Introduction
UGC NET Exam is a very popular exam in India for people interested in the research domain. NET(National Eligibility Test) is conducted by NTA (NATIONAL TESTING AGENCY) to identify qualified candidates for Assistant Professor positions in colleges and universities, as well as Junior Research Fellowships (JRF). This article will discuss the UGC NET Exam of Aug 2016 Paper-II(Re-Test) - Part 2 solutions from questions 26 to 50. You can find the solutions to Q1 to 25 in Aug 2016 Paper-II(Re-Test) - Part 1.
26.Which of the following statements is not true with respect to microwaves?
(A) Electromagnetic waves with frequencies from 300 GHz to 400 THz.
(B) Propagation is line-of-sight.
(C) Very high-frequency waves cannot penetrate walls.
(D) Use of certain portions of the band requires permission from authorities.
Answer: A
Explanation:
Frequencies of electromagnetic waves ranging from 300 GHz to 400 THz. It has a frequency range of (0.3 to 300) GHz. As a result, the first option is incorrect. Line-of-sight propagation is used. Correct Walls are impervious to ultra-high-frequency radiation. Correct Authorities must provide permission for certain parts of the band to be used. Correct
27. In a fast Ethernet cabling, 100 Base-TX uses ........... cable and maximum segment size is ............
(A) twisted pair, 100 metres (B) twisted pair, 200 metres
(C) fibre optics, 1000 metres (D) fibre optics, 2000 metres
Answer: A
Explanation:
Fast Ethernet, or 100 Base TX, delivers data at 100 Mbps. The segment is 100 metres long and is made of twisted pair cable. Base is an abbreviation for baseband.
28. A network with bandwidth of 10 Mbps can pass only an average of 12,000 frames per minute with each frame carrying an average of 10,000 bits. What is the throughput of this network ?
(A) 1 Mbps (B) 2 Mbps
(C) 10 Mbps (D) 12 Mbps
Answer: B
Solution:
12,000 frames per minute. Each Frame is carrying 10,000 bits
So, 12,000 * 10,000 / 60 seconds.
= 2 * 1000000 bits / seconds.
= 2 Mbps.
29.Match the following:
List – I List – II
a. Session layer i. Virtual terminal software
b. Application layer ii. Semantics of the information transmitted
c. Presentation layer iii. Flow control
d. Transport layer iv. Manage dialogue control
Codes :
a b c d
(A) iv i ii iii
(B) i iv ii iii
(C) iv i iii ii
(D) iv ii i iii
Answer: A
Solution:
The dialogue control is handled by the session layer.
Application layer software is what virtual terminal software is.
The semantics of the data sent through the display layer.
Flow control is managed by the transport layer.
30.Which of the following protocols is used by email server to maintain a central repository that can be accessed from any machine?
(A) POP3 (B) IMAP
(C) SMTP (D) DMSP
Answer: B
Solution:
The POP3 protocol is the third version of the post office protocol. POP is a protocol that listens on port 110 and is used to access a client machine's mail service. POP3 has two modes of operation: delete mode and keep mode.
IMAP stands for Internet Messaged Access Protocol, and it is used by email servers to keep a central repository accessible from any workstation.
The SMTP protocol stands for Simple Mail Transfer Protocol.
The DMSP protocol stands for distributed mail service protocol.
31.The number of strings of length 4 that are generated by the regular expression (0+1+|2+3+)*, where | is an alternation character and {+, *} are quantification characters, is:
(A) 08 (B) 09
(C) 10 (D) 12
Answer: C
Solution:
0001, 0111, 0011, 0101, 0123, 2323, 2333, 2223, 2233, 2301 are all possible length 4 strings.There are a total of ten strings that can be used.
32.The content of the accumulator after the execution of the following 8085 assembly language program, is
MVI A, 35H
MOV B, A
STC
CMC
RAR
XRA B
(A) 00H (B) 35H
(C) EFH (D) 2FH
Answer: D
Solution:
MVI A, 35H -- content of accumulator = 35H = 0011 0101
MOV B, A -- content of register B = 35H
STC -- set carry flag = 1.
CMC -- complement carry flag = not( 1) = 0.
RAR -- Each binary bit of the accumulator is rotated right by one position through the Carry flag. And modify carry = D0 and D7 = the previous carry.
-- Now content of accumulator = 0001 1010 , carry = 1.
XRA B -- The content of accumulator are exclusive OR with register B.
