Introduction
UGC NET or NTA-UGC-NET is the examination for determining the eligibility for the assistant professor and/or Junior Research Fellowship award in Indian universities and colleges. National Testing Agency examines on behalf of the University Grants Commission. In this article, we will cover questions 51 to 75. We have covered questions 1 to 25 in the first part of UGC NET Nov 2015 PAPER-III Part-1, and 26 to 50 in the second part of UGC NET Nov 2015 PAPER-III Part-2.
Questions
51. What is the most appropriate function of the Memory Management Unit (MMU)?
(A) It is an associative memory to store TLB
(B) It is a technique of supporting multiprogramming by creating dynamic partitions
(C) It is a chip to map virtual addresses to a physical address
(D) It is an algorithm to allocate and deallocate main memory to a process
Answer: C
Explanation: The Memory Management Unit (MMU) is a semiconductor that converts virtually to physical addresses.
52. Dining Philosopher's problem is a:
(A) Producer-Consumer problem (B) Classical IPC problem
(C) Starvation problem (D) Synchronization primitive
Answer: B
Explanation: The dining philosopher's issue is a classic synchronization problem in which Five philosophers sit around a circular table and alternate between thinking and eating.
53. In ............ allocation method for disk block allocation in a file system, insertion and deletion of blocks in a file is easy.
(A) Index (B) Linked
(C) Contiguous (D) Bit Map
Answer: B
Explanation: Insertion and deletion of blocks in a file are simple with the linked allocation approach for disc block allocation in a file system.
54. A UNIX file may be of the type:
(A) Regular file (B) Directory File
(C) Device File (D) Any one of the above
Answer: D
Explanation: Regular, directory, symbolic link, FIFO special, block special, character special, and socket are the seven standard Unix file formats.
55. Match the following:
List-I List-II
(a) Intelligence (i) Contextual, tacit, transfer needs learning
(b) Knowledge (ii) Scattered facts, easily transferrable
(c) Information (iii) Judgemental
(d) Data (iv) Codifiable, endorsed with relevance and purpose
Codes:
(a) (b) (c) (d)
(A) (iii) (ii) (iv) (i)
(B) (iii) (i) (iv) (ii)
(C) (i) (ii) (iii) (iv)
(D) (i) (iii) (iv) (ii)
Answer: B
Explanation: Intelligence makes decisions.
Knowledge can be codified and endorsed for its relevance and utility.
Information is a collection of disparate information that can be easily transferred.
Because data is contextual and tacit, it requires learning to transfer it.
56. Match the following knowledge representation techniques with their applications:
List-I List-II
(a) Frames (i) Pictorial representation of objects,
their attributes and relationships
(b) Conceptual dependencies (ii) To describe real-world stereotype events
(c) Associative networks (iii) Record like structures for grouping
closely related knowledge
(d) Scripts (iv) Structures and primitives to represent
sentences
Codes:
(a) (b) (c) (d)
(A) (iii) (iv) (i) (ii)
(B) (iii) (iv) (ii) (i)
(C) (iv) (iii) (i) (ii)
(D) (iv) (iii) (ii) (i)
Answer: A
Explanation: Frames are used to group closely related knowledge (A-iii), which is only available in options A and B. Scripts are used to explain real-life stereotypical events (D-ii), which is only found in options A and C, hence A is the correct response. Associative networks—-> A visual representation of items, their properties, and their connections. Dependencies between concepts —->Sentence representation structures and primitives.
57. In propositional logic P↔Q is equivalent to (Where ~ denotes NOT):
(A) ~(P∨Q)∧~(Q∨P) (B) (~P∨Q)∧(~Q∨P)
(C) (P∨Q)∧(Q∨P) (D) ~(P∨Q)→~(Q∨P)
Answer: B
Explanation: P ↔ Q = (P → Q) ∧ (Q → P)
P ↔ Q = (~P ∨ Q) ∧ (~Q v P)
58. Which of the following statements is true for the Branch-and-Bound search?
(A) Underestimates of remaining distance may cause deviation from the optimal path.
(B) Overestimates can’t cause the right path to be overlooked.
(C) Dynamic programming principle can be used to discard redundant partial paths.
(D) All of the above
Answer: C
Explanation: Branch and bind is a strategy for tackling combinatorial optimization issues. It speeds up the process when compared to other methods. It separates a problem into two halves. The Dynamic programming approach can be utilised to remove duplicate partial paths in branch and bound search.
