Message Authentication Codes
Suppose two users, a sender and a receiver, want to communicate using messages. In MAC or Message Authentication Codes, the sender and receiver share the same MAC Algorithm or Key.
What is MAC Algorithm?
It is a combination of Key Value and a Cryptographic function used to encode or decode a text.
Working of Message Authentication Codes
The following steps explain the working of Message Authentication Codes for checking the message integrity:
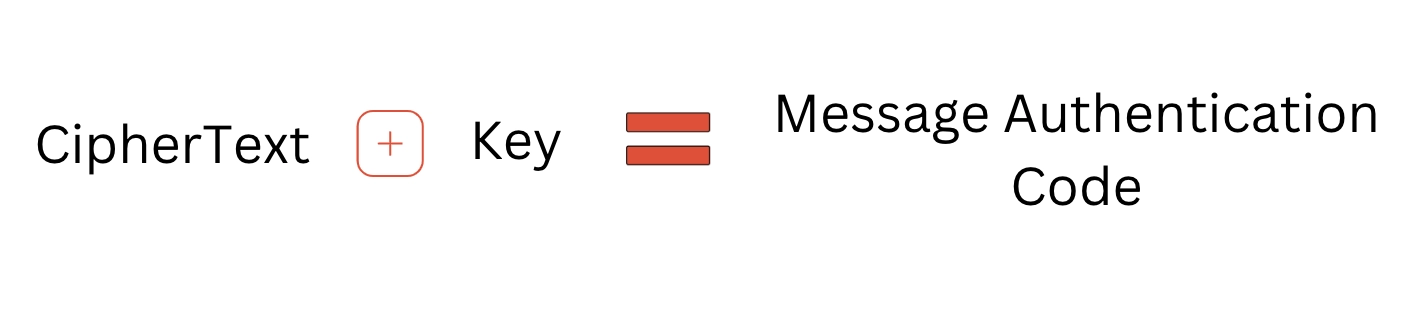
- The sender first uses the MAC Algorithm on the text message and generates an output called ciphertext.
-
Sender then combines ciphertext and key. This combination is called a MAC Code or Message Authentication Code.
- Sender shares that Message Authentication Code with the receiver.
- Once the receiver receives the Message Authentication Code, the receiver again runs the MAC Algorithm on the message to generate another Authentication Code. Then the receiver compares it with the Authentication code sent by the sender. If they match, then the message is verified; else, not.
Signature Schemes

In the real world, a signature is used to verify the authenticity of a document. Similarly, in the digital world, digital signatures can be used to verify digital messages. It is another way to check the authenticity of the messages.
Signature schemes also work in the same way as Message Authentication Codes.
This binds the user to the digital data.
Signing the digital data and verifying the same is based on the public and private keys principle.
Public Key
As the name suggests, this key is accessible to almost anyone. The receiver can decrypt the data using this key.
Private Key
Only the primary user has this key, also known as the secret key. This key encrypts the data and sends it to the sender.
Working of Signature Schemes
The signature schema works in the following manner:
- The Sender uses the private key to encrypt and send the message. The encrypted output is called a signature.
- The signature is appended to the original message.
- The receiver of the message on the other end holds a Public Key.
- The receiver then decrypts the message using Public Key. The encrypted signature can be decrypted and verified if the message is authentic.
Nonrepudiation
Non-Repudiation is the assurance that both sender and the receiver have acknowledged the information or the data so that neither can deny that they have received or sent the information.
Let us understand this in more straightforward terms.
Signature Schema
Suppose we are using Signature Schema. Since the key at the receivers’ end is a Public Key, anyone can verify the integrity of the message. Therefore, the reciever can show the message and the signature to anyone else and be sure that the other person will also consider the message authentic.
Similarly, it is impossible for the sender to sign the message and later claim that he did not. This phenomenon is called nonrepudiation.
Message Authentication Codes
In the case of MAC, there is no Public Key. There is a single private key that only the sender and the reciever have. Therefore, there is no third-party interference. Even if somehow third-party user got access to the secret key, he could not ensure that the sender or the receiver signs the message because both can encrypt or decrypt the message. So, MAC doesn’t provide non-repudiation. It is termed as Deniable.
Certificates

We mentioned earlier something about Public keys. Keys are accessible to almost anyone in public. Now Suppose, we have a public key. Do we actually know that the public key we received is valid? Of course not!
We need to find out if the public key itself is authentic enough. That’s where certificates come into action. A certificate is a digital document that proves a public key's validity. The certificate contains details regarding the key, information regarding the owner's identity, and the organization's digital signature that has examined the certificate's contents.
Most common examples include email encryption and SSL (Secure Socket Layer).
Hash Functions

A hash function is a public function accessible to everyone. The hash function takes a text message as input and generates a fixed-size output string called Hash Value. This is used to decrease the size of the input messages and is very useful when the message to be sent is lengthy.
Hashing is used along with Signature Schema or Message Authentication Codes to improve the overall efficiency of both algorithms.
Names of standard hashing algorithms are:
- MD5: It Generates a 128-bit Hash Value
- SHA-1: It Generates a 160-bit Hash Value
- SHA-2: It Generates a 2256-bit hash Value
Frequently Asked Questions
What is a public key?
As the name suggests, this key is accessible to almost anyone. The sender can encrypt the data using this key, and the receiver can decrypt the data using this key.
What is a private key?
This is also known as the secret key. Only the sender has a copy of the private key used to encrypt or sign a digital document.
What are digital certificates?
Digital Certificate is a digital document used to prove a public key's validity. The certificate contains details regarding the key and the owner's identity.
What do you understand by MAC Algorithm?
MAC stands for Message Authentication Code. Mac Algorithm combines Key Value and a Cryptographic function to encode or decode a text.
Conclusion
This article deeply discussed the definition of Message Integrity and how it is achieved. We also learned about the different algorithms or techniques used to verify a message's authenticity.
For more cryptography-related content, you can visit What is Cryptography, Cryptographic System, and Public key Cryptography.
Recommended Readings:
Please refer to our guided paths on Coding Ninjas Studio to learn more about DSA, Competitive Programming, JavaScript, System Design, etc. And also, enroll in our courses and refer to the mock test and problems available. Have a look at the interview experiences and interview bundle for placement preparations.
Keep learning, and Keep Growing!
Happy Learning!