(0011 0101 ) xor ( 0001 1010 )
= 0010 1111
= 2F H
33.In compiler optimization, operator strength reduction uses mathematical identities to replace slow math operations with faster operations. Which of the following code replacements is an illustration of operator strength reduction?
(A) Replace P + P by 2 * P or Replace 3 + 4 by 7.
(B) Replace P * 32 by P<<5
(C) Replace P * 0 by 0
(D) Replace (P<<4) – P by P * 15
Answer: B
Solution: Multiplication is substituted by the Shift Operator in option (B). Because shift operators are less expensive than multiplication operations, it reduces operator strength.
34.Which of the following are the principles tasks of the linker?
I. Resolve external references among separately compiled program units.
II. Translate assembly language to machine code.
III. Relocate code and data relative to the beginning of the program.
IV. Enforce access-control restrictions on system libraries.
(A) I and II (B) I and III
(C) II and III (D) I and IV
Answer: B
Solution:
A linker is a piece of software that combines two or more files produced by a compiler into one executable file. Option I is accurate, however option II does not look like a linker.
35.Which of the following is FALSE?
(A) The grammar S→aS|aSbS|Î, where S is the only non-terminal symbol, and Î is the null string, is ambiguous.
(B) An unambiguous grammar has same left most and right most derivation.
(C) An ambiguous grammar can never be LR(k) for any k.
(D) Recursive descent parser is a top-down parser.
Answer: B
Solution:An unambiguous grammar has same left most and right most derivation
36.Consider a system with seven processes A through G and six resources R through W.
Resource ownership is as follows:
process A holds R and wants T
process B holds nothing but wants T
process C holds nothing but wants S
process D holds U and wants S & T
process E holds T and wants V
process F holds W and wants S
process G holds V and wants U
Is the system deadlocked ? If yes, ............. processes are deadlocked.
(A) No (B) Yes, A, B, C
(C) Yes, D, E, G (D) Yes, A, B, F
Answer: C
Solution:
system is in Deadlock
due to process D,E,G
37.Suppose that the virtual Address space has eight pages and physical memory with four page frames. If LRU page replacement algorithm is used, .............. number of page faults occur with the reference string.
0 2 1 3 5 4 6 3 7 4 7 3 3 5 5 3 1 1 1 7 2 3 4 1
(A) 13 (B) 12
(C) 10 (D) 9
Answer: A
Solution:
Total 13page faults
38.Consider a system having ‘m’ resources of the same type. These resources are shared by three processes P1, P2 and P3 which have peak demands of 2, 5 and 7 resources respectively. For what value of ‘m’ deadlock will not occur?
(A) 70 (B) 14
(C) 13 (D) 7
Answer: B
Solution: For avoiding deadlock ‘m’ >= peak demands(P1 + P2 + P3)
i.e. m >= peak demands(2 + 5 + 7)
m >= peak demands(14)
39.Five jobs A, B, C, D and E are waiting in Ready Queue. Their expected runtimes are 9, 6, 3, 5 and x respectively. All jobs entered in Ready queue at time zero. They must run in ............. order to minimize average response time if 3 < x < 5.
(A) B, A, D, E, C (B) C, E, D, B, A
(C) E, D, C, B, A (D) C, B, A, E, D
Answer: B
Solution: Clearly, average response time will be minimum in case of "Shortest job first scheduling". Assuming x = 4, Shortest job first scheduling sequence shall be C(3), E(4), D(5), B(6) and A(9)
40.Consider three CPU intensive processes P1, P2, P3 which require 20, 10 and 30 units of time, arrive at times 1, 3 and 7 respectively. Suppose operating system is implementing Shortest Remaining Time first (pre-emptive scheduling) algorithm, then .............. context switches are required (suppose context switch at the beginning of Ready queue and at the end of Ready queue are not counted).
(A) 3 (B) 2
(C) 4 (D) 5
Answer: A
Solution:There are three processes: p1, p2, and p3.
Because p1's arrival time is 1, we decided to run it at that moment.
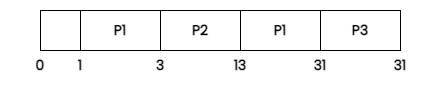
41.Which of the following is used to determine the specificity of requirements ?
(A) n1/n2 (B) n2/n1
(C) n1+n2 (D) n1–n2
Where n1 is the number of requirements for which all reviewers have identical interpretations, n2 is number of requirements in a specification.
