Introduction
Every time access our smartphone, laptop, smart TV or any other electronic gadget, we generate data. Heck, our smartwatches even generate data while we sleep. Truly, the 21st century is the ‘Internet Age’ which has revolutionised the way we live.
The outbreak of the Covid-19 pandemic has further aided to our dependence on technology. Every aspect of our life, from work to working out, has moved online. It has disrupted some industries like aviation and hospitality and forced many conventional businesses to go online. Seeing the recent trend, the numbers published by DOMO in its 8th Edition of Data Never Sleeps comes as no surprise.
In 2020, the internet has reached almost 60% of the population and each individual creates around 1.7MB of data every second. Every minute, people spend $1,000,000 online, stream 404,444 hours of video on Netflix, upload 500 hours of video on YouTube and post 347,222 stories on Instagram.
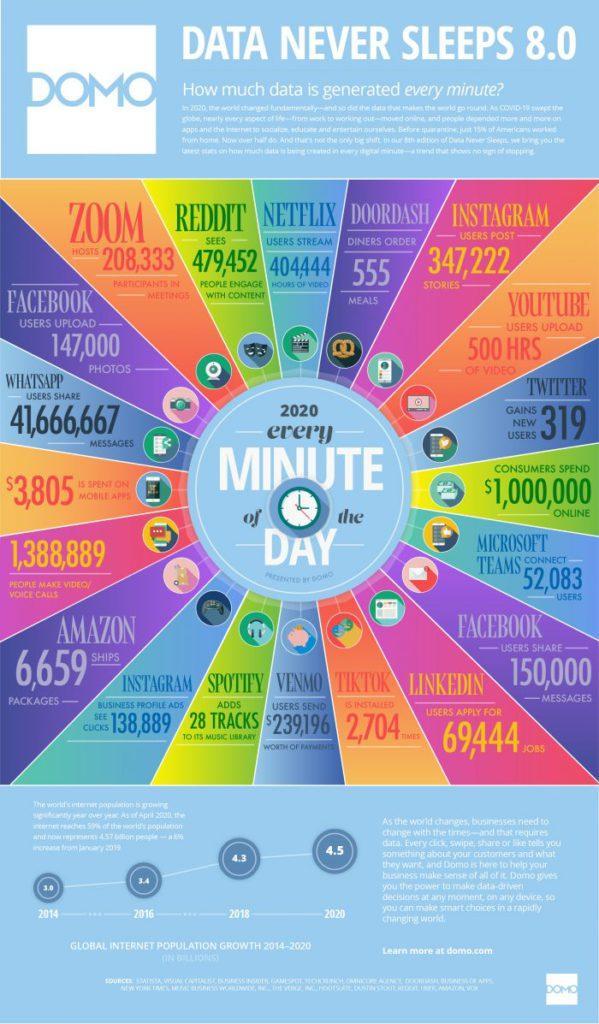 Source: DOMO Data Never Sleeps 8.0
Source: DOMO Data Never Sleeps 8.0
Evidently, every company aims to collect as many data points as possible and make sense out of it to learn about its customers and make data-driven decisions to drive revenues. Hence, every company’s information is its holy grail. Hackers, unable to collect these huge amounts of information by themselves, try to gain access to this information.
Although this information doesn’t seem important its theft can have some serious repercussions since some of this data is highly confidential. Hackers try to access the financial details of an individual to transfer the money in the individual’s account to their account, misuse the unique identification of an individual to steal their digital identity, access the data to a country’s military secrets, etc.
What exactly is ‘Data Theft’?
According to the U.S. Department of Justice, data theft or data breach is defined as “The loss of control, compromise, unauthorised disclosure, unauthorised acquisition, access for an unauthorised purpose, or other unauthorised access, to data, whether physical or electronic.” Keeping the information on customers safe is one of the biggest concerns of companies.
According to Kaspersky IT budget calculator, companies on an average allot a budget of almost a million dollars to their IT security in 2020, which is almost 40% more than the budget allotted in 2019. This budget comprises about 26% of the total IT spend. Moreover, following the current trend, the companies are assumed to increase their IT budget by 12% by 2023.
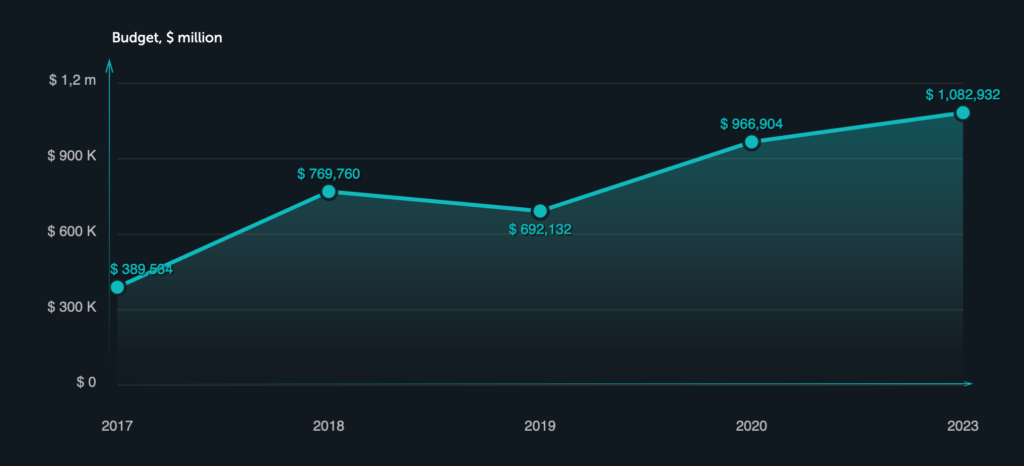 Source: Kaspersky IT Security Calculator
Source: Kaspersky IT Security Calculator
Despite all these painstaking efforts, about 45% of threats reported in the last 12 months are of data being breached. So, is it really worth spending almost a million dollars on IT security? Definitely! The security of any software is as good as its weakest link. If the weakest link is easily exploitable, companies will be susceptible to more attacks.
On average, the cost of one security incident is $312,117. Thus, it makes total sense to invest in securing data rather than being susceptible to data breaches. While the early adopters of data security policy were IT, banking and financial services, other organisations are catching up to improve their data security.
Also read - active and passive attacks




