difficult for an attacker to determine the shared secret key, even if they can see all communication between the two parties.
Uses
Some specific use cases of the STS agreement scheme include:
- Establishing a secure connection between a web browser and a web server using the HTTPS protocol.
- Securing communications between two computers in a network using a protocol such as IPSec.
- Protecting sensitive information, such as financial transactions or personal data, during transmission over the internet.
- Ensuring the confidentiality and integrity of messages sent between two parties, such as in email or instant messaging applications.
Working
The basic idea behind STS is to use the Diffie-Hellman key exchange protocol to agree on a shared secret, but with the added security of using digital signatures to ensure the authenticity of the messages exchanged between the stations.
Here's how it works:
- The two stations, Alice and Bob, first agree on a large prime number, p, and a primitive root modulo p, g. These values can be publicly known and are used as the basis for the Diffie-Hellman key exchange.
- Alice and Bob each generate their own private keys, a, and b, respectively. These keys are secret and should not be shared with the other station.
- Alice and Bob then compute their public keys, A and B, respectively, using the following formulas:
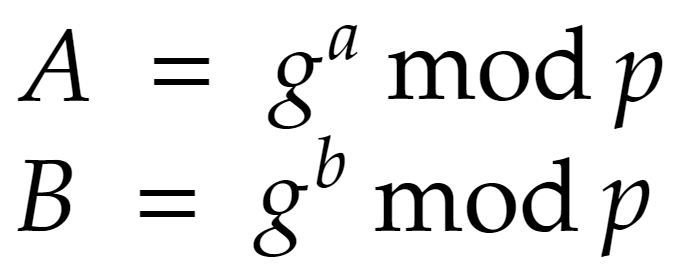
4. Alice and Bob exchange their public keys over the communication channel.
5. Once Alice and Bob have each received the other's public key, they can use them to compute the shared secret key, K, using the following formula:
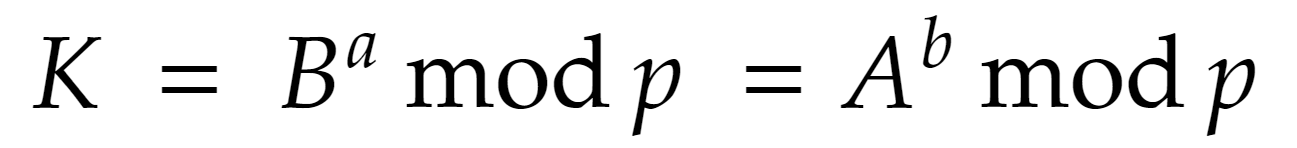
6. Alice and Bob can also use digital signatures to ensure the authenticity of the messages exchanged between the stations. This involves using a cryptographic hash function to compute a unique "fingerprint" for each message and then using a private key to "sign" the message. The other station can then use the corresponding public key to verify the signature and ensure that the message has not been tampered with.
Overall, the STS key agreement scheme provides a secure and efficient way for two stations to establish a shared secret key over an insecure communication channel. It combines the security of the Diffie-Hellman key exchange with the authenticity of digital signatures to provide strong protection against a wide range of attacks.





