Introduction
UGC NET or NTA-UGC-NET is the examination for determining the eligibility for the assistant professor and/or Junior Research Fellowship award in Indian universities and colleges. National Testing Agency examines on behalf of the University Grants Commission.
We have covered questions 1 to 25 in the first part of UGC NET Dec 2013 PAPER-III Part-1, 51-75 in the third part of UGC NET Dec 2013 PAPER-III Part-3. In this article, we will cover questions 26 to 50.
Questions
26. The means-end analysis process centers around the detection of differences between the current state and the goal state. Once such a difference is isolated, an operator that can reduce the difference must be found. But perhaps that operator can not be applied to the current state. So a sub-problem of getting to a state in which it can be applied is set up. The kind of backward chaining in which operators are selected and then sub-goals are set up to establish the precondition of operators is called
(A) backward planning
(B) goal stack planning
(C) operator subgoals
(D) operator overloading
Answer: C
Explanation: If an operator has been chosen but cannot be applied to the current state, creating a subgoal to discover a state where the operator can be applied is a beneficial method. This tactic is known as *operator subgoaling* (also known as precondition satisfaction) and is a popular AI technique.
27. In alpha-beta pruning, _________ is used to cut off the search at a maximizing level only, and _________ is used to cut off the search at minimizing level only.
(A) alpha, beta
(B) beta, alpha
(C) alpha, alpha
(D) beta, beta
Answer: B
Explanation: The minimax method has been tweaked to include alpha-beta pruning. It is a strategy for optimising the minimax algorithm.
28. If A and B are two fuzzy sets with membership functions μA(x) = {0.2, 0.5, 0.6, 0.1, 0.9} μB(x) = {0.1, 0.5, 0.2, 0.7, 0.8} Then the value of μA ∩ B will be
(A) {0.2, 0.5, 0.6, 0.7, 0.9}
(B) {0.2, 0.5, 0.2, 0.1, 0.8}
(C) {0.1, 0.5, 0.6, 0.1, 0.8}
(D) {0.1, 0.5, 0.2, 0.1, 0.8}
Answer: D
Explanation: μA∩B(x) = min [μA(x), μB(x)]
μAᴜB(x) = max [μA(x), μB(x)]
µA’(x) = 1 - µA(x)
29. The height h(A) of a fuzzy set A is defined as h(A) = sup A(x) x ∈ A Then the fuzzy set A is called normal when
(A) h(A) = 0
(B) h(A) < 0
(C) h(A) = 1
(D) h(A) < 1
Answer: C
Explanation: When h(A)=1, that is, when the height or membership function is 1, the fuzzy set becomes a normal or crisp set choice. A implies the element does not belong to the set, therefore neither a fuzzy nor a normal choice is available. Choice B is undefined (non-meaningful), as is choice D. Both cannot be the same, hence if it is more than zero, it will be only a fuzzy set and not a normal set.
30. An artificial neuron receives n inputs x1, x2,...., xn with weights w1, w2,...., wn attached to the input links. The weighted sum ________ is computed to be passed on to a non-linear filter φ called activation function to release the output.
(A) Σ wi
(B) Σ xi
(C) Σ wi + Σ xi
(D) Σ wi ⋅ xi
Answer: D
Explanation: weighted sum is calculated by multiplying inputs by their respective weights and then adding them all
which can be shown as Σ wi ⋅ xi
31. Consider the formula in image processing RD = 1 – C1R. CR = nn12 CR is called compression ratio n1 and n2 denotes the number of information-carrying units in two datasets representing the same information. In this situation, RD is called as relative _________ of the first data set.
(A) Data Compression
(B) Data Redundancy
(C) Data Relation
(D) Data Representation
Answer: B
Explanation: Data redundancy occurs when numerous copies of the same information are kept in various locations at the same time.
32. Find the false statement :
(A) In Modern Cryptography, symmetric key algorithms use the same key both for Encryption and Decryption.
(B) The symmetric cipher DES (Data Encryption Standard) was widely used in the industry for security products.
(C) The AES (Advanced Encryption Standard) cryptosystem allows variable key lengths of size 56 bits and 124 bits.
(D) Public key algorithms use two different keys for Encryption and Decryption.
Answer: C
Explanation: The AES (Advanced Encryption Standard) cryptosystem allows variable key lengths of size 128 bits , 192 bits and 256 bits . 56 is used by DES.