59. Match the following with respect to heuristic search techniques:
List-I List-II
(a) Steepest-accent Hill Climbing (i) Keeps track of all partial paths which
can be a candidate for further exploration
(b) Branch-and-bound (ii) Discover problem state(s) that satisfy
a set of constraints
(c) Constraint satisfaction (iii) Detects difference between current
state and goal state
(d) Means-end-analysis (iv) Considers all moves from current
state and selects the best move
Codes:
(a) (b) (c) (d)
(A) (i) (iv) (iii) (ii)
(B) (iv) (i) (ii) (iii)
(C) (i) (iv) (ii) (iii)
(D) (iv) (ii) (i) (iii)
Answer: B
Explanation: The strongest accent Climbing a Hill (Look for the best move which may or may not be optimal)
Branched and linked Keeps track of all partial pathways that might be worth exploring further.
The purpose of a branch-and-bound search is to keep the cheapest path to a target that has been discovered so far and its cost. Assume that this cost is fixed. If the search comes upon a path p that is bound by cost(p)+h(p), the path p can be pruned. If a path to a goal that hasn't been pruned is discovered, it must be better than the prior best path. This new solution is remembered, and the expense of this new solution is bound. It then continues to look for a better answer.
Satisfaction with constraints (Find problem state(s) that meet a set of requirements)
Analysis of means and ends The discrepancy between the existing state and the desired state is detected.
60. Match the following for methods of MIS development:
List-I List-II
(a) Joint Application Design(JAD) (i) Delivers functionality in rapid iteration
measured in weeks and needs frequent communication, development, testing, and delivery
(b) Computer-Aided Software Engg (ii) Reusable applications generally with one
specific function. It is closely linked with the idea of
web services and service-oriented architecture.
(c) Agile development (iii) Tools to automate many tasks of SDLC
(d) Component-based technology (iv) A group-based tool for collecting user requirements and creating system design. Mostly used in the analysis and design stages of SDLC
Codes:
(a) (b) (c) (d)
(A) (i) (iii) (ii) (iv)
(B) (iv) (iii) (i) (ii)
(C) (iii) (iv) (i) (ii)
(D) (iii) (i) (iv) (ii)
Answer: B
Explanation: JAD (Joint Application Development) is a method of incorporating a client or end-user in the design and development of an application through a series of collaborative workshops referred to as JAD sessions. Tools for CASE-> Several SDLC process automation tools —-> Agile software development The Agile SDLC model is a combination of iterative and incremental process models that emphasizes process adaptability and customer satisfaction by delivering a working software solution quickly. The product is divided into small, incremental builds using agile development approaches. These builds have gone through several iterations. Component-based technology allows for reusable apps with a single unique function. Web services and service-oriented architecture are two concepts that are closely related.
61. A context free grammar for L={w|n0(w)>n1(w)} is given by:
(A) S→0|0S|1SS (B) S→0S|1S|0SS|1SS|0|1
(C) S→0|0S|1SS|S1S|SS1 (D) S→0S|1S|0|1
Answer: C
Explanation:
A. S→0∣0S∣1SS (false. since 10001 can't generate)
B. S→0S∣1S∣0SS∣1SS∣0∣1 (false. Since it generates 1)
C. S→0∣0S∣1SS∣S1S∣SS1 (true)
D. S→0S∣1S∣0∣1 (false. since 1^+ generated)
62. Given the following two statements:
S1: If L1 and L2 are recursively enumerable languages over ∑, then L1⋃L2 and L1⋂L2 are also recursively enumerable.
S2: The set of recursively enumerable languages is countable.
Which of the following is correct?
(A) S1 is correct and S2 is not correct
(B) S1 is not correct and S2 is correct
(C) Both S1 and S2 are not correct
(D) Both S1 and S2 are correct
Answer: D
Explanation: Both are True.
Under intersection and union, RES is closed.
A set of RES is analogous to a set of Turing machines that can be counted, hence RES can be counted as well.
63. Given the following grammar:
G1: S→AB|aaB
A→aA|ϵ
B→bB|ϵ
G2: S→A|B
A→aAb|ab
B→abB|ϵ
Which of the following is correct?
(A) G1 is ambiguous and G2 is unambiguous grammar
(B) G1 is unambiguous and G2 is ambiguous grammar
(C) Both G1 and G2 are ambiguous grammar
(D) Both G1 and G2 are unambiguous grammar
Answer: C
Explanation:
Both G1 and G2 are ambiguous in this case
G1: For the string aab, we can create two parse trees.
