How does VPN tunneling work?
VPN tunneling means using a VPN service. So the answer to the above question is the same as the answer of ‘How does a VPN work?’
Data will be transmitted from the client machine to a point in the VPN network. The VPN point will encrypt the data and send it through the internet. Another point in the VPN network will decrypt the data and send it to the appropriate internet resource. Then the internet resource will send the data back to the point where it will get encrypted. This encrypted data will go to another point in the VPN network that will decrypt the data and send it back to the client machine.
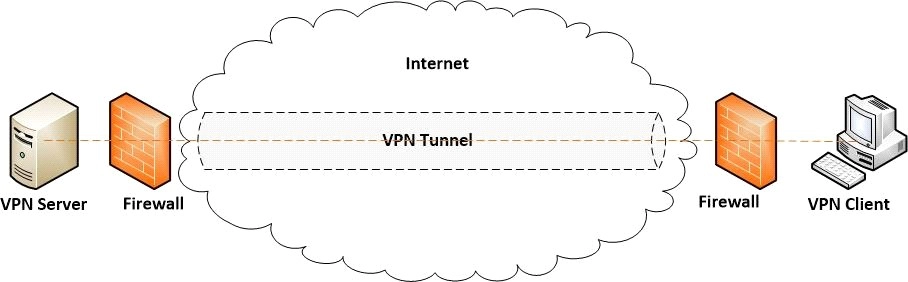
Source
Here are some works that the VPN tunnel will carry out:-
- It protects the data from third parties.
- It hides our IP address by funneling our traffic through to a VPN server.
- It secures wifi hotspots.
Types of VPN tunneling protocols
-
Internet Protocol Security(IPSec)
IPSec is generally used to secure Internet communication across an IP network. It verifies the session and encrypts each data packet during the connection. IPSec runs on two modes:- Transport and Tunneling Mode. Transport mode encrypts the message in the data packet, while Tunneling mode encrypts the whole data packet.
-
Layer 2 Tunneling Protocol(L2TP)
L2TP often combines with IPSec to establish a highly secure VPN connection. L2TP establishes a tunnel between two L2TP connection points, and then IPSec’s work is to encrypt the data and maintain a secure connection between the tunnel.
-
Point-to-Point Tunneling Protocol(PPTP)
PPTP is the most widely used VPN Protocol. It generates a tunnel and confines the data packet. It is used to encrypt the data between the connection. It is used on Windows, Mac, and Linux.
-
SSL and TLS
SSL stands for Secure Sockets Layer, while TLS stands for Transport Layer Security. Here the web browser acts as the client, and user access is prohibited to specific applications instead of the entire network in the VPN connection generated by SSL and TLS. Almost every web browsers come integrated with SSL and TLS, and SSL connections have ‘HTTPS’ instead of ‘HTTP’ at the starting of the URL.
-
OpenVPN
OpenVPN is an open-source VPN protocol, and it uses a traditional security protocol based on SSL and TLS protocols.
-
Secure Shell(SSH)
SSH generates a VPN tunnel for the data transfer. This tunnel is encrypted. An SSH client generates the connection, and the data transfer takes place through the tunnel from a local port onto the remote server.
FAQs
-
What is VPN Split Tunneling?
It is a feature by which we can choose which website or application can use a VPN tunnel and which cannot.
-
Name an open-source VPN Protocol.
OpenVPN is an open-source VPN protocol.
-
What is Encapsulation in VPN Tunneling?
The data that travels inside a VPN Tunnel is split into pieces called packets. These are then placed inside other data packets. This process is called Encapsulation.
-
What is WireGuard?
WireGuard is the best tunnel protocol available right now. It offers very high speed and security. It is also an open-source protocol.
-
What is Lightway?
Lightway is also an open-source protocol that uses the wolfSSL cryptography library. It provides a faster, more secure, and more reliable VPN experience.
Key Takeaways
In this article, we have extensively discussed Tunneling Protocols, how it works, and their different types.
We hope that this blog has helped you enhance your knowledge regarding Tunneling with VPN. If you would like to learn more, check out our articles on What is VPN, Types of VPN, What is Information Security, Need of Information Security.
Do upvote our blog to help other ninjas grow. Happy Coding!