33. The message 11001001 is to be transmitted using the CRC polynomial x3 + 1 to protect it from errors. The message that should be transmitted is
(A) 110010011001
(B) 11001001
(C) 110010011001001
(D) 11001001011
Answer: D
Explanation: The degree of the generator polynomial is 3; hence 3-bits are appended before performing division. After performing division using 2′s complement arithmetic remainder is 011 The remainder is appended to original data bits and we get M′=11001001011 from M=11001001.
34. _________ comparisons are necessary in the worst case to find both the maximum and minimum of n numbers.
(A) 2n – 2
(B) n + floor (lg n) – 2
(C) floor(3n/2)
(D) 2 lg n – 2
Answer: C
Explanation: Upper bound is 2(n-1)
Lower bound is Ceil ( 3/2n - 2 )
35. Let A and B be two n × n matrices. The efficient algorithm to multiply the two matrices has the time complexity
(A) O(n3)
(B) O(n2.81)
(C) O(n2.67)
(D) O(n2)
Answer: B
Explanation: the efficient algorithm to multiply the two matrices has the complexity O(n^2.81) using stressonr’s algorithm
36. The recurrence relation T(n)=mT(n/2) tan^2 is satisfied by
(A) O(n2)
(B) O(n1g m)
(C) O(n2 lg n)
(D) O(n 1g n)
Answer: B
Explanation: according to Master Theorem a=m , b=2 and f(n)=an2
nlog2m > f(n) for all m>4 [Using case-1: Master Theorem]
So, solution is O(nlog2m)
37. The longest common subsequence of the sequences X = <A, B, C, B, D, A, B> and Y = <B, D, C, A, B, A> has length
(A) 2
(B) 3
(C) 4
(D) 5
Answer: C
Explanation: The LCS of X and Y are BCBA, BDAB, BDBA (which can be observed from the list they may or may not be continuous in appearance ) i.e. are of length 4.
38. Assuming there are n keys and each key is in the range [0, m – 1]. The run time of bucket sort is
(A) O(n)
(B) O(n lgn)
(C) O(n lgm)
(D) O(n + m)
Answer: D
Explanation: Best and Avg. case= O(n+m)
worst case= O(n^2)
39. A _________ complete subgraph and a _________ subset of vertices of a graph G = (V, E) are a clique and a vertex cover respectively.
(A) minimal, maximal
(B) minimal, minimal
(C) maximal, maximal
(D) maximal, minimal
Answer: D
Explanation: Clique- A clique is a subset of a graph's vertices in which every two different vertices are nearby ( Every two vertices adjacent means a complete subgraph).
A minimal vertex cover of a graph is a collection of minimum vertices such that each edge of the graph is incident to at least one of the set's vertices.
40. The pumping lemma for context-free languages states: Let L be an infinite context-free language. Then there exists some positive integer m such that any w ∈ L with |w| ≥ m can be decomposed as w = uv xy Z with |vxy| _________ and |vy| _________ such that uvz'xyz'Z ∈ L for all z’ = 0, 1, 2, .......
(A) ≤ m, ≤ 1
(B) ≤ m, ≥ 1
(C) ≥ m, ≤ 1
(D) ≥ m, ≥ 1
Answer: B
Explanation: Assume L is an infinitely context-free language. Then there is some positive integer m such that if S is a string of L with a length greater than m, then
- S = uvwxy (for some u, v, w, x, y)
- |vwx| m
- |vx| 1
- uviwxiy ∊ L
for all nonnegative values of i.
41. The Greibach normal form grammar for the language L = {a^n b^n + 1 | n ≥ 0} is
(A) S → a SB, B → bB | λ
(B) S → a SB, B → bB | b
(C) S → a SB | b, B → b
(D) S → a Sb | b
Answer: C
Explanation: Only from option C we can generate all required string (b,abb,aabbb.....).
42. Given the following statements: S1: Every context-sensitive language L is recursive. S2: There exists a recursive language that is not context-sensitive. Which statement is correct? (A) S1 is not correct, and S2 is not correct.
(B) S1 is not correct, and S2 is correct.
(C) S1 is correct, and S2 is not correct.
(D) S1 is correct, and S2 is correct.
Answer: D
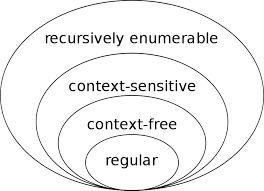
Explanation: Both are correct since context-sensitive is a proper subset of recursive languages.
43. What is the bit rate for transmitting uncompressed 800 × 600-pixel color frames with 8 bits/pixel at 40 frames/second?