S S
/ \ / | \
A B a a B
/ \ / \ / \
a A b B b B
/ \ | |
a A ∊ ∊
|
∊
G2: We can generate more than one parse tree for ab.
S S
| |
A B
/ \ / | \
a b a b ∊
64. Given the symbols A, B, C, D, E, F, G, and H with the probabilities 1/30, 1/30, 1/30, 2/30, 3/30, 5/30, 5/30, and 12/30 respectively. The average Huffman code size in bits per symbol is:
(A) 67/30 (B) 70/34
(C) 76/30 (D) 78/30
Answer: C
Explanation: 10100 - 5 bits A
10101 – 5 bits B
1100 – 4 bits – C
1101 – 4 bits D
1011 - 4 bits E
100 – 3 bits F
111 – 3 bits G
0 – 1 bit – H
average 5 * (1 / 30) + 5 * (1 / 30) + 4 * (2 / 30) + 4 * (3 / 30) + 3 * (5 / 30) + 3 * (5 / 30) + 1 * (12 / 30) = 76 / 30 Huffman code size
65. The redundancy in images stems from:
(A) pixel decorrelation (B) pixel correlation
(C) pixel quantization (D) image size
Answer: B
Explanation: Pixel correlation is the source of image redundancy. We can eliminate duplication and totally compress an image by transforming it into a representation in which the pixels are rectified.
66. In a binary Hamming code the number of check digits is r then a number of message digits are equal to:
(A) 2r-1 (B) 2r-r-1
(C) 2r-r+1 (D) 2r+r-1
Answer: B
Explanation: The Hamming Code is essentially the use of additional parity bits to allow for error detection.
67. In the Hungarian method for solving assignment problems, an optimal assignment requires that the maximum number of lines that can be drawn through squares with zero opportunity cost be equal to the number of:
(A) rows or columns (B) rows+columns
(C) rows+columns-1 (D) rows+columns+1
Answer: A
Explanation: The number of lines that can be drawn between squares at no cost is equal to the number of rows or columns.
68. Consider the following transportation problem:
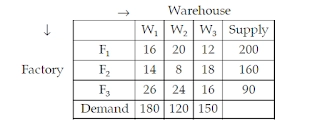
The initial basic feasible solution to the above transportation problem using Vogel’s Approximation Method(VAM) is given below:
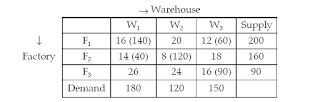
The solution to the above problem:
(A) is the degenerate solution (B) is the optimum solution
(C) needs to improve (D) is the infeasible solution
Answer: B
Explanation:
Because the number of allocations is m+n-1 (3+3-1) m, n being the number of rows and columns, it cannot be a degenerate solution.
Also, because of Total supply=Total demand=450, soln is not infeasible; hence, choices A and D are ruled out for optimality. Next, we'll see if each (Cij)' for the non-allocated cell is non-negative.
choose the row and column with the maximum allocation here we may assign U1=0 then V1=16 as C11=U1+V1 similarly U2=-2 as C21=U2+V1 similarly U3=-4 and V2=10, V3=20 now compute (Cij)' for vacant cell as Cij-(Ui+Vj)
C23=18-(-2+20)=0 for C12=20-(0+10)=10. C31=26-(-4+16)=14 C32=24-(-4+10)=18 are all positive, hence the solution is optimal and requires no improvement.
69. Given the following statements with respect to linear programming problem:
S1: The dual of the dual linear programming problem is again the primal problem
S2: If either the primal or the dual problem has an unbounded objective function value, the other problem has no feasible solution
S3: If either the primal or dual problem has a finite optimal solution, the other one also possesses the same, and the optimal value of the objective functions of the two problems are equal.
Which of the following is true?
(A) S1 and S2 (B) S1 and S3
(B) S2 and S3 (D) S1, S2 and S2
Answer: D
Explanation: The primal problem is the dual of the dual linear programming problem. The other problem has no conceivable solution if either the primal or dual problem has an unlimited objective function value.If one of the primal or dual issues has a finite optimal solution, the other has the same, and the optimal values of the two problems' objective functions are equivalent.