Answer: A
Solution:
42.The major shortcoming of waterfall model is
(A) the difficulty in accommodating changes after requirement analysis.
(B) the difficult in accommodating changes after feasibility analysis.
(C) the system testing.
(D) the maintenance of system.
Answer: A
Solution:The difficulty in adapting changes after requirement analysis is a key flaw in the waterfall paradigm.
Minor flaws include system testing, system maintenance, and accommodating changes following a feasibility analysis.
43.The quick design of a software that is visible to end users leads to ............
(A) iterative model (B) prototype model
(C) spiral model (D) waterfall model
Answer: B
Solution:The prototype model is the result of a short design of software that is visible to end users.Every phase of the iterative waterfall model has a feedback link to the phase before it.
44.For a program of k variables, boundary value analysis yields .............. test cases.
(A) 4k – 1 (B) 4k
(C) 4k + 1 (D) 2k – 1
Answer: C
Solution:Boundary value analysis produces 4 * k + 1 test for a programme with k variables.6 * k + 1 worst case testing gives 5 * k in robustness testing.
45.The extent to which a software performs its intended functions without failures, is termed as
(A) Robustness (B) Correctness
(C) Reliability (D) Accuracy
Answer: C
Solution:Reliability refers to how well a piece of software performs its intended functions without failing.
Robustness refers to a product's capacity to survive or overcome adversity or severe testing.
Correctness is defined as the characteristic or state of being error-free; accuracy.
Accuracy refers to how well a measurement, calculation, or specification's result matches the correct value or standard.
46.An attacker sits between the sender and receiver and captures the information and retransmits to the receiver after some time without altering the information. This attack is called as ..............
(A) Denial of service attack (B) Masquarade attack
(C) Simple attack (D) Complex attack
Answer: A
Solution: An attacker sits between the transmitter and the receiver and takes the data, which he then re-transmits to the recipient without changing it after some time. This is referred to as a Denial of Service (DoS) assault.
A masquerade attack occurs when an attacker impersonates an authorised user of a system in order to gain access to it or to obtain more privileges than they are permitted for.
47.................. is subject oriented, integrated, time variant, non-volatile collection of data in support of management decisions.
(A) Data mining (B) Web mining
(C) Data warehouse (D) Database Management System
Answer: C
Solution:A data warehouse is a subject-oriented, integrated, time-variant, and non-volatile data collection that helps management make decisions.
48.In Data mining, classification rules are extracted from ..............
(A) Data (B) Information
(C) Decision Tree (D) Database
Answer: C
Solution:Data mining extracts categorization rules from decision trees rather than databases, information, or data.
49.Discovery of cross sales opportunities is called as ...............
(A) Association (B) Visualization
(C) Correlation (D) Segmentation
Answer: A
Solution: The term "association" refers to the discovery of cross-selling opportunities.
In software engineering, visualisation refers to the representation of data from and about software systems.
In software engineering, correlation is the process of establishing a relationship or connection between two or more snippets.
Memory or a huge quantity can be segmented into various pieces or sections.
50.In Data mining, .............. is a method of incremental conceptual clustering.
(A) STRING (B) COBWEB
(C) CORBA (D) OLAD
Answer: B
Solution:COBWEB is a hierarchical conceptual clustering incremental system. Professor Douglas H. Fisher, currently at Vanderbilt University, invented COBWEB.
FAQs
What is the UGC NET exam for?
The National Eligibility Test (NET) is a test administered by the University Grants Commission (UGC) to determine whether Indian nationals are eligible for Assistant Professorships, Junior Research Fellowships, or both in Indian universities and colleges.
What is UGC NET exam eligibility?
If you hold a Master's Degree or equivalent in Humanities (including languages), Social Science, Computer Science and Applications, Electronic Science, etc., you are eligible to take the UGC NET test.
Is PhD compulsory for net?
To teach in central institutions, one must hold a PhD or have completed the UGC NET qualification exam, according to UGC regulations. The UGC, on the other hand, intends to scrap the regulation requiring experts to be hired and replace it with specific titles such as professor of practice and associate professor of practise.
How many papers are there in the UGC NET exam?
There are two papers, and the candidates get 3 hours for both papers. There are 150 questions in UGC NET combining both papers.
What is the full form of UGC NET?
UGC stands for University Grants Commission, and NET stands for National Eligibility Test.





