Introduction
In lock-based protocol, a transaction cannot access or write data unless it obtains a suitable lock. The Two-Phase Locking Protocol ensures transaction consistency by employing a set of rules. Transactions must obtain appropriate locks before accessing or modifying data, preventing conflicts and maintaining data integrity throughout the transaction's lifecycle.

Types of Locks Used in Transaction Control
In transaction control, there are two common types of locks shared lock and exclusive lock. Here is a brief overview about it:
- Shared lock: The transactions can only read the data items in a shared lock.
- While a transaction attempting to update the data will be unable to do so until the shared lock is freed, a transaction attempting to read the same data will be allowed to do so.
- Read lock is another name for shared lock, which is exclusively used for reading data objects.
2. Exclusive lock: The transactions can read and write to the data items in an exclusive lock.
- When a statement updates data, its transaction has an exclusive lock on the modified data, preventing access by other transactions.
- Until the transaction holding the lock commits or rolls it back, the lock is in effect.
Also read- multiple granularity in dbms
What is Two-phase locking (2PL)?
The two-phase locking divides the transaction execution phase into three components.
- When the transaction's execution begins in the first part, it requests permission for the lock it requires.
- The transaction then obtains all of the locks in the second part. The third phase begins when the transaction's first lock is released.
- The transaction cannot demand any new locks in the third phase. It only unlocks the locks that have been acquired.
A transaction follows the two-phase locking protocol if locking and unlocking can be done in two phases.
The two phases of the two-phase protocol are:
- Growing phase: During the growth phase, new locks on data items may be acquired, but none can be released.
- Shrinking phase: Existing locks may be released, but no new locks can be acquired during the shrinking phase.
Note: If lock conversion is allowed, the following phase may take place:
- Upgrading of lock (from S(a) → X(a)) is allowed in the growing phase.
- Downgrading of lock (from X(a) → S(a)) must be done in the shrinking phase.
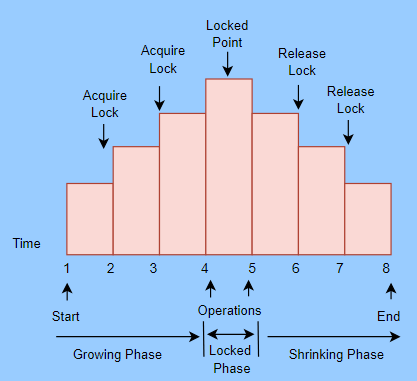
The depicted diagram illustrates the growing phase, where locks are acquired until all necessary transaction locks are obtained, defining the Lock-Point. Beyond this point, transactions transition into the Shrinking phase, ensuring a structured lock-based protocol.
Lock Point
It is a point at which the growing phase comes to a close, i.e., when a transaction obtains the last lock it requires.
Let’s look at an example:
T1 |
T2 |
|
|---|---|---|
1 |
Lock - S(A) |
|
2 |
Lock - S(A) |
|
3 |
Lock - X(B) |
|
4 |
……. |
……. |
5 |
Unlock(A) |
|
6 |
Lock - X(C) |
|
7 |
Unlock(B) |
|
8 |
Unlock(A) |
|
9 |
Unlock(C) |
|
10 |
……. |
……. |
The way unlocking and locking works in two-phase locking is:
Transaction T1:
- The growing phase is from steps 1-3.
- The shrinking phase is from steps 5-7.
- The locking point is at point 3.
Transaction T2:
- The growing phase is from steps 2-6.
- The shrinking phase is from steps 8-9.
- The locking point is at point 6.
The type mentioned above of 2-PL is Basic 2PL. It ensures Serializability, but it does not prevent Cascading Rollback and Deadlock.