70. Consider the two-class classification task that consists of the following points:
Class C1: [1 1.5] [1 -1.5]
Class C2: [-2 2.5] [-2 -2.5]
The decision boundary between the two classes using single perceptron is given by:
(A) x1+x2+1.5=0 (B) x1+x2-1.5=0
(C) x1+1.5=0 (D) x1-1.5=0
Answer: C
Explanation: Simply plot all of C1 and C2's points in 2-D coordinates and observe which option's line separates the points of C1 and C2. All of C1's points should be on one side of the line and all of C2's points should be on the other.
Only the line x1 + 1.5 =0 in option C accomplishes this.
71. Let A and B be two fuzzy integers defined as:
A={(1,0.3), (2,0.6), (3,1), (4,0.7), (5,0.2)}
B={(10,0.5), (11,1), (12,0.5)}
Using fuzzy arithmetic operation given by
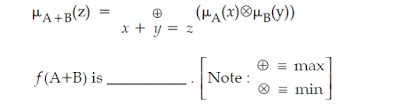
(A) {(11,0.8), (13,1), (15,1)}
(B) {(11,0.3), (12,0.5), (13,1), (14,1), (15,1), (16,0.5), (17,0.2)}
(C) {(11,0.3), (12,0.5), (13,0.6), (14,1), (15,1), (16,0.5), (17,0.2)}
(D) {(11,0.3), (12,0.5), (13,0.6), (14,1), (15,0.7), (16,0.5), (17,0.2)}
Answer: D
Explanation: According to query:
A={(1,0.3), (2,0.6), (3, 1), (4, 0.7), (5, 0.2)}
B={(10, 0.5), (11, 1), (12, 0.5)}
A+B(Z) = (x+y=z) =(A(x)B(y)) is given as follows (add elements of A and B while maintaining the minimum membership value, e.g. 1+10 =11 and min(0.3,0.5)=0.3 and so on for the rest).
D {(11,0.3), (12,0.5), (13,0.6), (14,1), (15,0.7), (16,0.5), (17,0.2)}
72. Suppose the function y and a fuzzy integer number around -4 for x are given as
y=(x-3)^2+2
Around -4={(2,0.3), (3,0.6), (4,1), (5,0.6), (6,0.3)} respectively. Then f(Around -4) is given by:
(A) {(2,0.6), (3,0.3), (6,1), (11,0.3)}
(B) {(2,0.6), (3,1), (6,1), (11,0.3)}
(C) {(2,0.6), (3,1), (6,0.6), (11,0.3)}
(D) {(2,0.6), (3,0.3), (6,0.6), (11,0.3)}
Answer: C
Explanation: y= (x-3)^2+2
around-4=((2, 0.3), (3, 0.6), (4, 1), (5, 0.6), (6, 0.1) putting x= 2, 3, 4, 5, 6 in 4=(x-3)^2+2 will provide 3 2 3 6 11 with their original x membership values (.3,.6,.1,.6,.3) here is present with 2 membership values 3 & 1 thus I is examined & the end result will be (3,1), (2,.6) (11,.3).
73. Match the following for UNIX system calls:
List-I List-II
(a) exec (i) Creates a new process
(b) brk (ii) Invokes another program overlaying memory
space with a copy of an executable file
(c) wait (iii) To increase or decrease the size of the data region
(d) fork() system call (iv) A process synchronizes with the termination of the child process
Codes:
(a) (b) (c) (d)
(A) (ii) (iii) (iv) (i)
(B) (iii) (ii) (iv) (i)
(C) (iv) (iii) (ii) (i)
(D) (iv) (iii) (i) (ii)
Answer: A
Explanation: exec: replaces the current program in the current process without forking a new process.
Brk() and sbrk() are used to shift the program break, which indicates the end of the process's data segment ().
The parent process can then use the wait system call to pause its execution while the child executes.
A new procedure is started via forking.
74. WOW32 is a:
(A) Win 32 API library for creating processes and threads.
(B) Special kind of file system to the NT namespace.
(C) Kernel - mode objects accessible through Win32 API
(D) Special execution environment used to run 16-bit Windows applications on 32 - bit machines.
Answer: D
Explanation: Wow 32 is a Windows operating system that allows 16-bit Windows applications to run on a 32-bit PC.
75. The Unix command:
$ vi file1 file2
(A) Edits file1 and stores the contents of file1 in file2
(B) Both files i.e. file1 and file2 can be edited using the ‘ex’ command to travel between files
(C) Both files can be edited using the ‘mv’ command to move between the files
(D) Edits file1 first, saves it, and the edits file2
Answer: B
Explanation:
With vi, You can work on many files at once.
vi file1 file2 vi simultaneously two (or more) files.