(A) 2.4 Mbps
(B) 15.36 Mbps
(C) 153.6 Mbps
(D) 1536 Mbps
Answer: C
Explanation: Uncompressed pixel = 800*600 per 8 bit = 800*600 *8 Bit rate for transmission = 800*600 *8 *40 =153600000 = 153.6Mbps
44. In IPV 4, the IP address 200.200.200.200 belongs to
(A) Class A
(B) Class B
(C) Class C
(D) Class D
Answer: C
Explanation: In classful addressing, the address space is divided into five classes:A, B, C, D, and E.
45. Which layer of the OSI reference model is responsible for the decomposition of messages and generation of sequence numbers to ensure correct re-composition from end to end of the network?
(A) Physical
(B) Data-link
(C) Transport
(D) Application
Answer: C
Explanation: The fourth layer in the OSI Reference Model is the transport layer. It reacts to Session layer service requests and issues Network layer service requests. The Transport Layer is in charge of transmitting communications between hosts.
46. A client-server system uses a satellite network, with the satellite at 40,000 km. What is the best-case delay in response to a request? (Note that the speed of light in air is 3,00,000 km/second).
(A) 133.33 msec
(B) 266.67 msec
(C) 400.00 msec
(D) 533.33 msec
Answer: D
Explanation: The request must ascend and descend, and the response must ascend and descend. As a result, the overall length of the trail walked is 160.000 km. Because the speed of light in air and vacuum is 300,000 km/sec, the propagation delay is 160,000/300,000 sec, or approximately 533 msec. The request must ascend and descend, and the response must ascend and descend. As a result, the overall length of the trail walked is 160.000 km. Because the speed of light in air and vacuum is 300,000 km/sec, the propagation delay is 160,000/300,000 sec, or approximately 533 msec.
47. The start and stop bits are used in serial communication for
(A) error detection
(B) error correction
(C) synchronization
(D) slowing down the communication
Answer: C
Explanation: Start and stop bits are used in serial communication for synchronization. The start and stop bits are used in asynchronous communication as a means of timing or synchronizing the data characters being transmitted.
48. _________ is a type of transmission impairment in which the signal loses strength due to the resistance of the transmission medium.
(A) Attenuation
(B) Distortion
(C) Noise
(D) Decibel
Answer: A
Explanation: Attenuation is a broad phrase that refers to any drop in signal intensity. Attenuation can happen with any sort of signal, digital or analogue.
49. Match the following:
| List – I | List – II |
| a. Indexed Addressing | i. is not used when an operand is moved from memory into a register or from a register to memory. |
| b. Direct Addressing | ii. The memory address is computed by adding up two registers plus an (optional) offset. |
| c. Register Addressing | iii. Addressing memory by giving a register plus a content offset. |
| d. Base-Indexed Addressing | iv. can only be used to access global variables whose address is known at compile time. |
Codes:
a b c d
(A) ii i iv iii
(B) ii iv i iii
(C) iii iv i ii
(D) iii i iv ii
Answer: C
Explanation:
(a) Indexed addressing is the operand's offset is the sum of the content of an index register S1 or DI and an 8 bit or 16-bit displacement, so it satisfies (3)
(b) Direct addressing is the operand's offset given in the instruction as an 8-bit displacement. In this mode, the 16-bit effective address of the data is the part of the instruction, so it satisfies (4)
(c) Register addressing is placed in one of 8-bit or 16-bit general-purpose registers. So it satisfies (1)
(d) Base indexed addressing is the operand offset is the sum of the content of a base register BX or BP and an index register S1 or D1. (2)
50. Which of the following is a design criterion for instruction formats?
(A) The size of instructions
(B) The number of bits in the address fields
(C) The sufficient space in the instruction format to express all the operations desired.
(D) All of these
Answer: D
Explanation: Instruction Format Design Criteria (How to outlast the current processor.)
1. Instruction Size Balance instruction size against needed capabilities, addressing, and inst. Fetch times are often measured in terms of word length or multiple word lengths. Consider the instruction fetch and instruction constructing, both of which needed numerous words. Fetching takes more time... as a result of this there are fewer instructions per second (average memory access time and I-cache make a difference)
2. Include enough bits to describe "ALL" operations to allow for future expansion, as well as certain "unassigned" opcodes.
3. Determine any address range or size constraints; a 32-bit address by byte only accesses 4GB of space. The address field size is determined on the number of RISC registers (32 regs 5 bits each)




